

Wednesday 15 July 2020 saw the compromise of multiple high-profile Twitter users, including cryptocurrency exchanges, famous individuals and organizations, with their accounts subsequently being abused to Tweet cryptocurrency giveaway scams
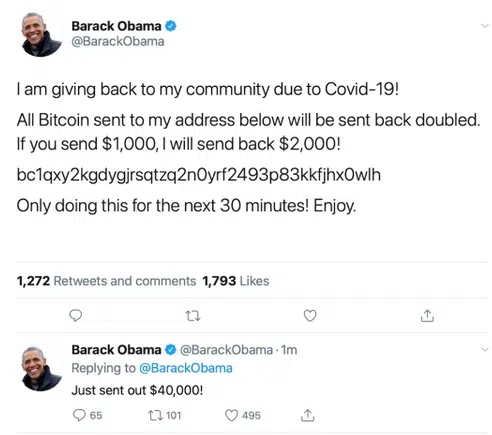
Figure 1 – Cryptocurrency Giveaway Scam via a compromised account
In addition to Tweets directly including a Bitcoin cryptocurrency address, bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh, Tweets containing a link to a now offline website cryptoforhealth[.]com, hosted on a domain registered on the day of the attacks, encouraged victims to make a Bitcoin payment that would be ‘doubled’ and returned (Figure 2).
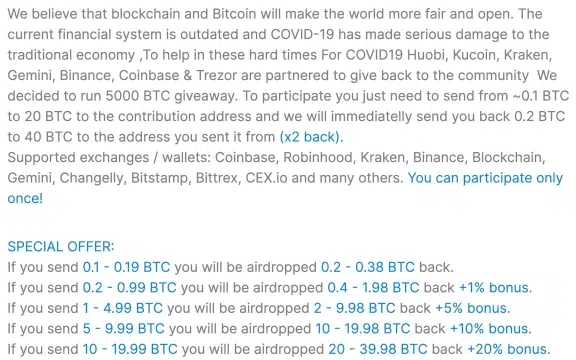
Figure 2 – Scam domain ‘cryptoforhealth[.]com’
As is to be expected in scams of this nature, victims sending Bitcoin to this BTC address will not receive anything in return, reinforcing the age-old adage, “if something is too good to be true, it probably is”.
Whilst the Whois record for the cryptoforhealth[.]com domain is now ‘redacted for privacy’, it was initially registered, seemingly with false registrant data, to an ‘Anthony Elias’:
Registrant Name: anthony elias
Registrant Organization:
Registrant Street: 7528 Logan Street
Registrant City: Vacaville
Registrant State/Province: CA
Registrant Postal Code: 95687
Registrant Country: US
Registrant Phone: +1.3185553332
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: mkeyworth5@gmail.com
Passive DNS indicates that this site was hosted by Cloudflare Inc. (US) with multiple IP addresses, likely part of their content delivery network (CDN), resolving to the domain throughout the day:
Note: Given that these IP addresses are part of Cloudflare’s hosting infrastructure, network activity involving these is not necessarily indicative of a host visiting the scam domain.
Unverified reports also suggest that this domain was being delivered via messaging services (Figure 3), unrelated to Twitter, potentially indicating broader scam activity.
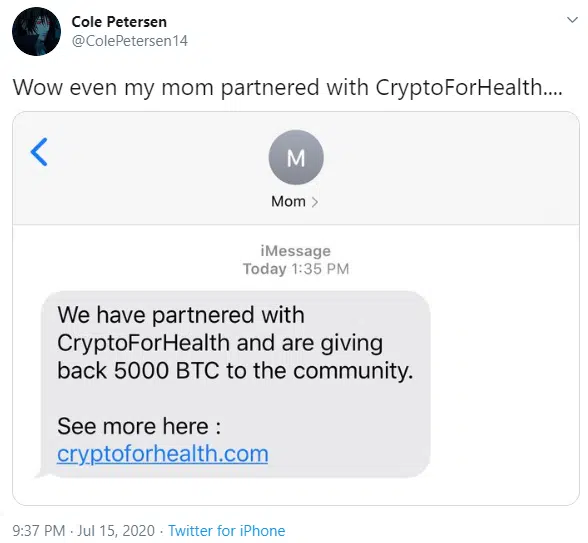
Figure 3 – Potential scam message (Via Twitter @ColePetersen14)
Further utilizing the ‘Crypto For Health’ moniker, an Instagram account seemingly takes responsibility for the incident with a subtle “It was us ” message along with a stylized Twitter logo (Figure 4).

Figure 4 – ‘Crypto For Health’ Instagram account
Based on Tweets posted to Twitter’s official support account, itself subject to abuse during this incident, Twitter are conducting an ongoing internal investigation. They believe that the accounts were compromised following a coordinated social engineering attack against Twitter employees to gain access to internal systems and tools.
Given this, it’s assumed that these systems and tools were abused to gain control of the high-profile accounts and send scam Tweets on their behalf.
Notably, posts made to 4chan, an imageboard website, include screenshots allegedly showing Twitter backend interfaces (Figure 5) although their age and authenticity cannot be determined.
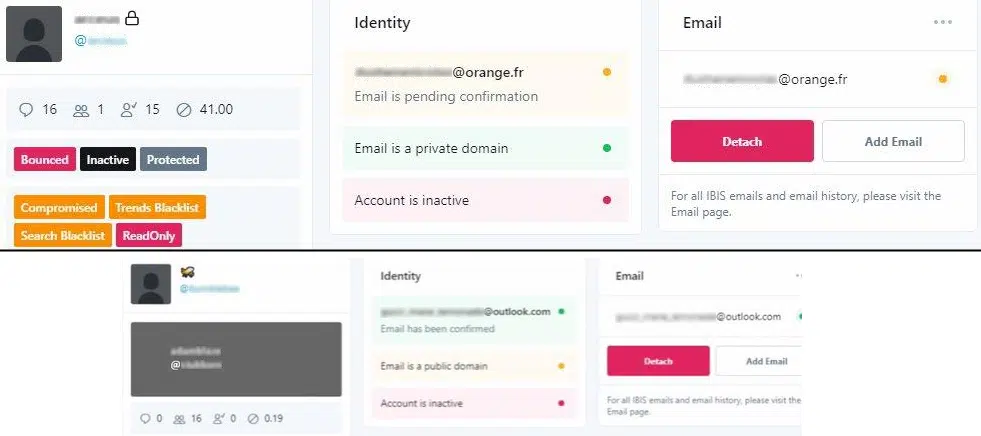
Figure 5 – Alleged Twitter backend screenshots (4chan /g/ – Technology)
Further suggesting that these may be old screenshots, and somewhat unrelated to today’s incident, the ‘follower’ and ‘following’ statistics do not appear to align with the three identifiable Twitter users, one of which currently has a display name and profile picture that is inconsistent with the ‘backend’ (Figure 6).
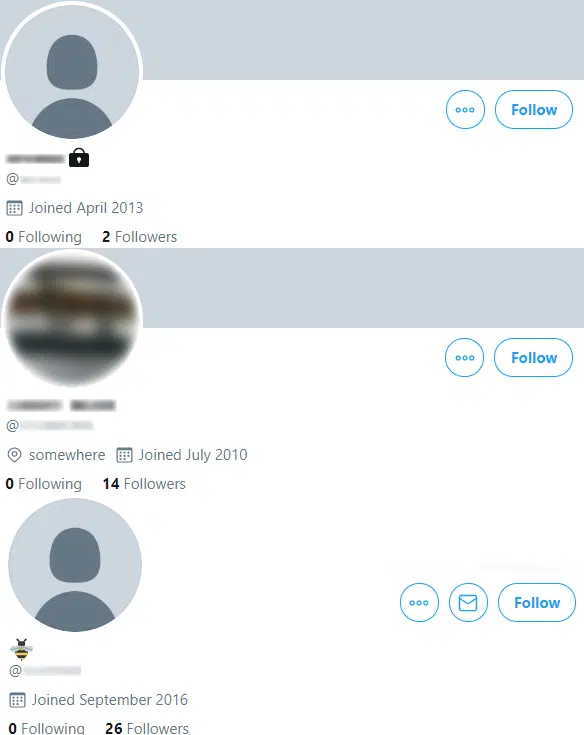
Figure 6 – Twitter profiles identifiable from the ‘backend’ screenshot
Whilst the full extent of this compromise is yet to be determined, with Twitter continuing their investigations and likely to provide updates via their @TwitterSupport [2] account, there is speculation that this could be an insider threat.
Again, whilst uncorroborated, an anonymous post on the 4chan website may provide an insight into Twitter’s investigation (Figure 7).
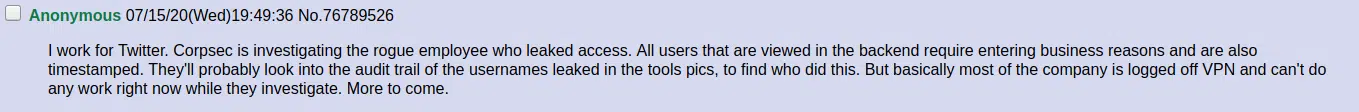
Figure 7 – Alleged ‘rogue employee’ (4chan /g/ – Technology)
Whilst Twitter’s initial response saw them disable the ability for all verified accounts to Tweet, this capability was later restored at 2040hrs EST on Wednesday 15 July.
Consistent with a Twitter backend compromise, and as would be expected from high-profile accounts of this stature, numerous reports confirm that multi-factor authentication was in use by many of the accounts and therefore discounts any theory of individual account takeover.
Based on public reports thus far, the following notable accounts appear to have been abused/compromised:
Based on the transactions associated with the threat actor’s Bitcoin address, some 376 transactions totalling some 12.86BTC [1] were completed between 1900hrs UTC on Wednesday 15 July 2020 and 0805hrs UTC on Thursday 16 July 2020. Current exchange rates suggest that this would equate to US$117,385.
Given the high-number of followers and the social media influence these accounts hold, many of them have been previously impersonated and used in past cryptocurrency giveaway scams.
The question remains as to why a compromise of this apparent scale would be used to launch a relatively low yield cryptocurrency scam and utilize modus operandi that are somewhat more consistent with lower-sophistication threat actors. That being said, these attack motivations may align with the capabilities of an insider that was either complicit in providing access for a third-party, or directly abusing accounts themselves.
Conversely, this same apparent backend access in the hands of a higher-sophistication threat actor could presumably have been used to facilitate intelligence gathering operations against a number of notable individuals or even an attempt at misdirection to hide some other more nefarious activity.
Aside from this access potentially allowing private direct messages to be viewed, leading to potential abuse such as in extortion attempts, a motivated threat actor could have attempted to manipulate an account’s followers by posting subtle Tweets. For example a government official’s account could be abused to influence politics or a prominent business person’s account might be abused to make announcements that influence stock market prices.
Regardless of the threat actor’s motivation and intention, Twitter will likely need to consider how they limit and control employee access to user accounts and take measures to prevent similar incidents from reoccurring.
Although the true extent of this compromise remains unknown until Twitter concludes their investigation, many elements can already serve as a reminder to organizations when considering their own threats and risks.
[1]https://www.blockchain.com/btc/address/bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh
[2] https://twitter.com/TwitterSupport/status/1283518038445223936
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


