


This week, we’ve decided to reflect on the evolution of the cyber industry, and identify the game players who have, whether intentionally or not, allowed the (parallel) relams of cybersecurity and cybercrime to reach the magnitude they have thus far.
Is the worlod of cyber a mere battle between good and evil? A game of cat and mouse, where the most sophisticated take the cake?
Or is it a complex sphere of creativity; an evolutionary byproduct of technology’s advancement since the beginning of time?
Co-Founder of Apple, named “one of Silicon Valley’s Most Creative Engineers”

Steve Wozniak wears many hats in our historical tech landscape. His most recent claim to fame is his discussion of the “Artificial Intelligence Revolution”, where he describes AI as:
“the next big disruptor, separate from the digital revolution that changed the world with personal computers and smartphones.”
AI is reaching a point where it’s closer to what the brain is…how it’s wired, what consciousness and intuition are.
Wozniak’s insights are pristine, insightful, and sharp. But what most interests us as cyber enthusiasts is the experience that brought forth his empirical wisdom, and the creativity that spiraled into his successes.
Initially, Wozniak’s debut to the tech scene (of which he is not only a ‘pioneer of the information revolution’, but an architect of its bedrock), dates back to his partnership with Steve Jobs, wherein he is considered the “brains and genius behind the first Apple computers”.
But before he started blending in with viral words like ‘Apple’, Steve Jobs’, ‘Siri’, and the like, what were his other interests and niches that fostered his tech successes, which ultimately threw him into the spotlight?
In fact, one weighted statement that Wozniak dished out this past April was: “cyber security is the greatest threat to the world today.”
How has Wozniak’s expertise in engineering, information tech, artifical intelligence, etc., allowed him to size up the perils of cybersecurity with such clarity?
Part of what made Steve Wozniak the “geek wizard of his generation” was his fetish for using his imaginative side of engineering to prank friends, family, and school authorities — which he proudly pulled off through hacking computers, bypassing security controls and telecom networks.
“I like to play jokes…” he explained during his Keynote Speech at the 2013 ASIS Conference. While never intruding security systems for profit, malice, or lawbreaking schemes, Wozniak enjoyed the light-hearted, imaginative and joking side of computer hacking.
Wozniak’s love for computer interception didn’t stem from a desire to destruct. On the contrary, he tested out his abilities to manipulate telephone networks and to get his hands on classified electronics and science manuals that were buried deep in Stanford’s engineering labs, forbidden to student access.
He was a budding computer engineer, and relished any opportunity to experiment and grow in knowledge, which he made possible by running his computing programs on punch cards; quenching his thirst to explore the network, and by learning about the exact frequencies in telephone systems.
Although he opted out of a career out of outsmarting computer and security networks, Wozniak has indeed provided expert cybersecurity insight, drawing his tech wisdom onto the evolution of security in our day and age, and dishing out the difficult truths of our abilities to overcome cyber risks.
In his ASIS Keynote, Wozniak explained how technology is changing security;
“Security used to be very physical. But that’s no longer the case. It’s not physical tools that people are using to break security,” Wozniak said.
“We need a new mindset.”
The challenge lies in maximizing the capacity of how technology can enhance our daily lives, and in that, figuring out how we can “keep information private, but yet secure.”
Wozniak represents the flip side of the cybersecurity coin. Good skills are used to commit evil damage, and our challenge as security experts is two-fold: to execute that knowledge to not only anticipate potential damage, but to foresee the solution(s) that will nip it in the bud.
This is the irony as we see it: while we have yet to disclose our full list of cyber heroes, so far, two out of the three are innovative, groundbreaking personalities in the tech world at large.
As cybercrime stoppers, whose side are we really on? Did the forefathers of high speed internet and information engineering win us over because we know they’ve given us the tools to defeat the threat actors?
Or on the contrary, do we appreciate these connectivity and computing milestones, for the sole virtue of enabling the birth of cybercrime, from its first stages of infancy?
Undoubtable on the bad side of our Hall of Fame, Anonymous use cybercrime to raise awareness of ideological causes, which simultaneously creates (and boosts) awareness for the severity of cyber threats.
In the spirit of their very own art of destruction, Anonymous group is a “hacktivist collective”, not restricted to a specific country (nor to a specific entity). They preach a modus operandi of anti-authoritarian retribution.
The group first came to public attention in January 2008, and have since been referred to as:
“the Internet’s greatest spectacle: raucous hacks, federal takedowns, scheming, betrayal and giggles…nihilistic marauders”.
Between 2010 and 2012 alone, at least 90 (Anonymous-associated) individuals worldwide had been arrested for online criminal activities. These arrests took place in the US, UK, and mainland Europe.
“‘Knowledge is free. We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.”
Anonymous celebrates a philosophy of “opposition to injustice”, or otherwise referred to as “establishment hypocrisy”.
They’ve spearheaded and supported wide-scale DDoS attacks, and have mastered the art of cybersecurity through-and-through.
The irony in Anonymous group’s track record of (heinous) attacks is such that all of their attacks are infact declared as an opposition/response or awareness campaign against a political or humanitarian cause; be it beastiality, homelessness, usage of Monsanto food products, Government Internet censorship, online trading of cheetah cubs, sexual abuse, ISIS, child abductors…you name it.
But the cause that won us over as cyber enthusiasts is one that Anonymous addresses in every attack they commit: awareness for the severity and scope of (weak) cybersecurity.
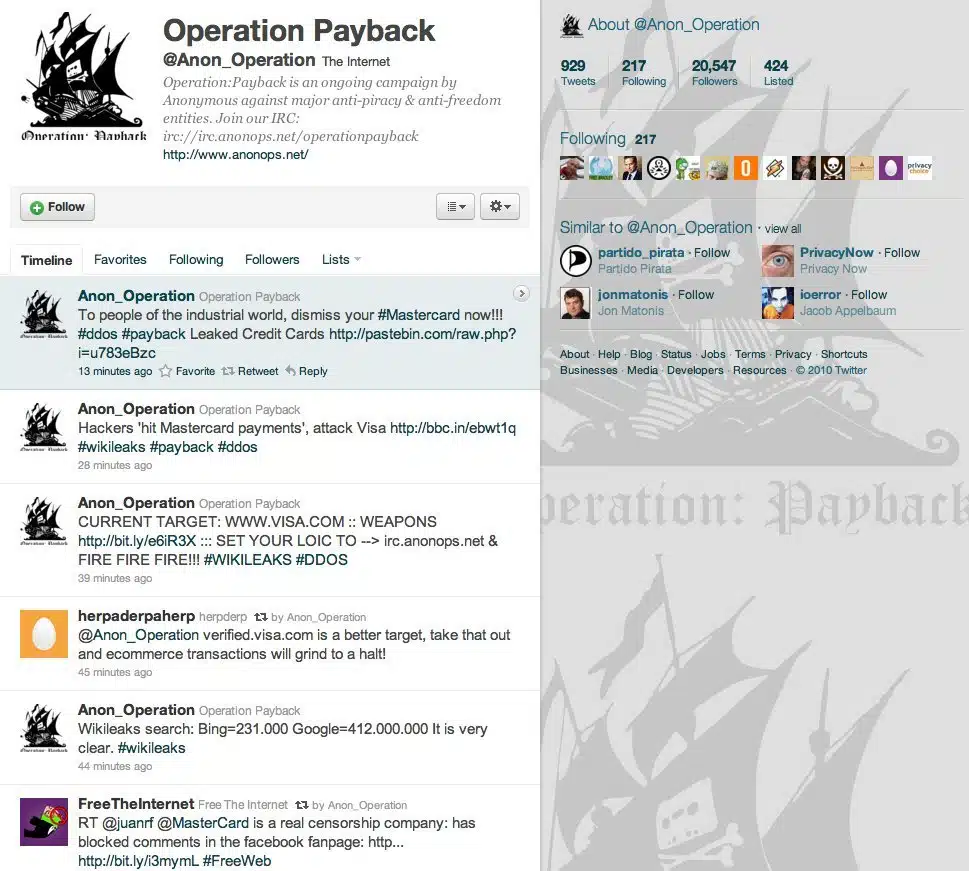
In December 2010, Anonymous targeted the firms that officially stopped processing donations to Wikileaks, such as Paypal, Mastercard, and Visa.
Anonymous’ motive behind this DDoS attack was to support the WikiLeaks campaign against censorship, as Anonymous declared their (collective hacktivist) opposition to “corporations and government interfering on the internet…we believe it should be open and free for everyone. Governments shouldn’t try to censor because they don’t agree with it.”
The hacktivists’ achievement in Operation Payback existed on several fronts:
Legally, four UK youths were arrested (by the US Department of Justice) for the attacks on PayPal’s site, facing ‘relatively minor’ misdemeanour charges. The defendants’ lawyers argued that the youths were acting on behalf of the defense of free speech, a protection guaranteed by the US Constitution.
PayPal’s monetary losses from the DDoS were hefty, costing the company around 3.5 million GBP.
On the whole, Anonymous left a vivid impression on victims, bystanders, and policymakers alike: in addition to making a strong argument in defense of free speech, the world learned the hard way that cybersecurity is as real as ever.
2016: Comelec Data Breach
More recently, Anonymous succeeded in a massive data breach, when they broke into the Comelec (Philippines Commission on Elections), effectively leaking the data of 55 million voters in the Philippines.
This time, the hacktivists left a message on the (tarnished) site after they finished their damage, which was, by the way, a gimmick to scare the public at large. Anonymous’s Comelec attack didn’t actually bring upon any detrimental damage, which is in fact how they intended it to be.
What they really wanted (and succeeded) to do was to scare the public about the daunting reality of election fraud, and how one reckless cyber attack could dictate an entire country’s Presidential election.
It’s certainly no coincidence that Anonymous chose an organization in the Philippines to amplify their message about how low cyber can go…the Philippines has recently been dubbed a “Cyber Crime Hotspot”.
Anonymous have mastered the art of striking public attention to get a message across. Anonymous knows how real the cyber threat is, but more so, they know how to show it.
Finally, what do Wozniak and Anonymous have in common?
The obvious is…obvious: both Wozniak and Anonymous know how to pull off a mean hack. They’re clearly tech savvy, and use their creativity in ways that we wouldn’t expect from the get-go.
But as we see it, the creativity + hacking equation can have two outcomes;
Wozniak’s used his version of creativity to explore the avenues of engineering, which is part of what enabled him to create one of the most jaw-dropping companies that the world has ever known.
As for Anonymous, their fusion of hacking and creativity is not as pretty. They’ve shown the wider public just how deep the damage of hacking can sink in.
Even though this notorious group of hacktivists does spread conducive messages that will ultimately boost our preparedness, the measures they resort to are harmful, to say the least.
Each of our heroes have shown us what hacking is really capable of. And in the meantime, they’re getting a run for their creativity, with a bit of an impromptu (cyber) show-off on the side.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


