


No excuses. Don’t even try to act shocked, or tell me you didn’t know this could happen. In May 2017, the WannaCry ransomware spread viscously across the worldwide web, affecting more than 300,000 PCs across the globe. And, then again on June 18th, 64 countries and more than 2,000 victims fell prey to Petya, mimicking the very same security flaw as WannaCry.

Source: twitter.com/mrjefftang
Both attacks could have been avoided by using less than a handful of common best practices. Pardon my French, but why the hell are organizations still not patching their systems in 2017!? With patch management systems, vulnerability scanners, and threat intelligence, why are we still falling into the same trap?
I mean, there are so many good (and not so good) cyber security vendors out there, the technology that is supposed to safeguard us from an attack is sound! Don’t get me wrong, there are no silver bullets here, but you can make it hard enough for the bad guys to deter them from even trying!
My professional network is filled with talented cyber security practitioners who work at some of the very best technology vendors out there. Which is why I’m puzzled when these sorts of things happen, putting nation state attacks aside, these types of campaigns should just not exist in 2017.
So, tell me, what was your excuse?
I’ve deduced that it is one of the following reasons. Either the companies that got hit, were ignorant or they lacked the resources needed to act upon this threat, or both.
There is a sigh of relief here, in my little rant. What you need now, is a plan of action, so let’s get started.
The warning period is far from over, you’ve been hit twice already, right? Now, is the time to take action. Microsoft already addressed the importance of patching these vulnerabilities in March, and again last week. Patch your workstations and servers, or you can say goodbye to your organization now. Here are the patches available for the following systems:
MS17-010 Update for Windows 10
MS17-010 for Windows 7 and Server 2008
Windows Server 2012 (KB4012214)
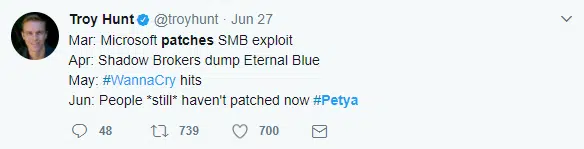
Hopefully organizations have learnt from delayed patching and that this should be a wakeup call to follow through with IS maintenance, especially when it comes to applying security patches as well as managing your backups.
Technology vendors such as Symantec, Solarwinds and Quest are just a few that offer patch management systems. While companies like Qualys, Tripwire and Beyondtrust, offer vulnerability management platforms that are continuously updated with known vulnerabilities.
Out of all the niches in the security market, I would say that the EDR (Endpoint Detection and Response) or next generation endpoint protection segment is by far the most competitive at this point and possibly the most mature. Almost all of the vendors in this space have released a video following the last two campaigns demonstrating how they would have detected and stopped both Wannacry and Petya. To be honest, I believe most of them would have!
According to Gartner, “Organizations investing in EDR tools are purposefully moving from an ‘incident response’ mentality to one of ‘continuous monitoring’ in search of incidents that they know are constantly occurring.”. Once again, today’s technology is more than capable of helping organizations deal with these types of threats.
Yes, I know, this is probably the most overused couple of words in the industry in the last few years. But, and this is a big but, utilizing threat intelligence well, would have helped in this case. While there are plenty of vendors offering all sorts and types of threat intelligence, there are a few that provide their customers with context and actionability. As in this case, both the SMB vulnerability and its patch were disclosed publicly a few weeks before the attack happened. Consuming threat intelligence in the right channels and acting upon IOCs in a timely manner, would of mitigated this threat before it even materialized.
There are many TI vendors out there and one such vendor is CyberInt (apologies for the shameless plug). Working with our Argos Threat Intelligence Platform, along with our team of analysts allowed our customers to take the correct actions to prevent and resolve the threats of both Wannacry and Petya.
We know that it’s tough with so many things to do, and never enough working and qualified hands to do it all. If this is how you are feeling, then it’s time to reach out to vendors who can help. The cyber security ecosystem is filled with high quality service companies that can come in and act as an extension for your team. They can help you achieve the above goals in a fraction of the time and with far less headaches, CyberInt happens to be one of those companies.
Now that you have an action plan in place, use the momentum of these latest attacks in order to secure a decent budget from the boardroom. This way you can make sure that you are safe next time such an attack comes around.
So, did this little rant and pep talk help?
It isn’t always easy, although this time it kind of is. Stop spending time and money on redundant technologies. Understand what needs protecting and how to protect it. Make a plan and follow through. Use external help when needed and experts to guide you. And, most importantly, make sure you’re patching your software.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


