


Over the last few weeks, Cyberint has witnessed an ongoing attack campaign targeting social media influencers, attempting to infect them with malware by impersonating large clothing retailers. The campaign targets influencers across multiple social media platforms but currently appears to mostly focus on influencers operating on YouTube. Further, although the infection process is not sophisticated, it is notable and appears to be evolving.
The recent campaign impersonates large retailers and reaches out to social media influencers via email, regarding a collaboration to promote the brand. As part of the partnership, the influencers are offered a product for their choosing which they can redeem by downloading a “catalog”. The claimed value of the product changes from brand to brand but is mostly between $1,000 and $3,000 USD.
The end-goal of the threat actor is currently unknown, but Cyberint’s assessment is that their intention is to take control over the influencers’ social media accounts, and then either demand a ransom, or leverage the accounts for additional phishing purposes.

Figure 1: “Promotions” sent to influencers
While attack campaigns targeting social media influencers have been seen in the past[1], there are several unique characteristics in this attack worth mentioning:
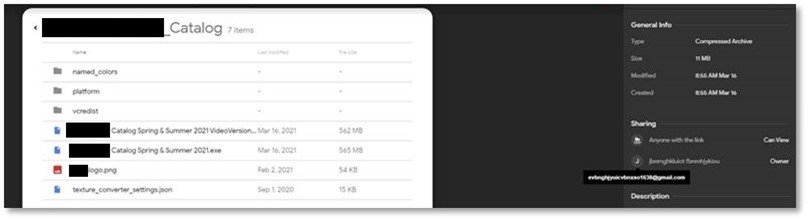
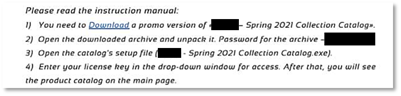
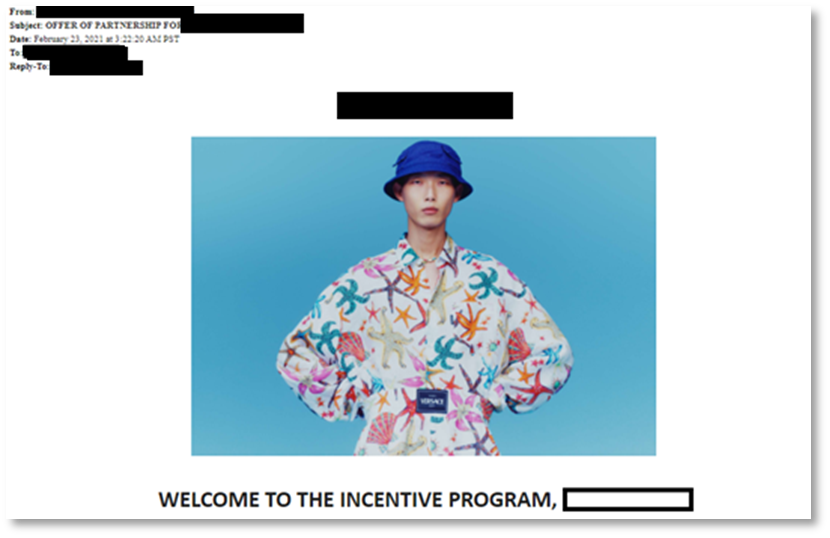
Figure 4: Email sent to a targeted influencer
As the campaign does not target the companies but rather independent influencers, mitigation options are limited. Nevertheless, Cyberint recommends considering operating a dedicated brand ambassador or influencer outreach program to share the following key points:
[1] https://techmonitor.ai/techonology/cybersecurity/instagram-ransom-attacks
[2] https://www.zscaler.com/blogs/security-research/latest-version-amadey-introduces-screen-capturing-and-pushes-remcos-rat
[3] https://otx.alienvault.com/pulse/56965d5a4637f2624bcdd0ab/
Fill in your business email to start


