


It is common and intuitive to think that a security manager is responsible for the protection of their own team and organization. Spending the company’s resources on the security of another organization may sound unreasonable. However, recent events in the retail industry teach us otherwise. Today more than ever, as 3rd-party risk is gaining speed, executives are exposed to threats from unexpected directions and involving new weak points. The following report presents two examples of such incidents occurring in the retail industry, representing this new approach taken by cybercriminals.
Original forum post by “ShinyHunters”
On January 25, 2021, menswear brand Bonobos informed its customers of a data breach affecting customer personal information. The breach was attributed to “ShinyHunters”, the actor who distributed the compromised information on a fraud forum.
Cyberint detected the post and downloaded the database. Initial investigation revealed a massive database of 70 GB in size, exposing private user information such as physical addresses, email address, phone numbers, partial credit card numbers, order information, and password histories.
At first glance it seems like another unfortunate data breach. However, Cyberint’s deep-dive analysis revealed a substantial number of retail sector executives who appeared to be customers of Bonobos, and therefore were directly affected by the breach. The key datapoint that exposed these executives was their organizational email, which they used when they signed up to the platform.
It is worth mentioning that “ShinyHunters” alone is associated with more than 10 data breaches since the beginning of 2021, including the Nitro and the Meetmindful breaches. Cyberint’s analysis indicates that the findings of recent breaches are similar, as organizational email addresses of high ranked retail employees were detected on additional databases.
The organizational email addresses linked the breached records to the influential public figures behind them, putting the executives at risk: falling into the wrong hands, this information could not only be utilized for fraudulent transaction on the executives’ behalf, but could also be leveraged against the organization through spear phishing campaigns and even identity theft. Furthermore, as users often reuse their passwords among several online platforms, such breaches may actually disclose corporate login credential pairs for the involved executives.
Unfortunately, Cyberint are not the only ones to recognize the dangerous potential of 3rd-party breaches. On December 2, 2020, Cyberint detected an email sent to executives of several major Canadian retailers, claiming that information of theirs had been breached as part of a ransomware attack against Parkland Fuel (the largest Canadian fuel retailing company owning several gas station chains). The breach itself seems to have taken place last November, and the email was sent to the affected partners of Parkland on December 2nd.
To prevent threat actor and attack proliferation, most security experts recommend ransomware victims refuse to pay ransoms. This challenges the attackers, who need to find creative ways to extort their victims and force them to pay. One of the popular MOs is uploading the exfiltrated data (before encryption) of a stubborn victim to a designated dark web repository, which doubles the risk for the victim adding potential loss of competitive advantage, reputation damage and customer churn.
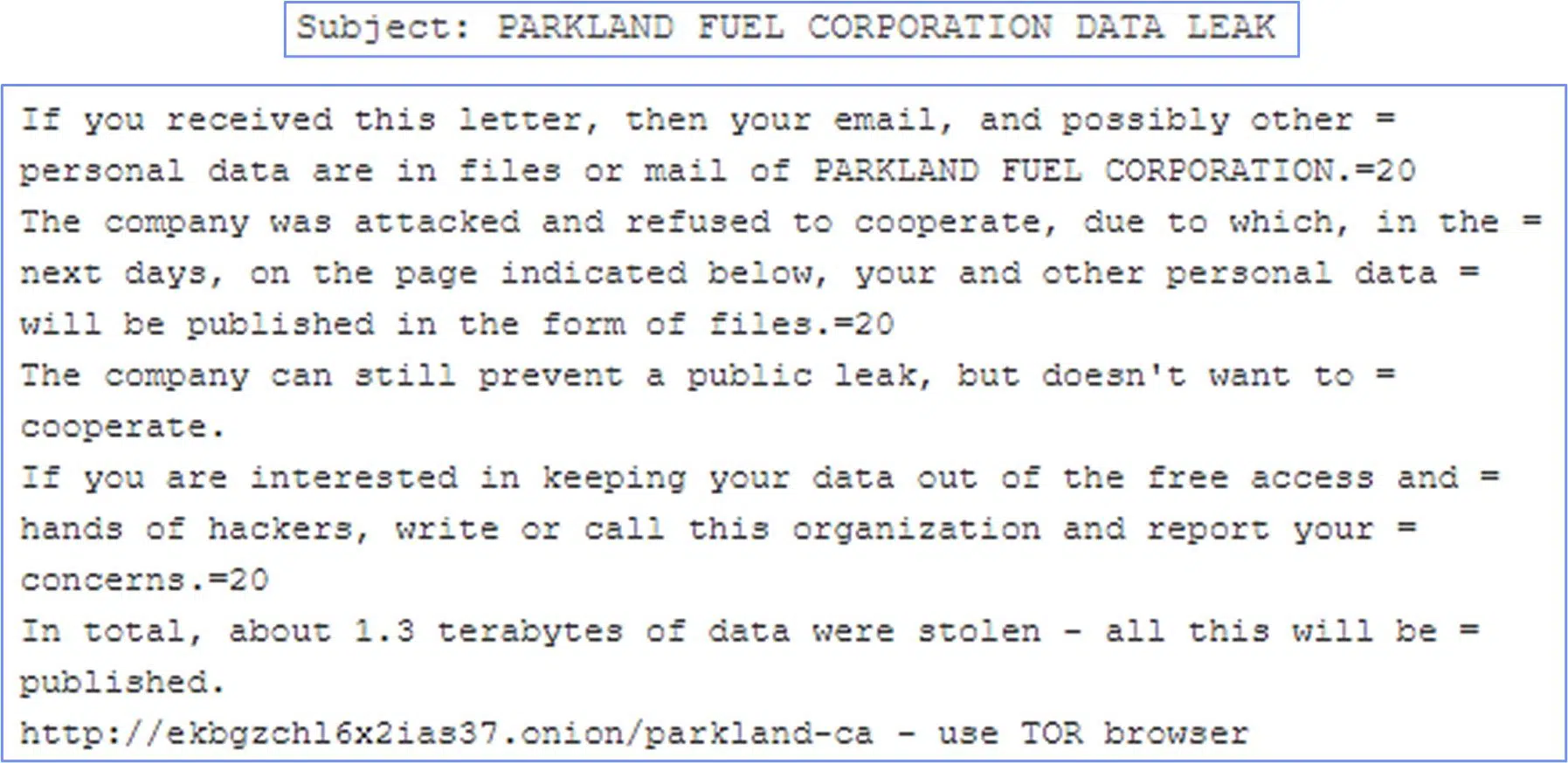
Snippet from the ransom email
The exposure of data shared between the companies could be utilized by threat actors and competitors to gain inside knowledge of the company’s operations and business; those may result in significant financial loss.
For the threat actors behind the Parkland ransomware, this MO did not end there. The group, named “Clop/cl0p” and associated with the financially-motivated threat group TA505, had begun uploading information from Parkland to a dedicated repository on their dark web website. At the same time, they sent an extortion email to the executive employees of Parkland’s partners, threatening them that if they will not convince Parkland to cooperate their personal information would be disclosed.
As demonstrated above, attackers no longer see the targeted organization as the sole potential victim of their attacks, but are actually starting to take advantage of the compromised 3rd-party information they possess including personal information of high-ranked employees in other companies.
Cyberint advises organizations to take the following precaution measures in order to avoid 3rd-party threats:
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


