


Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
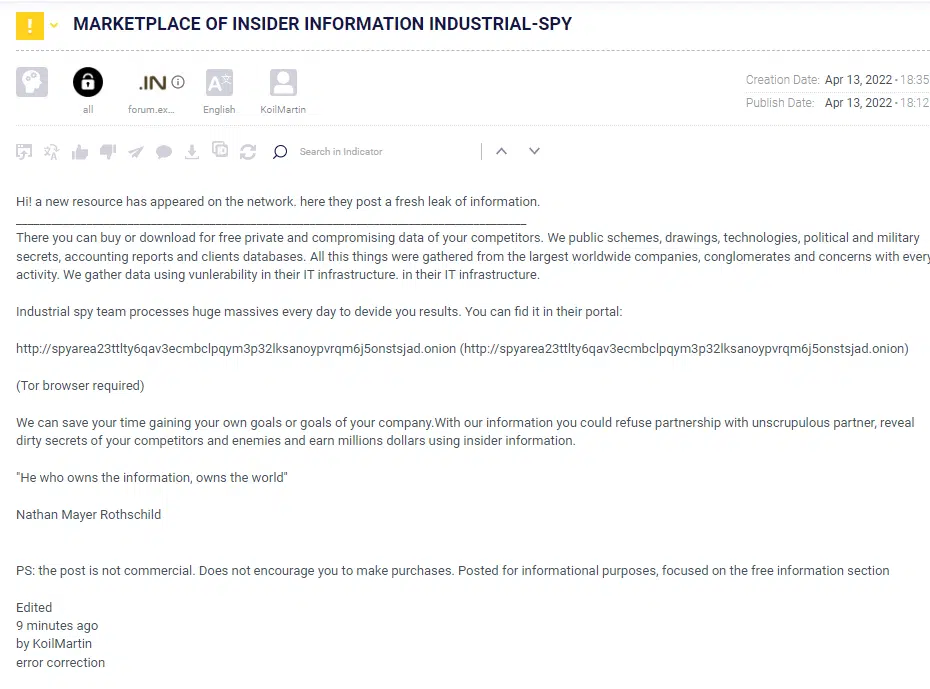
In recent weeks, Cyberint has been monitoring a new marketplace that appeared in the TOR network, an insiders network called Industrial Spy. This new platform was established in around mid-March this year and is currently being promoted on known Darknet forums and Telegram channels.
The platform’s main goal is to become the ultimate repository containing victims’ data, which is mainly gathered by threat actors and insiders. Both threat actors and insiders can financially benefit from the publication of this data. As declared by the operators, they like to create a convenient platform to assist companies comparing or revealing sensitive and confidential data on potential partners or competitors.
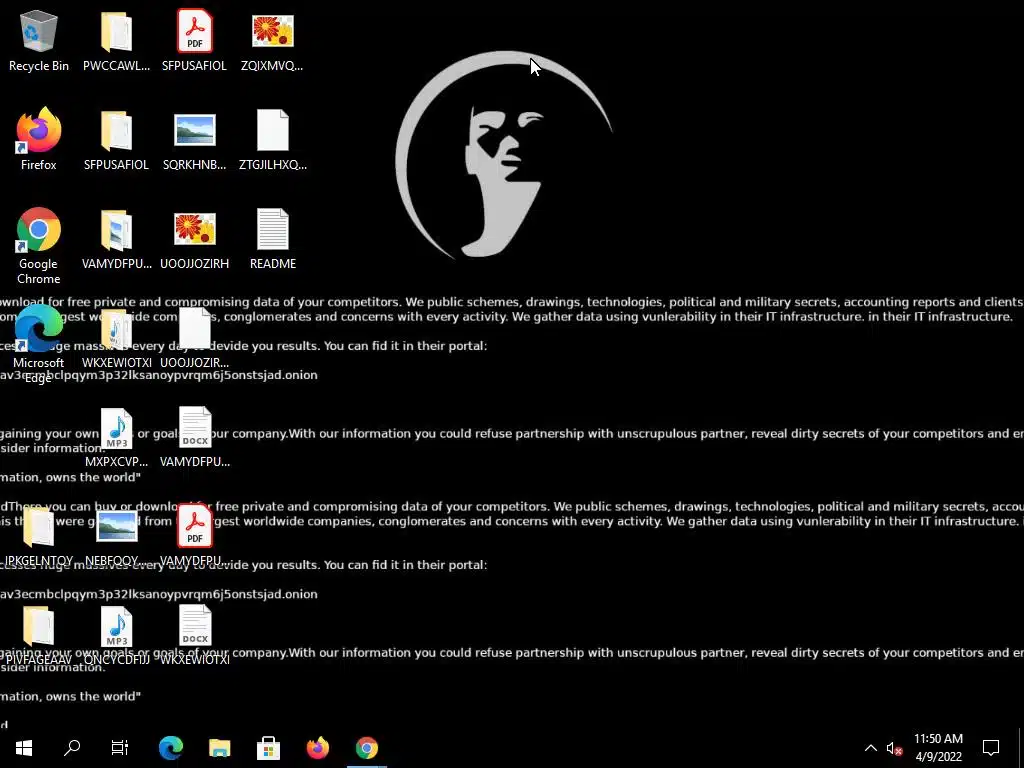
In addition to the promotion throughout the Darknet, the platform has its own organic and unusual way to announce its existence: malware that is dropped onto victims’ computer and generates multiple readme files across desktop folders and operating system, as well as changing the system background theme to Industrial Spy’s logo.
The platform’s marketplace’s unique method of dissemination is divided into three main sections: the Premium Section, where you can exclusively purchase new data; the General Section for specific file and non-exclusive purchasing; and the Free Section, which gives registered users full access to the published data.
As of this publication, the marketplace is down and is not accessible. At its last online activity, there were nearly 30 companies published on the platform, from SMBs to Large 1B+ organizations, the last two victims of the premium Section were priced at $400K and $750K (approximately 10-20BTC).
In order to understand if the Industrial Spy operators are a new cyber-criminal group with unique TTPs, including a marketplace or a premium reseller that collaborates with the big names, we will examine multiple layers of attributions and similarity comparisons to arrive at a verdict on this new competitor.
As the platform mainly presents itself as insiders\competitors data marketplace, the first question that comes to mind when you encounter this kind of platform is how common the insider threat is. How is it even possible that in such short amount of time the platform enrolled around 30 companies to the platform? We need to take a deep dive into the data presented on the platform and analyze its attributes in order to determine its integrity.
We will examine the data in four different layers:
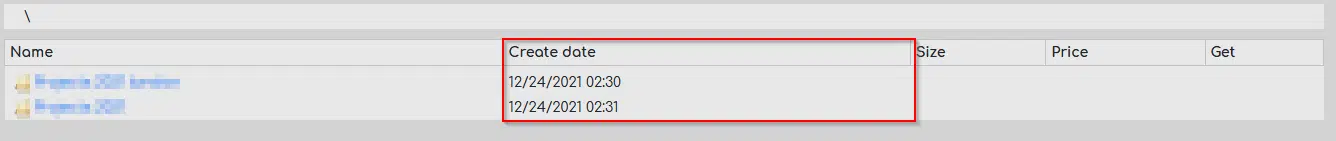
Cyberint ran analysis on the abovementioned victims list and noticed that 20% of the victims were already targeted or were declared as having been targeted by a ransomware group, mainly by a specific one – Conti. All of the recycled data can be found under the Free Section, and was dated as late 2021.
The reason for recycling the data may vary and may be speculative. It is likely to create an impression of an active marketplace until the group obtains its unique data. A couple of weeks ago one of the recent premium section victims announced that they were victim to a serious cyber-attack, which indicates that the premium section data is relatively new and valuable.
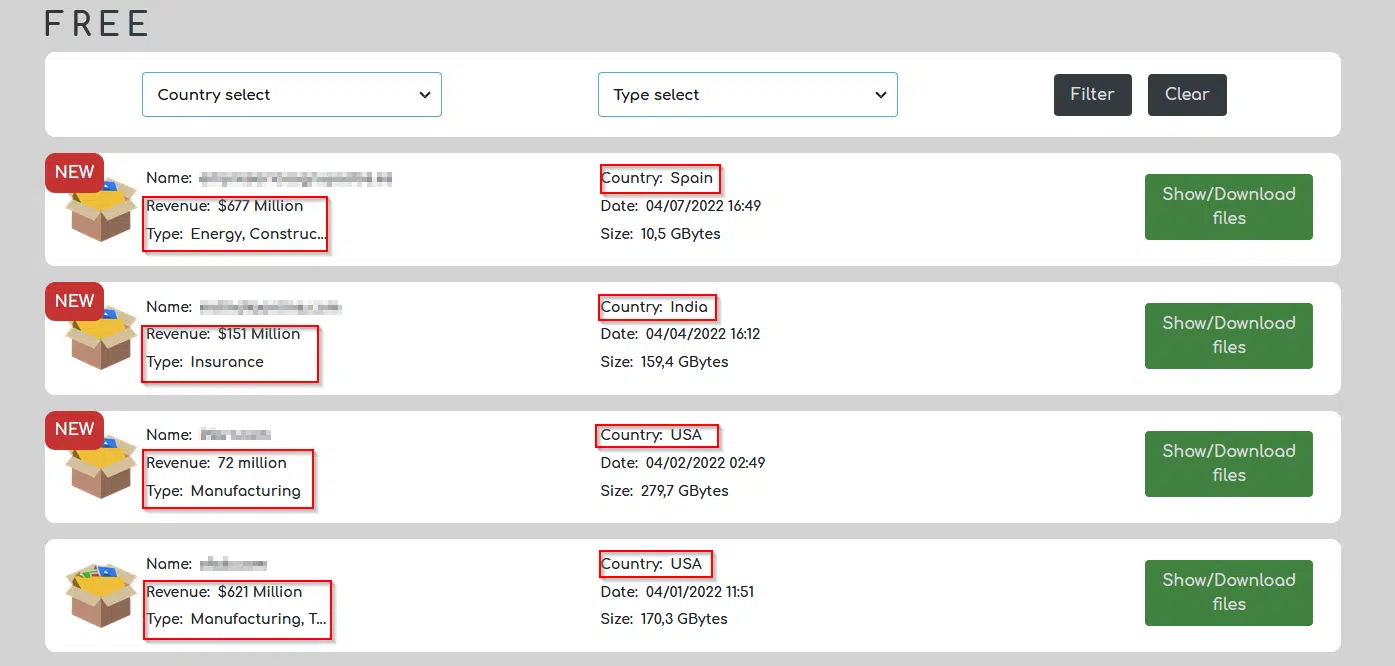
The vast majority of targets are mainly from the US and western Europe (80%); few victims are from Asia and South America. Similar to ransomware groups’ victims, there is no specific victim profile. The victims vary widely both in revenue and industry, from software and medical companies to manufacturing and insurance companies.
This profile is highly similar to the known Eastern European ransomware group targets.
As the ransomware portfolio keeps evolving, groups keeps rebranding and deploy an attack is becoming simpler. These days, threat actors are stepping up their game to gain reputation and followers. They enhance their methods of advertising their marketplaces by posting all over the network and deploying channels on various platforms.
In order to let the marketplace gain reputation and traffic, good PR is needed. Some of the best PR can be found in one of the most familiar forums, ExploitIN.
As seen above in Figure 1, the KoilMartin user published a post on April 13 in the notorious forum elaborating the main goal of the marketplace and how to access it. In addition, a publication post was shared in another known forum. Although this kind of post should create noise, present the new game changer platform and make the insider threat accessible, it did not attract much traffic or comments.
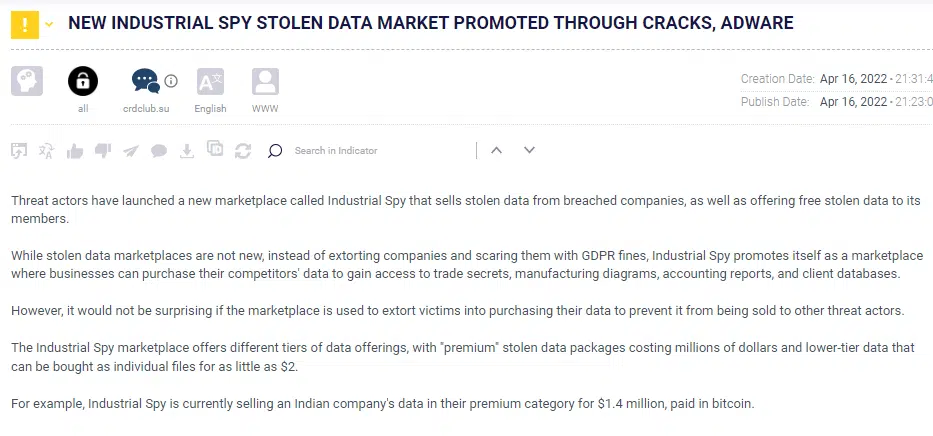
We observed a new method of promotion. Operators have started using malware executables, ads and cracks in order to spread the word, a very uncommon way to gain traffic. Let’s examine the executable from a high-level perspective.
The executable, named “tools.exe”, was uploaded multiple times to VirusTotal and received a maliciousness score of 50/69.
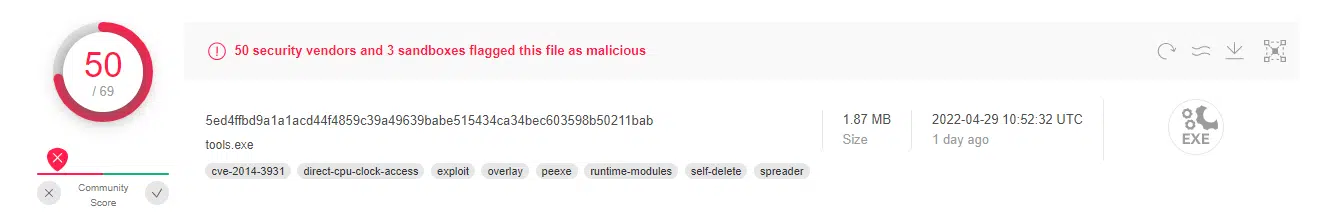
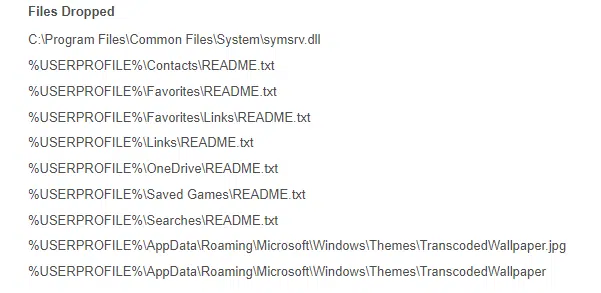
The executable was dropped from known malwares and stealers. It creates multiple readme files with Industrial Spy generic advertisements, and changes the desktop background Industrial Spy’s logo:

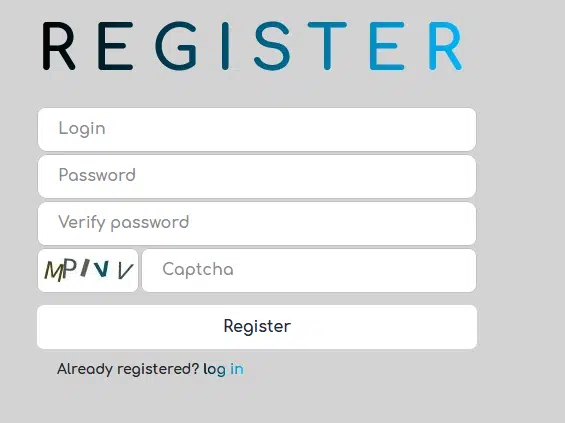
First, the threat actor implements an easy-to-handle platform, without any exhausting Captchas or any notorious multi-stage questionnaires. Instead, there is a very simple registration process, an easily solvable Captcha, and you’re in. It doesn’t get any easier.
After completing the registration process, the main page is revealed. On top of the main page there is a navigation bar, which contains multiple tabs:
This seems quite unique in comparison to other groups’ websites; the data is organized differently to what were are used to seeing in underground websites and data marketplaces.

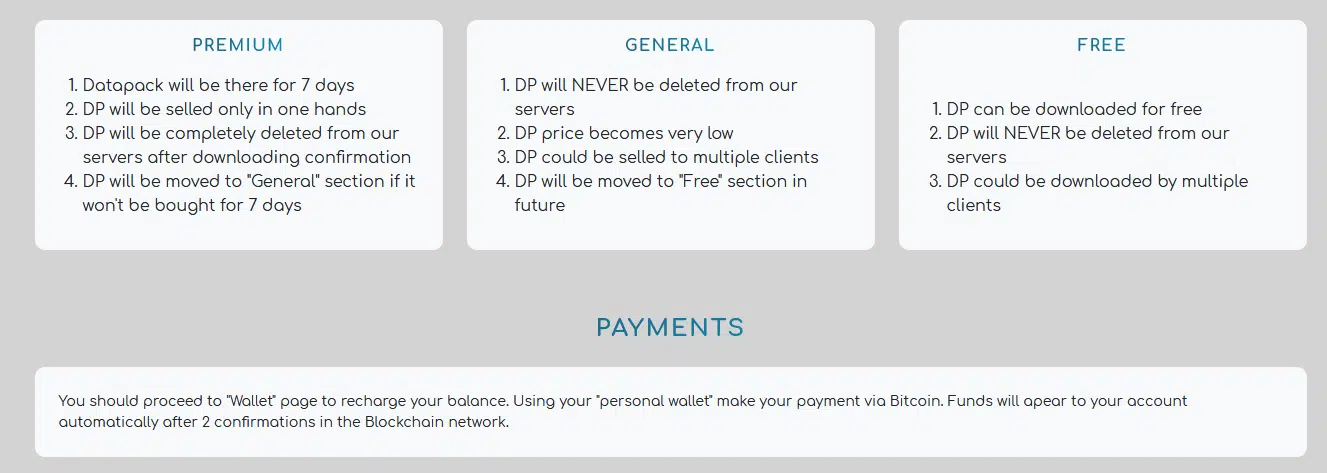
The marketplace operators elaborate how it all works in the Home tab. It is quite interesting. The new-comers are first offered in the exclusive Premium Section. After 7-days in the section, if a buyer does not appear, the data will be transferred to the General Section, and, finally, the data will be stored in the Free Section.
As presented in the marketplace, there are three main data sections:
Premium Section – New victims’ data is first offered via a 7-day, single-buyer, exclusive purchase method.
General Section – Files are transferred to the General Section if the 7-day premium offering was not successful. In the General Section, one can purchase files as individuals at a much lower price.
Free Section – Files that had been in the General Section long enough or did not provide much value to the operators, are added to the Free Section. They will never be removed from the servers, and can be downloaded freely.
As mentioned, the Premium Tab contains exclusive victim data for sale, however, you can explore the directory list without accessing the actual files in order to get a sense of the data’s value without asking for samples, etc. This makes it more convenient both for the seller and the potential buyer.
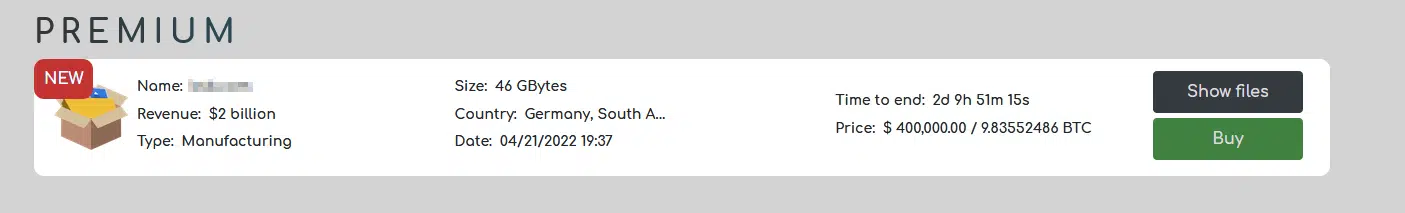
In all three section, each listing contains general information about the victim:
To enhance to user-experience in comparison to other data markets, the operators implemented a new feature for each section – a filtering option allowing one to sort and filter the data by country and industry.
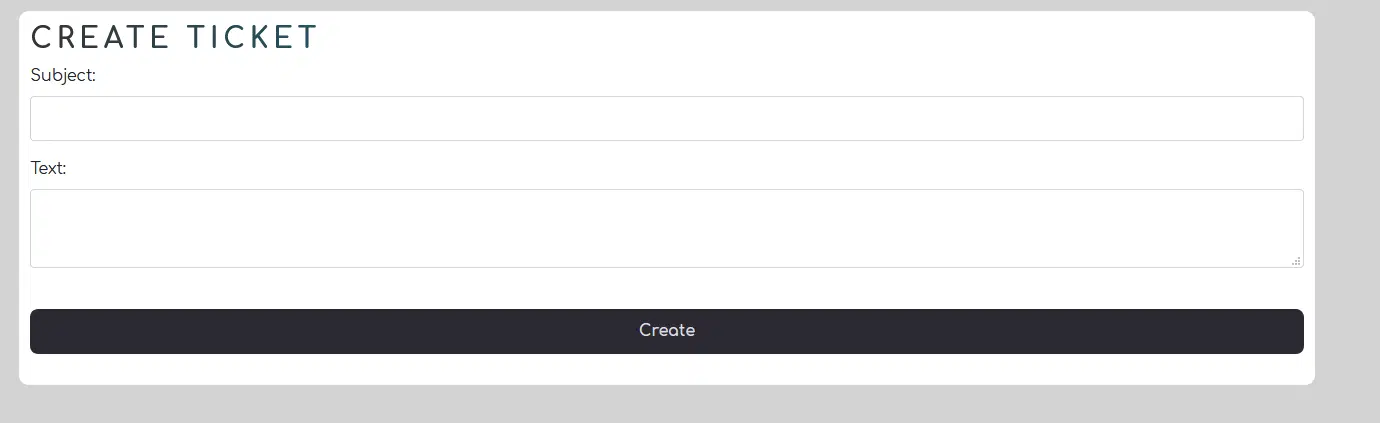
Throughout the entire process, we wondered how one can propose new victim data to the operators, as well as how commission works in the business logic.
A registered user can “Open a ticket” and contact the administrators directly for any kind of request. To date, we have not witnessed any other alternatives for communicating with the administrators about dedicated issues, besides the general request in the platform. It seems that all communication is based on top of the platform.
Allows you to maintain your account, change your password, charge the account wallet with funds and view the current balance.
Although this is not the first marketplace we’ve witnessed in the data selling domain, it is the most unique in its data offering. The known equation of “data equals money” plays a major part in this marketplace – if the revenue of the company is high and the leak is good quality, a threat actor could earn a high amount of BTC in exchange for the data.
The platform is accessible through the Darknet in the same way as other threat groups share victims’ data. This group also maintains a Telegram channel and Twitter account, which points to their publicity efforts.
Similar to ransomware groups’ victims, there is no specific victim profile. The victims vary widely, from software and medical companies to manufacturing and insurance companies.
Currently, the platform is down but we should not eulogize it yet, as we all know that threat actors may take a moment to reorganize themselves and return stronger.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start
