

Cyberint has observed increased use and availability of ‘account checker’ tools that allow threat actors to bulk test credentials, typically obtained from data breaches or leaks, against a variety of online retailers and services. These ‘credential stuffing’ attacks allow threat actors to identify customers that have reused the same credentials across multiple sites and, when a successful combination of credentials has been found, automatically extract pertinent account information such as details of any credit balance or subscription status.
Once a list of valid credentials for an online retailer or service has been identified through the use of an account checker, their value can be determined at a glance (Figure 1) and subsequently traded on underground marketplaces and forums, if not directly abused by the threat actor.
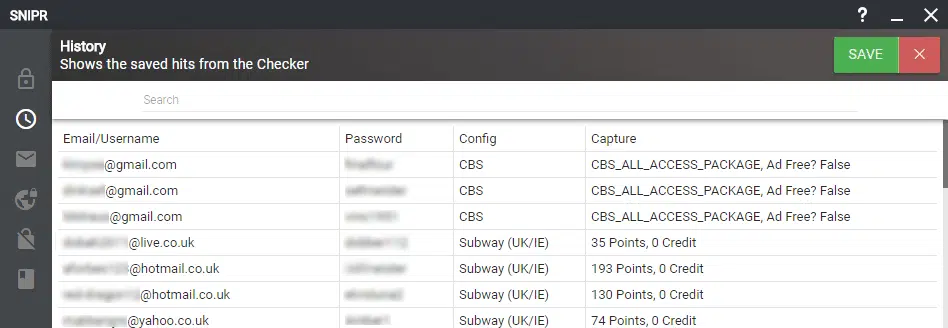
Figure 1 – Account checker with additional details (SNIPR)
Subsequent abuse of compromised accounts can include the extraction of payment card data, if not properly secured by the retailer, theft of credit or gift card balances, and the fraudulent acquisition of goods and services.
In the last case of fraudulent transactions involving digital goods, such as the purchasing of gift cards, subscription codes or digital download codes, the act itself requires little sophistication on behalf of the threat actor. Digital purchases can typically be completed by a threat actor from anywhere in the world and will be easy to resell or trade. Conversely, transactions involving physical goods will likely require a threat actor to be located in the same region as the retailer as well as need a ‘drop’ address to receive the goods so that the fraud is not directly linked to him.
Whilst numerous site- and service-specific account checkers exist (Figure 2) as both online tools and downloadable executables, this report focuses on two extensible tools that are readily available, well-supported and popular amongst threat actors wishing to target a variety of online retailers and services, i.e. ‘Sentry MBA’ and ‘SNIPR’.
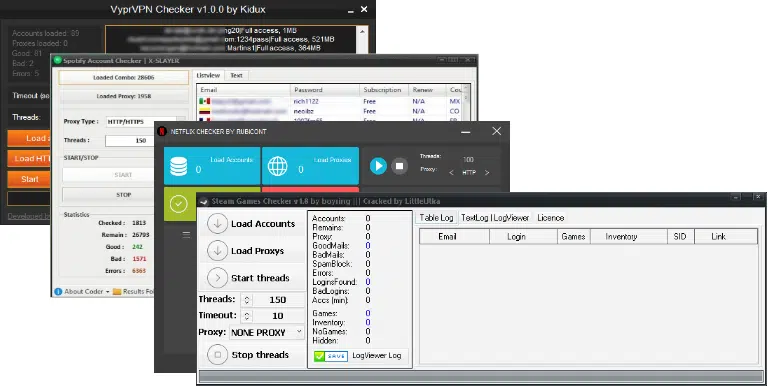
Figure 2 – Example site/service-specific account checkers
Before using the account checker tool, the threat actor will first need to obtain and compile a list of ‘combos’, that being a text file containing a combination of potential usernames or email addresses as well as passwords (Figure 3).
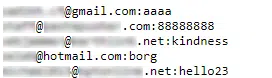
Figure 3 – Example ‘combos’ list in the format <email address>:<password>
In addition to commonly being traded on underground forums and marketplaces (Figure 4), many threat actors may seek to download or build their own ‘combos’ from leaked credential dumps often posted to text-sharing websites.
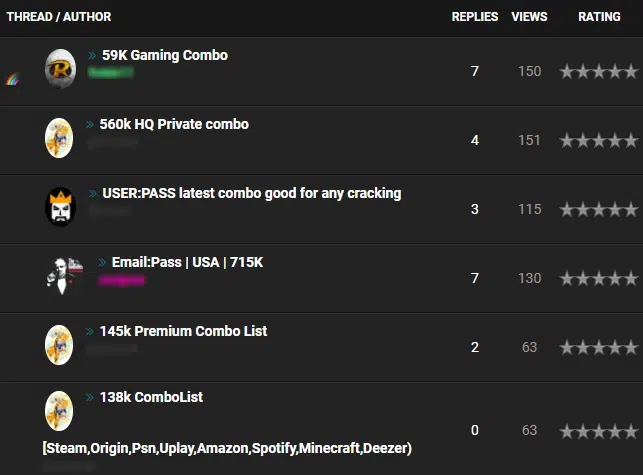
Figure 4 – Example trade of ‘Combos’
While a few advanced threat actors may compromise hosts to gather their own sets of credentials, the most common users of these tools will be less capable and therefore reliant on combos obtained from other sources.
Furthermore, threat actors experienced in the use of account checkers may seek to increase the tool’s efficacy by compiling targeted lists of credentials, for example, building a list containing only ‘.co.uk’ based credentials to target a UK-based organisation.
Considering that over five-million data records are reportedly lost or stolen every day (1) and that numerous studies and surveys have indicated that sometimes up to 80% of users reuse passwords across multiple sites, the potential return on investment for threat actors is incredibly high. The off-the-shelf nature of these tools, credential sets and site-specific configurations, allow unsophisticated threat actors to be relatively successful when using high volumes of lost or stolen credentials given the high proportion of users with poor security practices.
Click Here to Download the Full Brief Including the Following Chapters:
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


