


First coming to light as a local elevation of privilege vulnerability affecting pre-release versions of Windows 11 (Figure 1), subsequent investigations into the issue, namely sensitive registry hive files being accessible to all users when ‘System Protection’ is enabled, confirm that it also affects Windows 10.
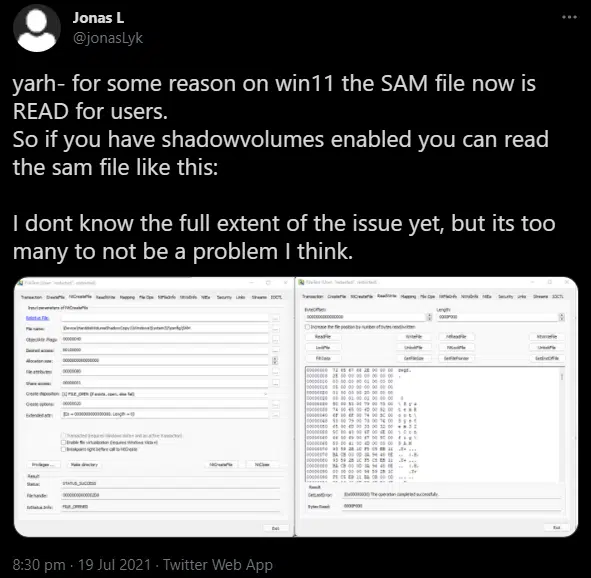
Initially dubbed ‘HiveNightmare’ and ‘SeriousSAM’ by security researchers, CVE-2021-36934 has been assigned to this vulnerability although the CVSS score has yet to be determined.
Whilst there are no reports of this vulnerability being exploited in the wild, proof-of-concept (PoC) code has been released [2] and could allow a threat actor with local access to take advantage of the overly permissive access control list (ACL) rules to acquire sensitive data from the Windows registry.
In response to this vulnerability being publicized, Microsoft have launched an investigation [3] in addition to providing workarounds. It is not yet known if a patch will be released in due course.
Given the wide adoption of Windows 10 and the sensitivity of data stored within the registry, especially the Security Accounts Manager (SAM) registry hive which contains hashed credentials, the severity of this vulnerability is likely to be high.
Whilst requiring the threat actor to have local access to a target machine, this elevation of privilege vulnerability arises from non-administrator accounts, as defined by the BUILTINUsers group, having RX (read and execute) access to the following sensitive registry hive files:
%WINDIR%System32configSAM%WINDIR%System32configSECURITY%WINDIR%System32configSYSTEMIn normal circumstances, and regardless of access privilege, these files would still be inaccessible due to them being locked ‘open’. That being said, the proof-of-concept (PoC) code and attack vector for this vulnerability takes advantage of the Windows ‘System Protection’ feature that allows any user to access a volume shadow copy (VSS) of the system volume and, in turn, gain access to unlocked versions of these sensitive files.
Analysis of currently available PoC code indicates that these registry hives can be accessed from the VSS via the following path (where <FILE> is one of the three registry hive files):
\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\<FILE>Using a script, or specially crafted executable, to read and save this path to file would allow the threat actor to leverage the sensitive information contained within for multiple scenarios, such as:
As a consequence of these scenarios, a threat actor could easily elevate their privileges on the local machine and/or gain access to other devices within the victim network.
According to Microsoft, the following versions of Microsoft Windows are officially recognized as affected:
Based on our own limited testing, and anecdotal reports via Twitter, in practice the affected versions may vary across build numbers and update status, for example, the author’s test installation running Windows 10 20H2 build 19042.1110 did not appear to be vulnerable.
Unexpected access attempts to the volume shadow copy data may be indicative of exploitation, especially in the following instances:
\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SECURITY\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEMicacls %windir%system32config<FILE> Where <FILE> is each of SAM, SECURITY and SYSTEMBUILTINUsers:(I)(RX) appearing in the output.%WINDIR%System32config using the following command:
icacls %WINDIR%System32config . /inheritance:evssadmin delete shadows /for=c:[1] https://twitter.com/jonasLyk/status/1417205166172950531
[2] https://github.com/GossiTheDog/HiveNightmare/
[3] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


