First published July 16th, 2024
The Handala Hacker Group takes its name and symbol from Handala, a character created by Palestinian political cartoonist Naji al-Ali in 1969. Handala is depicted as a 10-year-old boy who turns his back to the viewer, symbolizing his rejection of foreign-imposed solutions to the Israeli-Palestinian conflict. The character represents the steadfastness and resilience of the Palestinian people and has become an iconic symbol of their struggle.

Handala’s origin reflects deep roots in Middle Eastern culture. The name is derived from the Arabic word “Hanzal,” (Arabic:” ل ظنح”) referring to a plant known for its bitter fruit and ability to regrow after being cut, symbolizing resilience and persistence.
The group’s primary online presence is a Telegram channel with over 3,500 subscribers, established on December 18, 2023. They also maintain a Twitter account with 270 followers, a backup Telegram channel, and a Telegram data leak channel set up on April 2, 2024. Following the shutdown of their previous website (handala[.]cx), they launched a new one, handala[.]to, on May 25, 2024. Handala has positioned itself as a capable and serious threat to Israeli cybersecurity, particularly targeting critical infrastructure.
Their activities are characterized by sophisticated cyber-attacks, including phishing campaigns, ransomware, and website defacements. They frequently release partial evidence of their successes to maintain a reputation as a significant threat, even when the full extent of their claims is not verifiable.
Since its establishment, the group presented itself as a highly capable cyber-attack group that poses an actual threat to Israel by targeting essential entities and infrastructures while challenging and antagonizing the Israel National Cyber Directorate, which is responsible for those target’s cyber- defense.
Cyberint chose the following instances to exemplify the group’s Modus Operandi, agenda, and most impactful activities against Israel.
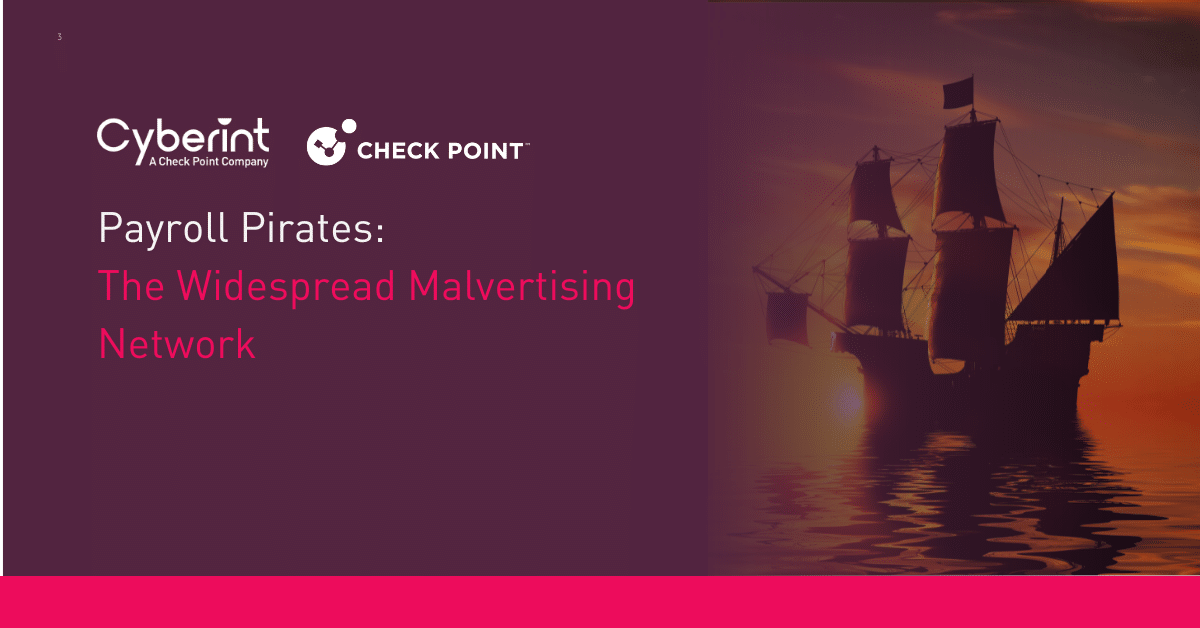
As mentioned, the group’s official Telegram channel was established in December, after Hamas’s horrific attack on October 7, 2023. Interestingly, on December 26 a group shared a post that showcased itself only once as a “small fighter” in the Hamas movement due to an alleged Israeli airstrike attack that killed an important figure in Iran’s Revolutionary Guards, Sayyed Razi Mousavi, who endorsed the Palestinian resistance.
Additionally, the group took responsibility for cyberattacks targeting Israeli citizens using Phishing. This attack is considered part of Iran’s retaliation,emails disguised as F5 important security updates which indicates that the group has a connection or financial support for the aforementioned assassination. It refers to an Al-Arabiya article about the Israeli Cyber Security Directorate (INCD) warning against such attacks.
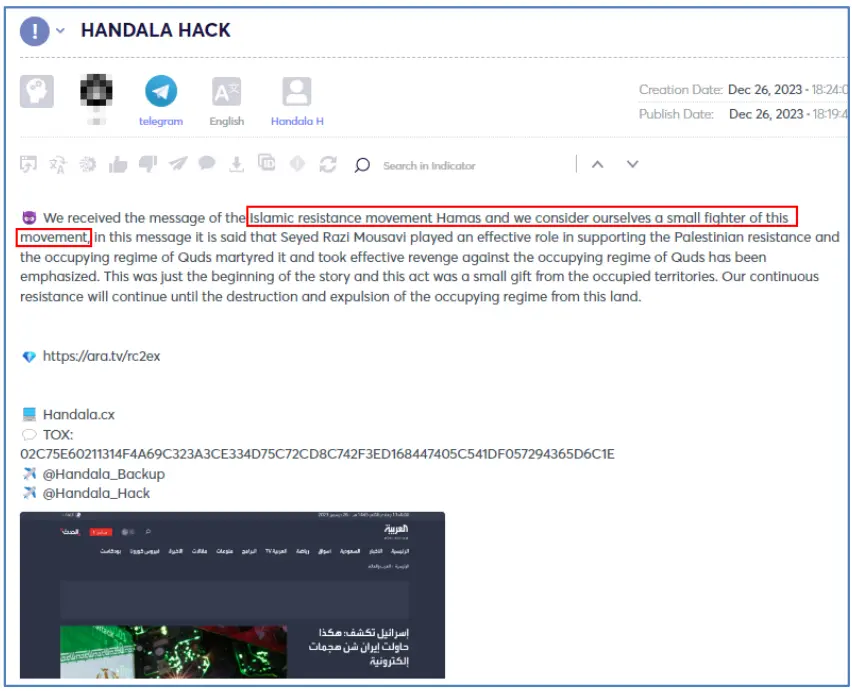
Even though Hamas wasn’t mentioned once more, the group is affiliating itself to the ongoing war between Israel and Hamas by posting “We stood by Rafah” on February 13, around the time the Israeli government ordered the IDF to start planning a military operation in Rafah, and alongside a malicious campaign of multiple Israeli websites defacement and alleged data leakage that took place on February 27th.
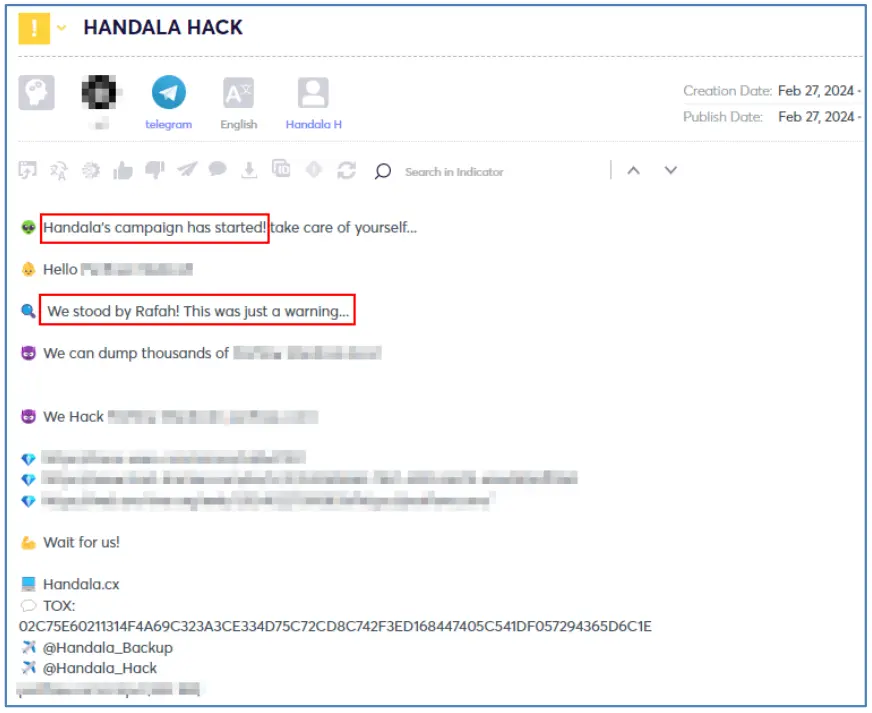
Iron Dome systems and sirens are high-level targets for hacktivist groups due to the potential damage from their malfunction. While these are mostly attacked by Distributed Denial of Service (DDoS) attacks, Handala, positioning itself as a more capable group, claimed on March 3 to have successfully hacked into a multi-purpose tactical radars company called DRS RADA.
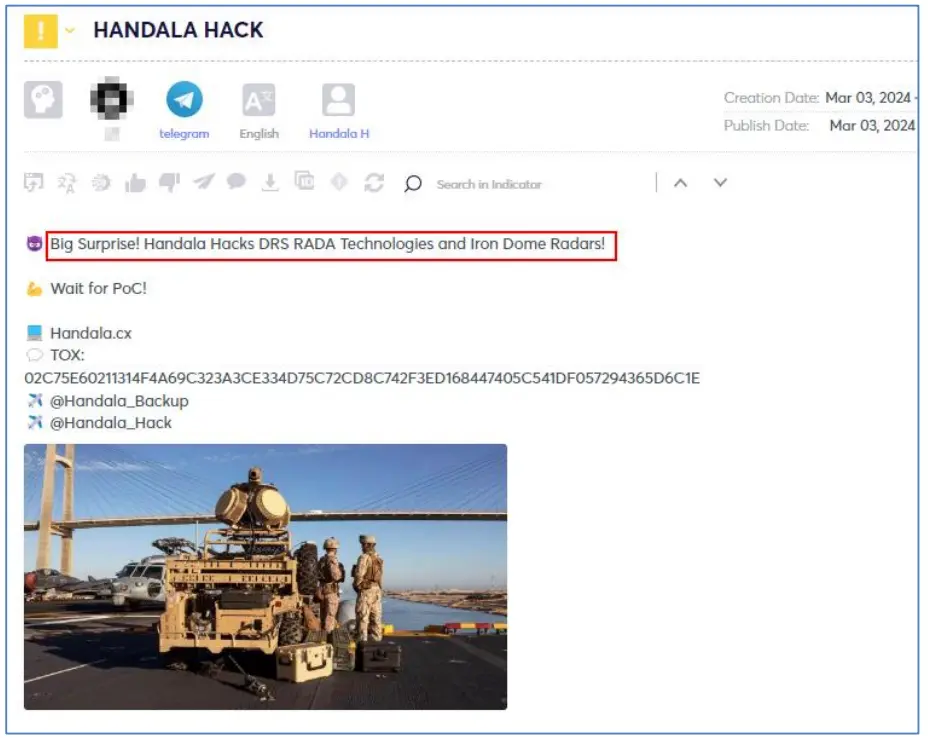
The provided evidence includes multiple screenshots of allegedly internal system interfaces, defacement of the websites rada[.]com and rada[.]co[.]il, and the threat to leak 2 terabytes of data. Further analysis indicates that the DRS RADA official website is drsrada.com, while the defaced websites were indeed attacked but are currently inaccessible. No related leaked data files were shared.
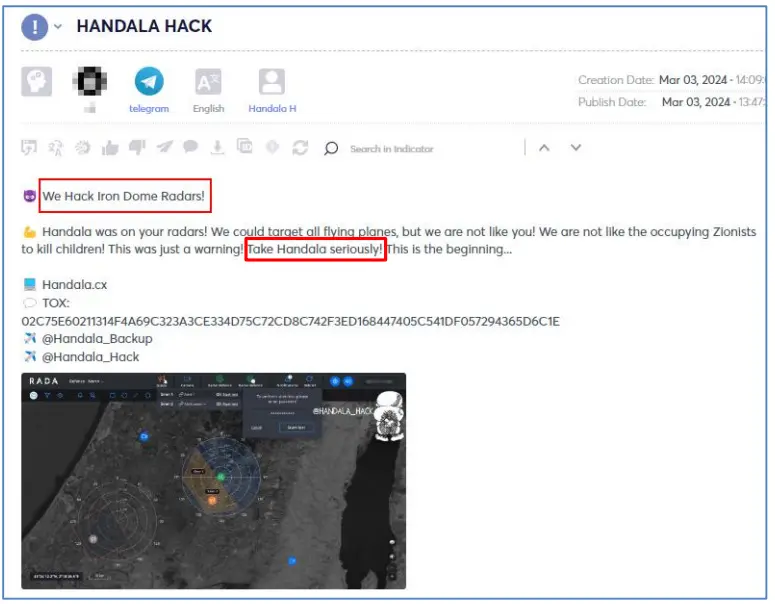
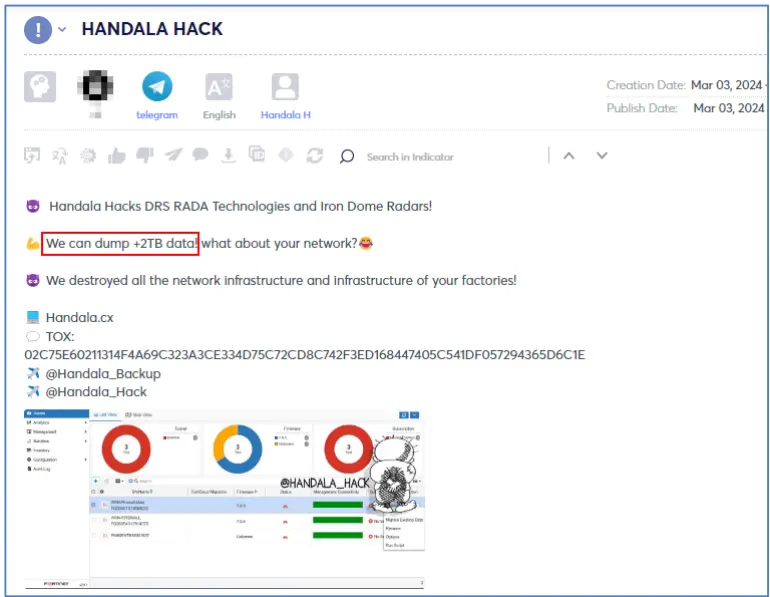
Although the defacement attack appears successful, it is unclear whether the internal interface and data were indeed compromised. The group emphasizes that Handala should be taken seriously, implying that the partially provided proof of concept led the group to believe that Israel perceived it as unsuccessful or under-skilled.
On June 1, fear grew among the citizens of Ma’ala Yosef regional council after receiving an alarming SMS text message in Hebrew:

The message contained a download link to MyCity mobile application, which offers crisis management solutions for local authorities. The incident was confirmed as a cyber-attack by Israeli media. On June 3, Handala claimed responsibility, suggesting it is involved in more cyber-attacks targeting Israel that are not always disclosed by the group. This correlates with the group’s behavior of providing partial evidence of successful attacks while stating there is more potentially compromised data without actual evidence, presenting the group as a prominent threat regardless of the facts.
The group also shared a short video clip demonstrating how the false message was allegedly sent by them.
On June 15, 2024, Handala claimed responsibility for a ransomware attack on Ma’agan Michael Kibbutz, exfiltrating 22GB of data and sending over 5,000 warning SMS messages. The ransom message criticized the kibbutz and Israel, highlighting the group’s political stance.
Ma’agan Michael Kibbutz, one of the largest and most financially independent kibbutzim in Israel, has diverse economic activities and relies on modern technologies in agriculture and industry. Handala likely used sophisticated phishing campaigns to gain initial access, employing malware known for its obfuscation techniques.
The attack underscores the ongoing threat posed by ransomware groups like Handala, highlighting the need for robust cybersecurity measures to protect against sophisticated threats.
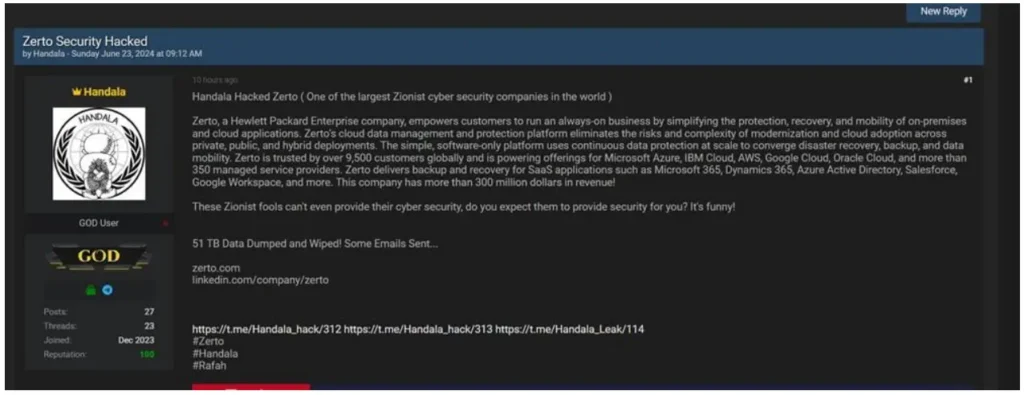
Handala, recently claimed responsibility for a significant cyber-attack against Zerto, a subsidiary of Hewlett Packard Enterprise (HPE) specializing in disaster recovery, ransomware resilience, and cloud data management solutions. The attack was publicized on a prominent dark web forum, highlighting Handala’s political motivations rather than financial gain or industrial espionage.
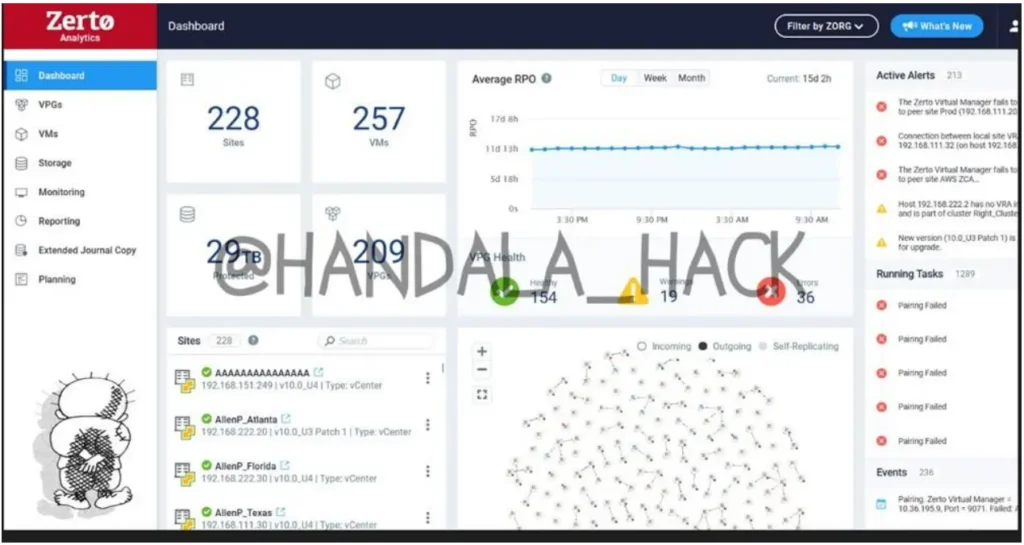
According to Handala’s claims, the attack on Zerto involved the exfiltration and subsequent deletion of a massive 51 terabytes (TB) of data. This trove of data purportedly included sensitive customer information, backup configurations critical for disaster recovery, and proprietary intellectual property such as source codes and algorithms developed by Zerto. Additionally, operational data revealing internal IT infrastructure details was also allegedly compromised.
The attack was accompanied by a statement mocking Zerto’s cybersecurity capabilities, framing it within Handala’s broader narrative of challenging Israeli technological prowess. This narrative aligns with Handala’s previous cyber activities, which have targeted Israeli defense systems, infrastructure, and technology sectors as part of their ideological campaign.
The infiltration and deletion of such a vast amount of data represent a severe operational and reputational blow to Zerto. Beyond immediate financial implications, such breaches undermine customer trust, potentially exposing sensitive corporate and client data to exploitation or misuse.
Moreover, Handala’s demonstration of capability in executing such a sophisticated attack underscores the evolving nature of cyber threats driven by geopolitical tensions and ideological motives. The incident serves as a stark reminder to organizations globally about the importance of robust cybersecurity measures and proactive defense strategies against politically motivated cyber threats.
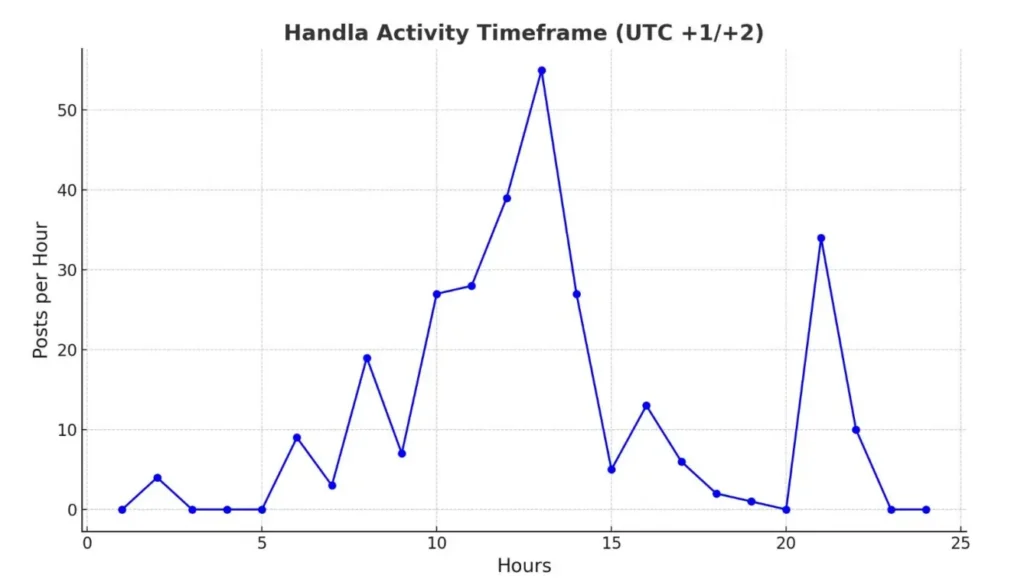
To determine the potential time zone of the threat actor based on their activity, we analyzed the pattern of posts per hour. The approach was:
1. Identify Peak Activity Hours – look for hours with the highest number of posts.
2. Consider Typical Daily Routines – people usually have more activity during their waking hours and less activity during sleeping hours. For many people, the highest activity is often observed in the evening hours (6 PM – 10 PM) as they have more free time to spend online.
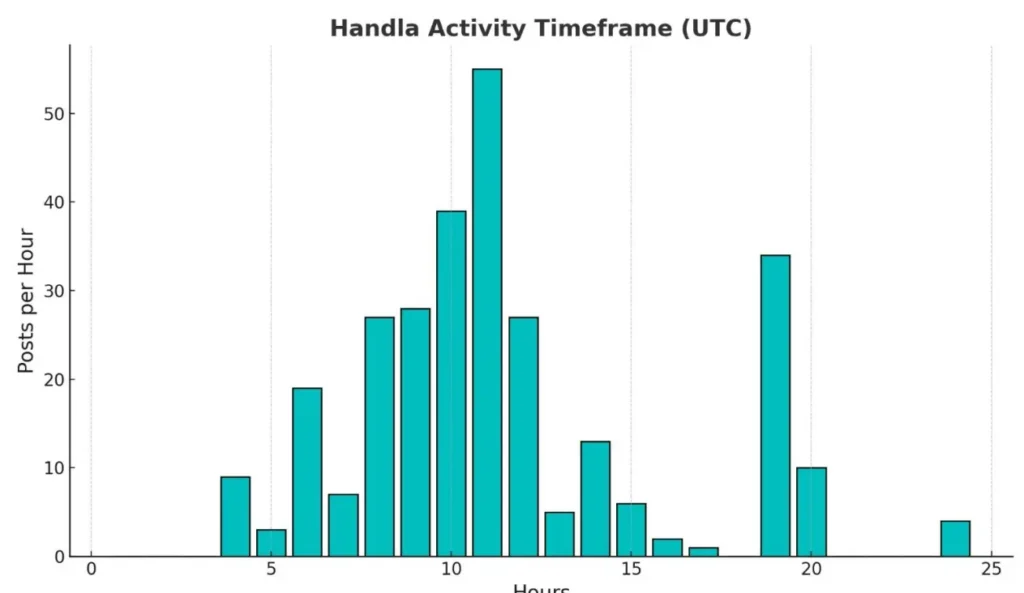
From the graph: To estimate the time zone based on peak and low activity times, we need to consider typical human behavior patterns, such as sleeping and waking hours.
Peak Activity Hours:
Low Activity Hours:
The use patterns suggest that the individual might be awake and active during the daytime and evening hours, which aligns with a typical daily schedule of being active in the morning and evening, and less active at night.
Hypothesis: The individual’s peak activity from 9 AM to 11 AM suggests they are likely starting their day, while the evening peak from 7 PM to 9 PM indicates activity before winding down for the night. Assuming a typical sleep pattern of 8 hours per night, their sleeping hours could be approximately from midnight to 8 AM.
These peak activity hours imply that the individual may be in a time zone where 9 AM to 11 AM and 7 PM to 9 PM UTC align with common active hours. A likely candidate is UTC+1 or UTC+2, depending on daylight saving time.
Considering the group’s focus on “the pain of the Palestinians” and the timing of their activity, it is possible to narrow down the origin of the group to a limited number of countries: Israel (Gaza/West Bank) Lebanon, Egypt, Algeria, and Morocco.
31.192.237[.]207:2515 https://sjc1.vultrobjects.com/f5update/update[.]sh 8f69c9bb80b210466b887d2b16c68600 8bdd1cb717aa2bd03c12c8b4c9df2d94
| SHA256 | Type | File Name |
|---|---|---|
| fe07dca68f288a4f6d7cbd34d79bb70bc309635876298d4fde33c25277e30bd2 | Windows Executable | NET F5UPDATER.exe |
| ca9bf13897af109cb354f2629c10803966eb757ee4b2e468abc04e7681d0d74a | Windows Executable | NET F5UPDATER.exe |
| e28085e8d64bb737721b1a1d494f177e571c47aab7c9507dba38253f6183af35 | Windows Executable | NET Hatef.exe |
| 454e6d3782f23455875a5db64e1a8cd8eb743400d8c6dadb1cd8fd2ffc2f9567 | Windows Executable Delphi | Handala.exe |
| 6f79c0e0e1aab63c3aba0b781e0e46c95b5798b2d4f7b6ecac47 4b5c40b840ad | Encrypted bash script | update.sh |
| ad66251d9e8792cf4963b0c97f7ab44c8b68101e36b79abc501 bee1807166e8a | ZIP | |
| 64c5fd791ee369082273b685f724d5916bd4cad756750a5fe95 3c4005bb5428c | ZIP | |
| 336167b8c5cfc5cd330502e7aa515cc133656e12cbedb4b41eb bf847347b2767 | Windows Executable | Flash Develop |
| f58d3a4b2f3f7f10815c24586fae91964eeed830369e7e0701b4 3895b0cefbd3 | AutoIt Interpreter | Naples.pif |
| aae989743dddc84adef90622c657e45e23386488fa79d7fe7cf0 863043b8acd4 | Obfuscated Auto It Script |