

The simple answer to the question as to whether you are vulnerable to Domain Hijacking is a resounding yes; your website and your business identity absolutely need to be protected from this threat. And, in fact, Domain Hijacking is a threat that every website owner will want to take steps to protect themselves from.
Domain Hijacking occurs when an attacker changes the registration of a domain name without the consent of the original registrant. In the last few years, there have been cases of domain hijacking owned by major brands, including Donald Trump’s website in 2017. Just a year after Trump had attacked Clinton for her “treasonously weak cybersecurity,” Trump’s website secure2.donaldjtrump.com, which was mainly used for fundraising, was defaced and taken over by a hacker acting under the pseudonym “Pro_Mast3r.”
A hacked domain can result in a damaged reputation as well as a loss of income. The attacker could demand money in exchange for returning the domain or use the domain to redirect to another site for malicious activity.
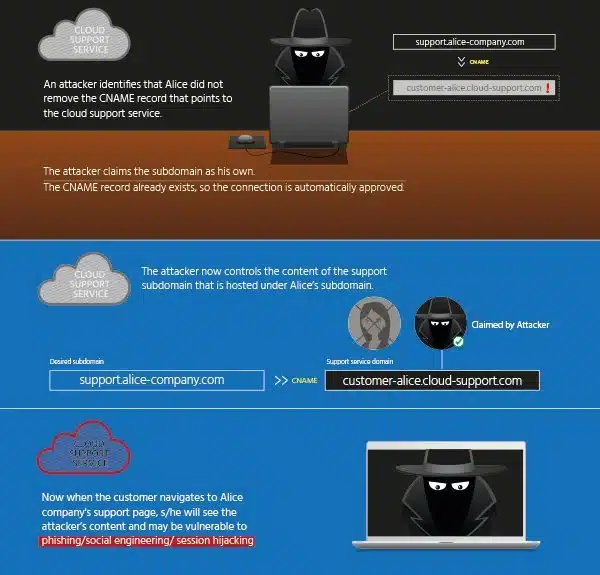
With the popularity of cloud services, one of the more common ways domains are hijacked is through the exploitation of neglected DNS records tied to cloud services. The situation creates itself when an organization uses a cloud service to build a resource and configure a subdomain for users to access the resource using CNAME or DNAME records. If the DNS records for the subdomain are not removed when the cloud resource is gone, anyone can claim the subdomain and there is no notification to the original domain owner of the change. This is also the case if an organization forgets to renew domain registration.
CyberInt’s research team has noted that a large number of cloud providers don’t perform ownership verification on domains and subdomains, which means anyone can claim ownership of abandoned or expired domains. Resolving the issue with the cloud provider may be troublesome since the original owner is no longer a customer thus the provider doesn’t feel any responsibility for the issue.
Domain hijacking can be a segway into further attacks. The attacker can leverage the domain to conduct a phishing campaign as the targets will have no way to discern the content is not originating from the original domain owner. More extensive attacks can be launched if applications use session cookies with a wildcard domain. If an attacker can lure users to a hijacked domain, they can extract the cookies, including cookies with a secure flag.
CyberInt’s Subdomain Takeover Tool can help organizations gain insight into their domains and subdomains to determine if they are vulnerable to domain hijacking attacks. This tool scans the domain and automatically discovers any existing subdomains and checks for domain hijacking vulnerabilities. The user is sent an email with the list of discovered assets, vulnerabilities found, and remediation recommendations.
Once a subdomain is hijacked the results can be severe and extremely difficult – let alone time consuming – to recover.
Click Here – protect your organization and scan your domains now!
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


