The bigger your business, often the larger the size of the attack surface you need to secure. That’s why multi-national enterprises typically face a different set of cyber security priorities than SMBs.
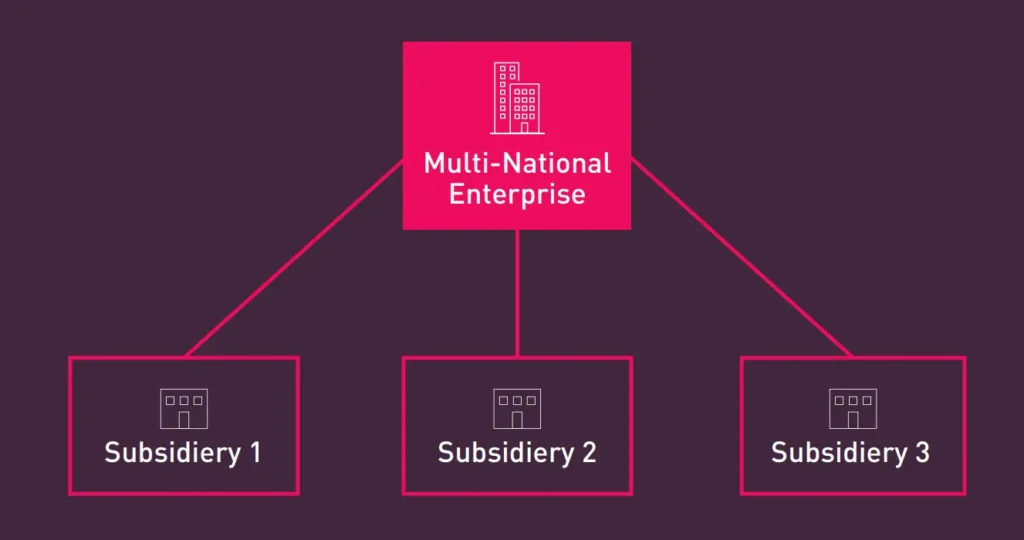
Here’s another, less often discussed factor that can complicate security and risk management: Whether your company is a multiple entity or a single entity. Corporations that operate multiple subsidiaries or branches, typically spread across the globe – must contend not just with the standard cyber security challenges that affect any large business, but also with unique cyber security risks and threats.
These corporations have a more complex attack surface than other types of businesses, and they must address multi-tenant security challenges that don’t apply in most other contexts. In addition, multi-national enterprises also face unique brand protection risks that stem from the complex, multi-faceted nature of their operations.
That’s why multi-national enterprise cyber security is a unique discipline that requires unique tools and strategies. Keep reading for details as we unpack each of the key security challenges that these organizations face, along with tips on how cyber security leaders can implement an effective multi-tenant security architecture that protects sprawling multi-national businesses.

One approach is to create just one team for the entire company and have it manage security for all subsidiaries. But it comes with 2 big challenges:
Overstretched personnel and lack of focus people in the subsidiaries. The many teams approach isn’t smooth sailing either.
Representatives of each subsidiary’s cybersecurity teams rarely get together in the same room to set policies, let alone communicate about the conflicts that each part of the organization may face in its ability to adhere to a unified security strategy.
From data exposure and asset overlap & misplacement and more.
Now there is not just one brand 2 protect but many, and not one logo to protect but many. There is also the issue of taking down another subsidiary’s asset.
Conglomerates tend to buy smaller companies on a frequent basis. These companies may not have the same level of cyber security and each acquisition increases the attack surface.

Conquering multi-national enterprises cyber security challenges with Cyberint, a Check Point Company.
We’ve been supporting the cyber security needs of global of multi-national enterprises across a range of industries – from finance, to retail, to agriculture and beyond – for years. We know what it takes to manage the inherent complexities and protect them against external risk.
There are two basic ways to organize cyber security teams within a multi-national enterprises – and both come with steep tradeoffs. One approach is to create just one team for the entire company and have it manage security for all subsidiaries. This helps to centralize operations and visibility. It also ensures that there is a clear team to contact about security issues, no matter where they arise within the conglomerate or which assets they impact.
On the other hand, the “one team” approach leads to the following drawbacks:
Trying to have just one team manage cyber security for dozens of subsidiaries is a recipe for overworking and overstretching staff. They will inevitably miss some alerts and risks, and they may not be able to assign high priority to issues that merit it. This problem is exacerbated by the global cyber security talent shortage,
which means that even if the enterprise budgets enough money to hire sufficient staff, it may not actually be able to hire enough.
When one team oversees everything across dozens of subsidiaries, it becomes challenging to delegate “ownership” over specific risks and assets to specific people. In turn, it’s often unclear whom to contact about a certain type of issue within a particular subsidiary, or who will take the lead in responding to it.
In a bid to mitigate these challenges, many multi-national enterprises opt to create multiple cyber security teams, usually by creating a separate team for each subsidiary. This solves the challenges we just described, but it creates other problems – like lack of a unified security strategy and trouble mapping and defending the attack surface.
Let’s explore those issues by walking through additional cyber security challenges that multi-national enterprises face when they opt for a “many team” structure.
At a multi-national enterprise, each subsidiary often relies on its own cyber security team using its own tools and strategies. Rarely is there a centralized team that oversees cyber security across the entire business.
For this reason, the headquarters that oversees the company typically has limited visibility into the cyber security threats that its various subsidiaries face. Nor can it easily enforce a unified security strategy and set of policies based on Priority Intelligence Requirements (PIRs) that apply to the business as a whole. Representatives of each subsidiary’s cyber security teams rarely get together in the same room to set policies, let alone communicate about the conflicts that each part of the organization may face in its
ability to adhere to a unified security strategy.
This decentralized security architecture leads to several distinct challenges:
When each subsidiary manages cyber security in its own way, every branch ends up effectively operating like an independent business, at least as far as security is concerned. The result is little consistency across the organization with regard to the way teams prioritize and respond to threats.
“Lack of resources, siloed operations and poor tool implementation often prevent security and risk management (SRM) teams from detecting and responding to threats,” Gartner says. These challenges are especially acute in conglomerates due to the highly siloed nature of their cyber security operations.
If the multi-national enterprise appoints a CISO or other leader to oversee security across the company, having disparate teams within each subsidiary makes it challenging to apply policies consistently. When you have dozens of individual teams to oversee, it’s hard to ensure that they all act in concert, and that communication channels exist to keep local teams in sync with business-wide risk priorities.
In multi-national enterprises with an array of distinct security teams, it’s often not clear who owns what within each subsidiary, or whom to contact about a threat or risk. This is especially true in cases where each subsidiary’s security operations are divided into subsets – like cyber, brand protection and fraud protection.
The result is that centralized cyber security personnel have little idea whom to contact when they detect an issue that impacts a subsidiary.
Cyber security teams tend to be overstretched due to issues like the ongoing cyber security personnel shortage. As Dark Reading notes, there is a “significant cyber security talent shortage, with 225,200 more workers needed to fill nearly 470,000 job openings” in the United States alone.
This problem is compounded when each subsidiary relies on its own team because the business ends up with analysts who handle redundant responsibilities within each subsidiary – while at the same time, teams lack the overall personnel they need to address risks. Individual teams may end up ignoring or failing to respond quickly to alerts because they’re not able to use staff resources efficiently.

Multi-national enterprises face the challenge of having not just a large attack surface to secure, but also one that is uniquely complex in several ways.
Typically, each subsidiary in a multi-national enterprise uses its own vendors and tools, and these vendors and tools expose the subsidiary’s data to cyber risks. The parent company is on the hook when an exposure occurs, but the multi-faceted nature of the organization gives central IT leaders a limited ability to force subsidiaries to adhere to a uniform set of data management policies and procedures in order to minimize the risk of data leakage.
On top of this, in the event that a centralized security or compliance team does detect data security risks, passing the information onto the relevant subsidiary team to mitigate the issue is often a time-consuming and inefficient process. Centralized asset mapping and data monitoring tools can generate alerts, but they can’t guarantee that subsidiary teams will respond quickly.
When you have multiple tenants within your organization, automated asset discovery processes can end up misclassifying assets or duplicating assets because they detect the same asset in multiple tenant environments.
As a result, the business faces a steeper challenge in identifying which are the exact assets it needs to take note of and mapping its attack surface. It may also end up with attack surface mappings that contain inaccurate data until engineers update them manually to make clear which assets belong to which subsidiaries, and who manages each one.
This translates to greater difficulties in defining and securing all facets of the multi-national enterprise’s cyber security attack surface.
A related challenge is that the parent company may purchase an asset on behalf of a particular subsidiary – so although the asset appears to originate with the parent company, it doesn’t actually belong to it.
Often the HQ has a cyber security risk score that they are responsible for keeping low, but the issue is that their risk score is impacted by the subsidiaries risk score as it is all interconnected. But there are different heads and different policies, so there is a lack of control. All they can do is tell the other head, this is your score, please take care of it.
Understanding this level of detail requires a more nuanced approach to attack surface management (ASM) that allows multi-national enterprises to distinguish between different levels of asset ownership and define security policies accordingly.
Brand protection – which means protecting against misuse of a company’s brand names, logos, domains, social media accounts and other digital representations – is also especially challenging for multi-national enterprises in several unique ways.
Often, licenses are managed at the subsidiary level. This means that each branch of the parent company maintains its own Letters of Authorization to document its brand properties.
This makes brand protection challenging in cases where the parent company detects a brand threat, but lacks the documentation to prove that it actually owns the asset in question. In addition, brand protection rules can vary across countries, making uniform brand management even more difficult.

When businesses detect brand threats, they can request takedowns to mitigate them. But often one subsidiary will request a takedown without realizing that the domain/webpage/social media profile etc. belongs to the other subsidiary. This might lead to an incorrect takedown and the retrieval process can be lengthy. The subsidiaries must coordinate with each other, which is hard when each subsidiary operates in a silo.
Smaller subsidiaries sometimes lack a big digital footprint and are often easy targets for threat actors who want to damage their brands because they lack a prominent social media presence. As a result, malicious parties can do things like register fake Facebook or X accounts in the subsidiary’s name, complete with misappropriated logos and other branding elements. From there, attackers can communicate with the subsidiary’s clients and impersonate its employees.
This type of abuse affects the parent company because it directly impacts one of its brands. But it’s hard for the parent company to prevent because the parent organization doesn’t directly control the social media assets of its subsidiary.
Often, a multi-national enterprise must manage threats against not just its own brand name and logos, but also those of its subsidiaries. This can amount to thousands of individual logos and other assets to track across dozens of websites, social media channels and so on. In some cases, the parent company’s cyber security teams may not even know which brands actually belong to its subsidiaries.
In a large company with many branches, there are often many executives – one set for each subsidiary. This makes these enterprises attractive targets for threat actors who want to impersonate executives as part of phishing attacks.

As we mentioned, brand protection regulations and enforcement can vary between countries. An enterprise might purchase a brand in one country but not buy rights to it in other countries. This creates opportunities for threat actors to abuse the brand in those other countries and leave the parent company with little recourse because it doesn’t actually own the rights in those jurisdictions – although customers won’t know this, leading to negative sentiment against the business all the same.
Not only that but if a malicious site/page is set up in a different country it can be used in phishing attacks in the country where the actual subsidiary exists causing a multitude of problems.
Multi-national enterprises tend to buy smaller companies on a frequent basis. This practice also leads to unique cyber security challenges because each acquisition increases the parent company’s attack surface, while also making it difficult to enforce cyber security policies uniformly.
The fact that the companies that are acquired are sometimes startups or smaller businesses without mature IT or security teams makes the problem even worse because it brings organizations without strong cyber security hygiene into the parent company’s fold. And while due diligence processes during acquisition validate purchases from a business risk perspective, these checks don’t always extend to cyber risk.

How can multi-national enterprises navigate these challenges? In most cases, simplifying the structure of the organization itself is not an option. Instead, large, multi-faceted businesses must invest in strategies that allow them to manage risks and threats effectively despite their complex, inherently siloed structures.
The following security practices can help.
To bring consistency to cyber risk management, parent companies can define policies that apply to the organization as a whole, as well as sub-policies designed for the nuanced needs of different subsidiaries. This makes it possible to accommodate varying regional and local laws and compliance mandates while still maintaining a coherent cyber security strategy across the company.
Policies should include a Service Level Agreement (SLA) for responding to security alerts. This ensures that there is a clear guideline that each subsidiary’s IT team is expected to meet when handling threats and risks, along with consequences for taking longer. In turn, SLAs make subsidiaries more accountable to the parent company from a cyber security perspective.
When assessing risks, the parent company should have risk scores for itself. In addition, individual subsidiaries should have their own risk scores. This approach allows the entity as a whole to identify and manage risks appropriately, while also granting subsidiaries the flexibility to handle risks that are higher-priority for them. It avoids situations where subsidiaries fail to react to an important risk because it’s not a priority for the parent company.
Although it’s not always possible to consolidate cyber security teams and operations across the entire multi-national enterprise, some level of consolidation is often feasible. For example, the business could create one centralized team for each major area of cyber security operations – like threat intelligence, ASM and fraud management. Subsidiaries that have additional requirements can continue to operate their own teams,
but there won’t be as much redundancy or inefficiency as there would if every branch had its own set of security personnel.
Within each subsidiary there should be a focal person that the HQ cyber team can reach out to. This person can then quickly and easily either deal with the issue or redirect it to the right internal team. This helps clarify who is in charge of which issues and facilitates efficient management of risk.
Even with highly efficient team structures and processes, there is no substitute for regular meetings and communication. The various cyber security stakeholders in the conglomerate – including those who work at headquarters and representatives of subsidiary teams – should sync on a routine basis, perhaps once a month, in order to update each other, identify pain points and discuss opportunities to gain even more
efficiency.
Turning on multi-tenancy features in cyber security tools makes it easier to manage and distribute tasks, as well as to reduce chaos. Multi-tenant controls should be configured in a way that makes it clear which branch owns which assets and which threats it consequently needs to manage.
Multi-tenant architectures aren’t always ideal. They can increase complexity more than they add value in cases where most assets are shared. But in general, multi-tenancy helps streamline operations and increase attack surface visibility. Often teams will decide which asset belongs to which tenant and assign it to that tenant.
Another alternative that Cyberint, now a Check Point Company offers is asset groups, where you can group assets by a category under 1 tenant.
Instead of trying to mitigate all multi-national enterprises cyber security challenges at once, address them one-by-one. For example, focus on implementing consistent brand protection first, then move onto attack surface management, then threat intelligence. Or start with one brand and then add one at a time. Often there is not enough manpower to turn on everything at once, so start slow and increase.
Start with turning on the most crucial alerts, and reduce criticality needed to be alerted until you find what you can handle. This is a more feasible way to overhaul conglomerate security practices.
The above brings us to analysts, if the cyber team is only being alerted for the most critical issues, teams can have an analyst monitor and review all the incoming data to ensure nothing is missed. The inherent complexity of the multi-national enterprise attack surface means that automated ASM tools are likely to miss or misclassify assets.
To mitigate this risk, ensure that analysts review assets as they are discovered and reassign them as needed.
Analysts can also verify impersonation alerts. They can gather all relevant parties together in one meeting and guide them through delicate questioning on how they’re operating as a team together and who’s in charge of what. Although in a perfect world this process would be fully automated, in the real world it’s important to include a human in the loop, especially when contending with the complexity of a multi-national enterprise.
To reduce the risk of asset duplication, asset discovery can occur at the parent company level (this is only appropriate in some cases). From there, assets can be allocated to individual subsidiaries as needed, while headquarters continues to oversee the discovery process itself. This can be done under one tenant with asset grouping.
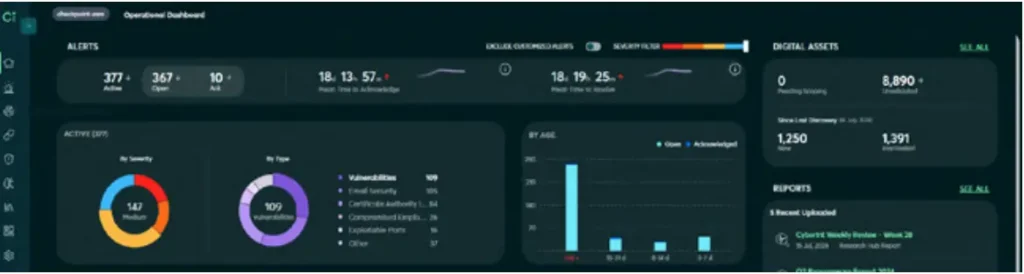
By having the Cyberint solution coupled with a Cyberint dedicated analyst the ADAMA SOC team ensures full assets and asset misconfiguration coverage across their large, global conglomerate
ADAMA’s security team is run out its central headquarters, overseeing numerous subsidiaries worldwide to ensure adherence to the company’s cyber security policies. To discover their assets across a large external attack surface and rapidly identify vulnerabilities, they rely on the Cyberint solution, now a part of Check Point.
ADAMA, a global crop protection leader, is now a member of the Syngenta Group, the world’s largest agricultural inputs company. The conglomerate helps farmers combat weeds, insects, and disease to feed the world. With a diverse portfolio of high-quality products and advanced R&D, manufacturing, and formulation facilities, ADAMA’s 8,000 employees serve farmers in over 100 countries, enhancing yields and providing effective solutions to control weeds, insects, and disease.
Overall Challenge they face: As a conglomerate they face several challenges including ensuring security policy is enforced in each of their subsidiaries, checking for vulnerabilities in each of their subsidiaries and speed of response.
CHALLENGES: Gaining visibility into all the company’s and its subsidiaries’ externally facing digital assets
Detecting vulnerabilities in those assets and remediating those vulnerabilities quickly
SOULTION: The Cyberint (now a Check Point Company) Solution, with the managed service component.
THE ISSUE: EXPOSED INTERNAL INFORMATION
One day, an issue was discovered using the Cyberint Solution augmented by ADAMA’s dedicated Cyberint analyst. ADAMA’s subsidiaries in India and Indonesia had unknowingly exposed internal information by using localized assets, separate from those monitored by the headquarters’ IT team. This misconfiguration led to the exposure of both company confidential information and employees’ personally identifiable information (PII).
Their Cyberint analyst identified that there were several misconfigurations in server access permissions. Cyberint’s managed service, enhanced by their expert analysts, ensured that all assets were covered, preventing any from slipping through the cracks. To address the issue, ADAMA’s IT team reached out directly to each subsidiary, instructing them to immediately remove the affected servers from the network. This proactive approach, supported by Cyberint’s robust asset management and analyst enhancements, ensured that all assets were covered, and no critical information was left exposed. By partnering with Cyberint, ADAMA successfully mitigated the risk of information. exposure and improved their overall asset management, showcasing the effectiveness of Cyberint’s comprehensive and analyst-enhanced solutions.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start