


I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
As we get to the end of 2024, we thought we’d look at all the significant updates Cyberint (now known as Check Point Infinity External Risk Management) has introduced over the year. These new features are designed to help you better manage your cyber risks and improve your overall security posture. Here’s a look at the five biggest feature additions and their impact:
The Attack Surface Monitoring Module has undergone a major overhaul to help you effectively manage cyber risks related to your organization’s external attack surface. Key improvements include:
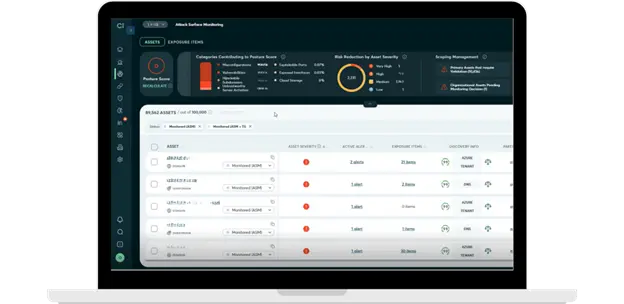
These enhancements help you maintain a comprehensive view of your attack surface, prioritize remediation efforts, and improve your organization’s overall security posture.
Cyberint’s AEV capability actively tests your organization’s exposures for exploitability. It continuously validates exposures, from open ports and unpatched software to exposed login pages and web apps. Key features include:
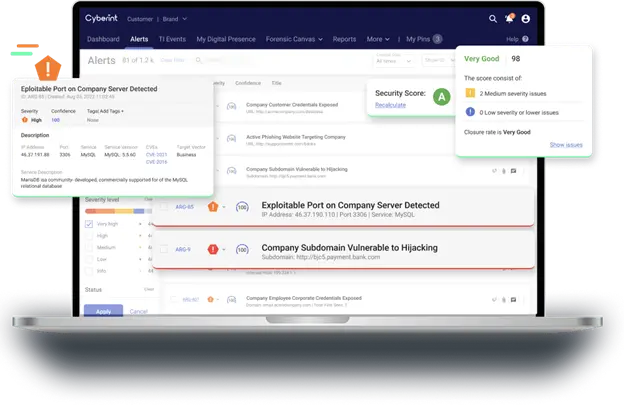
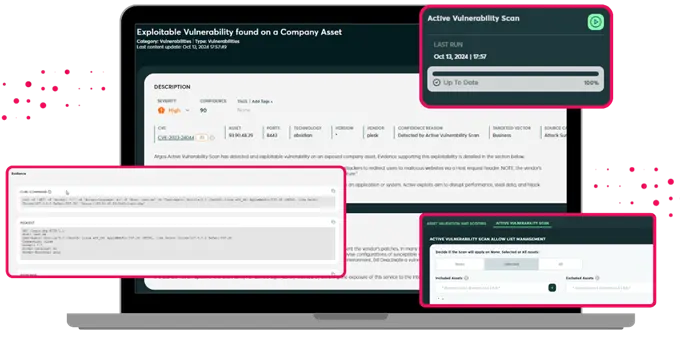
By leveraging AEV, you can level up your CTEM program and ensure that your organization’s digital assets are continuously monitored and tested for vulnerabilities, helping you stay ahead of potential threats.
This module allows you to follow trends in your specific threat landscape, tailored to your industry and region. It helps you stay informed about the threats most relevant to your organization. By understanding these trends, you can:
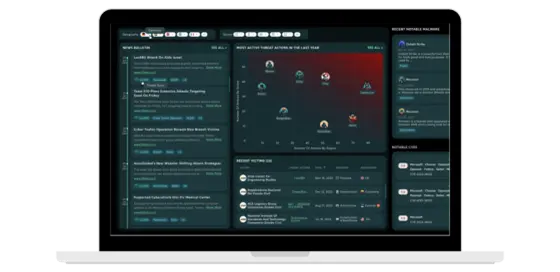
This module allows you to make informed decisions and proactively protect your organization against evolving cyber threats.
Cyberint has released a Threat Hunting License to enable you to:
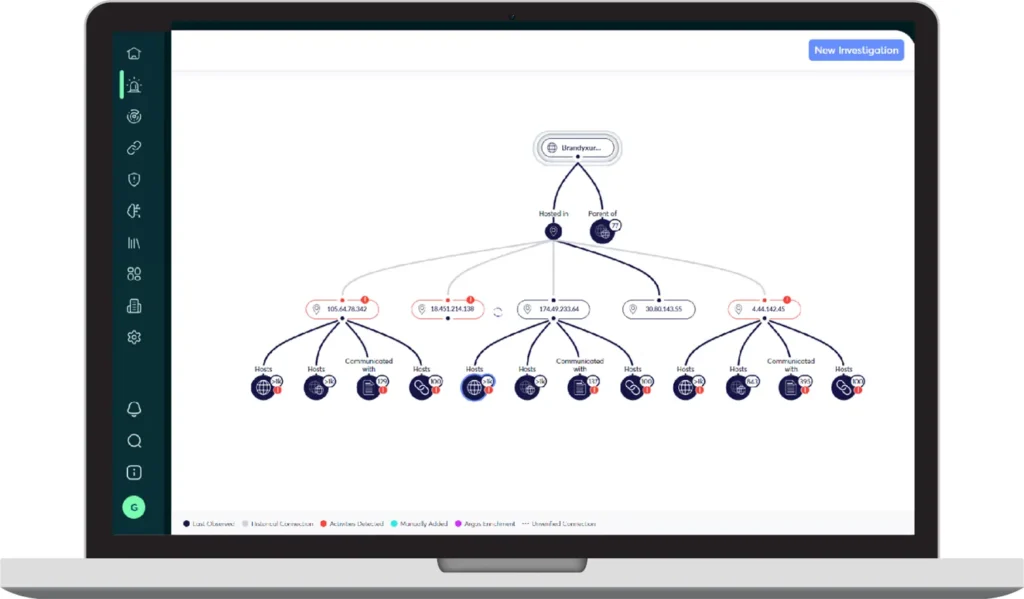
The Threat Hunting License provides extensive capabilities, tools, and data to dramatically improve the efficacy of your threat hunting activities. By leveraging the license, you can enhance your team’s ability to detect and respond to sophisticated threats, ultimately strengthening your organization’s security posture.
The new Risk Dashboard gives an executive-level overview of an organization’s external cyber risk profile. There is an overall risk score, assigned on a scale from 1 to 100, which is determined by three more granular scores:
The Risk Dashboard also provides benchmark scores to put your score into context and help you understand whether you’re more secure or less secure than organizations in the same industry and region.
In addition, the Risk Dashboard provides a high-level view of an organization’s strengths and weaknesses; the areas where risk is being effectively mitigated, as well as the areas that are presenting significant risk and should become a focus.
Several tools have been introduced over the course of 2024 including:
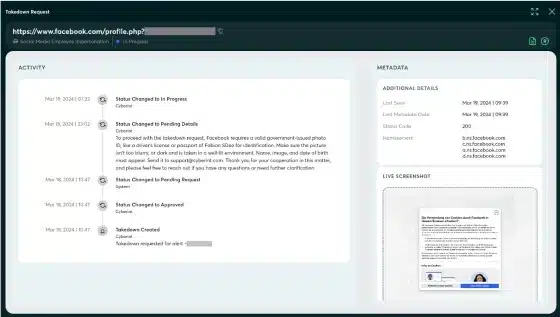
Takedown Request Screen
increases transparency into the takedown process. It provides greater details on each step and makes it easy to track and report on all the requests you’ve made. This feature helps you:
This screen simplifies the takedown process, making it more efficient and effective for your team.
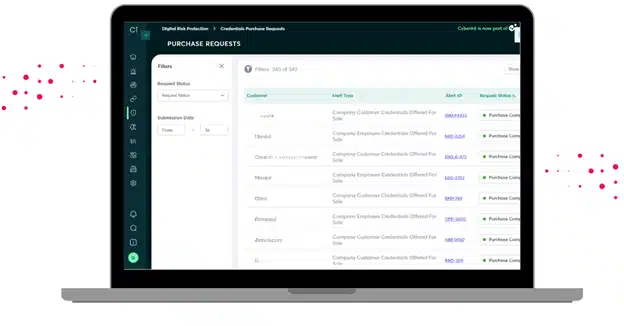
The Credentials Purchase Request Screen
When credentials are suspected to be compromised Cyberint has the ability to purchase these credentials to validate them. Now you can track the credentials that have been purchased, including when the request was made and if it was completed, when it was completed.
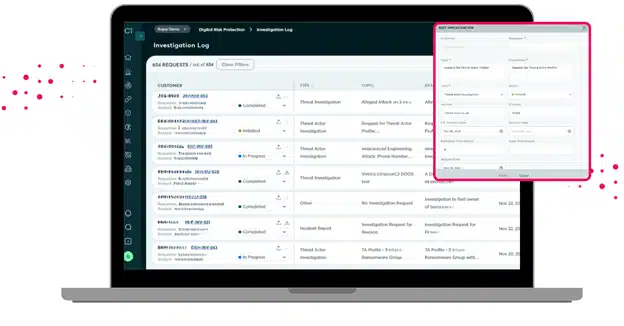
The Investigations Log
Most organizations don’t have the tools or time to keep up with escalating and increasingly sophisticated threats to their digital assets. With Cyberint’s Deep Dive Cyber Investigations, you can hunt, assess and respond to these threats with the help of our highly skilled analysts. And now you can
These updates represent significant advancements in Cyberint’s (Now Infinity ERM’s) capabilities, helping you stay ahead of evolving external cyber threats and manage your security posture more effectively.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start