



Itai Dahari is a cybersecurity professional residing in Tel Aviv. Itai's journey with various roles and positions has led him to launch a career in the cybersecurity realm. Alongside his role as a CTI Analyst on Anastasia Plotkin’s Americas Team at Cyberint, he finds joy in music and sports.
Insider threats pose a substantial risk, stemming from the potential misuse of access granted to employees, contractors, and third-party vendors. These threats, which can be both intentional and accidental, threaten the security of sensitive data and can significantly impact an organization’s financial stability, reputation, and operational efficiency.
The motivations behind these threats are varied and complex, ranging from financial incentives and personal grievances to ideological beliefs and external coercion. Each type of motive necessitates a tailored approach to detection and prevention, emphasizing the need for a nuanced understanding of the human elements involved in security breaches.
To effectively mitigate these risks, institutions must implement comprehensive security measures. This includes enforcing strict access controls based on the principle of least privilege, deploying sophisticated monitoring tools to detect unusual access patterns or data movements, and conducting regular security audits to identify and rectify vulnerabilities.
Additionally, promoting a culture of security awareness through regular training sessions and encouraging ethical behavior are crucial. These efforts help to foster a secure and transparent work environment where employees are aware of the risks and are motivated to act responsibly, thereby significantly reducing the likelihood of insider threats.
Insider threats arise from the actions of individuals associated with an organization, such as employees, contractors, or third-party vendors, who misuse their authorized access to the organization’s systems and data. These threats can be intentional or accidental, but they pose a risk to the security of sensitive information.
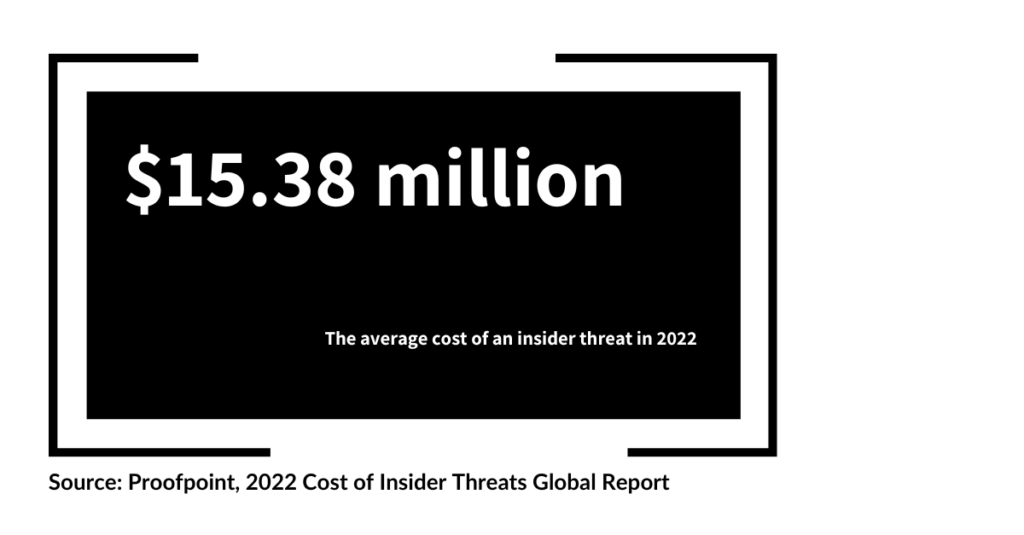
The consequences of insider threats are multifaceted, affecting an organization’s financial health, reputation, and operational capabilities. For instance, if an insider intentionally leaks confidential data, it could lead to substantial financial penalties, erode customer trust, and interrupt normal business activities.
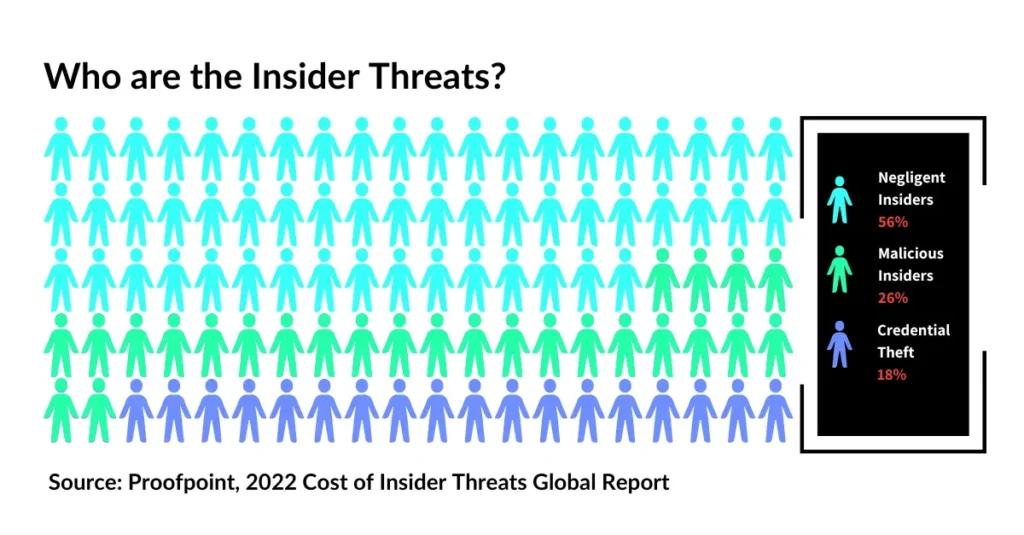
Insider threats stem from diverse motivations, each adding layers of complexity to the security challenges faced by institutions. The motives behind insider threats are varied and can be driven by various personal, financial, and psychological factors. Understanding these motives is crucial for implementing effective security measures. Here are some common motives:
These examples illustrate the complexity of insider threats and their varied motives, underlining the importance of tailored security measures that address the technical aspects of data protection and human factors. Each type of insider threat requires a nuanced approach to detection and mitigation, emphasizing the need for comprehensive security strategies that include robust monitoring, employee training, and fostering a security-conscious organizational culture.
About: This threat occurs when employees or contractors misuse their legitimate access rights for unauthorized purposes. Such misuse can include accessing confidential data beyond the scope of their job requirements, modifying or deleting sensitive information, or facilitating external breaches through insider collaboration. The risk is elevated in roles with extensive access privileges, making it critical for organizations to implement the principle of least privilege and maintain strict access controls.
Example Case: At Wells Fargo, employees created millions of unauthorized accounts to meet sales targets, leading to regulatory fines and reputational damage.
Source: Consumer Financial Protection Bureau
About: Insiders may collaborate with external attackers, providing them with access credentials or sensitive information, which facilitates broader security breaches.
Example Case: In the Carbanak APT, insiders at over 100 banks across 30 countries facilitated the installation of malware. This insider assistance enabled the group to steal approximately $1 billion by manipulating banking systems.
Source: Kaspersky’s Carbanak APT description
About: The shift to remote work has expanded organizational perimeters, often weakening the security controls that are more easily enforceable in traditional office environments. Insiders might exploit these vulnerabilities to access and exfiltrate sensitive data from less secure networks or inadvertently expose systems to cyber threats through inadequate home security measures.
Example Case: A report named ‘RDP Access Remains Cheap and Easy’ explains the current RDP sales landscape.
Source: BankInfoSecurity
About: With the adoption of advanced technologies like artificial intelligence and machine learning, insiders may manipulate these tools to carry out unauthorized activities or enhance their ability to access and exfiltrate data. The complexity and developing understanding of these technologies can allow such activities to go unnoticed, often compounded by the challenge of distinguishing between legitimate and malicious use.
Example Case: A sophisticated cyberattack targeted GitHub developers through a complex supply chain attack. Malicious actors exploited automated systems to distribute compromised software packages, leveraging GitHub’s infrastructure to push updates that included malicious code. This allowed the attackers to access sensitive data and further infiltrate systems that used these compromised packages.
Source: Dark Reading
About: This refers to insiders’ unauthorized data transfer outside the organization. Such actions can be motivated by financial gain, revenge, or espionage, often involving sensitive personal or corporate information. Data exfiltration can be facilitated through physical means (like USB drives) or digital methods (such as emails or cloud storage), highlighting the need for comprehensive data loss prevention strategies.
Example Case: ION Group, a financial software provider, suffered a ransomware attack by the LockBit group. The attack disrupted operations and included data exfiltration that affected major banking, brokerage, and hedge fund clients. This highlights the dual threat of operational disruption and data theft.
Source: Sekoia.io
About: These threats arise from careless or uninformed actions by employees that compromise security, such as clicking on phishing links, misconfiguring databases, or mishandling sensitive information. Unlike malicious threats, these actions are not intended to harm the organization but can be just as damaging. Addressing these requires robust training, awareness programs, and technological safeguards to minimize human error.
Example Case: A financial analyst inadvertently installed malware on the company network by clicking a phishing link, leading to a widespread data breach.
Source: ProofPoint
To mitigate insider threats, organizations should implement a comprehensive and layered security approach that includes both technical and human-centric strategies:
Insider threats represent a complex challenge for all sectors, necessitating a multifaceted approach to mitigation. By implementing strict access controls, enhancing monitoring capabilities, conducting regular audits, and promoting a culture of security awareness and ethical behavior, financial institutions can better protect themselves against the risks posed by malicious and unintentional insider actions.
As technology evolves and the perimeter of corporate networks expands, particularly with the increase in remote work, these strategies must also adapt to address new vulnerabilities and protect sensitive information effectively. Ensuring robust security measures and fostering an environment of awareness and accountability are paramount to safeguarding assets and reputation.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


