


The phishing phenomenon is a recurring, almost daily, mention in major publications — (BBC, Engadget Business Wire, the list goes on…) “even my dad knows what it is”, writes Palo Alto blog’s Kate Taylor.
But why is phishing always on our minds? And more than that, it’s flooding the news of the masses, reaching far beyond the news feeds of the security savvy.
One of the most common contexts where phishing, and hacking in general, come up is the world-famous Facebook social network, which boasts somewhere around 1.23 billion users.
When was the last time Facebook was hacked? Not so recently, only four days ago (June 5th, 2016), but it’s been fairly quiet since then.
All of a sudden, Zuckerberg’s Pinterest showed this:
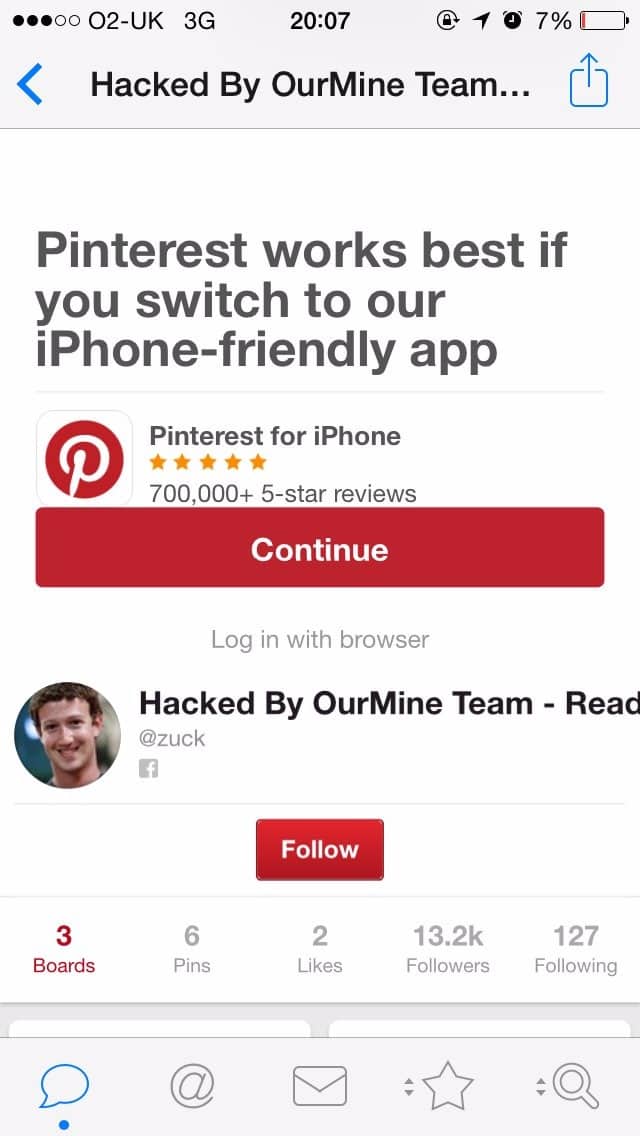
And if Zuckerberg’s personal social media accounts were hacked in one blow, what does that say about his self-made social legacy, and its propensity for falling victim?
In the last month, the Facebook phish on the loose was under the guise of “Who Posted Your Photo Here?”. At the moment, images and screenshots from this hoax have been taken offline, but this is the confirmed information as of yet (according to hoax-slayer.com, an online security website that boosts awareness and warns end users of scams that may be targeting them):
Allegedly, Facebook users are asked (by a message from one of their fellow Facebook friends), “who posed your photo here?”, with a ‘shocked’ emoticon, suggesting that their photo was posted without permission.
The user is then prompted to enter his Facebook login details, which is sent to criminals to access the victim’s account. The ‘who posted your photo’ message is sent onward to other users, ultimately supplying the perpetrator-gone-phishing with a surplus of Facebook user credentials.
The damage from this phishing incident has either been mild, or yet-to-be-disclosed. Either way, Facebook phishing incidents have the (proven) potential to be as brutal as possible.
Hacker’s are blessed with a full palette of options when it comes to cyber crime, but the same can be said about phishing variants, as there are many to choose from.
Either way, phishing is an ultimate fan favorite — In Q1 of 2016 alone, the rate of phishing attacks increased by 6.3 million in raw numbers, with 789% jump since Q4 of 2015.
The truth hurts: Q1 of 2016 has seen more phishing attacks than at any other time in history.
As far as social engineering schemes go, hackers are always happy (to say the least) to access users’ financial data and anything that can guide the way to the big bucks.
The retail/service sector is the most sought out address for phishing enthusiasts, with the world’s most infected country being China, where 57.24% of computers are infected.
When push comes to shove, phishing attacks can be performed by the simplest level of hackers, and the profits are easy to come by.
Hackers love phishing because it’s an easy way in. They use people’s lack of attention to details (like a misspelled URL) and a legitimate looking website to collect credentials which are integral steps in their attack process.
Ultimately, sensitive information is sensitive for a reason, and when it’s accessible via malleable communication networks, it’s even more promising. When the most unsophisticated hackers find out that passwords, credit cards, and financial details could be speedily delivered to their doorstep, they’re going to pursue until they prevail.
Ransomware has undoubtedly become a phishing-favorite: as of this past March, 93% of phishing attacks contained encryption ransomware.
It’s pretty easy to see why ransomware is a go-to method for phishing enthusiasts;
It’s not only getting easier and easier to send, it also offers an easy, quick ROI.
Because victims need to (and can) pay up ransom fees quickly in order to regain access to their encrypted data, criminals are rewarded instantaneously, and happily so.
And it’s only getting worse;
It’s basically anyone and everyone. Average users, businesses, law enforcement and government agencies, emergency services, and so on. But businesses and the enterprise at large are go-to phishing targets. Where there’s business, there’s money, and where there’s money, there’s what to phish for.
In the UK alone, ransomware attacks happen on an average of 2,000 per day.
Recently, S/TrojanDownloader.Nemucod has earned its fame as a nasty ransomware payload that’s swirling around the globe.
These particular malware contains a JavaScript file that installs Nemucod on the victim’s PC, once it’s opened and downloaded by the user.
The end payload is a crypto-bug, such as TeslaCrypt and Locky, both of which require a ransom for decryption. The encryption standards involved are similar to those used by financial institutions to secure online payments.
In early 2016, Carole Gratzmuller, CEO of Etna Industrie, a medium-sized industrial equipment company in France, fell victim to a specialized email phishing attack, often referred to as “Bogus Boss”. BBC calls this type of phishing scam “a boss’s worst nightmare.”
Gratzmuller and her accountant were pressured by fraudsters to authorize a ‘highly confidential’ money transfer of 500,000 Euros to foreign bank accounts. Three of the four transfers were held up by the banks, leaving only 1 of them (valued at 100,000 Euros) to go through successfully.
According to FBI’s IC3 (Internet Crime Center), business email compromise scams have affected about 7,000 companies in the last two years, amounting to somewhere near $740m.
After being at Infosec this week, we have been witnessing a surge in anti-phishing technologies and techniques, each of which have a different method to boost employee awareness and their company’s ability to mitigate attacks — by monitoring people’s inboxes to detect phishing emails.
All the while, only a rare few tackle the problem on the phishing site end; detecting phishing sites that succeed by exploiting the business’ brand to seize opportunities for phishing.
Gartner is quite decisive about how businesses can react to phishing, specifying that monitoring DNS and social media profiles may indeed reduce the probability of phishing attacks that target enterprise assets, but that alone isn’t enough.
Gartner insists that beyond-perimeter technologies must be in place in order for phishing campaigns to be sufficiently prevented. Online messaging activity must be scanned, analyzed, classified, and so forth, which is beyond the capability of most enterprises.
Fill in your business email to start


