


We all know about the phishing scams, malware, and look-a-like phishing sites, but there are more and the dark web is the place for criminals to plot and source their attack method of choice.
Here are the top fraud 6 fraud attack vectors that we recommend looking out for:
Every organization hopes to have all their employees do their job with honesty and integrity. Unfortunately, there are times when the lure of “easy money” can cause an employee to take advantage of their privileges and access.
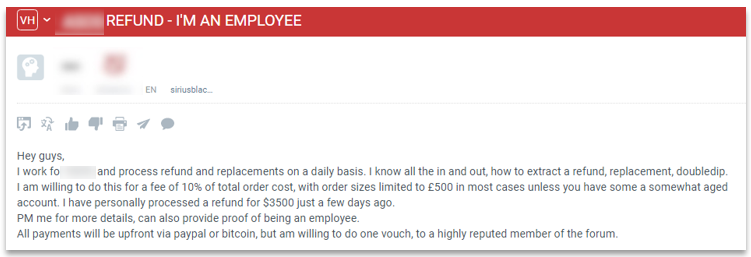
In one such case, an employee was offering information on a deep web forum that would enable people to submit fraudulent refunds. Since he had access to internal intellectual property and confidential data, he knew how to instruct people to submit a fraudulent refund of $500. In exchange for helping commit this fraud, he was charging a 10% upfront fee to be paid via PayPal or Bitcoin. Using threat intelligence software, the retailer was alerted to this activity.
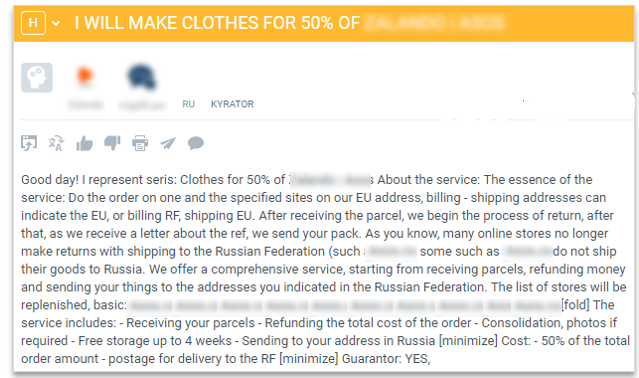
It’s not always an employee that will be out there on the deep web offering fraudulent refunds. In this use case, a threat actor posted on a deep web forum offering refunds for a specific clothing retailer for a fee of 50% of the purchase price.
Here’s what happened next: this retailer was alerted by their threat intelligence system; the cybersecurity analysts were able to learn more about the source and methods of this threat by contacting the cyber criminal via chat. By interacting with the cyber criminal, the analyst could determine if the threat was real, what information they had, and how extensive the threat was. This type of case highlights the value of combining intelligent cyber automation and alerting with cyber analysts who can follow up on the alert to bring context and immediacy of action required by the threat.
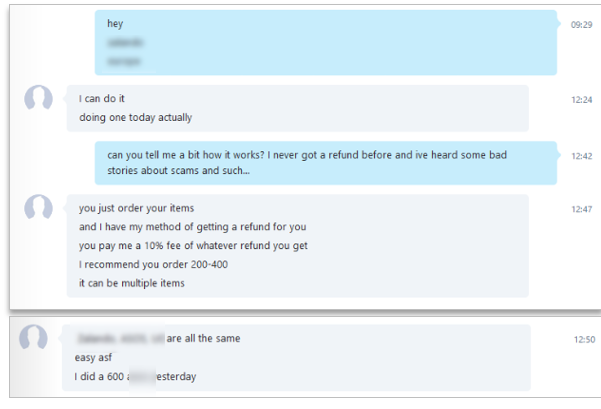
Again, another scam targeting refunds. This time, rather than charging a percentage of the refund for a service, the threat actor is selling a tutorial on how to submit a fraudulent refund for a specific retailer. The tutorial teaches consumers how to steal from retailers so that anyone, even those without any tech or hacking experience, can follow the instructions to commit fraudulent refunds.
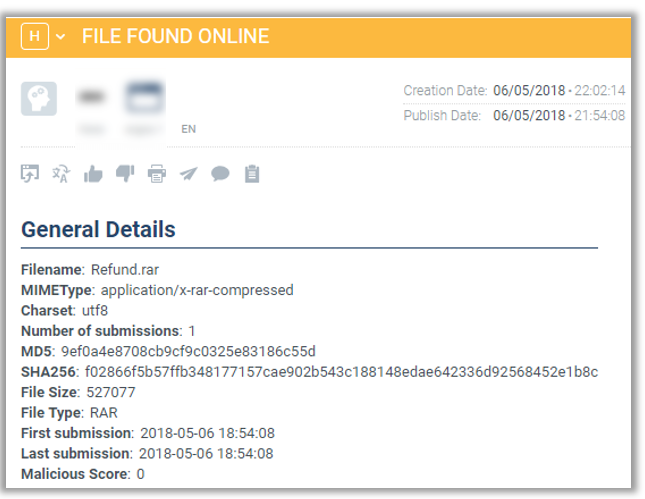
This tutorial was found on the dark web in a file sharing repository that contains refund tutorials for several retailers. One of the online retailers was alerted by their threat intelligence system. Cybersecurity analysts could then review the content of the files to gain insight into how the retailer’s refund process is being exploited. This information is critical in helping the retailer resolve weaknesses in the order and delivery process.
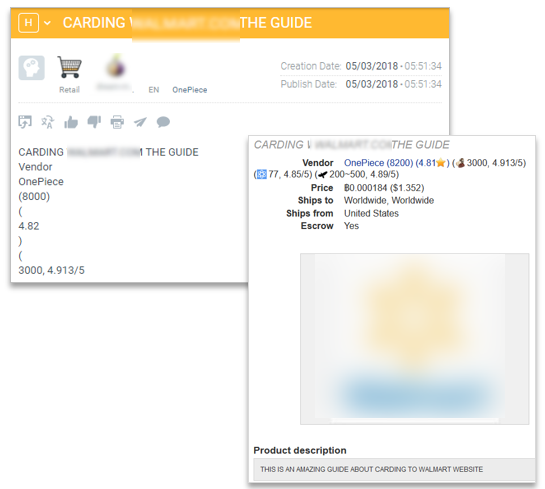
Carding involves the use of stolen credit card information to purchase goods online. In this particular use case, tutorials and carding guides can be found or purchased in darknet marketplaces and deep web forums targeting specific retailers. A threat intelligence system can detect these threats and alert the retailer if they are specifically being targeted in the threat. The online retailer’s cybersecurity provider can then purchase the targeted carding guide to learn the methods used. In this way, at least the retailer’s cybersecurity team can begin to take action to prevent further attacks using this method.
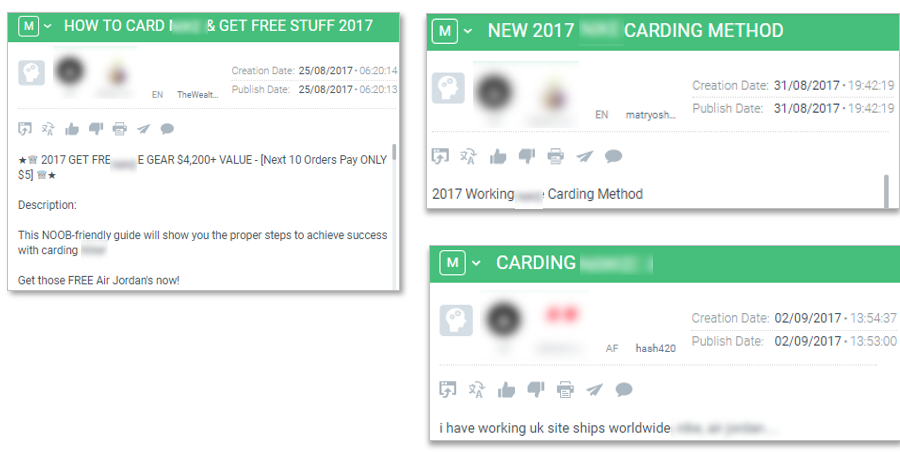
In this use case, cyber criminals have obtained customer account information from specific online retailers and are selling them on the dark web. Someone who purchases a stolen customer account can use the information to login to a retailer’s website and purchase items using the credit card information stored in the customer account.
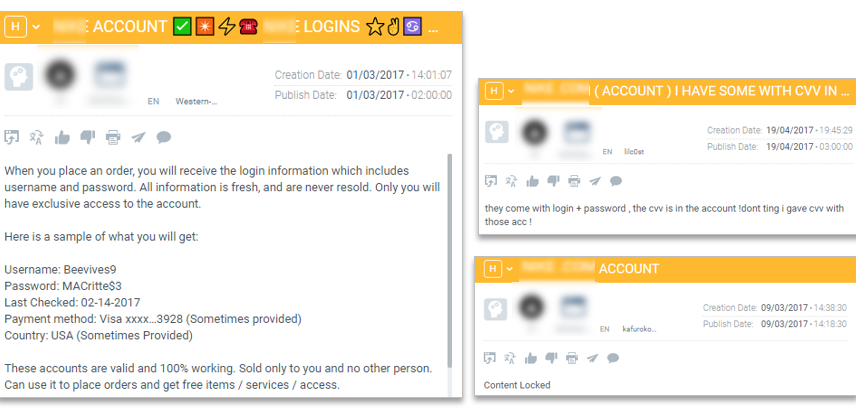
The retailer, in this use case, was alerted by their threat intelligence platform that customer data had been stolen. The retailer requested that their cybersecurity provider purchase other available customer accounts from the threat actor in order to investigate the source of the breach. Further probing could also include a HUMINT investigation of the cyber criminals.
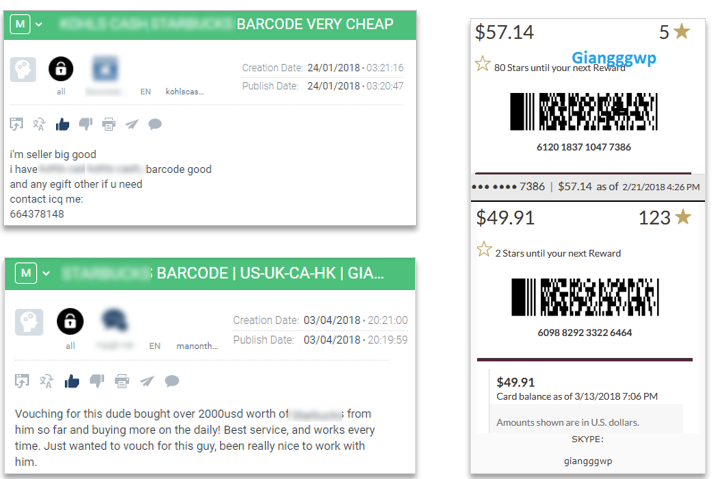
This use case shows yet another fraudulent attack vector: selling online retailers’ e-Gift cards and bar codes on deep web forums. Thousands of dollars worth of these barcodes and e-Gift cards were purchased from this threat actor. After being alerted of these attacks, the retailer’s cybersecurity analyst contacted the cyber criminal, posing as an interested buyer, to gain an understanding of the source of the e-Gift cards and barcodes.
The combination of an advanced threat intelligence platform and expert cybersecurity analysts are instrumental in keeping you armed with everything that is needed to help prevent these attacks. Don’t just hope for the best, contact Cyberint and see what else you can do to prepare for this holiday season.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


