


The first step in combating retail fraud is learning which forms it takes. That’s easy enough, because there are two main types of retail and eCommerce fraud today:
The second step in stopping retail fraud from harming your business is to understand how each type of fraud works, then implement a strategy to protect against it. Read on for guidance as we unpack how each type of retail fraud works – along with a “bonus” section that details another form that eCommerce fraud occasionally takes.
Let’s begin by discussing the most common type of retail fraud – websites that mimic a company’s actual site.
These sites are typically defined by several key characteristics:
What makes the sites fraudulent is that they don’t actually ship the products they claim to offer. Instead, they deliver packages filled with clutter or junk, often following delivery periods that take many weeks. By the time the delivery arrives and the victims realize what has happened, it’s too late for them to open a claim with their credit card provider, since disputes typically must be filed within thirty days.
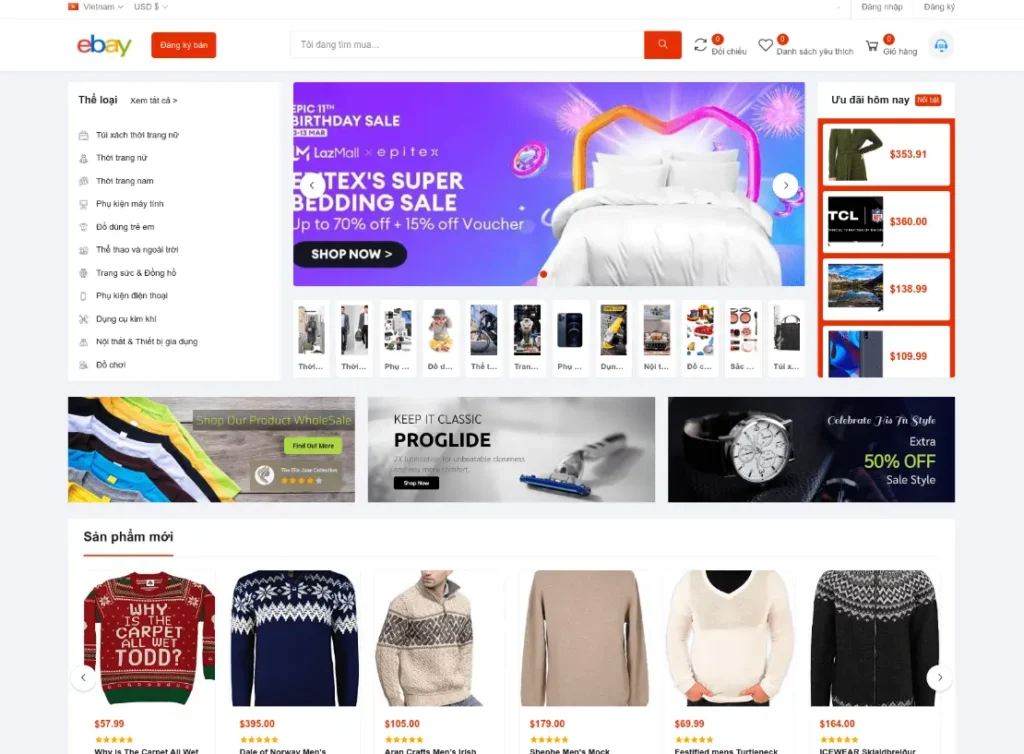
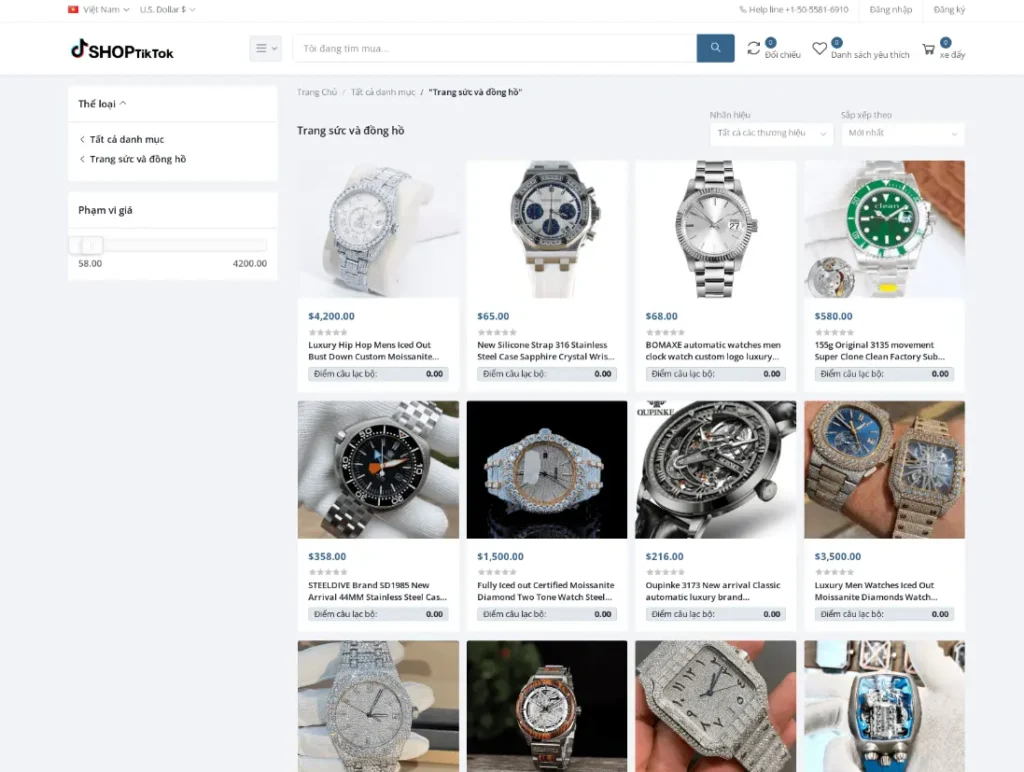
In addition to harming customers who fall victim to fraudulent sites, these operations are also bad for retailers in two ways. First, they may reduce a retailer’s revenue because shoppers spend money on fake sites – where, again, they may be enticed by lower prices.
Second, retailers’ brands can suffer harm if shoppers who place orders on fraud sites associate the fraud with the eCommerce business that was impersonated. Some victims may never realize that they bought something on a fraudulent site; instead, they’ll think they used a legitimate one, and that it’s the legitimate retailer’s fault that they never received the items they paid for.
“Impersonation is a security challenge that damages brand reputation and creates financial risks for organisations and all of their stakeholders,” as the World Trademark Review notes.”
Fraudulent sites like these are essentially a form of phishing, but with a unique twist: Instead of tricking victims into handing over sensitive data, the attackers trick them into making payments in exchange for junk.
Notably, in most cases these sites don’t steal credit card information. Instead, their goal is to enable ongoing exfiltration of funds by tricking customers into paying for products that they never receive. If they stole credit card numbers, credit card companies would simply takedown the site within a few days in most cases. But by running a fraudulent retail site that uses a third-party payment processor, threat actors can remain in business for months. Credit companies usually have a 28 day limit for reporting fraudulent transactions, so by the time the empty package arrives it is too late to report it. These sites often remain live for a significant period of time – that is of course unless the company whose brand they are impersonating takes down their site first.
Fraudulent sites rely on two main methods for drawing in victims.
1. One is malvertising, which means placing ads designed to attract traffic to their sites. If a victim with an interest in a legitimate brand clicks a malvertisement, he or she is directed to the fraudulent site.
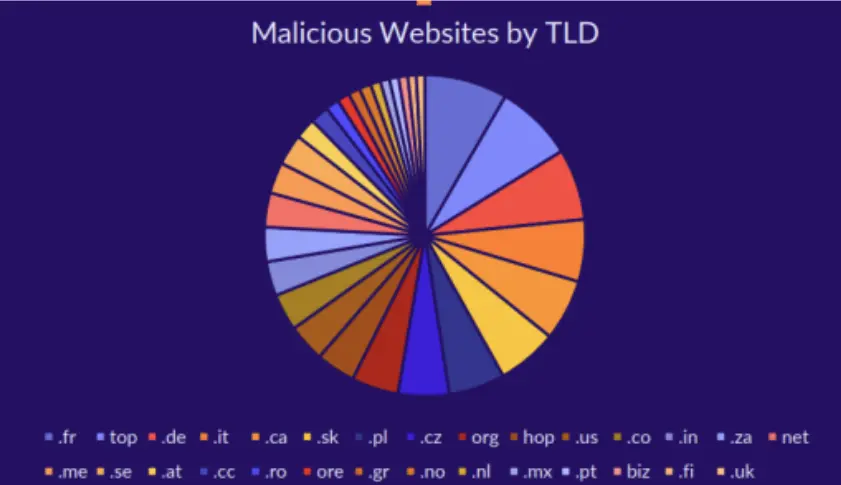
Interestingly, Cyberint’s Threat Intelligence Team found in a 2022 analysis that the malvertising ads are geolocation-specific in many cases and correspond to the specific TLD that the malicious website is hosted on. We analyzed all TLDs used in a campaign concluded that aside from .com, the TLD that hosts the vast majority of the domains, the most prominent TLDs are .fr (France), .de (Germany), .it (Italy), .ca (Canada), .sk (Slovakia), .pl (Poland), .cz (Czech Republic), .us (United States), .co (Colombia) and .in (India). The following pie chart provides a breakdown of these domains based on our study:
2. The second main technique for attracting victims is via social engineering. Threat actors create fake profiles on social media sites. In each profile’s “about” section, they place a link to their fraudulent site. They may also post links in their feeds or run malicious social media ads from that profile.
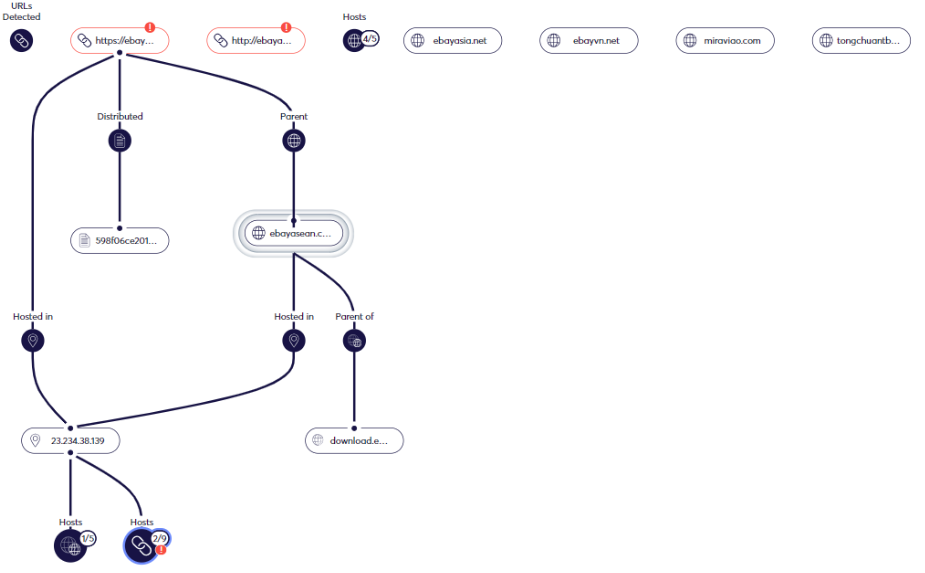
Fraudulent retail sites often appear in groups. Threat actors create multiple fraud sites using the same infrastructure, IP address and hosting provider. That means that once you know the domain, you can look up its IP address. With that, you can look at the passive DNS of the IP and find other domains associated with it. At Cyberint, we’ve experienced cases where we located up to twenty fake sites based on one that was reported to us, allowing us to take down multiple fraud sites in one fell swoop.
This is valuable because as Dark Reading notes, “Fraudsters are getting more sophisticated about how they set up and make adjustments to brand impersonation scam sites.” The faster security researchers can find clusters of fraudulent sites, the faster they can take them down, no matter how convincing the content on the sites may seem.
A less common type of eCommerce fraud – but one that can cause serious harm nonetheless – is attacks involving knock-off products.
The goal of threat actors in this case is to offer products that resemble ones a company actually sells, but at lower prices. The products are of much lower quality.
This attack harms retailers by depriving them of the revenue they’d earn if customers bought their legitimate products instead of fake ones. In addition, it can harm a company’s reputation because people may receive the fake products, realize they are of low quality and then hold the legitimate brand responsible because they don’t know the products are fraudulent.
Malvertising is the most common technique for threat actors who sell fake products. They run ads that direct shoppers to sales channels that they control.
The best strategy for taking down fraudulent content depends on which type of fraud you’re dealing with.
In the case of fake sites, a cybersecurity company like Cyberint can work with hosting providers or other platform owners to take down fraudulent sites. It’s easy to prove that the sites violate terms of service because they are impersonating someone else’s brand.
Blocking fake product sales is harder because businesses must first prove to hosting providers that the products are fake. But this can be done; it just requires a little extra preparation. When we take down this type of content at Cyberint, we usually obtain a letter from our clients attesting that the products for sale are fraudulent, as well as any additional documentation we are able to collect to prove quickly that the offending content should be taken down.
Before closing, let’s discuss a third type of retail fraud that is not as common, but could result in major harm: Attacks where threat actors target the employees of a retailer with phishing content. Their goal is to obtain access credentials to retailers’ software, creating a backdoor into the organization.
This attack often requires more time and effort to carry out because threat actors need to identify specific groups of employees and create phishing sites tailored to them. But it can be done. Imagine, for example, that threat actors create a site that impersonates a company’s HR portal. If employees attempt to log into the site, they may give away their actual usernames and passwords to the attackers.
Although attacks like these are not very frequent, you should factor them into your attack surface defense strategy.
No matter which type of retail or eCommere fraud you face, Cyberint has the expertise to stop the attack quickly. We offer a comprehensive set of phishing and brand impersonation takedown services to help companies remove malicious content and block fake sales channels as quickly as possible – often, within a matter of hours. In addition, our Deep and Dark Web intelligence helps companies anticipate threat actors’ plans and gain early insight into attacks against retailers.
To learn more about how Cyberint keeps brands safe, request a demo.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


