



I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
If you’ve paid attention to recent cybersecurity trends, you know that monitoring your supply chain is important due to the surge in supply chain attacks.
But who, exactly, is responsible for that monitoring? Traditionally, the answer has been GRC (Governance, Risk and Compliance) teams, who monitor supply chains to help protect organizations against third-party risks.
In an era when supply chains are under intense attack, however, there’s a strong case for involving security teams, too, in supply chain monitoring. Even if they don’t assume sole responsibility for supply chain monitoring, they should at least partner with GRC teams to help detect and mitigate supply chain risks.
Here’s why, and what businesses can do to ensure that security teams collaborate effectively around supply chain monitoring.
Conventionally, the main goal of validating vendors within supply chains was to ensure that vendor relationships did not expose a company to compliance or legal risks. That’s why the task typically fell to compliance officers.
But today, vendors can also be a major source of cybersecurity risk. Indeed, although it remains common to think of malware infections as the root cause of data breaches, supply chain attacks – meaning ones where threat actors compromise a third-party vendor to harm all the other organizations that use that vendor’s products – have now surpassed malware-based attacks by a rate of 40 percent. It’s easy to understand why such attacks have become so popular: As SecurityWeek notes, “A successful attack against a supplier can lead to multiple opportunities against the supplier’s downstream customers.”
The Solarwinds attack, which was first reported in 2020, helped to inaugurate this trend. But it has only intensified due to ongoing supply chain breaches – such as those against Okta and SiSense, to name just two of the most significant recent supply chain attacks.
All of the above means that supply chain monitoring is no longer just a matter of compliance. It also plays a critical role in cybersecurity.
Actually building an effective process for monitoring for supply chain risks is a multi-stepped affair. The risk management processes that many organizations already have in place offer a foundation, but supply chain risk monitoring requires additional practices beyond conventional compliance checks.
Here’s a look at everything you should be doing to identify and manage supply chain risks.
First and foremost, you need to know if one of the vendors in your supply chain has experienced a breach. This visibility is critical for ensuring that you can stop using affected products or (if they’ve already been compromised) take steps to prevent the breach from escalating to other systems.
Gaining this visibility requires a comprehensive inventory of all vendors in your supply chain, as well as continuous monitoring of security disclosures.
Knowing when threat actors are considering attacking a vendor provides early warning into potential supply chain breaches. You can gain this visibility by monitoring the Dark Web for discussions of vendors, then take steps to erect strong security defenses around their products.
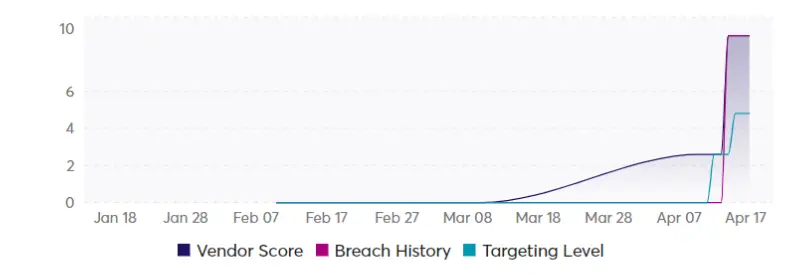
Consider the example of SiSense, which experienced an attack:
Through Dark Web monitoring, Cyberint identified a rising target level against SiSense starting two days before any public disclosure of malicious activity involving this vendor:
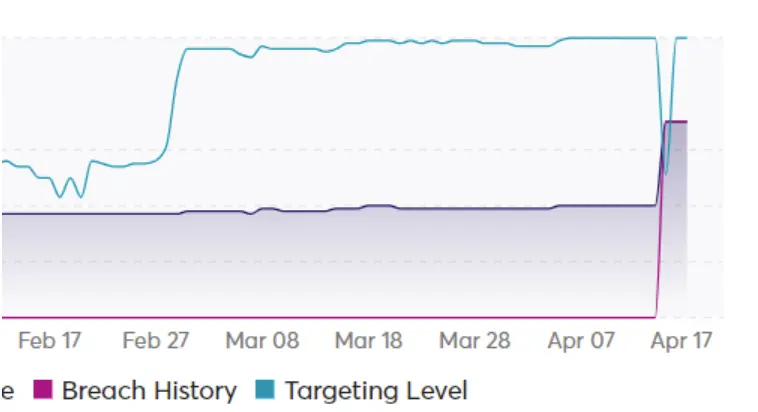
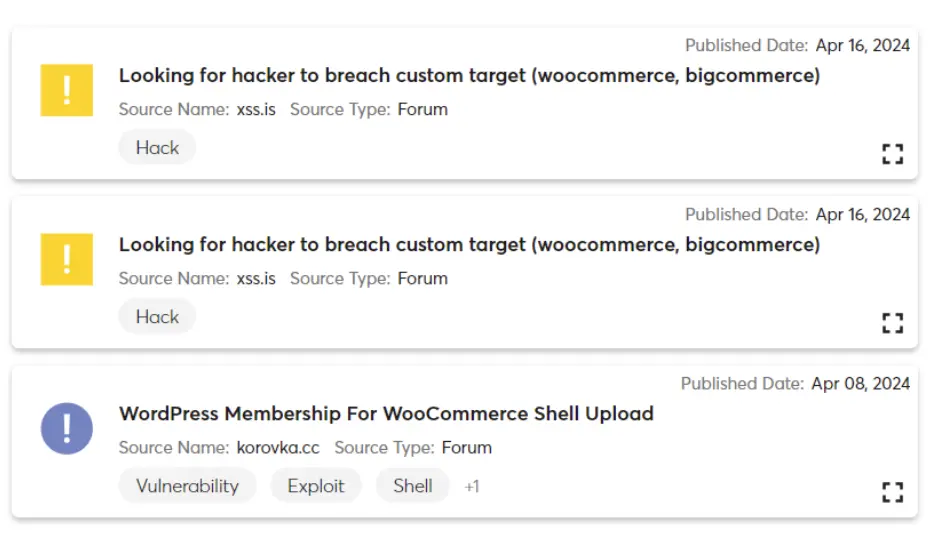
Cyberint gained similar early indication of the attack against WooCommerce by tracking discussions of potential attacks against the company, as well as sharing of exploits, before the attack became public:
Traditional compliance monitoring often includes assessment of vendor criticality, meaning how important a vendor is to a given business. This is important because it helps companies determine how much exposure they may have to a supply chain risk.
However, vendor criticality can change over time, and static compliance supply chain monitoring doesn’t always update criticality assessments. It’s important to reassess vendors on an ongoing basis because their role in your business can evolve.
In some cases, credentials can be leaked through vendors even if vendor software doesn’t contain vulnerabilities. This happened, for instance, during the recent Okta attack, in which threat actors were able to access private customer data managed by Okta.
Knowing about incidents like this one ahead of time can help companies revoke credentials that threat actors might have accessed before the attackers can use those credentials to break into systems. However, traditional compliance reports don’t provide this type of visibility, which is one of the reasons why bringing cybersecurity teams into compliance monitoring is critical.
Compliance reports often assess the level of exposure of vendors, but they don’t usually dig too deeply. For instance, they might look only at a company’s primary domain, without considering connected assets.
A more effective supply chain monitoring strategy comprehensively assesses all of a vendor’s assets to evaluate its entire attack surface.
Compliance reporting typically assesses vendor cyber hygiene through questionnaires, asking questions like which tools and processes the vendor uses to detect threats. That’s a start, but to assess supply chain risks most effectively, businesses should actually investigate their cyber hygiene directly.
This becomes possible when cybersecurity teams, not just compliance teams without cybersecurity experience, can engage with vendors.
Managing compliance and legal risks should be one goal of supply chain monitoring. But today, detecting cybersecurity threats that originate in digital supply chains has become an equally critical component of supply chain risk management. As the headline of a Forbes article puts it, “Compliance isn’t enough. Security is key.”
That’s why it’s time to evolve supply chain monitoring into a collaborative affair where compliance and cybersecurity teams can work together.
Cyberint can help. Through continuous supply chain monitoring, Cyberint provides early insight into vendor risks – including in cases where attacks have not yet been discovered or announced publicly – so that you can respond proactively. Learn more by requesting a demo.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


