


Cyber threats against critical infrastructure – such as energy and transportation networks – remain pervasive as ever, with 2023 witnessing an astounding 420 million such attacks in total.
That’s the bad news. The good news is that critical infrastructure is set to become more secure, at least in the European Union, thanks to the NIS 2 Directive (also known as E.U. Directive 2022/2055).
Here’s what organizations that manage or depend on critical infrastructure need to know about NIS 2 and its implications for cybersecurity in the E.U. and beyond.
NIS 2, officially known as E.U. Directive 2022/2055, is legislation enacted by the European Union to help secure critical infrastructure. The law was passed on January 16, 2023, and an expanded version appeared in February 2024.
NIS 2 replaces NIS, an E.U. cybersecurity law introduced in 2016.
As Insight notes, “NIS2 is not just another piece of legislation.” It’s a “game-changer” that promises to enhance global cybersecurity in dramatic ways by encouraging a more collaborative, comprehensive approach to cyber hygiene and resilience.
At a high level, NIS 2 imposes three main requirements:
At a more granular level, NIS 2 requires organizations that operate critical infrastructure in the E.U. to implement a variety of measures in areas such as:
This is only a partial list of the main requirements of NIS 2. Note, too, that like many cybersecurity directives and compliance frameworks, NIS 2 establishes high-level objectives that organizations must meet, but it leaves it to the organizations to determine how best to meet them.
For example, while NIS 2 requires adequate network security measures, it doesn’t specify exactly how affected organizations need to design and monitor their networks. Those are decisions that businesses need to make for themselves based on the types of resources they operate and the threats they face.
NIS 2 affects any organization involved in the operation of critical infrastructure, such as infrastructure that supports oil or gas, transportation, water, healthcare or telecommunications. The directive also applies to digital service providers, such as network operators, who provide essential services.
In general, the directive applies to organizations with at least 250 employees. However, E.U. member states have the option of deeming smaller companies subject to NIS 2 if they believe those organizations operate infrastructure that should be covered by the requirements.
Importantly, NIS 2 applies not just to organizations that are based in the E.U., but also to non-E.U. entities that help to operate critical infrastructure inside the E.U. This means that if your company is headquartered in, say, North America, but it runs or manages critical infrastructure in the European Union, the NIS 2 requirements apply to you.
NIS 2 classifies organizations into two groups – “essential” and “important” – based on the level of criticality of the infrastructure they operate. Both groups face a variety of cybersecurity and reporting requirements, but the rules are somewhat stricter (and the maximum allowable fines are higher) for “essential” entities.
As noted above, NIS 2 was enacted in January 2023, but its implementation will be gradual. Here are the key deadlines associated with NIS 2:
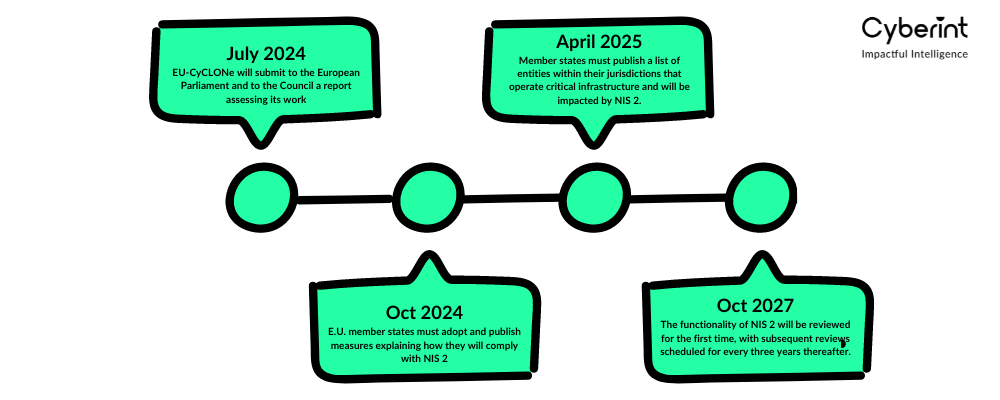
Because of the gradual implementation timeline, organizations involved in the management of critical infrastructure have a bit of time to prepare for the new requirements. But they should start that process now, since overhauling cybersecurity practices to support NIS 2 is no small feat.
Impacted organizations that fail to comply with NIS 2 face the possibility of steep fines. The exact amount varies depending on company size, as well as the extent to which the infrastructure that the company operates is deemed critical.
That said, basic fine guidelines include:
Beyond the direct financial impact of fines, businesses that violate NIS 2 may also face lawsuits, reputational damage, temporary managerial bans, the appointment of a monitoring officer and additional reporting requirements. In severe cases, criminal sanctions are permissible for NIS 2 violations.
As noted above, NIS 2 replaces NIS, an older cybersecurity directive. The main changes in NIS 2 vs. NIS include:
In a variety of ways, Cyberint directly helps organizations prepare for and meet NIS 2 mandates.
|
Area of NIS 2 focus |
How Cyberint helps |
|
Risk management |
Threat intelligence and attack surface management identify, assess and prioritize relevant risks |
|
Supply chain security |
Track risks in digital supply chains and detect breaches in real-time |
|
Threat intelligence actionability |
Contextualized alerts with accurate risk scoring simplify prioritization and minimize MTTR |
|
Incident reporting |
Demonstrate due diligence in tracking threats with Cyberint threat intelligence. Discover incidents quickly and obtain the context needed to report the incident effectively. |
One of the key focuses of NIS 2 is requiring organizations to identify the level of risk they face. This means understanding which types of attacks they may encounter, where their vulnerabilities may lie, what their digital supply chains look like and so on.
As MTI notes, comprehensive risk identification and assessment is important because it has become “a common mistake…to assume that cybersecurity risks always relate directly to the organisation’s systems or infrastructure. In fact, as organisations have become more digital, risks have grown in number and scope, many of which occur beyond the organisation itself.”
Cyberint delivers a range of capabilities that help businesses to assess risks, including:
In addition, the mere fact of being able to demonstrate that you’ve documented and reported relevant threats thanks to comprehensive threat intelligence reporting capabilities from a vendor like Cyberint will go far toward achieving NIS 2 compliance.
With these capabilities, organizations impacted by NIS 2 can effectively evaluate their risks, then implement protections to manage them.
Cyberint was recognized as the “Company of the Year” in the Global External Risk Mitigation & Management (ERMM) industry by Frost and Sullivan. Click HERE to get the full report.
As noted above, NIS 2 requires entities to manage risks not just within their own IT estates, but also within their digital supply chains.
They can do this using Cyberint’s Supply Chain Intelligence Module, which continuously discovers a business’s vendors and technologies, monitors and evaluates those 3rd parties for exposures, and generates alerts about third-party breaches in near real-time.
Supply chain intelligence makes it possible to leverage automation to discover the third-party technologies in use across your environment, as well as the third-party vendors and suppliers that provide those technologies. Organizations also gain powerful reporting features so they can inform stakeholders about relevant supply chain risks.
Assessing threats and risks is one thing. Getting your team to take action against them is another – but it’s an essential step under NIS 2, which requires not just monitoring and reporting but also effective response capabilities.
With Cyberint Threat Intelligence, organizations receive actionable guidance about threats that affect all facets of their digital presence, allowing them to react quickly and efficiently. Cyberint threat intelligence reports provide the essential context and risk assessments that organizations need to determine how serious a threat is and what it will take to mitigate it with minimal MTTR.
Disclosing and reporting about breaches is another key component of NIS 2. Here, Cyberint helps by providing incident detection and response capabilities, ensuring organizations are continuously aware of attacks against them. For instance, Cyberint quickly detects leaked employee and customer credentials, leaked source code and more. This allows for quick remediation and incident reporting. These measures help to demonstrate due diligence and avoid NIS 2 sanctions.
Cyberint reports also have the context needed to produce detailed incident reports.
Incident response also requires other capabilities that aren’t a focus of Cyberint, like the coordination of cybersecurity operations following a breach. But we deliver the actionable threat intelligence you need to get ahead of risks and report them as necessary under NIS 2 mandates.
Cyberint possesses key certifications necessary to drive effective cybersecurity outcomes for customers facing strict compliance requirements, including:
Exactly how the new directive impacts your particular company depends on a variety of factors. Nonetheless, virtually every business affected by NIS 2 can benefit from the capabilities that Cyberint delivers for identifying, assessing and reporting about threats.
As a comprehensive platform for external cyber risk management that seamlessly unifies cyber threat intelligence, Dark Web monitoring, attack surface management, brand protection and third-party risk management, Cyberint provides the complete set of capabilities necessary to conquer NIS 2 compliance challenges.
Learn more by requesting a demo.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


