


The Cyberint Research Team work round the clock to unearth the latest threats to SMBs and enterprises. They are on top of the latest TTPs and monitor rising threat groups, malwares and trends.
An investigation into a suspicious Facebook Messenger message led to the identification of an active Facebook phishing campaign seemingly resulting in victim accounts being abused by the threat actor to further propagate the phishing lure.
Masquerading as a link to a YouTube video sent from a contact known to the recipient, those that click on the nefarious link are, unbeknownst to them, redirected through multiple websites that first determine if the victim is using a mobile device, presumably as the attack will be less noticeable, before presenting a Facebook phishing page and, after multiple redirects, culminating in the presentation of the legitimate Google Play Store site.
Other than the theft of Facebook credentials, seemingly abused to further the reach of this campaign, the motivations or final objectives of the threat actor remain somewhat vague.
Aside from the potential for some kind of referral-fraud, assuming that the redirection chain passed the victim through websites offering affiliate schemes, it appears unusual for a phishing campaign to not culminate in the victim being returned to the targeted site.
Whilst the phished credentials appear to be used to further propagate the threat, it is not clear if any other data theft or account fraud is occurring within Facebook, especially given that the ‘noise’ generated by sending unsolicited messages to multiple contacts would likely alert the victim to the malicious activity and allow them to secure their accounts soon after compromise.
That being said, a webpage statistics service used by the threat actor provides an indication of the scale of this incident with, as of 1700hrs UTC on 16 October 2020, some 450 thousand page views being recorded.
As such, the impact of this incident appears somewhat severe and therefore our initial findings were promptly shared with Facebook in addition to both Bit.ly and StackPath whose servers were being abused within the redirection chain.
Notably, all three organizations should be commended for their prompt response, taking down offending content and hosts to halt the propagation of this threat that and protect countless other Facebook users.
Commencing with the delivery of a localized lure message via Facebook Messenger from a known contact (Figure 1), a link masquerading as a YouTube video is accompanied with text suggesting that the video “looks like” the recipient and therefore encourages them to view the content.

Figure 1 – Initial Facebook Messenger lures (Hebrew, Greek & English examples)
These lures appear take advantage of Facebook’s Open Graph protocol that allows HTML content with meta and property attributes to manipulate what is displayed in the URL preview. As such, the use of og:title has been set to a localized version of “it look[s] like you” whilst og:image displays the YouTube logo to add a sense of legitimacy to the message. The use of these meta tags were also observed within the redirection chain, potentially providing entry points for other campaigns or targeted platforms (Figure 2).
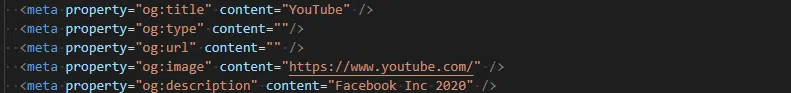
Figure 2 – Example Open Graph Meta Tags
Should the Facebook Messenger recipient be lured into clicking on the fake video link, they are redirected to an initial website outside of Facebook that , in addition to having Open Graph metadata itself, loads a JavaScript that checks the screen width of the victim (Figure 3).
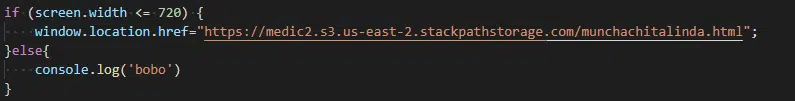
Figure 3 – Determining the victim device based on screen width
Should the screen width be less than 720 pixels, the victim is redirected to the next stage, otherwise the string ‘bobo’ is logged to the console, an action invisible to a standard user, and no further action taken.
Seemingly in preparation for the phishing page, the victim is redirected to a cloud storage bucket with a new object (“Keys”) seemingly being generated for each visit. Content delivered from this bucket once again includes HTML content with Open Graph metadata (Figure 4) and, via an obfuscated JavaScript, displays the Facebook phishing page.
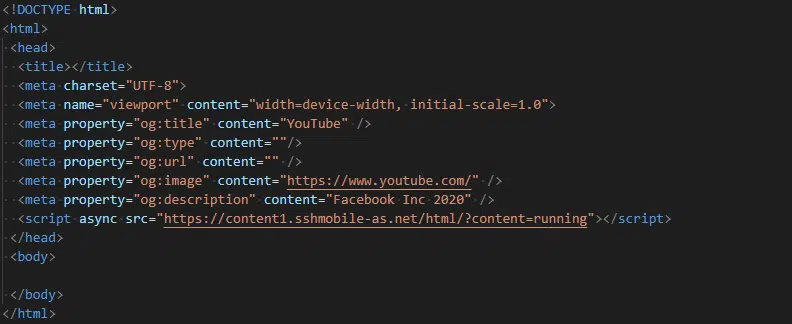
Figure 4 – Redirection to the Facebook phishing page
To deliver a single resource to the victim, the obfuscated JavaScript contains base64-encoded image files and mimics a login page that would be consistent with Facebook when viewed on an Android device (Figure 5).
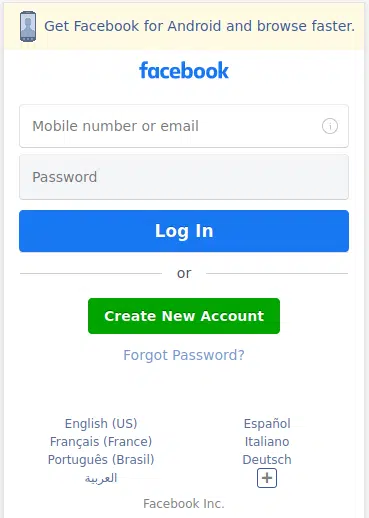
Figure 5 – Facebook phishing page (Note the Android messaging)
Notably at this point, a legitimate third-party tracking service, ‘Whos.Amung.Us’, is loaded and based on their unique identifier, zb6325, their ‘dashboard’ can be accessed to determine the scale of the campaign (Figure 6).
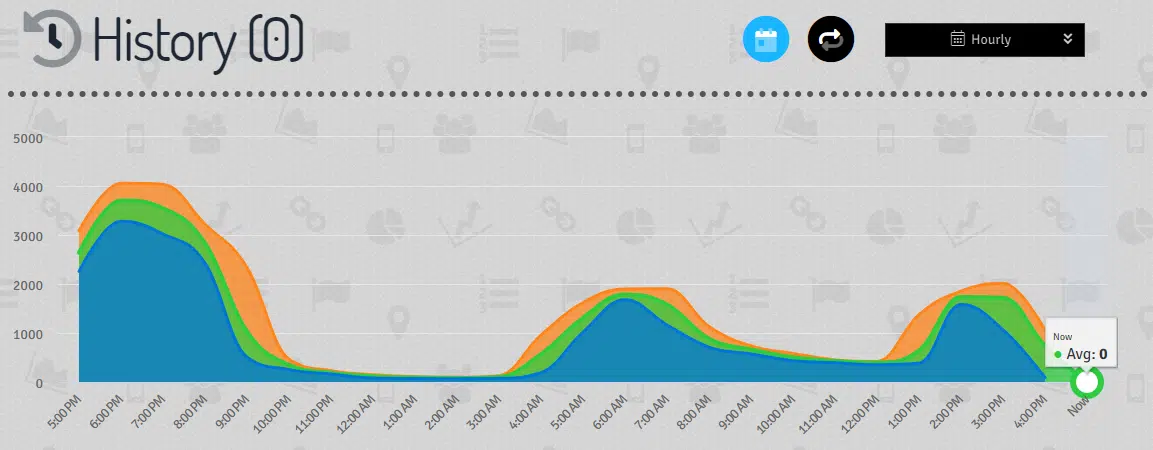
Figure 6 – Potential victim volume (16 October 2020, hourly view)
As can be observed from these statistics, notifying StackPath of the abuse on their platform enabled them to take down the offending cloud storage bucket which resulted in the number of potential victims dropping.
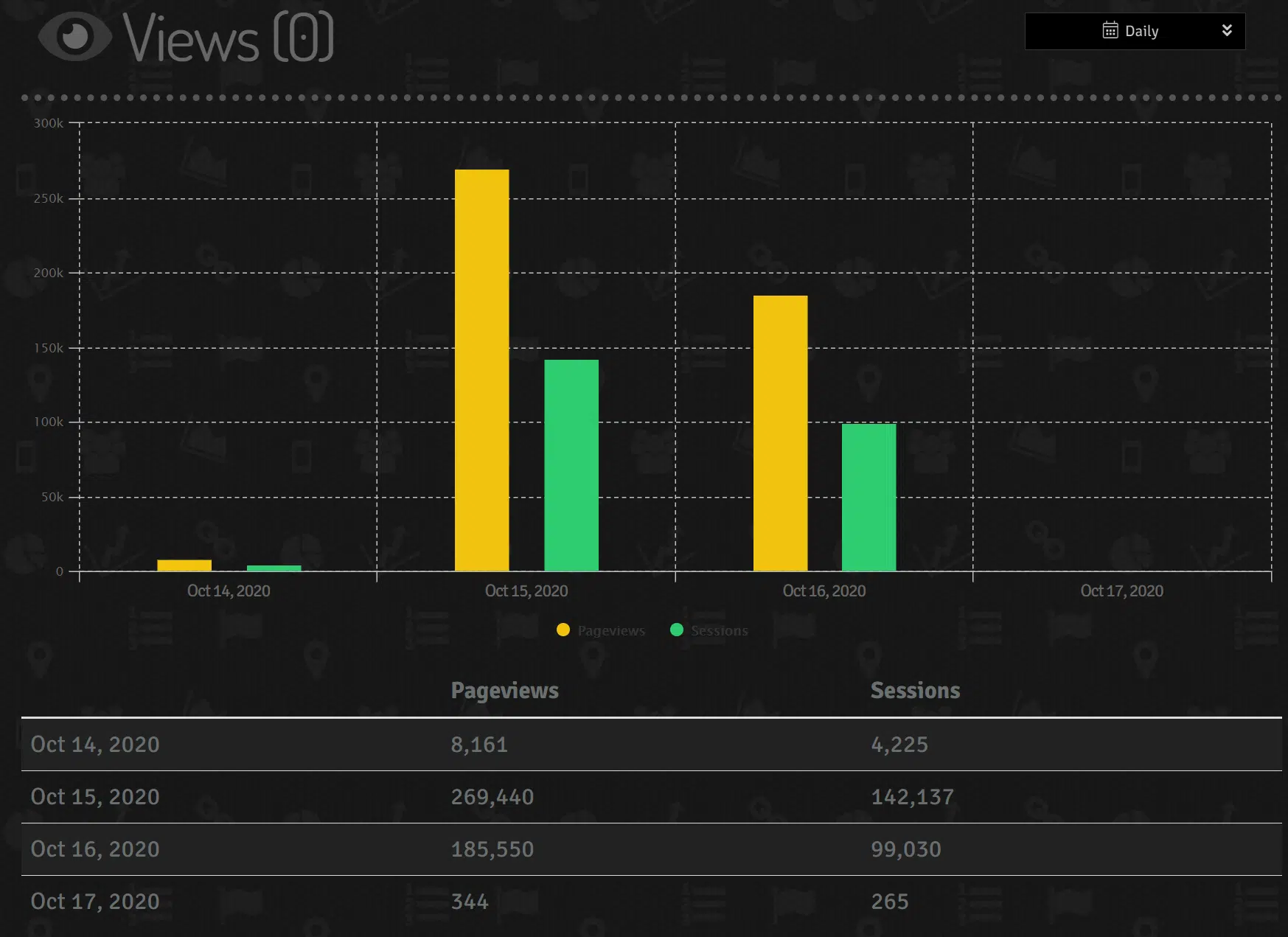
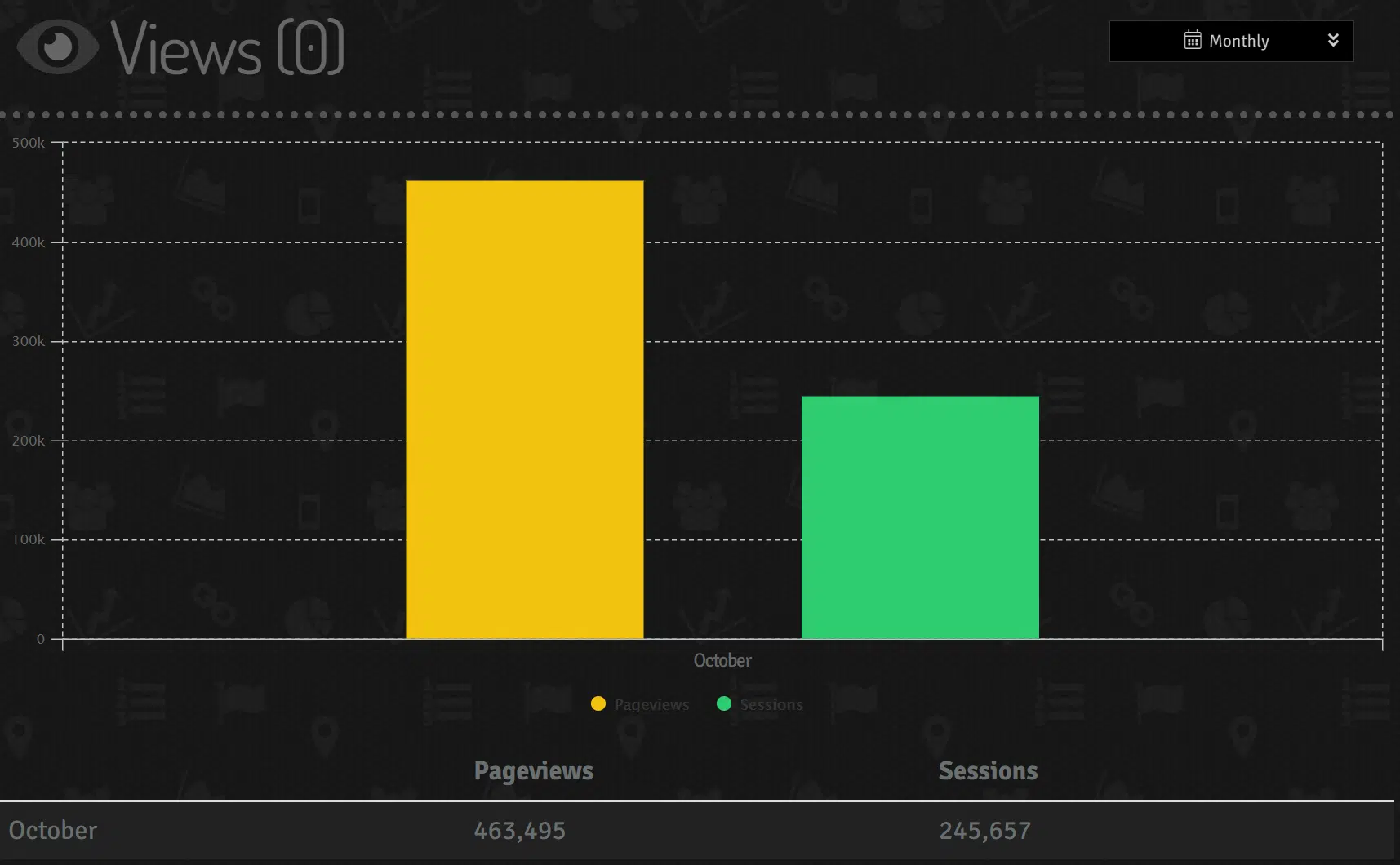
Whilst there are periods of lower activity, likely due to the time zones of those targeted, accessing the ‘views’ section of this dashboard (Figure 7) provides a staggering indication of the number of Facebook users potentially clicking through this campaign with some 245 thousand sessions and 463 thousand page views.
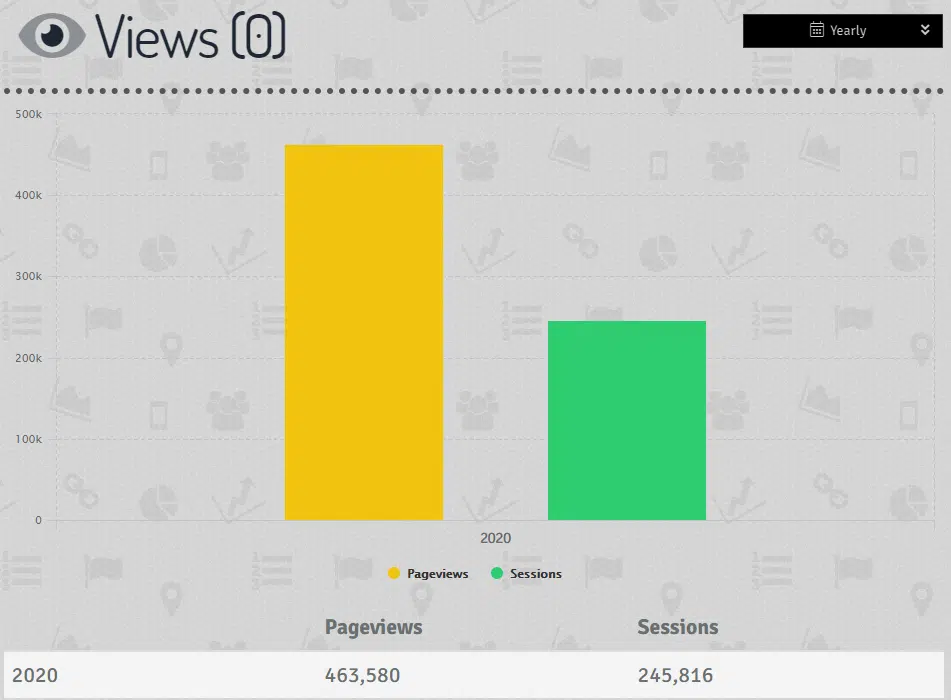
Figure 7 – Recorded pageviews and sessions associated with the campaign
Although it is not possible to determine if these pageviews and sessions resulting in Facebook credentials being phished, the volume of potential victims will undoubtedly result in a significant return for the threat actor.
Those falling for the phishing page and entering their Facebook credentials will find their email address and password being sent via a HTTP POST request in the appropriately named form values email and pass to yet another host, hxxps://secure.sshmobile-as[.]net/iframe.php.
Interestingly, and presumably as an attempt to evade analysis, the obfuscated JavaScript used at this stage appears to attempt to identify if the browser’s development tools are being used (devtools.isOpen) although this could be bypassed and the code both reviewed and deobfuscated.
Having submitted content to the phishing form, be that valid or not, a Bit.ly short link URL was used to redirect the victim to another nefarious domain, potentially allowing the threat actor to gather additional campaign statistics and/or to allow them to reconfigure this stage of the redirection chain without needing to update already deployed JavaScript payloads.
In yet another campaign disruption and takedown effort, Bit.ly were notified of our findings and swiftly acted to remove both the offending short link, replacing it with a warning message, and deactivating the associated account.
Those that were redirected prior to this action would have momentarily seen a ‘loading’ screen (Figure 8) before being redirected yet again to suspicious intermediate websites before arriving at the final destination, the legitimate ‘Google Play’ store.

Figure 8 – Post-phish ‘Loading’ screen
Whilst the true intention of having victims pass through these intermediate websites (Figure 9) cannot be fully determined, visiting them outside of the redirection chain appears to result in potentially pay-per-click revenue generating content being displayed.
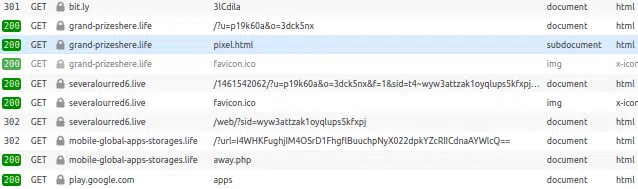
Figure 9 – Redirection chain
Victims finally reaching their unintended final destination, albeit confusingly Google Play rather than a YouTube video consistent with the initial lure, would then, assuming they submitted valid credentials, find their Facebook accounts potentially accessed and abused to further propagate the campaign.
In addition to notifying both StackPath and Bit.ly of the abuse on their services, resulting in swift takedown actions that disrupted this particular campaign, Facebook were also quick to act on our tipoff and remove offending content to protect their users.
By proactively reaching out to the relevant parties, we were able to disrupt and mitigate the attack:
Although those behind this campaign acquired full Facebook account access, abusing new victims to further propagate the malicious link to their contacts via Facebook Messenger, no account takeover activity was observed in a ‘honeypot’ account used during this investigation.
Based on the multiple redirections involved, and the method of distributing the initial lure, it appears that the primary motive for this campaign was to perform some form of click or referral fraud and, therefore, we surmise that the threat actor is exclusively focused on financial gains.
Seemingly by setting up numerous fake pages, likely using automated methods given the consistency in naming, campaigns of this nature may start by delivering some initial lures before the operation grows organically.
As much as Facebook is considered a safe platform, with automated security tools such as link scanning, the ability to share links and content is both the platform’s strong point and weakness. This is especially true when nefarious parties can craft appealing lures by abusing the Open Graph protocol to manipulate URL previews with their own metadata and effectively hide malicious links from users by masquerading as legitimate content.
As such, we would recommend that users of Facebook, and other social media platforms, consider the following:
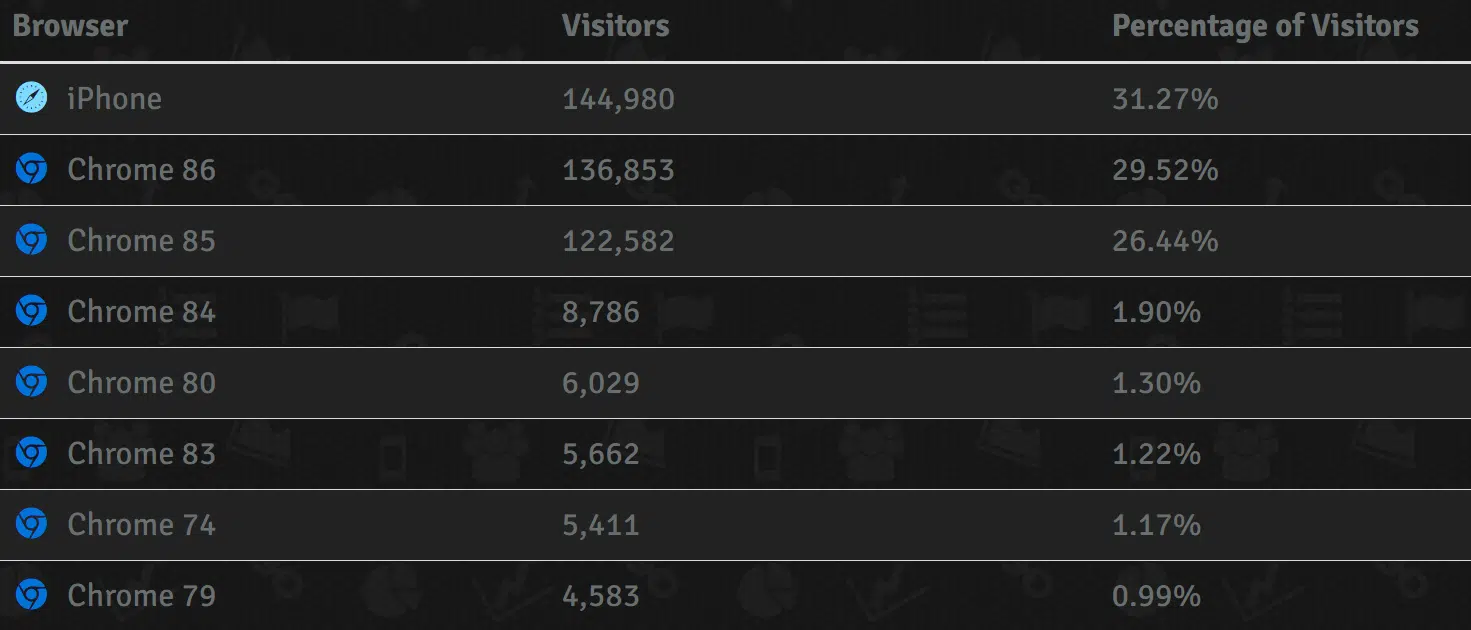
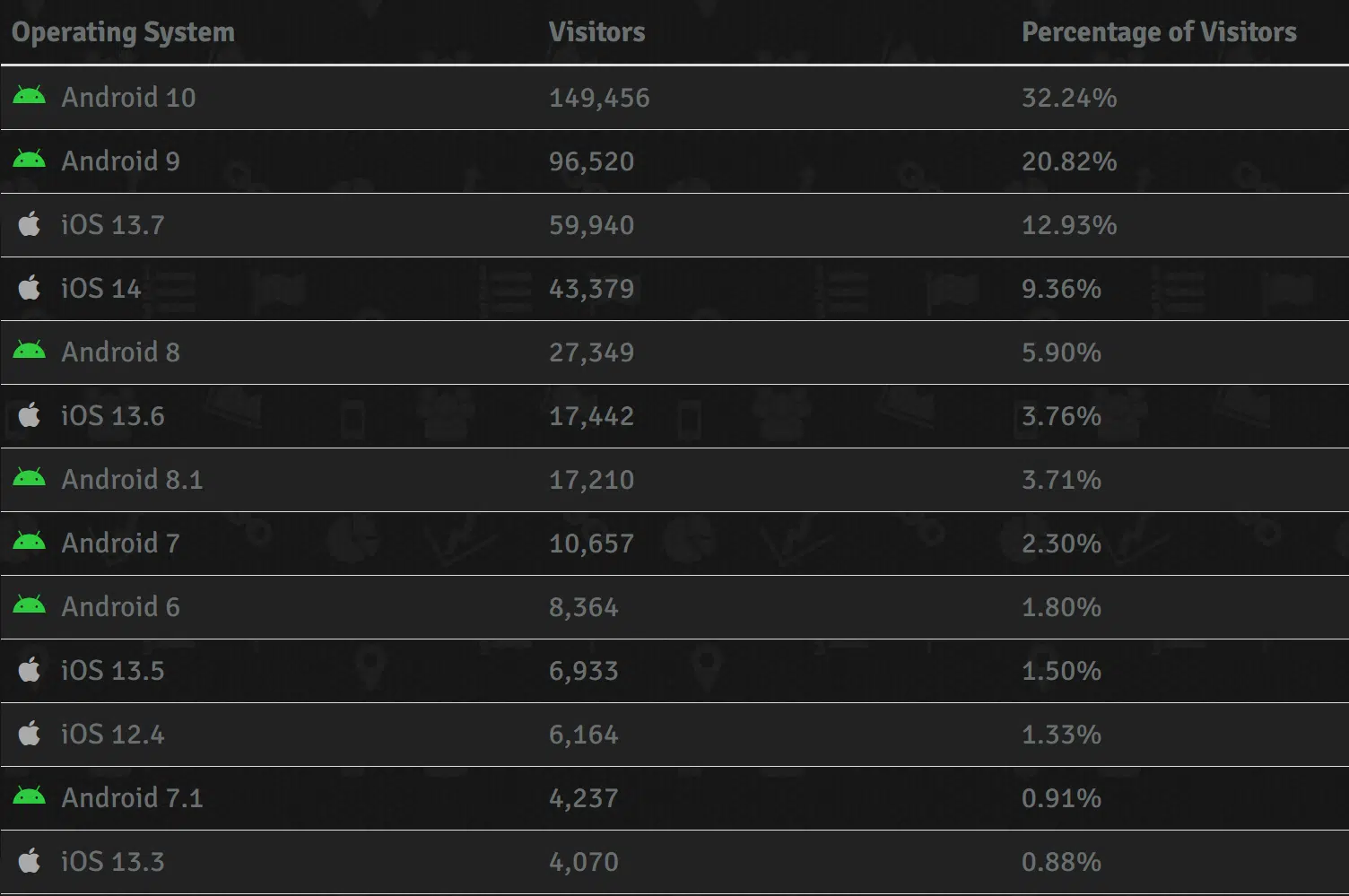
For reference, the following statistics were obtained from the legitimate tracking service during the incident.


The following Facebook pages, since taken down, appear to be related to the delivery of unsolicited messages in recent months and as such, any content originating from them, or similarly structured names, should be ignored:
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


