Self-Published Author and a digital marketing specialist. Read his thought leadership articles for information on the Attack Surface and Threat Intelligence.
Threats to the e-commerce industry have increased in the last year as multiple threat actors have complicated their attacking tactics, tools and procedures in order to gain higher efficiency and quick profit. The following report will cover the major threats in the upcoming holiday season and provide critical information and mitigation steps.
Over the course of time, a trend that started in the United States has been adopted across the globe.It is the Friday after Thanksgiving, called Black Friday. Many shopping centers, supermarkets and malls open early – sometimes even as early as midnight – and offer lucrative discounts that can tempt anyone to go on a shopping spree.
As we have transitioned to a cyber-dependent era, the Black Friday tradition adapted to the current cyber landscape, offering a much more diverse selections of deals and an easier way of shopping with the effortless access of online shopping or “e-Shopping”, simply using a mobile device.
The biggest threat to date is still ransomware, especially on the busiest Friday of the year. With every customer racing to many online shops to find the best deals they can, it is a great opportunity for threat actors to capitalize on this event.
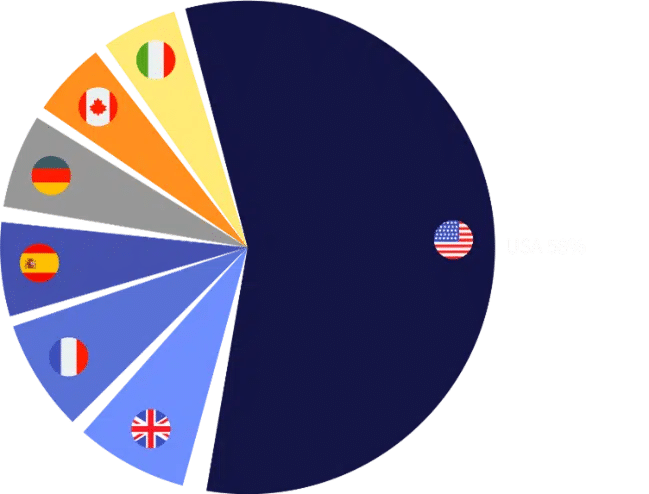
The ransomware industry maintains its grip on western victims, with the US, Canada, and western-European countries being the most targeted. The ransomware groups are banking on the sensitive timing and may set a new record. The groups are attempting to be as efficient as possible by launching attacks on e-commerce-based companies in order to profit quickly.
Several new ransom groups have emerged recently, one of which is the Royal ransomware group, which has claimed over 30 victims in the last two weeks and relies heavily on malicious advertising (aka malvertising). The group employs a variety of delivery methods, including using contact forms on targeted organizations’ websites to deliver phishing links, hosting Trojans and using Google Ads in at least one of their campaigns, effectively blending in with normal traffic.
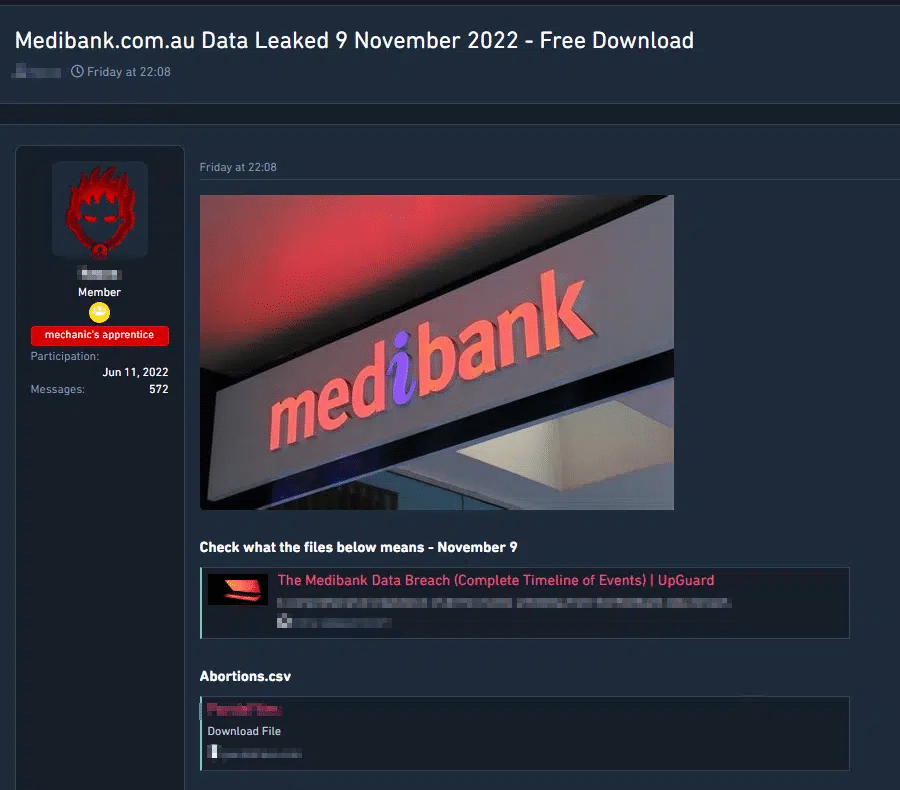
With the latest news on Medibank’s ransomware breach, the perpetrators, believed to be a Russian-based cybercrime group, released confidential information about Medibank and its customers following the institution’s refusal to pay. They leaked comprehensive information about all Australian Health Management members, including details about their health and medical history.
It is very evident from this breach that the ransomware group’s tactic of Double Extortion is being used, with them encrypting the victims’ data to render it inaccessible and stealing that same data and threatening to release it publicly.
As of this writing, Medibank has adamantly refused to pay the ransom. The amount currently demanded by the ransomware group is $10 million. With this breach, the foreseeable financial damages that Medibank is facing are around A$700 million in compensation alone, according to Bloomberg.
In line with the increased consumer demand that emerged during the COVID pandemic, companies have increased investment in cloud systems, IT and OT infrastructure, extended supply chains and third-party services, and increased overall uptime in order to enhance the consumer experience. As a result, retailers have also increased their attack surface that Threat Actors are liable to exploit. With Cyberint’s ASM (Attack Surface Mapping), we can provide visibility of the true attack surface, map the digital assets that clients are aware of or unaware of, and are capable of identifying malicious or rogue assets.
With one of the busiest seasons of the year for consumer purchases looming, Threat Actors are keen to exploit this precarious time to earn a profit, as they also expect that companies will be keener to pay the ransom if it negatively affects sales and projected profits. This is also confirmed in recent trends, with retail organizations suffering more ransomware attacks than the global average.
The most prevalent infection vectors for ransomware are commonplace spear-phishing emails or sophisticated phishing campaigns that emulate Microsoft interfaces and other commonly used interfaces for businesses.
According to data on last year’s Black Friday, many of the threats, especially Phishing attacks, are most present during this period of intensive shopping sprees. They include massive amounts of Black Friday related phishing frauds and fake infrastructures. Threat actors create fake websites, domain impersonations, fake mobile applications and malicious emails in a bid to harvest users’ financial and personal identity information.
A week before Black Friday and Cyber Monday, Amazon left hundreds of relational database (RDS) instances open, leading to extensive personal information leakage. This is only one of multiple data leakages that have occurred in the past year, providing threat actors with important information that can be leveraged into successful phishing attacks. Each holiday season during the last five years has consistently reached new heights in sales levels, but this also correlates with customer losses as more high-end spoofing websites keep appearing and luring more users into purchases.
While most financial entities are preparing for the year’s biggest weekend, the Threat Actors are constantly focused on the approaching Black Friday. The screenshot below shows that some of the Threat Actors and Groups are in active collaboration with each other, looking for additional tools for their arsenal.
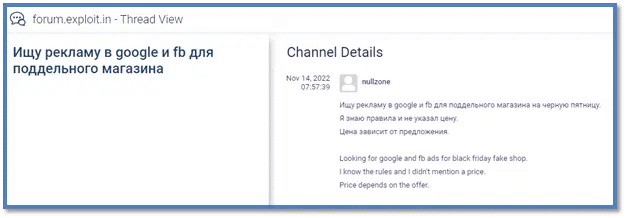
In the conversation above, a Threat Actor is preparing for his upcoming “fake shop” – a phishing site to be deployed when the clock strikes Black Friday. According to telemetry data, there has been an observable increase in malicious activities aimed at the financial sector. This includes phishing websites and, compromised payment cards and credentials.
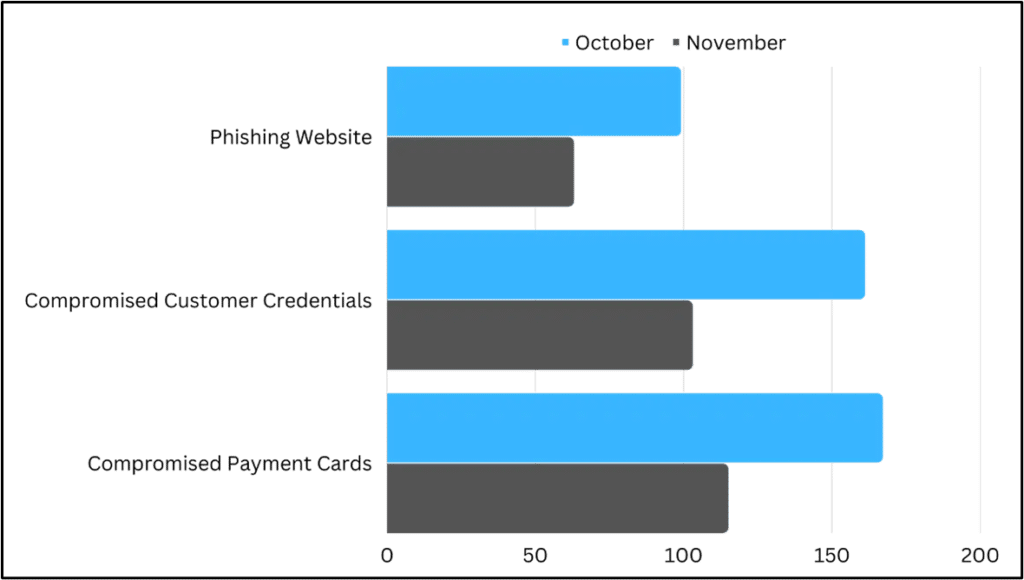
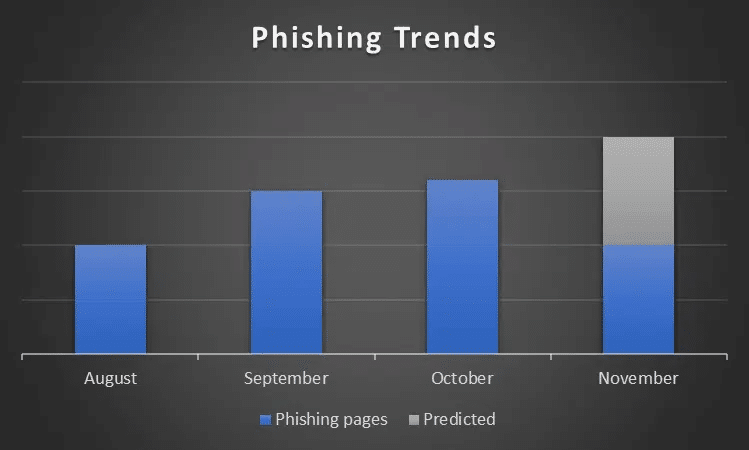
While just into the second half of November, data shows that the number of malicious activities targeting the financial sector is already catching up with last month’s data. Although there are several factors to consider, the increase is an indicator that the offenders are intensifying activity in preparation for the coming Black Friday and Cyber Monday tradition – a tempting opportunity for them to be able to cash in.
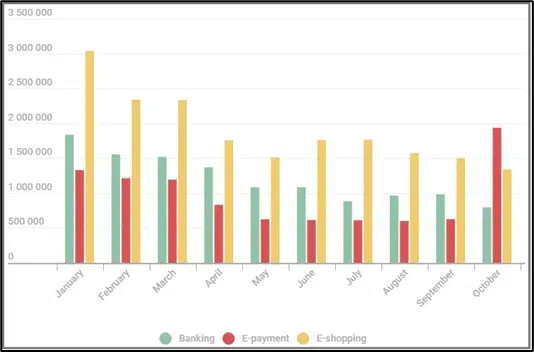
Looking back at the previous year’s trend, Threat Actors who specialize in phishing stepped up their game to steal account credentials for e-payment (electronic/online payment) platforms. October 2021 saw the activity doubled, compared to the month before.
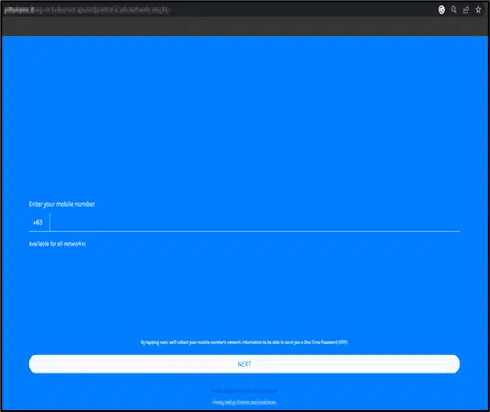
While banking credentials are still mostly targeted, as of this writing, phishing actors are shifting to e-payment systems, as those have risen in popularity by a wide margin during the last two years.
Despite recent news of the expected economic downturn and the impact of the Covid pandemic of 2019-2021, it is predicted that holiday sales in 2022 will stay strong, and even grow by $20 billion dollars, according to the ‘National Retail foundation’. While consumers are predicted to remain resilient, so, too, are the Threat Actors preparing for the season with increased fraud and cyberthreat activity, taking advantage of retailer discounts, higher sales volumes and fraud controls that are often relaxed in order to improve buyer experience.
Consequently, this also increases Threat Actors’ desire to invest more in fraudulent e-commerce websites and sophisticated phishing sites to steal customer credit cards and credentials. As a result, the risk of fraudulent purchases rises, exposing businesses to increased legal claims and potential financial liability.
One of the most popular techniques makes use of “site cloning”, whereby Threat Actors duplicate customer interfaces by copying their source code and leveraging them to harvest customer credentials or sensitive personal identity information. The second most popular cloned brand (after Microsoft) is PayPal, which is exploited for fraudulent purchases on various retail platforms. Threat Actors later sell the products at a discount on other marketplaces.
On our Argos Threat Intelligence platform, we have also detected an overall increase in Threat Actor engagement and various “buyers” for the aforementioned activities, due to the various “Black Friday Sales.” We also expect increases in fraudulent purchases on the various retail platforms and credential-stuffing activities, since Threat Actors can demand a premium for credentials that were verified in advance.

With Microsoft being the most impersonated brand, employees are constantly at risk, especially with the expected promotions for Black Friday and holiday gifts. As it is not unusual to receive holiday gifts or vouchers from the employer during the holidays, employees are more prone to fall for phishing scams, particularly if the phishing emails are able to successfully mimic the company email domain.
Sophisticated Threat Actors are expected to capitalize on this expectation with phishing campaigns that target several sectors. This might be demonstrated by forcing employees to confirm their credentials before they can “acquire” the purported gift from the company, or by sending fake Gift Cards. These harvested credentials can later be used by threat actors to exfiltrate sensitive, internal information and even access internal systems that will authorize these credentials or similar ones.
Much like the others, bigger Threat Actors and Groups have markets (black market), too, in which they also offer deals and discounts to the small timers for leaks involving data from financial entities, such as banks.
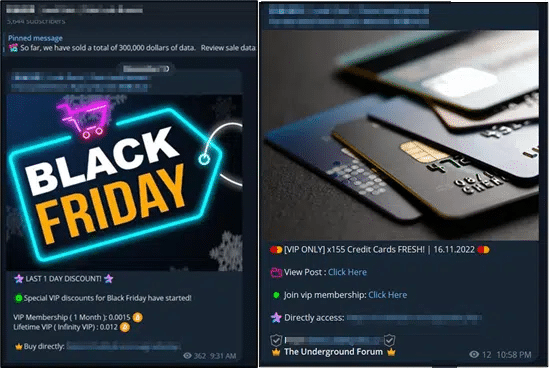
At the top of the echelon, bigger threat groups are also preparing for their Black Friday sale. The group is known to be actively involved in data breaches and leaks against large, leading companies all over the world, particularly targeting financial companies.

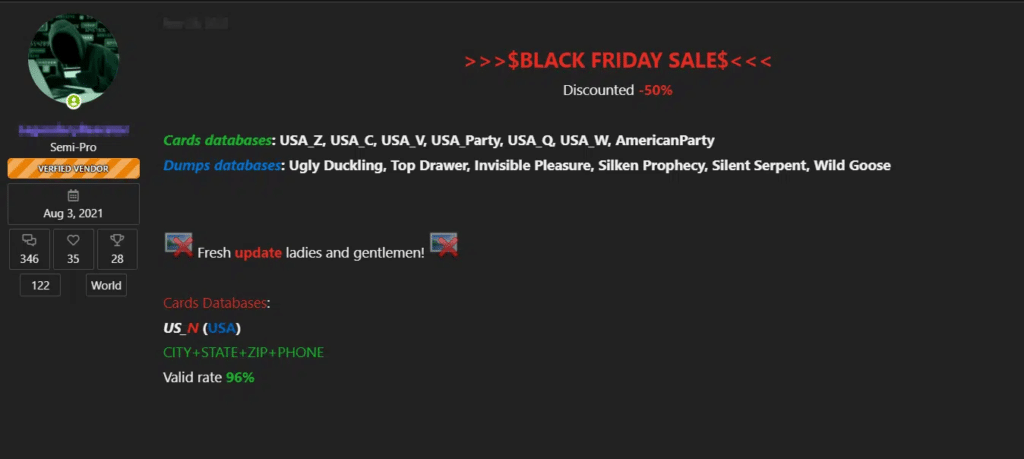
We all know that with the coming sales and discounts for Black Friday, Threat Actors will try to utilize stolen Financial Data to purchase bargain deals online to monetize their illegal assets. As seen in the screenshot below, many of the Threat Actors with expertise in Payment Card theft are at peak activity to prepare for the coming black Friday, since this is the peak season to purchase digitally. As such, they are selling stolen online banking accounts for use by whoever purchases the stolen data.
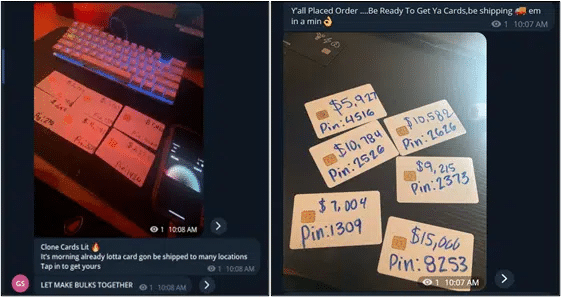
Clone Cards are in a special situation for the coming sale. They are very tricky for Threat Actors to use, but at the moment they still work. With the coming Black Friday Sale, Cyberint predicts widespread use of illegally cloned payment cards from the black market.
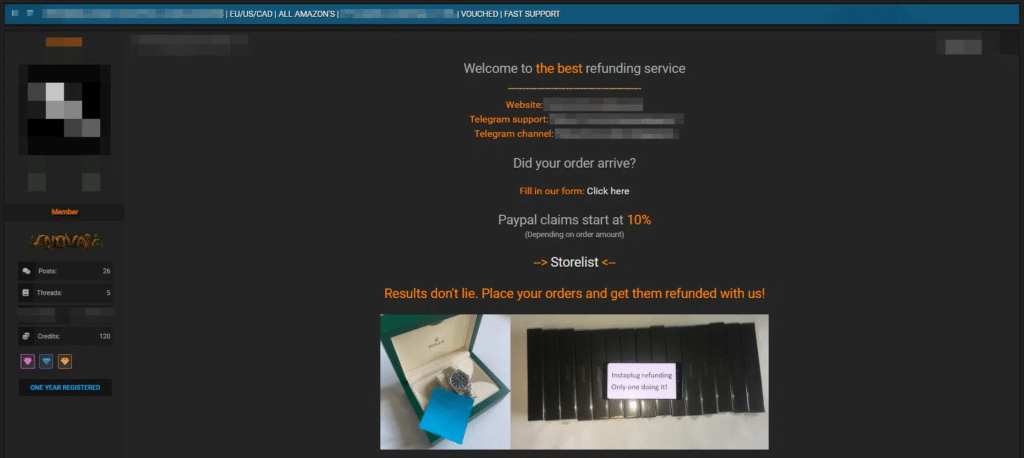
Fraudulent refund services and tutorials are still prevalent on dark web forums. Threat actors file fraudulent chargebacks, claiming that the products have not arrived or were not the products purchased and exploiting retailers’ good faith policies. The business impact for retailers is direct revenue loss, especially compounded when combined with the sales expected by consumers on Black Friday.
Fill in your business email to start