


The AXA Group has been targeted by Ransomware and the threat actors have publicly announced this incident.
AXA Group’s IT Operations were affected regionally in the Philippines, Thailand, Malaysia and Hong Kong. The hostaged data, amounting to approximately 3 terabytes, consisted of customers’ personally identifiable information, health records, medical claims, patients’ personal health conditions, photos of IDs and passports, bank documents, and hospital invoices.
The Avaddon attackers shame victims who do not pay the ransom on their site avaddongun7rngel[.]onion.
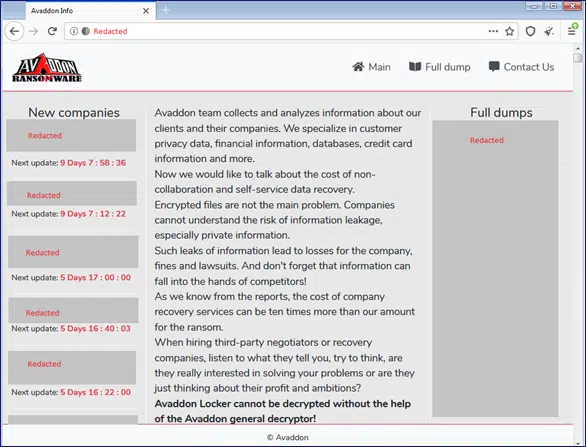
Figure 1: Screenshot of the Avaddon announcement blog
They demand approximately $40,000 in BTC for a decryption tool that will release the victim organization from the ransomware. Those who would like to enter negotiations with Avaddon may do so at hxxp://avaddonbotrxmuyl[.]onion upon entering their ID.
While a decryptor was released in February 2021 – a result of a flaw in the Avaddon encryption discovered by a security researcher that gave rise to a free decryptor – Avaddon quickly modified the encryption process one day later, rendering it ineffective.
The Avaddon ransomware has been active since June 2020 and is operating with the Ransomware-as-a-Service (RaaS), where the victim is tricked into downloading a malware loader. It is mostly distributed via malspam campaigns that lure victims with a supposed image of them in the email attachment.

Figure 2: Screenshot of Avaddon’s announcement of AXA’s compromise
In January 2021 Avaddon announced that they will launch DDoS attacks against victims until they begin ransom negotiations, potentially hampering recovery efforts and piling even more pressure on the victims.
The group has already reportedly launched a DDoS attack against the affected AXA Group assets and there are additional reports of other AXA Group companies being “DDoSed”. It is unclear if the latter is being carried out by Avaddon or by another threat actor group dissatisfied with the fact that the insurance provider will no longer cover ransom payments in France. Previously, many ransomware groups have relied on cyber-insurance policies covering their demands as it increases their chances of being paid.
The hackers have since deployed the Sliver open-source tool to maintain access to victims’ networks.
They have also been observed exploiting multiple publicly known vulnerabilities, including the recently disclosed zero-days in Microsoft Exchange.
In one observed incident, the actors used access gained from the SolarWinds exploit to compromise a certificate issued by Mimecast.
Victims receive a ransom note that appears as follows:
-------=== Your network has been infected! ===-------
***************** DO NOT DELETE THIS FILE UNTIL ALL YOUR DATA HAVE BEEN RECOVERED *****************
All your documents, photos, databases and other important files have been encrypted and have the extension: <FILE_EXTENSION>
You are not able to decrypt it by yourself. But don't worry, we can help you to restore all your files!
The only way to restore your files is to buy our special software. Only we can give you this software and only we can restore your files!
We have also downloaded a lot of private data from your network.
If you do not contact as in a 3 days we will post information about your breach on our public news website (avaddongun7rngel[.]onion) and after 7 days the whole downloaded info.
You can get more information on our page, which is located in a Tor hidden network.
How to get to our page
--------------------------------------------------------------------------------
1. Download Tor browser - https://www.torproject[.]org/
2. Install Tor browser
3. Open link in Tor browser - avaddonbotrxmuyl[.]onion
4. Follow the instructions on this page
--------------------------------------------------------------------------------
Your ID:
--------------------------------------------------------------------------------
<BASE64_ENCODED_DATA>
--------------------------------------------------------------------------------
* DO NOT TRY TO RECOVER FILES YOURSELF!
* DO NOT MODIFY ENCRYPTED FILES!
* * * OTHERWISE, YOU MAY LOSE ALL YOUR FILES FOREVER! * * *
<POTENTIAL_VICTIM_ID>
Cyberint has observed Russian threat actors of the same name, “Avaddon”, conducting recruitment activities since February 2021, with indicators of high levels of organization and an adherence to a strict code of conduct.
Since May 11, threat actors have been using the Avaddon ransomware to target healthcare and health insurance organizations in the U.S., Australia and Asia-Pacific.

Figure 3: Cyberint observes Russian threat actors announcing changes in ransomware conduct
However, on May 14 and 15, they posted the following on a hacker forum (See Figure 3):
Due to the situation currently ongoing in the USA, we are adding several new rules:
2. It is prohibited to [attack] the government sector, the healthcare sector and education organizations
3. Before you start working on a target, you have to coordinate with the affiliate program admins via a ticket.
Any violation of the rules will lead to deletion of the account. We are transferring to private (business, not via forums), please contact us via active adverts.

Figure 4: Threat actors advertise rates for interested collaborators
On March 2021, Avaddon became more aggressive in their recruitment, publicly stating their rates for collaborators. On March 4, they wrote:
We are ready to accept only networkers with a start rate of 25/75. When the volume is ready to do in the flesh up to 15/85.
We are also ready to accept pentesters for work under%. We are discussing the percentage.
Throw off your applications in pm.
On March 9, they updated with:
We are ready to accept networkers with a start rate of 20/80
We also remind you that [bots] are actively phoning and spamming. Also, if a [bot] gets into a blog, [it] is actively DDoS attacks and floods.
Inactive for 2 weeks without warning – the account is deleted!
Throw off applications in the PM. Anything like * let the contact have a deal * is ignored.
Also, the development of a new version of the Avaddon V2 locker has begun.
On March 31, threat actors clarified that they will only work with Russian-speaking threat actors (see Figure 5).
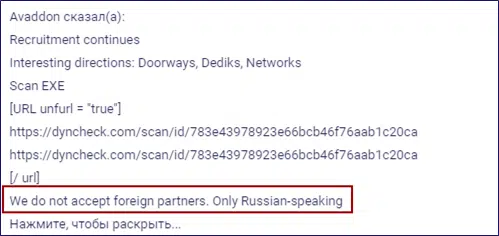
Figure 5: Threat actors announce that they only work with Russian-speaking threat actors
Avaddon ransomware samples identified in May 2021 include (SHA256):
0ff4058f709d278ed662719b9627618c48e7a656c59f6bfecda9081c7cbd742b2946ef53c8fec94dcdf9d3a1afc077ee9a3869eacb0879cb082ee0ce3de6a2e746a8c1e768f632d69d06bfbd93932d102965c9e3f7c37d4a92e30aaeca90567548d7cd572f14aed7a90d6b66097a885a889e6e7416a6aaa2eb442706ff661275753150ba6023cdcbb72767dcfc897b59f546e76d8b38d4c36b2b3eef814cccc1While historically appending the .avdn file extension to encrypted files, recent incidents appear to utilize a random file extension, for example ‘.aCcBdEdaeE’ and ‘.CbbaBABBC’, as can be matched by the regular expression:
.[a-eA-E]{9,10}
A ransom note is dropped onto the victim’s desktop, as well as in directories containing encrypted files, using a filename containing a random prefix, for example, ‘joF8SK_readme_.txt’, as can be matched by the regular expression:
[a-zA-Z0-9]{5,6}_readme_.txt
See other ransomware bulletins here:
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


