


Election fraud is a growing crisis.
The problem of organized crime has always been well-known; so too organized, and structured cybercrimes. But how about ones that affect real-world events and politics, and not just money and data theft?
Could a president actually be elected only because he succeeded in a cyber attack, which gave him false votes?
Is this (threat) for real?
Andres Sepulveda was asked what he thought about the possibility of cyber criminals manipulating/influencing the U.S. Presidential Campaign, he said:
“I’m 100% sure it is”
Who is Andres Sepulveda?

How did he do it? Well, for starters, Sepulveda was given a $600,000 budget to manipulate Nieto’s campaign. With that sum allocated for funding his hacking efforts, Sepulveda was both prepared and encouraged to invest profound efforts and pursuits to manipulate Nieto’s campaign.
Is Sepulveda’s contribution to Pena Nieto’s victory an anomaly? Or does it represent a growing trend in organized cyber crime?
Finally, is it happening with current election campaigns, and if not, will it happen soon enough?It depends on your (each election campaign’s) cybersecurity strategy
Since 2005, Sepulveda has been riding through a career of campaign website defacing; breaking into opponents’ donor databases; and assembling teams to spy, steal, and smear on behalf of Latin American presidential campaigns.
Sepulveda charged $12,000 a month — and the service included his crew that hacks smartphones, spoofs and clones web pages, and sends (forged) mass e-mails and texts.
If $12,000 doesn’t sound like enough, Sepulveda’s hacking missions can also be boosted to a premium; for $20,000, he will throw in a full range of digital interception: attack, decryption, and defense.
Sepulveda’s political hacks have made their way throughout Latin America: Nicaragua, Panama, Honduras, El Salvador, Colombia, Mexico, Costa Rica, Guatemala, and Venezuela. He’s manipulated political campaigns in every one of them.
Many times, presidential candidates only knew about the role Sepulveda was playing existed, and not of his identity, or any details beyond his end-goal.
More recently, election cybercrime has come up on the other side of the globe. Sadly, the political cybercrime threat doesn’t stop at Sepulveda.
On March 27, Comelec, the Philippines Commission on Elections, had their website broken into and defaced by ‘The Anonymous Philippines’ (Anonymous);
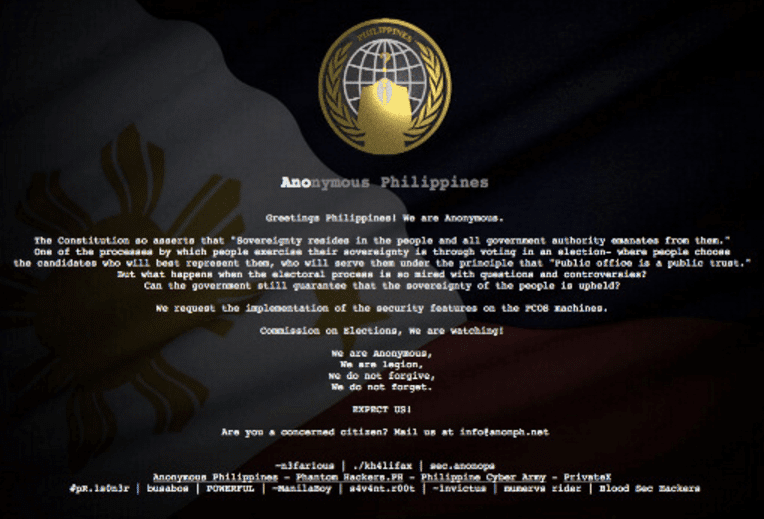
Anonymous posted the poll body’s database, accompanied by a message “asking the Comelec to make sure the PCOS have security measures in place”.
PCOS is Precinct Count Optical Scan, a type of AES (automated election system), that counts election votes automatically. These machines were used in both 2010 and 2013 for the Philippine elections.
In their warnings to Comelec, Anonymous confirmed their knowledge:
The database has a file size of around 340 GB, with some of the tables supposedly encrypted by the Comelec, yet the hackers stated that they have the algorithm needed to decrypt that data.
Anonymous also posted the following (rhetorical) questions:
“What happens when the electoral process is so mired with questions and controversies? Can the government still guarantee that the sovereignty of the people is upheld? We request the implementation of the security features on the PCOS (precinct count optical scan) machines”
The group warned the Comelec that it would be closely monitoring how the poll body would administer the elections.
As a result of Anonymous’s hack, this is what happened:
It seems that the Pena Nieto fiasco is not one of a kind, on the contrary…
Nieto’s motives behind his investment in cybercrime don’t need much unraveling. Nieto wanted to guarantee his success — he wanted to take home the ‘President’ hat. And he did.
But what about Anonymous Philippines?
They too, don’t need much deciphering — they stated their motives upfront:
“…But what happens when the electoral process is so mired with questions and controversies? Can the government still guarantee that the sovereignty of the people is upheld?” (Anonymous Philippines posted this on the Comelec website)
The hackers have no incentive to manipulate the presidential elections, on the contrary: They want to make sure Comelec knows how dire the threats are of a hack…and how seriously they must take the cybersecurity element of their voting plan.
What Can Comelec Do?
This past February, Comelec spokesperson James Jimenez stated in an interview that Comelec will not be using PCOS machine for the 2016 elections, and instead, they will only use VCMs (Vote Counting Machines), as shown below:

What advantage does VCM hold over PCOS? What do they do differently, that could prevent the discrete actions of Anonymous and their crew(s)?
VCMs are standalone machines that run vote-counting, different than the system that runs the Comelec website. This setup is a result of a network segmentation strategy. With this segmentation, the Comelec website, www.comelec.gov.ph, is able to be separate from the site where the poll body will upload election results this coming May.
Should the Comelec website get hacked, the VCMs are inaccessible to those hackers, and so too, the vote counts. In security terms, this means that Comelec is isolating their crown jewels (the polls) from unwanted hands.
But sadly, for Comelec, many more security measures are needed to secure their crown jewels in the best way possible:
Insider threats exist essentially in every phase of election processes; before, during, and after voting takes place.
Two examples, among many, of insider cyber threats that exist in elections are:
What if a campaign employee unknowingly plugs an isolated VMC (or any isolated device) to the internet, when the device was meant to remain entirely detached from it?
What if a USB with malicious content is unknowingly connected to the system, or worse, what if an employee connects his USB in order to steal data?
These things happen…
Every political election, no matter the size or scale, needs to emphasize cyber awareness among every employee, no matter their position. These authentication glitches can happen easily, but they can also be prevented just as easily.
Domain Abuse
A solid example of how domain abuse can manipulate political campaigns is found among none other than Donald Trump and Jeb Bush, in the 2016 U.S.A Presidential Campaign.
In January, when a curious Republican voter clicked on JebBush.com, he thought it was being directed to Jeb’s website. But instead, he saw a big, smirking picture of Donald Trump flashing a banner that declares “SHOW YOUR SUPPORT FOR DONALD TRUMP.”
Sadly, Trump bought Bush’s domain, just to have this effect on potential Jeb voters.
While those seeing this banner may not be immediately swayed to support Donald Trump, the pop-up certainly diminished Bush’s credibility. And of course, in our digital world, this negative sentiment wasn’t limited to Jeb Bush’s alleged website:
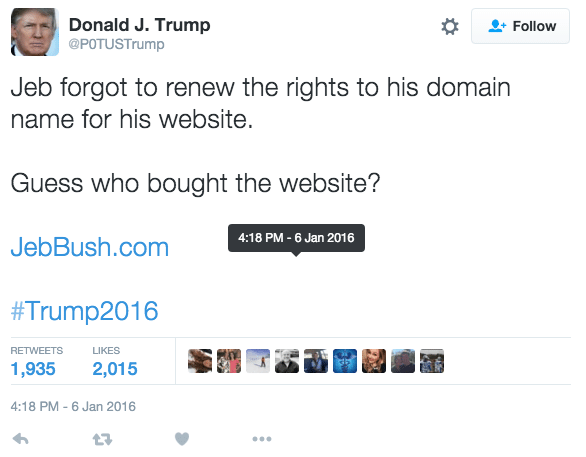
Trump’s hack spread like wildfire to Twitter, with 1,935 retweets, and 2,015 Likes. That doesn’t leave much room for positive sentiment towards Mr. Bush.
How can domain abuse be mitigated?
For starters, automatic threat detection tools, such as Argos, see to it that every and any fraudulent domain is monitored, identified, and caught in its tracks.
Phishing
In election campaigns, phishing can (and has been known to) create fictitious sites that solicit fake support for donations, which actually end up going to the opponent of whoever payers think they are donating to.
This is what happened in 2004 with Kerry and Edwards.
Potential voters were receiving emails that solicited donations, and those that provide their credit card numbers thought they were generously supporting their candidate, when really, they were supporting their opponent.
While phishing is less manageable with security tools, awareness is key. Next week, we’ll discuss different email bugs that our cyber analysts were able to identify and spread awareness for — which allow these threats to be mitigated.
Comelec’s measures to use VCMs instead of PCOS machines is a step in the network architecture direction, but it leaves room for more. Owners of crown jewels (in this case the polls or voters data) must segment every form of communication away from their goods, as much as physically possible.
In the past, we’ve advised political candidates and their teams to segment their most sensitive phone calls by using a different phone than their usual one, with a prepaid SIM card. If you don’t want any hackers bugging your phones on behalf of opponents, you need to tap into the hackers’ mindset, and think of what and how they would do to listen in to your chatter.
Sadly, cyber isn’t only after industries like finance, gaming, telecom, etc. They want politics, and they want as many campaigns as they can get.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


