


Following the attack on FireEye, the US Department of Homeland Security (DHS) has issued an Emergency Directive (ED) regarding a backdoor being exploited in SolarWinds Orion products, versions 2019.4 through 2020.2.1 (inclusive).
Based on file signatures, FireEye considered this campaign to have started around March 2020, potentially affecting up to 18,000 organization worldwide.
This campaign, now known SUNBURST Solorigate, uses signed, backdoored infected DLL’s to gain access to organizations by communicating with malicious C2 infrastructures.
This campaign is considered as critical, as it’s based on a “Supply Chain Attack” – the attackers were able to infect key files from SolarWinds and perform “DLL Hijack” to make the application load the trojanized malware.
The list of products affected is quite comprehensive:
Having infected a victim host the threat actor will attempt to deliver additional malware threats including:
This report focuses on `Teardrop` and its impact, the other threats can be detected and mitigated with the rules mentioned in the recommendations.
Although at this point it is not possible to attribute the campaign to a specific group, FireEye has given the campaign an uncategorized ‘UNC’ identifier, dubbing the group ‘UNC2452’, whilst Palo Alto’s Unit-42 assigned the threat actor as ‘SolarStorm’.
The impact of this incident at this time should be considered critical given that it could lead to a full organization compromise. If affected, assume breach and begin Incident Response immediately.
Currently observed victims seemingly include government, consulting, technology, telecom and other entities in North America, Europe, Asia and the Middle East.
Based on the certificate used, the trojanized patch in question dates back to March 2020:
Once applied, the trojanized patch will extract malicious DLL’s to the Solarwinds folder:
Files in question are all signed using the following certificate (53f8dfc65169ccda021b72a62e0c22a4db7c4077f002fa742717d41b3c40f2c7, Serial Number 0f:e9:73:75:20:22:a6:06:ad:f2:a3:6e:34:5d:c0:ed):
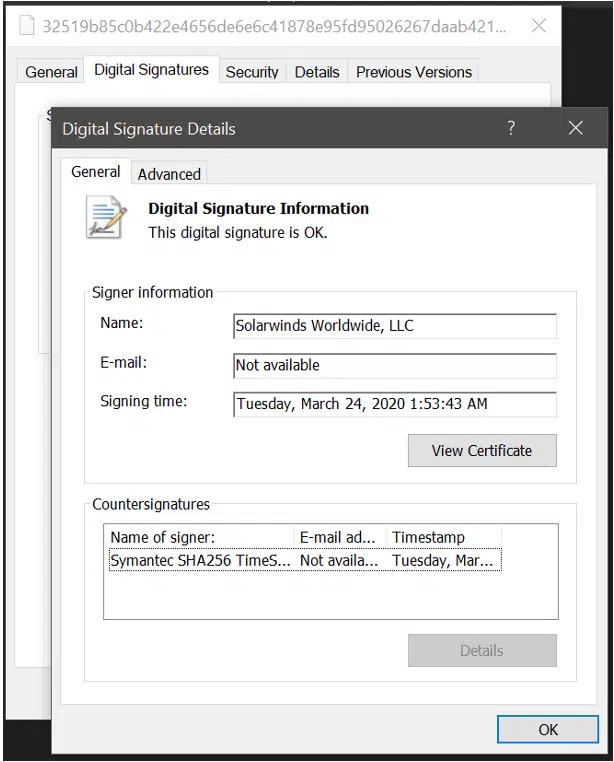
Once in folder, legitimate SolarWinds executables will attempt to execute it (performing an attack called “DLL Hijack”):
SolarWinds.BusinessLayerHost.exeSolarWinds.BusinessLayerHostx64.exeIn a period of up to 2 weeks, the malware will attempt to resolve to the following address:
avsvmcloud[.]comOnce resolved, a CNAME record will be returned, in order to perform C2 communications. This can be one of the following four:
Once initial access is gained, the threat actor group will attempt to perform Lateral Movement using a variety of techniques, sticking to legitimate credentials and remote access for access into a victim’s environment.
In one of the infection cases, a never seen before memory-only dropper dubbed TEARDROP was used as part of the operation to deploy a Cobalt Strike beacon.
TEARDROP is a memory only dropper that runs as a service, spawns a thread and reads from the file “gracious_truth.jpg”, which relies on Steganography for payload download and execution.
Once executed, the payload will check that HKU\SOFTWARE\Microsoft\CTF exists, decode an embedded payload using a custom rolling XOR algorithm and manually load into memory an embedded payload using a custom PE-like file format.
The malware piece will attempt to generate (using Domain Generation Algorithm) domains for communications over a random interval, from 1 to 3 minutes, 30 to 120 minutes and up to 420-540 minutes in case an error was handled.
Once generated, the malware will check against hardcoded IP’s for an updated A record domains for communications:
Once inside the organization, the threat actor will likely attempt to advance their attack to the next stage through the delivery of additional malware such as:
Potential other attacker activities include:
Attackers might attempt to get a list of users on the Exchange server and their current role using ‘Get-ManagementRoleAssignment’:
C:Windowssystem32cmd.exe /C powershell.exe -PSConsoleFile exshell.psc1 -Command “Get-ManagementRoleAssignment -GetEffectiveUsers | select Name,Role,EffectiveUserName,AssignmentMethod,IsValid | ConvertTo-Csv -NoTypeInformation | % {$_ -replace ‘`n’,’_’} | Out-File C:temp1.xml” Retrieve information about the configured Virtual Directory using Get-WebServicesVirtualDirectory:
C:Windowssystem32cmd.exe /C powershell.exe -PSConsoleFile exshell.psc1 -Command “Get-WebServicesVirtualDirectory | Format-List” Querying and extracting data from Active Directory using AdFind:
C:Windowssystem32cmd.exe /C sqlceip.exe -default -f (name=”Organization Management”) member -list | sqlceip.exe -f objectcategory=* > .SettingSynclog2.txt Attackers might use PowerShell to create new tasks on remote machines:
$scheduler = New-Object -ComObject (“Schedule.Service”);$scheduler.Connect($env:COMPUTERNAME);$folder = $scheduler.GetFolder(“MicrosoftWindowsSoftwareProtectionPlatform”);$task = $folder.GetTask(“EventCacheManager”);$definition = $task.Definition;$definition.Settings.ExecutionTimeLimit = “PT0S”;$folder.RegisterTaskDefinition($task.Name,$definition,6,”System”,$null,5);echo “Done” Targeting multiple machines at once:
C:Windowssystem32cmd.exe /C schtasks /create /F /tn “MicrosoftWindowsSoftwareProtectionPlatformEventCacheManager” /tr “C:WindowsSoftwareDistributionEventCacheManager.exe” /sc ONSTART /ru system /S [machine_name] Once Exchange access was gained and data was found, attackers might search and exfiltrate data using the following command (for example, last year alone):
For the sake of easy exfiltration (as an archive and not file-by-file), attackers created archives on the Exchange server so it could be exfiltrated using a single HTTP command:
C:Windowssystem32cmd.exe /C .7z.exe a -mx9 -r0 -p[33_char_password] “C:Program FilesMicrosoftExchange ServerV15FrontEndHttpProxyowaauthRedir.png” C:Tempb.pst An example URL for the attacker to collect the exfiltrated data would be:
On disk, this was located at the following path:
\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\ \Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\Current\themes\resources\ Finally, the attacker added their own devices as allowed IDs for active sync for a number of mailboxes using Set-CASMailbox:
C:\Windows\system32\cmd.exe /C powershell.exe -PSConsoleFile exshell.psc1 -Command “Set-CASMailbox -Identity <UserID> -ActiveSyncAllowedDeviceIDs @{add=’XXXXXXXXXXXXX’}” File path:
Vetted Hashes
Exchange Management Shell PowerShell commands potentially used:
Domains:
IP’s:
| Technique | Tactic |
| T1012 – Query Registry | Discovery |
| T1027 – Obfuscated Files or Information | Defense Evasion |
| T1057 – Process Discovery | Discovery |
| T1070.004 – File Deletion | Defense Evasion |
| T1071.001 – Web Protocols | Command & Control |
| T1071.004 – Application Layer Protocol: DNS | Command & Control |
| T1083 – File and Directory Discovery | Discovery |
| T1105 – Ingress Tool Transfer | Command & Control |
| T1132.001 – Standard Encoding | Command & Control |
| T1195.002 – Compromise Software Supply Chain | Initial Access |
| T1518 – Software Discovery | Discovery |
| T1518.001 – Security Software Discovery | Discovery |
| T1543.003 – Windows Service | Persistence, Privilege Escalation |
| T1553.002 – Code Signing | Defense Evasion |
| T1568.002 – Domain Generation Algorithms | Command & Control |
| T1569.002 – Service Execution | Execution |
| T1584 – Compromise Infrastructure | Resource Development |
[1] https://cyber.dhs.gov/ed/21-01/
[2] https://www.solarwinds.com/securityadvisory
[3] https://activedirectoryfaq.com/2018/06/o365-hybrid-exchange-federation-trust/
[5] https://docs.microsoft.com/en-us/cloud-app-security/investigate-risky-oauth
[6] https://github.com/fireeye/sunburst_countermeasures
[7] https://github.com/sophos-cybersecurity/solarwinds-threathunt
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


