



Experienced in various public diplomacy projects, OSINT, WEBINT, analytical research, troubleshooting, intelligence gathering, auditing, and more.
In this blog we will cover what we know about the Finastra breach, what we know about who might have been compromised and an analysis of the validity of the Threat Actor abyss0.
On November 8th a threat actor (TA) known as “abyss0” posted on BreachForums, a well–known online platform for illicit data trade, and claimed to have exfiltrated and put for sale 400 GB of data from Finastra using IBM Aspera. The data, allegedly taken from Finastra’s Enterprise Service Bus, claimed to have various file types and documentation. The reported breach, which the threat actor claimed to occur in November 2024, has not been officially confirmed or denied by Finastra. The user “abyss0” has a history of leaking and selling data breaches on the forum, and has a credible reputation.
Since then Finastra have formally acknowledged the alleged breach and have announced that they are investigating it.

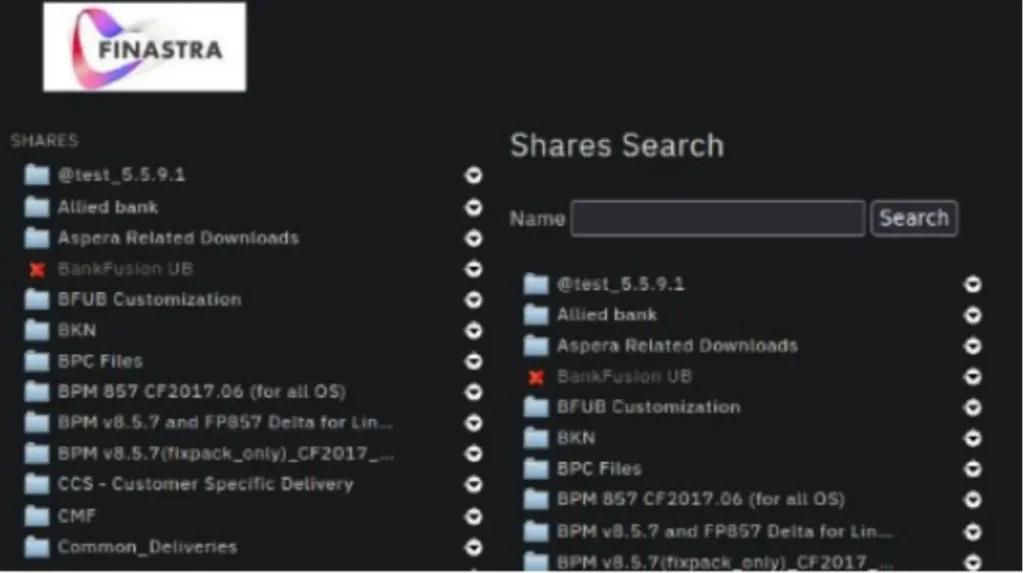
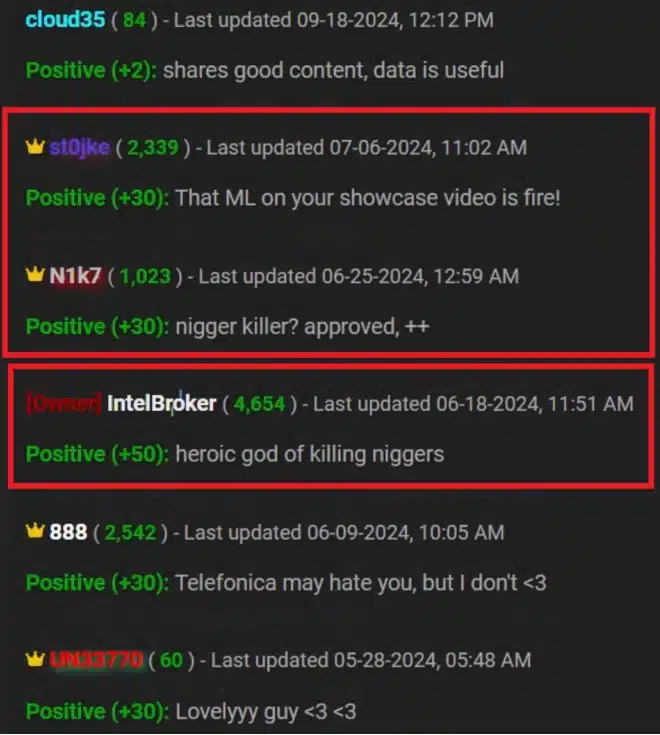
With that taken into consideration, it is plausible to assume that the TA either managed to sell the data, resulting in the closing of the thread, or removed it without selling it. After conducting an extension OSINT search, Cyberint searches, and various monitoring of the Threat Actor’s threads and posts it appears that threads are credible, created and deleted daily pertaining to different leaks and breaches.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


