


During a recent investigation using CyberInt’s Argos™ platform, a number of websites were identified as using the popular open-source WordPress content management system and discovered to be compromised with suspicious obfuscated JavaScript.
Subsequent analysis of the obfuscated JavaScript on these initial websites led to the discovery of over 1,600 further sites exhibiting similar payloads, seemingly as part of mass-injection campaigns against vulnerable WordPress installations.
Whilst campaigns of this nature are unfortunately commonplace, targeting vulnerable or out-of-date WordPress websites, this discovery reiterates the need for website owners to ensure that their installations are well maintained, minimising the time between vulnerabilities being discovered and patched, as well as demonstrating how regular site content audits or monitoring could alert website owners to these unauthorised changes.
Based on a review of the websites identified as currently compromised, a variety of WordPress versions and plugins have been identified. As such it is likely that multiple vulnerabilities are being exploited, potentially by multiple campaigns and threat actors, in some cases resulting in one website having multiple instances of injected nefarious payloads.
Whilst many websites may employ old WordPress and plugin versions, likely detectable and exploitable by automated processes, the following recently announced vulnerability is reportedly being exploited by those conducting mass-injection campaigns.
Affecting version 1.2.40 and earlier, this remote code execution vulnerability[1], discovered by researchers at Synacktiv[2], is present within the Duplicator[3] plugin which provides the ability for administrators to migrate or clone their WordPress sites from one location to another.
Following the use of this plugin, a number of PHP files remain on the migrated or cloned site (Figure 1) which can be reused to inject malicious code, such as that used to subsequently inject the JavaScript payloads identified in these campaigns.
Figure 1 – Example files remaining following the use of Duplicator v1.2.40 or earlier
Furthermore, a ZIP-compressed archive, containing a full copy of the site, in addition to a SQL database backup file (Figure 2) also remains and can potentially expose sensitive data.
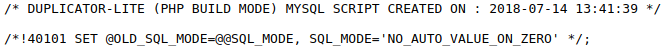
Of the sites observed using a vulnerable version of this plugin, exposed data was detected including API credentials for cloud services, such as Amazon Web Services, as well as API credentials for PayPal (Figure 3).
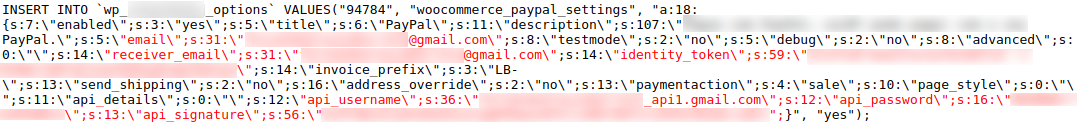
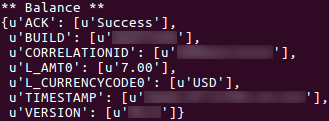
In addition to potentially abusing cloud service credentials for further nefarious activities, the PayPal API credentials could allow the account holder’s balance to be queried (Figure 4) along with various transaction processes, including refunds, potentially permitting fraudulent activity.
Whilst this vulnerability has now being patched by the vendor[1], administrators are recommended to ensure that all installation, and potentially sensitive, files are removed post-migration.
Fill in your business email to start


