I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
NIST has long been an important acronym in the world of cybersecurity, where organizations have for years used the NIST Cybersecurity Framework to help guide their security investments.
But the practices and controls associated with NIST have evolved recently, due to the release of CSF 2.0. If you’re stuck in the era of 1.x, it’s time to adapt.
Read on for guidance on what’s new in CSF 2.0 and how to get started building a cybersecurity strategy that aligns with the updated NIST requirements.
CSF 2.0 is the latest version of the NIST Cybersecurity Framework (CSF). Released in February 2024, it replaces CSF 1.1, which dates to 2018.
To dispel any confusion, we should note that CSF/NIST 2.0 is different from NIS 2, a cybersecurity directive from the European Union that also aims to help strengthen defenses, but has no direct relationship to the NIST CSF, which is developed by a U.S. government agency.
CSF 2.0 is based on the same core concepts as earlier versions of CSF, including:
That said, CSF 2.0 introduces some significant changes to each of these concepts.
CSF 2.0 adds a sixth function – govern – on top of the five functions that existed in earlier versions of CSF (identify, protect, detect, respond and recover).
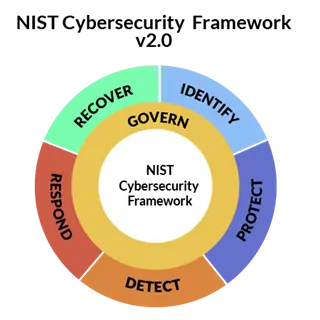
The purpose of the govern function, according to NIST, is to ensure that an organization has a governance plan in place to manage who is responsible for carrying out the other functions, and what the responsibilities of stakeholders are within the realm of cybersecurity. This concept was reflected within the categories of earlier versions of NIST, but transforming it into a standalone function increases the emphasis placed on having a solid governance strategy.
“The introduction of the Govern function signifies a crucial industry acknowledgment that effective management is an integral part of the CISO role,” Shirley Salzman, CEO and Co-Founder of SeeMetrics, writes on DarkReading.
There are still four tiers in NIST 2.0: Partial, risk-informed, repeatable and adaptive.
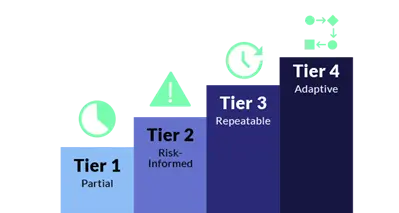
However, climbing the tiers by achieving a higher level of cybersecurity maturity is a bit tougher in the context of CSF 2.0 due to additional requirements – such as the need to secure software supply chains, which was not a focus in earlier versions of CSF.
While the underlying concept behind CSF profiles hasn’t changed, profiles under CSF 2.0 have become more flexible. The new version of the framework encourages organizations to develop a profile tailored to their unique priorities and risks. “NIST’s role is to not overprescribe technology…NIST Cybersecurity Framework 2.0 reframes critical ideas that need to be central to anyone who is building or refactoring a security stance,” says Jason Soroko, Senior Vice President of Product at Sectigo.
To this end, CSF 2 makes the CSF more adaptable. NIST compliance is no longer about cross off items on generic checklists; it’s about setting priorities and establishing a profile that helps your organization address them.
Beyond the changes to CSF core, tiers and profiles that we just described, CSF 2 introduces some other updates as well:
There are now 23 categories, compared to 22 previously and there has been some reorganization,10 categories have been removed, but 11 have been added. For the most part, the concepts within each category remain the same, although a notable change is that governance has now been elevated to the level of a function instead of being addressed at the category level.
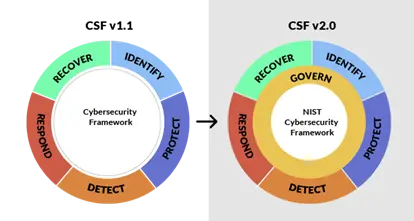
As mentioned above, govern has become its own function in CSF 2.
To implement this function, businesses should start by identifying their organizational context – i.e. what their priorities are (a lot of the concepts come from business environment in 1.1, therefore you probably already addressed this in 1.1).
From there, they can move into risk management by identifying the risks that could impact their ability to protect their priorities. These practices previously fell under the identify function, but they’re now defined as part of governance. Likewise, the concept of formulating policies existed in previous versions of CSF. But it has now become a core element of the new govern function.
CSF 2 uses the govern function to introduce novel concepts and practices, too. Key examples include oversight, which focuses on ensuring that the organization delegates responsibilities to ensure someone actually oversees and carries out policies.
Supply chain risk management, too, exists as a new category under govern with the goal of helping businesses manage third-party risks – including not just tasks like finding and mitigating vulnerabilities in the supply chain, but also determining how you’ll factor incident response planning into supply chain risk management. It has significantly expanded from 5 subcategories to 10 indicating that the supply chain is crucial.
The identify function has changed somewhat for CSF 2.0. It still focuses on identifying an organization’s cybersecurity needs and capabilities, which means tools that can comprehensively map an attack surface remain critical. Organizations need to know what assets they have including data, hardware, software, facilities etc.
The asset management category is a foundational category as without correct mapping, the following functions cannot occur effectively. The risk management category follows on where organizations prioritize and manage the risks.
The identify function now places stronger emphasis on the concept of improvement, meaning the ability to improve cybersecurity abilities on a continuous basis, including the reduction of false positives.

The protect function still includes five categories that focus on protecting assets after you’ve identified them. But because governance has become a core focus on CSF 2.0, the protect function places more emphasis on practices like aligning protection capabilities with identity and access management controls that are part of an organization’s governance strategy.
CSF 2 also reorganized or recategorized some aspects of the protect function. Most notably, it introduces the concept of platform security, which covers hardware, software, physical and virtual protections as an integrated concept.
The detect function – which focuses on monitoring for anomalous activity, detecting risks and knowing when to take action – has been overhauled for CSF 2. Only two categories remain from CSF 1.1.
The updated function places emphasis on practices like continuous monitoring to detect threats in real time, detailed event analysis and analysis of the scope of an event to determine how many systems or assets are impacted.
The respond function, which focuses on reacting to threats or attacks, is based mostly on the same core concepts as in earlier versions of CSF. But it places special emphasis on careful incident analysis, as well as on communication with stakeholders during incident response operations.
The function ensures that correct triage and response is setup and managed i.e. a detailed incident response plan is in place and the relevant people know what to do.

The recover function in CSF 2.0 includes two categories. It hasn’t changed in a major way; it remains focused on ensuring that a business ensures plans are implemented to recover systems, or at least ensure that systems can run in a degraded state until full recovery is possible. The recover function needs to ensure that organizations recover systems to an operational state, while not recovering malware and reintroducing the incident.
Now, however, there is strong emphasis on communication – including not just within the organization, but also with external stakeholders, such as customers, following an incident.
Although CSF 2 reflects some major changes, the good news for organizations focused on NIST compliance is that evolving to meet CSF 2.0 protection guidelines is not all that difficult if you were already conforming with CSF 1.1.
The core practices still boil down to identifying your attack surface, protecting against risks, detecting active threats, responding when threats appear and recovering effectively from incidents. CSF 2 also expects organizations to tie all of these functions together through a coherent governance policy, but as we mentioned, the idea of governance already existed in CSF 1.1. It just wasn’t spelled out as a standalone function.
When it comes to meeting CSF 2 requirements, Cyberint can help.
| Function | How Cyberint Aligns |
|---|---|
| Govern | Reporting and creating a policy is based on risk assessment. Cyberint gives you a risk score to enable you to see how stringent your plan needs to be. Cyberint also allows you to compare yourselves to other organizations of similar size. |
| Identify | Cyberint is key here in identifying all digital assets. Using publicly-available data, like DNS records, WHOIS data, and SSL certificates, Cyberint’s Attack Surface Management module is able to map out an organization’s external attack surface. All discovered assets are checked for common security issues. The categories of assets detected are: IP addresses, domains, subdomains, cloud storage, and organizations (i.e. trademarked brands). Cloud based assets we discover are S3 buckets, Google cloud storage, Azure data lakes, Azure storage, AWS accounts & more. These are the types of security issues we identify: ● Certificate Authority issues ● Compromised Credentials ● Email Security issues ● Exploitable Ports ● Exposed Cloud Storage ● Exposed Web Interfaces ● Hijackable Subdomains ● Mail Servers In Blocklist ● SSL/TLS issues With Cyberint’s automation, we can precisely determine which assets are part of your organization’s external IT infrastructure. Moreover, we offer automated validation and scoping based on your preferred confidence level (e.g. 80% or 90%). This reduces the time and effort involved in scoping and asset validation, resulting in a seamless single flow that occurs automatically from discovery to alerting. |
| Protect | Each issue’s risk score is calculated according to a sophisticated algorithm and depends on a number of factors including the type of issue found and the asset that is related to the issue. Attack surface issues are also prioritized further by threat intelligence. For example, if Cyberint detects that an organization’s industry is being targeted with a certain attack against a certain CVE that asset risk issue is prioritized. |
| Detect | – |
| Respond | Cyberint’s managed service offers in depth investigations |
| Recover | – |
With Cyberint, you can easily map your attack surface – including not just conventional assets, like servers, but also domain names, brand identities, social media profiles and any other type of resource threat actors might target – to identify risks.
Cyberint also actively protects digital assets against all manner of attacks – from domain name typosquatting, to social media impersonation, to attempts to sell credentials on the Dark Web and beyond.
And when you need to respond to a threat, we offer takedown services to remove it quickly.
Learn more by requesting a Cyberint demo.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start