


For nearly six months, a three-day cyber attack on JD Wetherspoon went undetected. The names, personal information and some credit card details of 656,723 customers fell into the hands of a Russian hacking group and no one at the U.K. pub and hotel chain knew about it. CyberInt eventually discovered the attack in late 2015 and the hospitality company addressed the issue.
The customer data was stolen from the company’s website and patrons who logged on to free WiFi at JD Wetherspoon pubs. The hack took place over three days, but the mass of stolen data and the company’s inability to protect information and notice it straight away, is one of many examples of companies falling victim to an attack under a deluge of threats. These are tough times for enterprises needing to protect data.
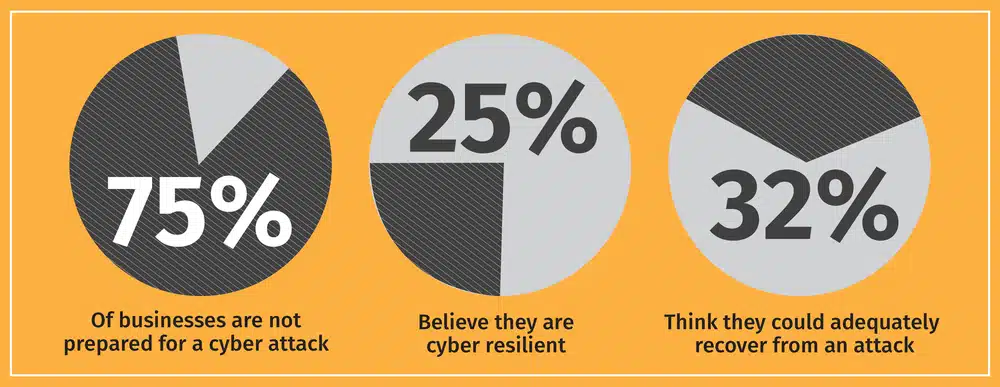
A recent study from the Ponemon Institute revealed that 75% of businesses are not prepared for a cyber attack, while only 25% believe they are cyber resilient and 32% think they could adequately recover from an attack. Part of that recovery includes the lawsuits and consistently large victim payouts. To cover these sums, companies rely on data privacy and cybersecurity insurance. These policies take a big portion of the financial burden off a company facing millions of dollars in settlements.
The reliance on this insurance is more common than one might think. A survey from Wells Fargo showed 44% of businesses with cybersecurity and data privacy insurance policies have already filed a claim, proving the frequency of attacks and use of this type of insurance.
Yet being covered for financial loss from an attack is not a deterrent or by any means protection from cybercrime. If Ponemon Institute’s study is representative of business, 75% of companies should be considering cybersecurity with greater fervor and seriousness. Insurance is one step, but they can take other steps to combat an attack before an insurance claim is necessary.
1. Incident Response Plans and Drills
One such step is that every company should have an Incident Response Plan (IRP). This plan, just like a fire evacuation plan, is preventative and precautionary. It should be well-organized, thoughtful and run at least once a quarter as a drill, just as a fire drill prepares people for the worst. Knowing the exact steps of how to respond to a cyber attack will lessen its effects and give any company peace of mind.
An effective incident response plan should rapidly detect an attack, minimize loss and destruction, mitigate the weaknesses exploited, and restore IT services.
To implement an IRP, it is important to ensure the plan is documented, a team has been assembled to focus on understanding the process, and a third-party vendor who specializes in cyber attack response has been chosen. These steps give the plan significance, meaning it will be taken seriously when needed. Many organizations are seeing the advantages of enforcing such IRPs. For example, the Bank of Israel issued Directive 361 in May 2015 to require all banks to have cybersecurity leadership focused on these response plans and other cyber readiness strategies.
To further advance the weight of such a plan, it is good to run drills. The IRP team, the vendor and all employees will be able to see what about the plan works, what doesn’t, and how to improve it. Aligning a company, from all angles, with the plan helps make it work when an attack happens.
2. Train Employees
Many workers are still unaware of the dangers of cyber threats. In a company like JD Wetherspoon, where the focus is on the physical business of running pubs, restaurants and hotels, cyber threats are harder to catch. Many smaller technology companies also struggle to keep up with potential attacks as they focus primarily on business gains, letting cybersecurity fall to the side. In a changing digital landscape, that awareness needs to sharpen. Employees should be vigilant of threats, know the warning signs, be digitally educated and receive training on safe cyber practices.
Many times, hackers gain access to a company’s data through phishing scams that take advantage of a naïve employee. The massive data breach of the health insurance company Anthem happened because an employee was entering information on a faux site that replicated the real company site.
With even the most basic training, the employees, who became victims and a gateway to hackers, would have been more knowledgeable about what to be more attentive about when using the computer. Training employees also alerts them to their own personal cyber protection.
3. Establish Privacy Policies
While this is a good business practice in general, establishing a privacy policy is crucial for the preparation and response to a cyber attack. A policy ensures a company’s customers know what information is collected, how it is gathered and how it is used. It also minimizes potential liability in the case of a cyber incident. Even if people are checking a box without reading the fine print, your company is still operating legally in trying to keep people safe from cyber attacks.
Following this policy begins with the design of a compliance program that is in line with all international laws regarding privacy. It is also important to appoint an individual to be the keeper of the policy and be responsible for safeguarding customer data. This individual should be able to tailor a policy to the company’s practices and train employees on how to comply and use it in their work.
4. Get Prepared with Pro-active Cybersecurity
Although so many companies feel ill-prepared for a cyber attack, there are ways they can ease their worry. By following the steps above, companies can begin to build their defenses. But even together, these are not enough.
Using a cybersecurity solution that predicts and mitigates attacks can be the ultimate defense against threats. Expert cybersecurity vendors, such as CyberInt, analyze a company’s weaknesses and fortify its protection. Cyberint runs ‘cybersecurity posture checks’ on companies, simulating real life, complex attack scenarios. While continuously monitoring the companies’ online assets — web site, social media platforms, their supply chain and more, in order to ascertain their weak spots open to hackers. Continuous checks ensure the hackers stay out and that changes within the company, their employees and new systems used, don’t make them vulnerable to hackers.
There is lots to be done in the fight to protect against cybercrime. Don’t fall victim to a breach like JD Wetherspoon, TalkTalk and the likes. Stay vigilant with these strategies.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


