


You trust your vendors enough to do business with them, but would you trust them with your cybersecurity? The reality is, you already do.
The chains of trust which make doing business possible can also be the conveyor belts of malwares, ransomware, rootkits, and other activities which form a part of advanced persistent threats (APTs). This is true especially when it comes to the vendors who are “tightly integrated” into your systems or your business processes. This is why in today’s integrated environment, vendor risk management is crucial for your own cybersecurity.
Those who don’t lock the doors to their house are very unlikely to keep their valuables safe. And because today’s business and application environments are integrated, your security depends in large on your vendors locking their doors and using safes, because they are more than neighbors, they’re your roommates.
When your website loads, it also dynamically loads the code of vendors you work with. If you think about the functionality of your digital assets, they are heavily dependent on 3rd party tools. From payment platform to CRMs and advertising plugins, they all expose you to potential risk. A risk which must be managed.
3rd party software providers act as a predominant attack vector that has recently been in the news. The NotPetya wiper attack of last year is an excellent example of this. Attackers had compromised the servers of MEDoc (a firm whose tax software is widely used in Ukraine) which distributed its users software updates. The attackers then managed to insert their malicious code into a package disguised as a software update, which was downloaded and executed. The compromise of this software company led directly to an attack on the companies that used their software.
The first step to managing that risk is quantifying it; you can’t manage your weight without stepping onto a scale. Here at CyberInt, we’ve developed Cyberscore, a unique cybersecurity scale to help our customers determine the extent of their vendor cybersecurity risk. Simply put, Cyberscore is a platform that validates vendor risk management by continuously scanning your vendors’ cyber posture.
Cyberscore scans your vendor’s cyber posture from the outside, finding any open ports, IPs that are connected to a botnet, or any other indication of compromise that can be validated from the outside. 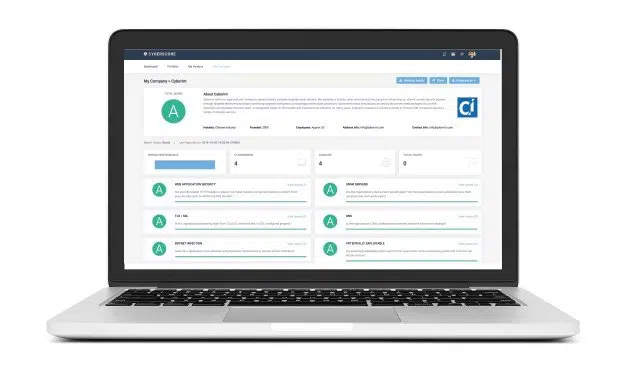
In total, Cyberscore is comprised of the following 10 categories:
Web Application Security: Security-related HTTP headers affecting all traffic to and from the web app server, and their configurations to validate their effectiveness in protecting you from a man in the middle (MITM) and cross site scripting (XSS) attacks.
TLS/SSL Security: Validates that your vendor is protected from all known TLS/SSL vulnerabilities and making sure these are configured correctly. Including validating that all SSL related libraries are patched to the most current version.
Botnet Infections: Does your vendor have detection and prevention mechanisms to prevent against botnet infections.
Email Security: Is your vendor protected from email spoofing and phishing attacks? Are adequate SPF and DKIM configurations in place that make it harder for attackers to forge your vendors’ domain as a sender address.
Unsafe File Sharing: Validating that peer-to-peer communication to malware-infected file sharing communities are being monitored and blocked.
Spam Servers: Are any of your vendors’ mail servers spreading spam? Have any of their email addresses been compromised and sending spam?
DNS: Are your vendors’ DNS servers configured correctly to prevent the leakage of sensitive information? And, are they configured in a way that prevents those servers from being used in a DNS amplification attack?
Ports: Continuously validate that your vendor closes all unnecessary ports to minimize its attack surface.
Compromised Credentials: Checking for any user or administrator credentials belonging to the vendor which are shared on the Dark Web or other websites and repositories.
Social Media: To what lengths do your vendors go in order to protect themselves from malicious activities such as malware, and phishing messages delivered through social media.
Vendor risk management is a crucial part of your cybersecurity infrastructure because your attack surface extends to everyone you do business with. Supplier security audits are key to quantifying, minimizing, and mitigating vendor cybersecurity risk.
Interested in assessing your vendor risks? Contact us to learn more.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


