

Highly motivated, problem solver, dot connector, energetic multi-dimensional & professional management with commercially oriented, customer service skills & PMO abilities in high-growth, fast-paced organizations.
A day after Cyberint published this report, law authorities announced that they had arrested a 16-year-old Oxford teen, on suspicion of being the leader of the LAPSUS$ gang. Six other teenagers are also suspected to be members of the gang.
2022 saw several significant and historical cases in the ransomware industry, new players were introduced and some already have caused major damage to top-of-the-line organizations around the world.
Although LAPSUS$ commenced its operations in December 2021, they have made its greatest impact in 2022, compromising major organizations such as NVIDIA, Vodafone, Samsung Microsoft, LG and Okta.
The LAPSUS$ group keeps things simple and has some unique characteristics, whether it’s their leak channel, the way to choose the victims, and due to the lack of knowledge sharing from the victim’s perspective – their TTPs and initial infection methods.
In addition, the big question is, is the group’s operation might come to an end anytime soon and can we compare them to the big game hunters?
On February 28, LAPSUS$ shared an announcement on their Telegram group that NVIDIA was hacked, the official announcement shared that the group gained access to NVIDIA’s infrastructure for a week; initially performed privilege escalation (i.e. admin permissions) to gain access to the most sensitive data, right after that the group exfiltrated 1TB of information including schematics, drivers, firmware, SDKs, documentation and Fast Logic Controller (Falcon).
At this point, there is no evidence of ransomware activity being deployed on NVIDIA’s systems.
After the data exfiltration, LAPSUS$ left instructions note for NVIDIA to contact them back, which they did.
A couple of hours after the first announcement, the group’s reputation started to take off, NVIDIA was just the beginning.
One hour after the announcement, LASPSUS$ started to release the first part (18.9GB) of the internal source code, silicon designs, driver certificates, infrastructure of Falcon and the LHR (Lite Hash Rate technology that put strict limits on the mining performance of select GPUs), which later, the group uploaded to an AWS server, that later on was taken down.
However, it did not stop there, the group’s unique way of delivering the leakage and communicating with the subscribers, helped with the distribution process – subscribers uploaded the leaks to multiple sources and shared the links along the thread, the files are not going to disappear anytime soon.
Two hours after the announcement, additional demand from LAPSUS$ posted on their telegram channel.
LAPSUS$ demanded to remove all limitations on “30 series” (i.e. GeForce 30 series), otherwise- they will leak the NVIDIA Hardware repository with the excuse of helping the gaming and mining community.
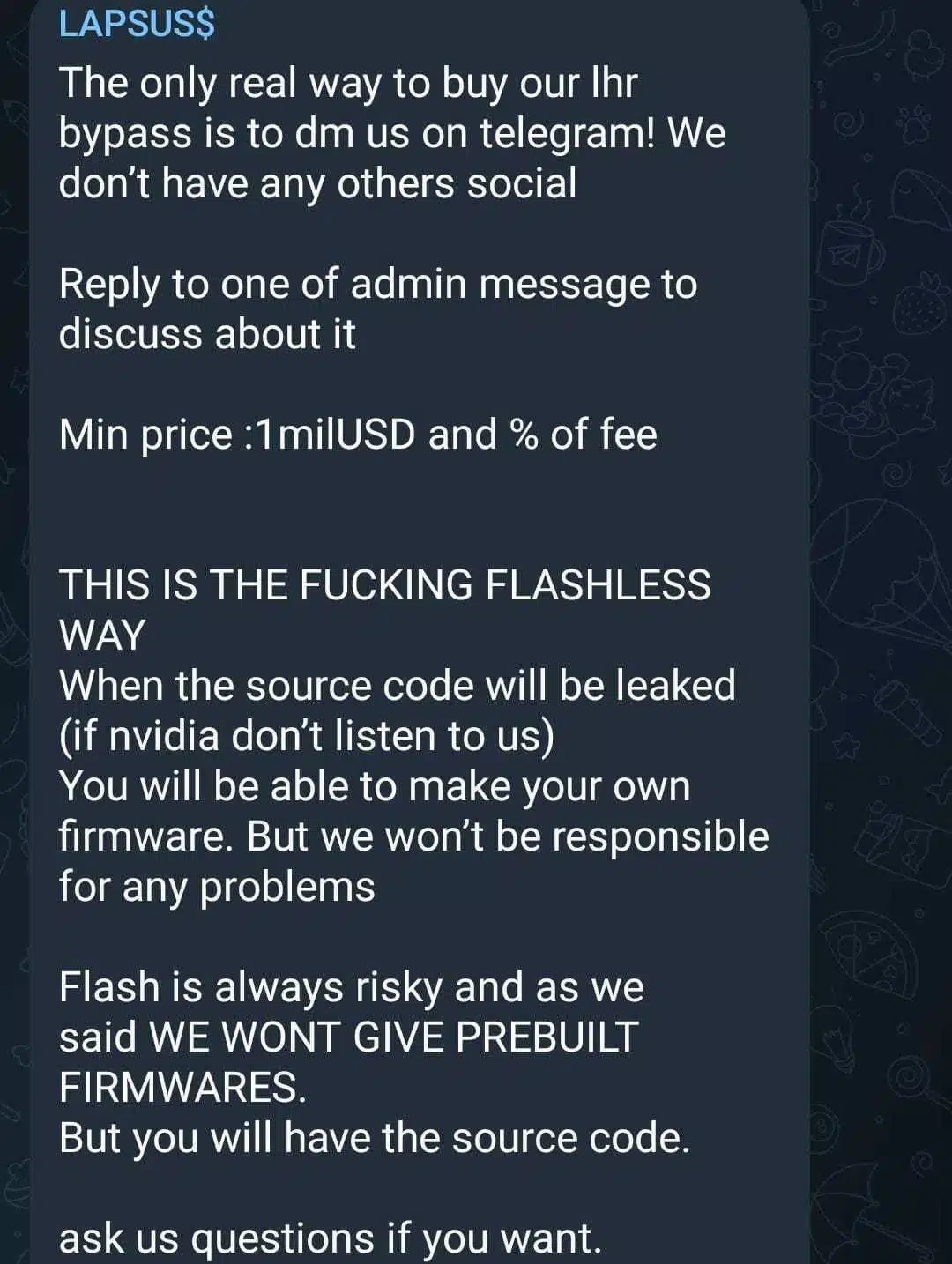
The subscribers noticed that something is missing – the LHR bypass and they asked for clarifications from the gang, which announced that they will not share the bypass anytime soon due to the fact that it might harm the GPU. However, on March 2, LAPSUS$ offered the LHR bypass data for sale – the price? 1M$ and a fee (Figure 1). Money comes first.
On March 1, the group announced the fourth demand, and perhaps the major one:
NVIDIA should commit to fully open-source their GPU Drivers for Windows, MacOS and Linux, which Nvidia did not follow and initiated a move of their own.
Aware of the breach from February 23th, Nvidia didn’t confirm if it was LAPSUS$ who breached their networks and exfiltrated data but approved that the threat actor took employee credentials and some Nvidia proprietary information from their systems and begun leaking it online.
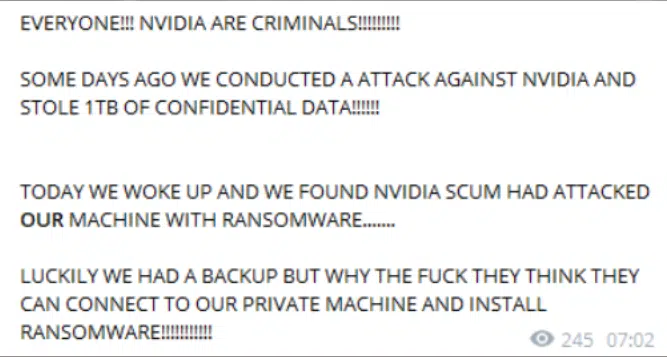
A few days later, LAPSUS$ shared an uncommon message, which they claim to be targeted back by ironically, a ransomware attack, possibly to mitigate the damage that can be done by the leaked data. Apparently, LAPSUS$ created a backup with the stolen data which disrupted Nvidia’s efforts.
It’s currently unclear if NVIDIA succeeded to encrypt their own data. Regardless of the result, taking this kind of significant action may introduce us to new tactics when handling ransomware or data leakage attack.
Given that, one month passed from the first NVIDIA leak and still no sign of whether the remaining data will see daylight, It is still possible that Nvidia’s counterattack was successful.
Meanwhile, other large-scale corporations’ data has been exfiltrated and exposed by LAPSUS$ team.
To date, Cyberint detected a minimum of 130 instances of malicious files signed by the leaked NVIDIA certificate, in several cases we have witnessed known stealers, such as Agent Tesla, taking advantage using this attribute.
The certificate infringing method seems to be spreading as more and more malicious executables are signed with NVIDIA’s certificate.
Shortly after leaking NVIDIA’s data, another major announcement was published by the group in their Telegram channel. On March 4th, an additional international company was introduced to the victims list — this time releasing data purportedly stolen from Samsung Electronics.
The leaked files size was 401GB and available via torrent. The leak is divided into two main sections – Samsung Online Services and Samsung Devices/Hardware data.
The sensitive Device/Hardware leaked data contains the source code for every trusted applet – including DRM modules and Keymaster/Gatekeeper, algorithms for all biometric unlock operation, including low-level sensor code, bootloader source code for all recent Samsung devices (including Knox), and confidential source code from Qualcomm.
In the Online Services section, LAPSUS$ shared Samsung activation server source code in addition to Samsung Accounts Full Source code – including Authentication, Identity, API, Services etc.
Samsung TrustZone (Knox) is the secure premise of Samsung devices, if the TrustZone is compromised, a threat actor could access the TrustZone environment and into the device’s sensitive data.
As the Telegram channel continues to grow and add subscribers, the group seems to be in-love with the PR they are getting and concurrently continue working on the upcoming victims data.
On March 7th, LAPSUS$ posted a poll in their Telegram channel followed by the topic – “What should we leak next?” (Figure 3), more compromised victims is now in the pipeline as Vodafone, Impersa (attacked by the group on January 2022) and MercadoLibre (“unauthorized access” was identified on the company’s source code potentially impacting approximately 300,000 company’s users) are up next.
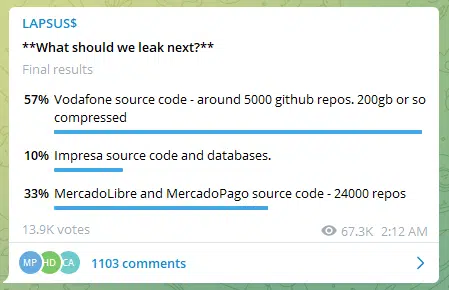
The poll was available for six days and gained almost 14k votes, 57% of the votes pointed to the next victim – Vodafone.
whilst the notorious team claims to have stolen approximately 200 GB of source code files, allegedly contained in 5,000 GitHub repositories, Vodafone announced on launching an investigation.
Recap to Mid-February, Vodafone Portugal suffered a major cyberattack that caused service outages in the country, media reported the temporary disruption of 4G/5G communications and television services. While the identify of the threat actors responsible for the Vodafone attack is unclear, it is possible that due to the time frame of all three incidents, this was the initial foothold of LAPSUS$.
On March 22nd, the group continued their quest to astonish the cyber security world, announcing three major corporations suffering new breaches.
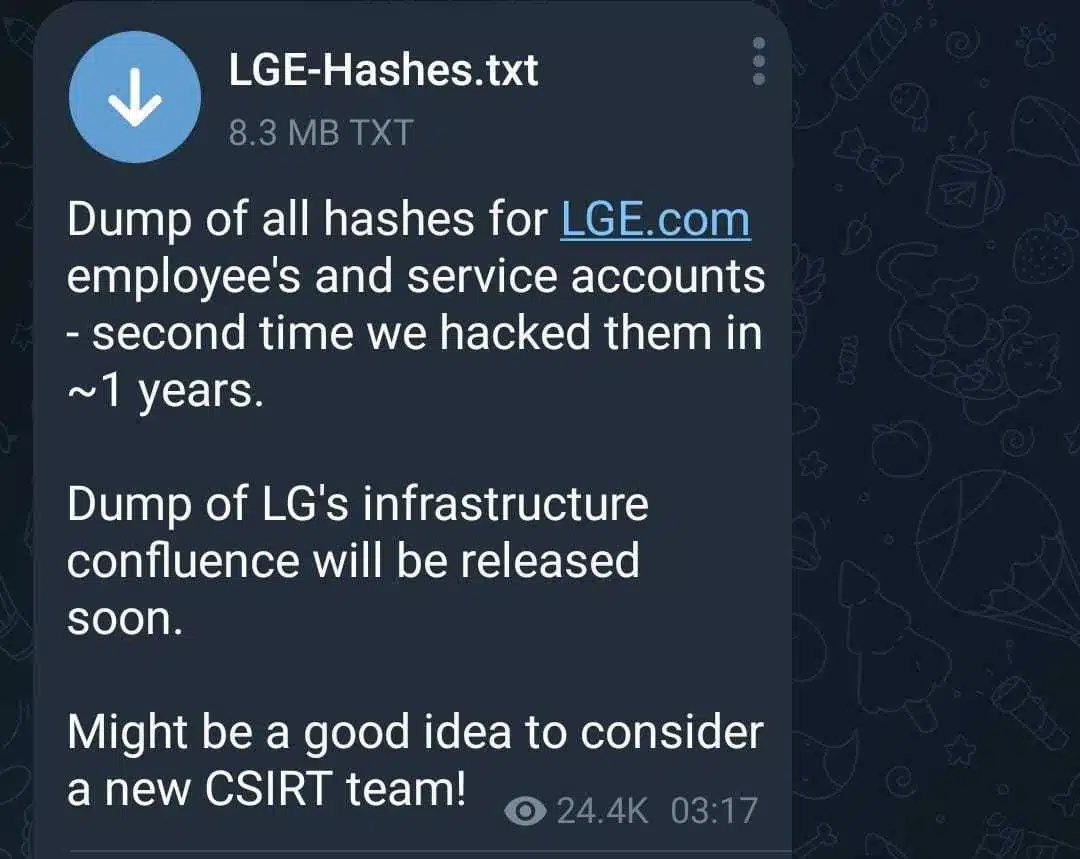
The first major leak is LGE – the group claims to have dumps of employee’s and services account hashes, admittingly, for the second time this year.
The group attached a 8.3MB TXT file which includes all of the data. If that wasn’t severe enough – the group shared that they got LG’s infrastructure confluence and it will be releases soon.
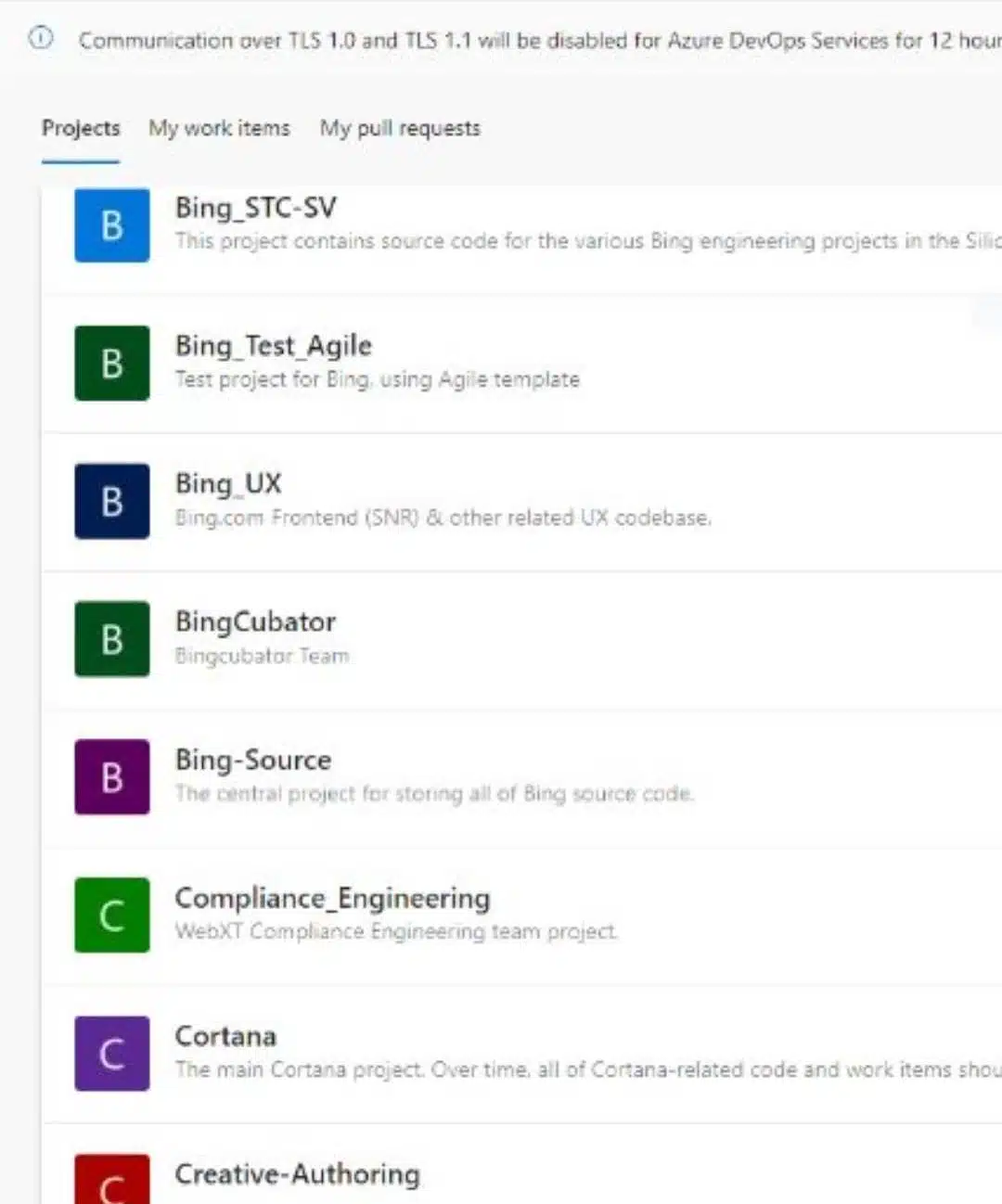
The second major leak of the day is Microsoft’s leak – it all started on March 20th as the group shared a screenshot of multiple repositories which includes Bing and Cortana Projects alongside additional internal projects (Figure 5). shortly after, the post was removed by the admins and a message “Deleted for now will repost later” appeared instead. PR machine works once again.
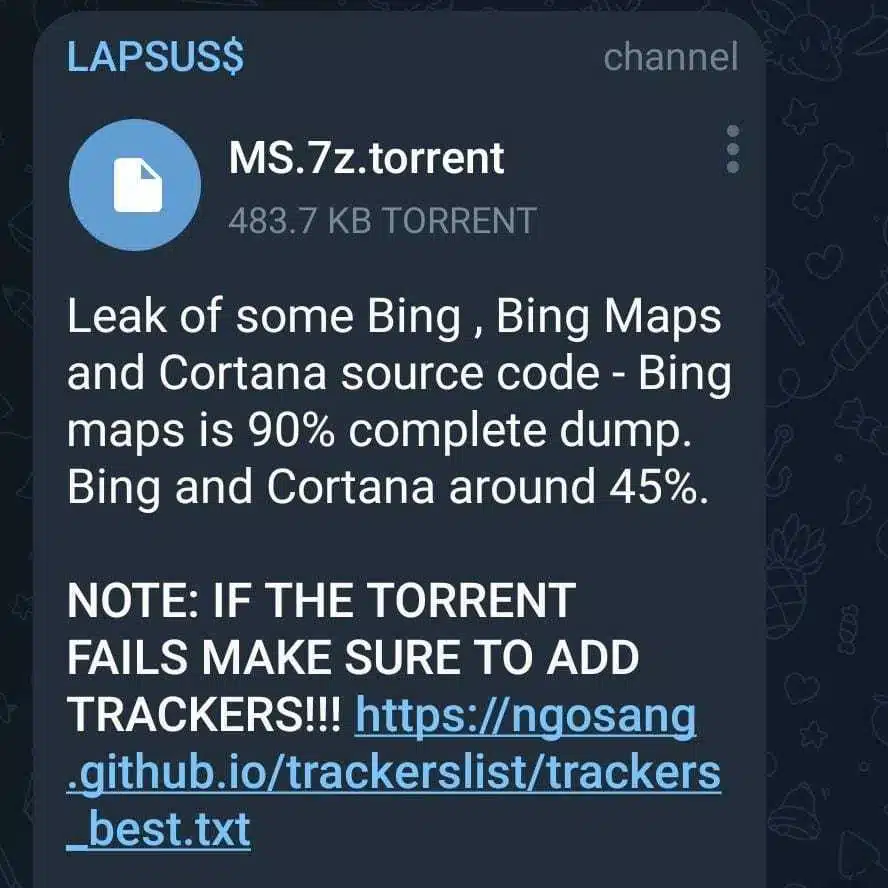
As mentioned, the group officially shared a torrent download with a description that the file contains 90% of Bing Maps and 45% of Cortana and Bing (Figure 6).
However, this leak does not seems to be the subscriber’s cup of tea as they demand more of NVIDIA and Samsung-type leaks.
A new message appeared on the group’s Telegram channel, indicating, what appears to be the “biggest” most influencing breach yet. Why breach single companies, never mind their size, such as Nvidia and Samsung when we can reach them all?
While Identity and access management services and Single-Sign-On (SSO) are both highly common these days, breaching the “center” of it, could lead to more than just one single victim.
The Okta breach, indicates a new level of thinking, allowing the group to access all of Okta’s customer list.
Looking at the screenshots published, we see that the dates on these go back two months (Figure 7), indicating the information and havoc LAPSUS$ could have already made.
LAPSUS$ openly answer and acknowledge this, as seen in figure 8.
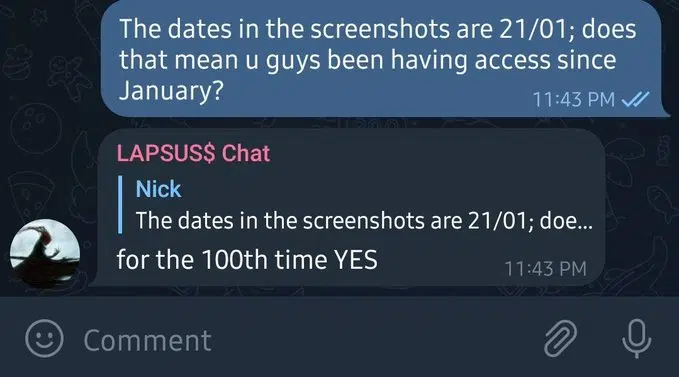
The initial message claims that “BEFORE PEOPLE START ASKING: WE DID NOT ACCESS/STEAL ANY DATABASES FROM OKTA – our focus was ONLY on okta customers”, which shows that Okta is not the target here, only a means to an end.
This breach can also shed some light on the recent (and future) leaks LAPSUS$ publish. This might be the “way in”, in most, if not all, of the recent breaches.
The immediate question here, is why burn down their bridge? Given that this is such a strategic breach, why publish the Okta breach? One assumption is that the breach got fixed, and LAPSUS$ lost their access, which led them to brag about the breach two months after the initial access.
On March 23rd, Okta’s Chief Security Officer, David Bradbury, shared the following statements:
In the first statement, Bradbury shared an unsuccessful attempt to compromise an account of a customer support engineer working for a third-party provider.
On top of that, Bradbury sheds light on the incident, revealing that there was a five-day window between January 16th-21st, where an attacker had access to a support engineer’s laptop.
Bradbury approved that the leaked screenshots provided by LAPSUS$ are related to this incident and elaborates on the limited access of support engineers who are unable to create or delete users or download customer databases. In addition, support engineers do have access to limited data – for example, Jira tickets and lists of users – that were seen in the screenshots.
At the moment, Okta continues its investigation and contacts all the allegedly affected customers and claims that the service is fully operational while announcing that only 2.5% of Okta’s customers were impacted by this breach, and already contacted by the company.
Due to the limited information provided in the screenshots, we assume that the access and valuable data LAPSUS$ obtained was limited, as the group’s mentality is to shame and blame and if they were possessing any valuable information they would sell or brag about it.
It didn’t take too long for LAPSUS$ to respond. A few hours after the first announcement, they wrote an elaborated message, opened with “I do enjoy the lies given by Okta” (Figure 9).
In their response, the group mainly tries to contradict Okta’s announcement, with no great success.
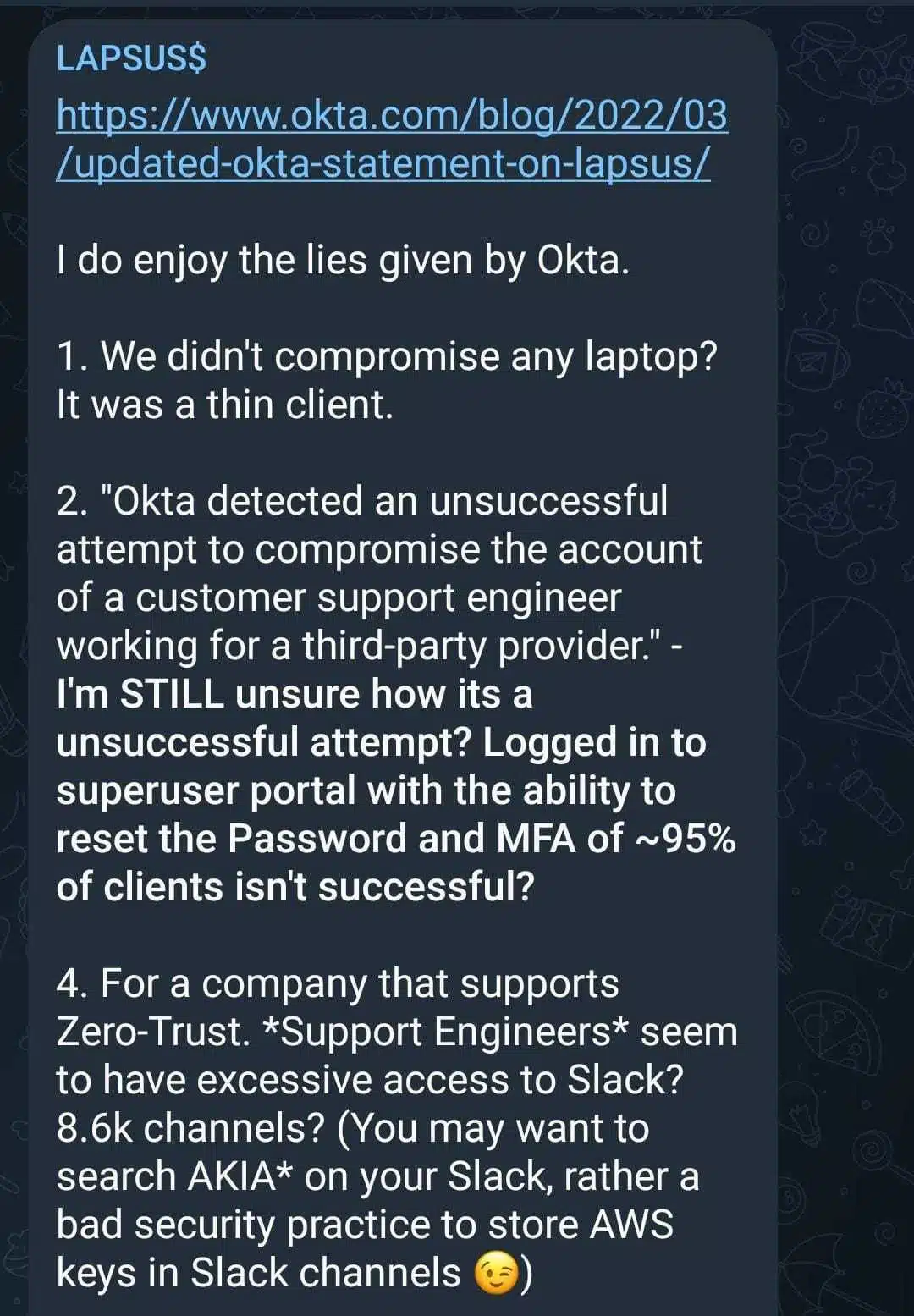
Regarding the support engineers’ limited access, the group commented that those limited access engineers had excessive access to Slack (about 8.6k channels) and those channels contained plaintext AWS keys. As AWS keys value depends on the permissions they grant, and since Lapsus$ describes these as “excessive”, we can only guess the magnitude of these. Obviously, Lapsus$ gang members should poses AWS knowledge to take advantage of these. Since Okta’s statement does not mention any AWS keys rotation, this makes us wonder if we will continue hearing about Okta in the next upcoming weeks.
It is quite notable that LAPSUS$ didn’t achieve their main goal via Oktas’ breach, through defensive-posture shaming posts without any clear evidence or goal. Also, the way they embedded internal insights into Okta’s team, perhaps reflects the potential impact of the breach.
Once again, the need to brag and to answer for every announcement Okta’s have made indicates of the immaturity of the leaders and their will to “show off” and to have legitimization in the cyber security community.
When it comes to the technical sophistication and professional maturity of the group, it seems that the group has gained a massive amount of followers due to their success, but they haven’t worked to expand the group itself.
Most of their campaigns are based on insider threats and no evidence of recruiting vulnerability researchers, reverses, and top-of-the-line developers were found. once they gain an employee creds, they still need some level of understanding of how to move and what to look for once they are inside the network.
The only adjustment the group made as a result of the growth of followers, was the migration of announcements to English from Portuguese.
LAPSUS$ keeps its methods simple at the moment and most of their work is done manually, including analyzing their findings and publishing the leaked data. We have witnessed several cases in which the group delayed publications of leaked data and chose almost amateur working methods.
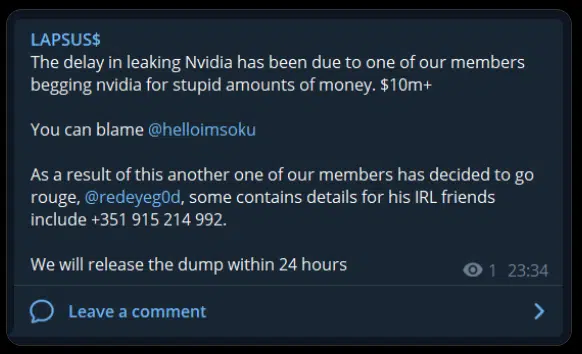
The group’s lack of sophistication and maturity is also seen in their temper the take-backs of their announcements, changing their demands and blaming each other in their Telegram channel for mistakes (Figure 10).
As most ransomware groups are using Onion-based blogs to upload the extorted data, LAPSUS$ mainly uses Torrent and AWS services to share the data and users re-upload the data into other storage services creating a distribution of the data on multiple sources.
To date, the dedicated LAPSUS$ Telegram group contains 43K subscribers.
While most groups communicate with their communities often in a one-sided relationship in which the group decides who is the next victim, LAPSUS$ chose a way for their audience to participate in the group’s strategy and in the decision making.
The first way is another Telegram channel in which their followers can talk to the group’s members and give them ideas, tips and talk to each other. The second, and more interesting way, is the group’s polls. The group chooses three compromised victims and give the followers the ability to choose which one will be leaked.
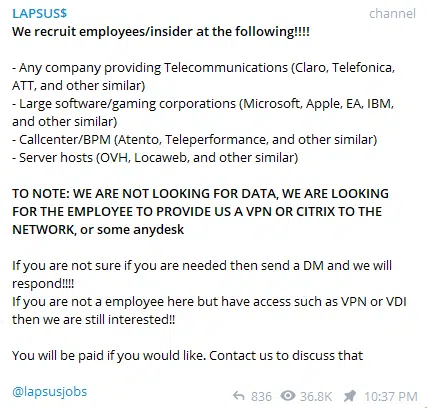
Currently, LAPSUS$ is not known for having very sophisticated techniques they implement when it comes to initial infection and gaining a foothold within the victim’s network. As the group is not well funded nor fully organized at the moment and lacks talented people that have the ability to exploit vulnerabilities and research for zero-days, they address the easiest way to gain a foothold, which is the insider threat.
The most simple yet lethal technique involves bribing and recruiting employees of potential victims that will intentionally compromise their credentials and help LAPSUS gain a foothold.
Although this technique is not new or unique to LAPSUS, as Lockbit2.0 is also known for doing so, it is very efficient as we saw in their last campaigns.
LAPSUS has published a recruitment message in their Telegram channel calling all employees that can provide them remote access to join the group (Figure 11).
Cyberint’s Research team actively monitors the gang’s activity and Telegram channel, LAPSUS is mainly targeting Telecommunication and large software/gaming companies.
As the group gained popularity, it also draw the attention of the cyber security community and in the process to understand the group better, some crucial details might have been compromised that affects the team’s activity.
Evidence shows a relationship between the Doxbin website and LAPSUS$. It seems that one of Doxbin’s former admin is currently one of LAPSUS leaders.
Doxbin is a document-sharing website that suffered a major breach in January. While the active admin has blamed the former one, an official Tweet was released with contacting information to the user sigmaphoned on Telegram (Figure 12).
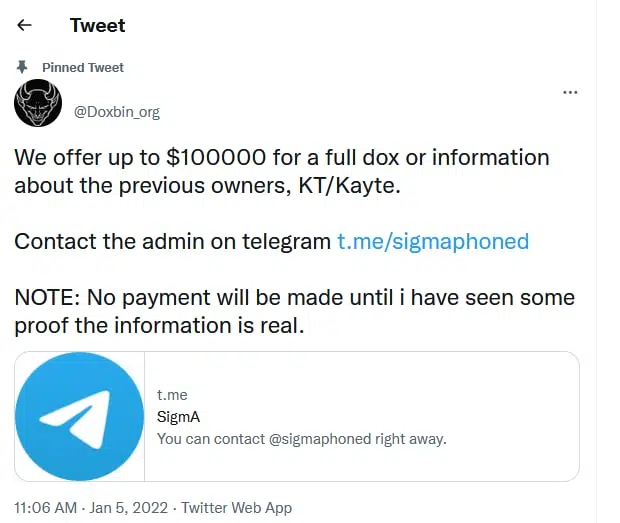
Looking at the Telegram channel of the group following this event, a new account was added as the admin’s new account – sigmaphoned (Figure 13).
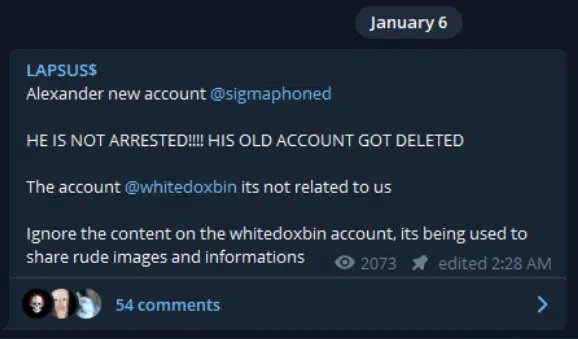
While the group suspiciously insists the other account,@whitedoxbin, is not related to them, also draw attention to this account. When looking at the Doxbin leaks for the relevant account, we are able to find the information of a certain individual in his teenage years, based in London, UK, that is suspected to be LAPSUS$ leader.
Chatters found regarding this individual indicate that law enforcements are currently on the pursuit of this individual that fled the UK, and at the moment is off-grid.
The claim that LAPSUS is but a group of teenagers or young adults aligns with many behavior patterns we have seen of the group.
After Okta’s incident, it seems that LAPSUS$ has drawn a lot of heat. Some speculations suggest that several Law enforcements entities including the FBI are currently in pursuit of the leaders.
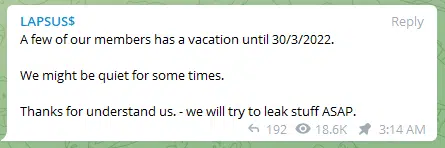
One of LAPSUS$’s last announcements is that some of the members are going to take a vacation of a week and that they might be “quiet for some times” (Figure 14).
LAPSUS is a unique group for many reasons and although they are responsible for several big-scale campaigns such as Nvidia, Ubisoft, Samsung, and more, their methods are not too sophisticated and their management techniques and logistics of the group are very poor.
There is a big question mark regarding if the group continues to exist, given the allegedly leaked identity of the leader which will make things very hard to improve and expand the group’s activities and personal.
LAPSUS$ success in these major organizations leads us to understand that given basic knowledge in security, with a single insider threat, any organization, specifically supply chain organizations, regardless of the security measures, is vulnerable.
Also, we can learn that attacking these targets might be easier for threat actors given the massive amount of employees they hire – more employees, more inside threat potential, more strategic damage for the organization.
Although Okta’s announcement doesn’t leave a lot of room to worry, given the gravity of this case, we would like to suggest additional security measures that might help mitigate and identify any potentially compromised accounts within Okta’s customers.
user.account.reset_passworduser.mfa.factor.updatesystem.mfa.factor.deactivateuser.mfa.attempt_bypassuser.session.impersonation.initiate©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


