



Daniel is a seasoned cybersecurity product marketing professional with experience in cryptographic solutions, attack surface management, threat intelligence, and more.
Originally Published September 3rd 2023. Updated April 7th 2024.
The Common Vulnerability Scoring System (CVSS) is used to evaluate and communicate the technical severity of software, hardware and firmware vulnerabilities. While CVSS has been around for nearly 2 decades and now stands as an industry standard tool for scoring the severity of a vulnerability, the framework still has its limitations.
To mitigate some of these challenges and improve the efficacy of the system, an updated version of CVSS was released in November 2023. This blog post will discuss some of the issues identified in CVSS v3 and outline the changes planned for CVSS 4.0.
The Common Vulnerability Scoring System (CVSS) was developed by the Forum of Incident Response and Security Teams (FIRST), a non-profit organization founded in 1990 that “aspires to bring together incident response and security teams from every country across the world to ensure a safe internet for all.”
Prior to the CVSS, many different people—software vendors, independent security researchers, cybersecurity professionals at enterprise organizations, etc.—were each using their own homemade scoring systems to define the severity of a vulnerability. These systems were not compatible, which made it difficult for people to collaborate and exchange knowledge about documented CVEs, as they lacked a shared scoring system. The first version of the CVSS was released in February 2005 to overcome these obstacles.
Over the years, new versions of the CVSS were introduced to improve upon previous versions:
Now, CVSS 4.0 was actively tested by a Special Interest Group (SIG) and officially published on November 1, 2023, according to the FIRST website.
Before we dive into the details of CVSS 4.0, let’s take a moment to understand exactly how CVSS is designed today.
A CVSS score is made up of three metric groups:
There are a few differences between the Base group and the other two metric groups. First of all, the Base Metric Group is required to produce a CVSS score, but the other two metric groups are recommended but not mandatory.
Second, the Base metrics are typically defined by the person or people who discovered the vulnerability—e.g. the vendor that produces a software product or a team of independent security researchers. The Temporal and Environmental metrics, on the other hand, are defined by the end-user organization.
As the name suggests, the Temporal metrics change over time and must be updated to reflect the current state of a specific CVE. For this reason, the Temporal inputs must be set by the end-user organization when evaluating the severity of a vulnerability. Environmental metrics must also be entered by the end-user organization, as nobody else can define how critical a particular system or asset is within a given environment.
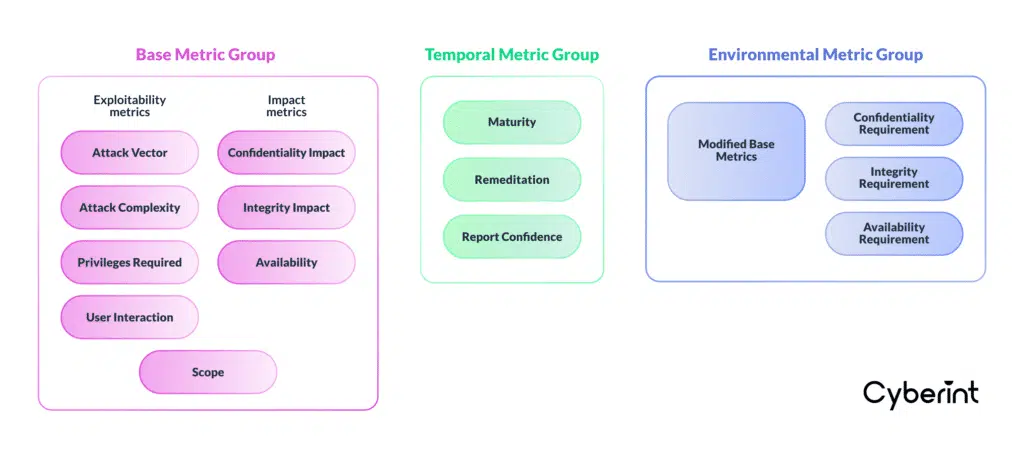
The Base Metric Group comprises two categories—the Exploitability sub-score and the Impact sub-score—plus a third variable known as Scope.
The Exploitability sub-score is derived from these four metrics:
The Impact sub-score is a function of the following three metrics:
Experienced Information Security professionals will recognize the three components in the Impact sub-score as the CIA triad.
Lastly, the Base Metric Group considers the scope of a vulnerability. This score reflects the impact of exploitation beyond the scope of the vulnerable software, hardware, or firmware. For example, if successful exploitation of a vulnerability in a web server software gives the attacker access to, say, a database that interacts with a web application running on the web server, then the sScope of the vulnerability is greater than the particular system on which the vulnerability exists.
As noted above, Temporal metrics are not required for generating a CVSS score, though they are recommended. Temporal metrics must be entered by the end-user organization when calculating a CVSS score.
Just like Temporal metrics, Environmental metrics are recommended but not essential in generating a CVSS score and they must be defined by the end-user organization.
This dimension of a CVSS score takes into account how severe the impact would be if a particular IT asset is compromised. Some assets may be of comparatively low importance, so the fallout is minimal if an attacker manages to gain full control of the asset. Other assets are business-critical and the organization may incur substantial financial damages if the asset is compromised.
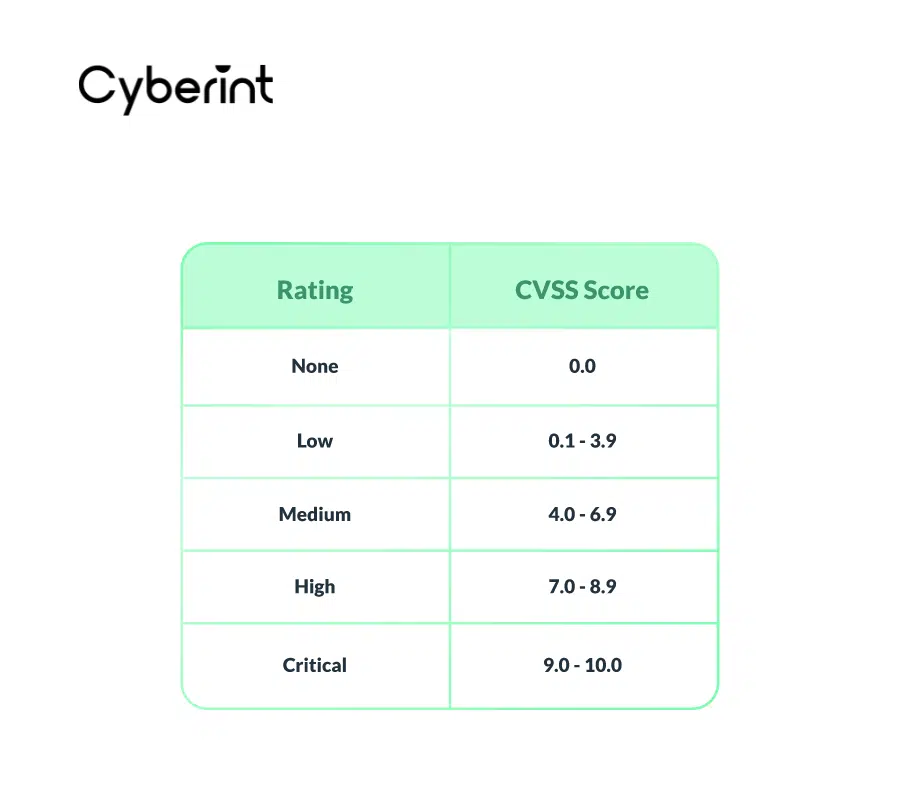
With all of the metrics above defined, the CVSS produces a base score on a scale from 0 to 10. After the quantitative score is given to a CVE, a qualitative label is assigned to make it easy to quickly communicate and understand the severity of a particular vulnerability.
There are a few major challenges with CVSS as it stands today. First and foremost, CVSS measures the technical severity of a vulnerability, not risk. This may seem like a minor point but, in fact, it is extremely important to make this distinction. In the FIRST organization’s own words, CVSS produces a score that measures “the intrinsic characteristics of a vulnerability which are constant over time and across user environments.”
Recall that only the Base metrics components of CVSS are required to generate a score. The Base metrics are also the only part of CVSS that can be completed by any qualified professional (rather than the end-user organization that is trying to protect their networks, systems, and data).
For these reasons, the organizations that maintain a public repository of documented vulnerabilities—e.g. the NIST National Vulnerability Database (NVD) or the MITRE Corporations CVE program—use CVSS to assign Base scores for every new vulnerability. All too often, the CVSS Base metrics score provided in these public databases is mistaken for an objective risk score.
Moreover, because different people will use the CVSS in different ways and assign different scores or labels, the same vulnerability can be given inconsistent Base scores. Take CVE-2022-23720 for example:
The vendor, Ping Identity Corporation, assigned the CVE a base score of 7.5 while the NIST team, gave it an 8.2. This may seem like a minor difference but it demonstrates how the subjective nature of CVSS can lead to inconsistencies.
The FIRST team notes several other Challenges and Critique of CVSS v3.1 in a presentation introducing CVSS v4.0:
All of these limitations were identified as areas for improvement with the new CVSS v4.
The initial draft of the CVSS 4.0 specification document was released on June 8, 2023 for review and comments from the information security community. The comment period closed on July 31, 2023, with FIRST aiming to address feedback and make revisions by August 31, 2023. The target date for official publication of CVSS v4 is October 1, 2023.
While it is not yet finalized, the CVSS 4.0 specification document outlines a number of major changes to the framework. Here is an overview of the planned modifications and enhancements.
One of the major adjustments coming in CVSS v4 is to the nomenclature of CVSS scores. To reinforce the concept that a Base score is not a complete assessment of a vulnerability’s severity, the following terms will be implemented:
In other words, there will no longer be a single name for a CVSS score. Instead, there will be a specific term for the score indicating which metric groups were taken into account in generating that score.
Another major change coming in CVSS 4.0 is the additional applicability to OT environments, industrial control systems, and IoT devices, such as medical devices. The increased applicability comes primarily from new Safety metrics, which we will discuss more below.
As it was in CVSS v3.1, the Base Metric Group in CVSS v4 comprises two categories—the Exploitability sub-score and the Impact sub-score. There have been changes to both of these metric subcategories.
The Exploitability sub-score now has a 5th metric: Attack Requirements. This
The Impact sub-score now contains three new metrics to indicate the impact to additional IT systems if/when a specific vulnerability is exploited. In sum, the Impact metric group includes:
Since the Impact Metric Group now covers the effect on both the vulnerable system itself as well as subsequent systems, there is no longer a need for the Scope metric. Thus, Scope was removed entirely from the CVSS.
Lastly, the User Interaction metric was changed from a binary Yes or No to a more granular approach, which includes None (no user interaction required), Passive (some indirect user interaction required), and Active (direct user interaction required).
The Temporal Metric Group was renamed to the Threat Metric Group. This metric has four options:
Two metrics previously included in the Temporal Metric Group of CVSS 3.1 — Remediation Level and Report Confidence—have both been retired. They will not be included in CVSS 4.0.
Just as in CVSS 3.1, the Environmental Metric Group in CVSS 4.0 must be set by the end-user organization.
The main adjustment to Environmental metrics in CVSS v4 is the addition of a safety metric to indicate the impact on the physical safety of human beings if the vulnerability is exploited. This metric is primarily useful for OT environments.
As before, the Environmental Metric Group in CVSS v4 also allows end-user organizations to override and replace Base metrics set by the person or persons who first detected the vulnerability.
A new metric group is added in CVSS 4.0: Supplemental metrics. They are as follows:
The Supplemental metrics are optional and they may not apply to every vulnerability.
As the renaming of the Temporal Metric Group to Threat Metric Group would suggest, the new CVSS 4.0 framework places greater emphasis on threat intelligence. This is true for several reasons.
To begin with, the threat landscape is constantly evolving. A known vulnerability may be relatively low risk one month, then represent a critical risk the next, all due to changes in threat actor behavior. A continuous source of real-time threat intel data is indispensable in evaluating the risk of a vulnerability.
Furthermore, without threat intelligence, it is impossible to know whether a specific vulnerability has ever been exploited in the wild, whether a public POC exists, or whether exploitation can be automated. These are all essential considerations in determining how to prioritize patch and remediation efforts.
Cyberint’s CVE Intel module is designed to provide impactful threat intelligence for each documented vulnerability. Using data collected from thousands of sources across the open, deep, and dark web, Cyberint can provide the following insights on each CVE:
All of these insights factor into the Cyberint score, which reflects the risk a CVE presents to an organization. The score helps organizations to understand the risk they face from outdated software in order to prioritize patch and remediation efforts, ensuring maximum efficiency of the resources dedicated to such efforts.
In the coming weeks, Cyberint will publish a second blog on CVSS 4.0 to discuss the need for threat intelligence in vulnerability scoring and prioritization in much greater detail. Stay tuned!
In the world of cybersecurity, there are no silver bullets. This is especially true when it comes to evaluating and quantifying cyber risk, particularly for the risk of a given vulnerability. These challenges exist for all InfoSec professionals, regardless of the size of their organization, their industry, or the exact configurations of their environment.
The upcoming CVSS v4 framework will serve as a useful tool for cybersecurity experts around the globe, providing several major enhancements over the current v3.1. While challenges will of course still exist, CVSS 4.0 should be adopted by vulnerability and patch management leaders as soon as its available.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


