Employees often need to access various online services for work and personal purposes. Whether signing up for industry newsletters, registering for webinars, or using online tools, a corporate email address is a convenient way to manage professional communication. However, this seemingly harmless habit can expose employees and their organizations to significant risks.
Since employees might reuse similar or even identical passwords for other third-party services and corporate interfaces, these credentials can be leveraged to obtain internal information and even access the company’s internal systems. Corporate emails serve as gateways to sensitive company information and, when used on third-party websites, can become prime targets for threat actors.
Threat actors could leverage such credentials in multiple ways, such as exposing the employee’s personal information, targeted spear-phishing, and even exposing the company to data breaches and lawsuits.
Companies can mitigate such risks by implementing strong email safety guidelines, using alternative secure communications channels, and implementing procedures in case corporate credentials are leaked.
This report outlines the dangers of using corporate emails on third-party websites, identifies potential threats, and offers best practices to mitigate these risks. It will help employees and companies better understand why safeguarding corporate email addresses is critical to modern cyber security.
A third-party website is a site that is neither owned nor operated by the employer’s company. Instead, it is managed by an independent entity. Examples include websites of vendors, online service providers, and any site not under the ownership of your company. For example an employee uses their corporate email to open a LinkedIn account or subscribe to an industry newsletter. These third-party entities may not have any formal association with your organization. However, employees use their corporate email addresses to register on these third-party websites, which could lead to the compromise of the .
Credentials typically consist of a username—often an email address—and a password. In some cases, they may also include additional information, such as answers to identity verification questions, like “your mother’s maiden name” or “your pet’s name”. Since many people tend to reuse passwords and identity verification answers for the sake of convenience, there is a significant risk that corporate credentials could be compromised in case of a breach in a third-party website.
The threats of using corporate emails on third-party websites range from phishing attacks to data breaches, malware, and beyond. In many cases, the security standards of third-party websites do not match the protocols that corporations typically enforce, leaving these external platforms vulnerable to exploitation.
Moreover, the misuse of corporate credentials can lead to severe consequences, including financial losses, legal repercussions, and damage to a company’s reputation . Understanding these risks is crucial for employees and companies, as it helps develop strategies to protect corporate assets and maintain the integrity of digital communications.

To truly understand the risks of using credentials on third-party websites, it’s important to recognize how widespread the practice of using corporate emails for personal purposes is among employees.
Between October 15 and November 15, 2024, Cyberint reported to our customers approximately 14,000 cases of employee credentials being exposed in third-party breaches and data dumps. Because cybercriminals cannot be trusted, and the credential combo lists dumped on the dark web are often fabricated data, Cyberint’s solution allows customers to configure their corporate password policy, which automatically filters out any exposed corporate credentials that don’t meet the policy. It is important to emphasize that most of the 14,000 credentials were all flagged because they complied with each company’s password policy. As a result, many clients required the affected employees to reset their passwords.
A significant challenge is that many individuals are exposing corporate credentials after using an infected personal device to access corporate resources. With hybrid work firmly established as the norm, employees may sometimes access corporate resources from their personal computer. If the personal device is infected with malware, such as an InfoStealer, the corporate credentials will be harvested and sent to the threat actor.
Additionally, Cyberint (now a Check Point Company) often detects malware infections on employees’ personal computers because those employees have used their corporate email for personal activities on their home devices. Common examples of such usage include streaming services like Netflix and Spotify, e-commerce platforms like Amazon and eBay, as well as financial and payment services.
These popular platforms’ users’ credentials are often leaked due to computers infected by InfoStealer malwares. InfoStealer malware is a malicious software designed to steal sensitive information from compromised devices. Many of the InfoStealers out there also harvest the credentials saved in the web browser. Once an employee has used his corporate credentials for private usage, he also risk compromising the credentials without a third-party website breach happening.
One major problem with using corporate credentials for personal purposes is password reuse. This practice involves using the same password across multiple accounts, including both corporate and personal ones. Moreover, if these credentials are saved in web browsers—a feature common in most modern browsers—their leakage becomes more and more likely over time.
To illustrate the severity of the issue, over the same period, Cyberint (now a Check Point Company) has detected almost 700,000 computers infected with malware, with their information exposed in the wild.
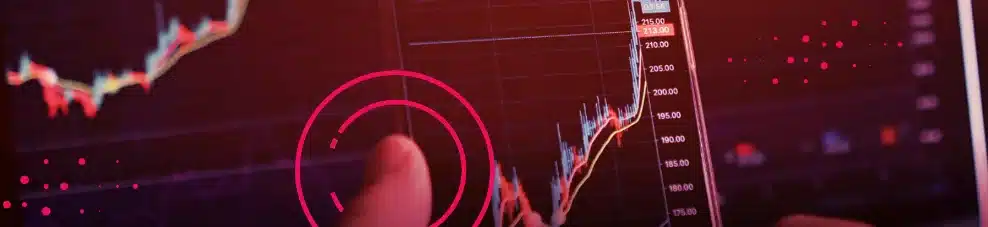
Corporate emails are often used on third-party websites for convenience. It assists employees in managing their work and personal activities, helping them stay organized on a single platform. However, this convenience carries hidden risks that can have serious consequences for individuals and their organizations, especially if employees reuse their corporate credentials, including passwords, on multiple sites.
Before diving into the different types of threats, it is important to note that once the credentials are leaked, they will stay in the wild for a long time.
Cyberint (now a Check Point Company) has seen examples of employees’ credentials re-exposed years after their initial leakage and even after the employee has left the company.
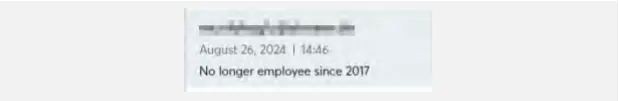
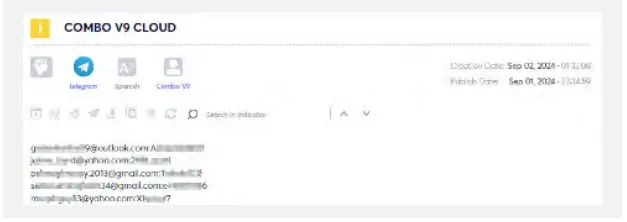
This is because threat actors republish the credentials after the initial leak as part of combo lists.
Combo lists are large files containing emails and passwords that usually do not specify which interfaces they are associated with (the format is email:password new line). People often reuse one password for multiple interfaces, therefore when such a list is exposed, threat actors can access all the interfaces to which those credentials can be used for login.
Threat actors tend to republish combo lists to increase their reputation; some credentials can be found more than once in multiple sources.
People often reuse passwords across multiple sites for convenience. If a third-party site is compromised, the attackers can use the stolen credentials to attempt access to corporate systems, potentially leading to unauthorized access.
Below is an example of employees’ email addresses that were leaked on multiple sources with the same credentials every time. The “Times Seen” column indicates how many times the Cyberint solution detected the same set of credentials from different sources.
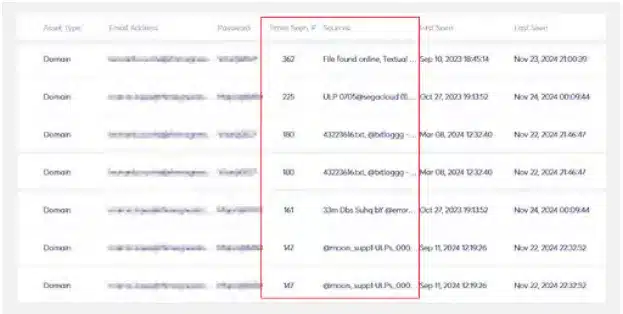
Combo lists are one of the most common data types that threat actors use for Account Takeover attacks. An Account Takeover (ATO) attack is a type of cyber attack in which a malicious actor gains unauthorized access to a user’s online account—like an email, bank, or social media account – often by testing leaked credentials from websites with low-security standards. Once inside, the attacker can exploit the account to make purchases, steal personal information, or spread further attacks.
When a threat actor gains unauthorized access to the employee’s corporate account, they can impersonate the employee, access sensitive corporate systems, and escalate privileges to cause significant damage. Many data leaks have happened due to a threat actor taking over an employee account.
Many tools take advantage of those leaked credentials for ATO attacks, for example the so called “credentials stuffing tools”, also known as “checkers”. Those computer programs check whether the credentials work for a certain website or not.
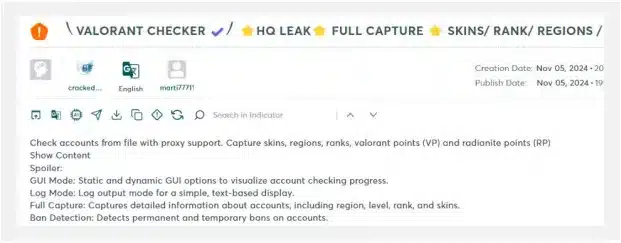
Many third-party websites do not have the same level of security as corporate networks. If a third-party site is breached, the data associated with corporate emails, including usernames and passwords, can be exposed and used in further attacks.
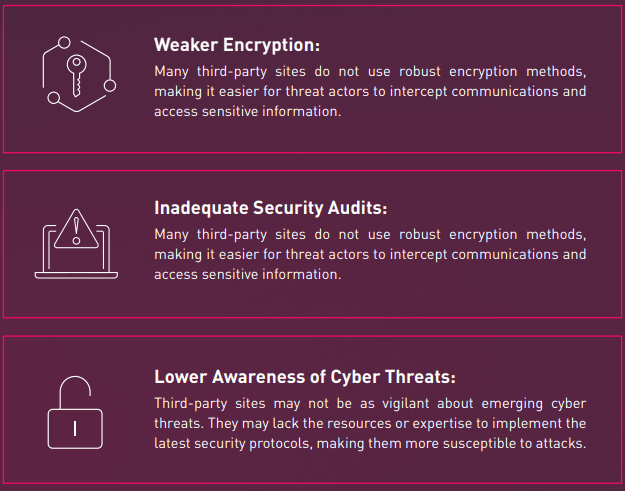
Corporations invest heavily in cyber security to protect their networks, data, and communications. This includes implementing robust firewalls, encryption, multi-factor authentication, and regular security audits. In contrast, many third-party websites lack those security measures, for example:
One of the best examples of the issues related to third-party website security is WordPress. WordPress is a versatile, open-source content management system (CMS) that enables users to easily create and manage websites and blogs, offering extensive customization through themes and plugins. It is also the most widely used CMS in the world.
As of the writing of this article, there are over 28,500 known vulnerabilities in WordPress. If a website that an employee is registered with has not been updated to the latest version of WordPress—which is quite common—there is a significant risk that the employee’s information and credentials could be compromised.
Phishing attacks are one of the most common and dangerous threats that can arise from using corporate emails on third-party websites.
Phishing involves sending deceptive emails to trick recipients into sharing personal or corporate information. Corporate emails are prime targets because they can provide access to company networks, sensitive data, and financial accounts.
When employees use their corporate emails to register on these platforms, they may receive phishing emails that appear legitimate but are designed to steal sensitive information or infect the employee machine with malware.
Below is an example of a phishing email targeting one of Cyberint (now a Check Point Company) client’s employees.
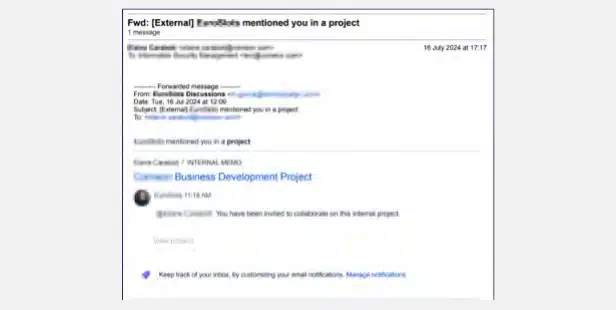
Phishing attacks often start with seemingly harmless emails sent to corporate addresses. These attacks often escalate into more significant security breaches, causing great harm to the company and its clients.
Such examples include the Los Angeles County Department of Health Services data breach in February 2024.
The Los Angeles County’s Department of Health Services (DHS) suffered an email phishing attack that led to the exposure of the personal data of more than six thousand patients. The breach occurred when 23 staff members were victims of phishing emails, allowing unauthorized access to their email accounts. Exposed information included names, addresses, dates of birth, medical details, and insurance data.
DHS has notified affected individuals and implemented stronger cyber security measures to prevent future incidents. Officials recommend vigilance against potential scams or identity theft targeting those affected
Employees using their corporate emails on third-party sites increases the risk of receiving phishing emails. Once threat actors access a corporate email, they can launch more targeted attacks, potentially compromising the entire organization.
Third-party sites often collect more information than necessary, including company-related data. This information could be sold or shared with other parties without the employee’s or company’s knowledge, leading to privacy concerns.
Data mining involves extracting valuable information from large datasets, often without the knowledge or consent of the individuals involved.
Employees using their corporate emails on third-party sites may unknowingly provide valuable data that can be mined for commercial purposes. This data can include contact information, purchasing habits, and professional networks. Companies that engage in data mining can use this information to profile employees and target them with specific advertisements or, worse, sell this data to other entities.
Third-party websites often collect more data than necessary, and in some cases, they may not disclose how they plan to use this information. For example, a seemingly innocuous registration process might require an employee’s corporate email, job title, and company name. This information can then be sold to data brokers or other companies, leading to increased spam, phishing attempts, and targeted attacks.
The privacy implications of data mining are significant. Employees risk having their personal information exposed or used without their consent. On the other hand, companies can suffer from the misuse of corporate data, leading to reputational damage, legal issues, and a loss of trust among clients and partners.
Using corporate emails on third-party websites can raise legal and compliance issues, especially concerning global data protection regulations.
Many jurisdictions have strict regulations regarding data breaches, especially involving personal or corporate information. For instance, under the General Data Protection Regulation (GDPR) in the European Union, companies must ensure that personal data is handled securely and report breaches within 72 hours. If a breach occurs due to the misuse of corporate emails on third-party sites, the company could face hefty fines and legal action.
In the US, all 50 states have laws requiring private businesses and, in most states, governmental entities to notify individuals of security breaches. If the company doesn`t act according to the law, it could even lead to imprisonment. Similarly in the Philippines, such an action would be charged with five years.
In case of a data breach, the company might be deemed liable if the attack was made possible by the use of corporate emails on a third-party sites. This could result in lawsuits, financial losses, and damage to the company’s reputation. Additionally, the company may be required to notify affected individuals, provide credit monitoring services, and take other costly remedial actions.
Compliance with data protection regulations such as the GDPR, or the California Consumer Privacy Act (CCPA) is crucial for companies that handle personal data. Misusing corporate emails on third-party sites could violate these regulations, resulting in severe penalties. Companies must ensure that their data handling practices align with these regulations and educate employees on the importance of compliance.
Misusing corporate emails can have severe consequences for a company’s brand and reputation, which are often harder to recover than financial losses.
Employees using corporate emails on third-party sites may inadvertently expose the company to negative publicity. For instance, if a data breach occurs, the company’s name could be associated with the incident, leading to a loss of trust among customers, clients, and the general public. This can result in decreased sales, lost partnerships, and long-term brand image harm.
Trust is a critical component of any business relationship. Customers or clients may take their business elsewhere if they believe a company is not protecting their data. This loss of trust can have long-term effects on the company’s bottom line, as it can be challenging to regain the confidence of those who feel their data was not adequately protected.
There have been several high-profile cases where companies have suffered reputational damage due to the misuse of corporate emails. In some instances, companies have faced backlash after employees used corporate emails on social media platforms that were later involved in scandals or data breaches.
In September 2020, an attack was conducted against the co-founder of the Australian hedge fund Levitas Capital. He received an email containing a fake Zoom link. After clicking the link, the malware was deployed on the hedge fund’s corporate network. Afterward, the threat actor issued fake invoices for nearly $8.7 million.
After discovering the breach, Levitas Capital minimized its losses to only $800,000, but the damage to its reputation was already irreversible. Their biggest client, Australian Catholic Super, has pulled its previous committed capital and canceled a planned additional $16 million Investment, which forced the fund to close.
This highlights the importance of protecting corporate email addresses and the potential consequences of failing to do so.
Corporate espionage is a serious risk that the misuse of corporate emails can intensify.
Threat actors can use third-party sites to gain access to corporate networks. For example, an employee might use their corporate email to sign up for a service that later turns out to be a front for a phishing attack or suffer from a data breach. This can provide a way to exfiltrate data, disrupt operations, or damage the company from within.
Corporate espionage involves the theft of trade secrets, intellectual property, or other sensitive information. By using corporate emails on third-party sites, employees may provide competitors or other malicious actors with access to this information. These threats can be challenging to detect and significantly harm a company’s competitive position and financial health.
Companies can take several steps to mitigate the risks of corporate espionage. These include implementing strict email usage policies, monitoring suspicious activity, and providing regular training on cyber security best practices. Additionally, companies should consider using tools that can detect and prevent data exfiltration and unauthorized access to sensitive information.
In an era where digital convenience often takes precedence, the practice of using corporate email addresses on third-party websites poses significant security threats to organizations. This report condenses the critical risks and consequences of such actions, aiming to heighten awareness and foster better cyber security practices among employees and corporations alike.
Some of the major threats that involve using corporate credentials in third-party websites include:

Third-party websites constitute less secure environments prone to exploitation, lacking robust encryption, comprehensive security audits, and awareness of emerging cyber threats.
It is recommended that corporate emails be restricted to secure, trusted platforms and that cyber security measures, including firewalls, encryption, multi-factor authentication, and regular security audits, be implemented and maintained within corporate environments.
It is important to note that once an employee’s credentials are leaked, they might remain in the wild for a long time. Cyberint (now a Check Point Company) has seen the corporate credentials of employees who left their companies more than ten years ago.
Misusing corporate emails on third-party websites can lead to severe repercussions, including financial losses, legal issues, and damage to the company’s reputation. Understanding and mitigating these risks through better practices and stringent security measures are vital for safeguarding corporate assets and maintaining the integrity of digital communications in today’s cyber security landscape.
Recommendations: Corporate Emails Safety Guidelines
Both employees and companies should follow certain best practices to protect against the risks of using corporate emails on third-party websites. This includes:
Regular training and awareness programs can help employees understand the risks of using work emails on external websites. These programs should cover topics such as phishing, social engineering, and the significance of data security. Companies can significantly reduce the risk of a security breach by keeping employees well-informed about the latest threats and best practices.
In addition to those practices, companies should secure their communication channels.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.


This playbook will provide a guide for security teams to respond to incidents involving compromised credentials from third-party website leaks. The goal is to mitigate risks and secure the organization’s systems when such credentials are exposed.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start