


Remote Desktop Protocol (RDP) is a communication protocol developed by Microsoft, which provides a user with a graphical interface to connect to another computer over a network connection[1]. Once connected, the remote user will be able to communicate with the machine using their input devices, keyboard and mouse, and to have their screen displaying the output of their actions – as if they were physically connected. Simply put, gaining access to your crown jewels.
Common use of this protocol would be IT personnel performing maintenance, or support teams providing training and assistance to end-users. It is also a useful tool for remote employees who want to connect the organization’s resources.
The protocol gained popularity, that naturally increased[2] during COVID-19 as most organizations moved to working from home; however, it was also noticed by malicious actors, who saw this as an opportunity to access organizations’ internal networks, steal or corrupt information.
Figure 1- RDP login interface
As a result of the exclusive capabilities RDP enables once in-use, RDP servers became an attractive target for cybercriminals. The first stage of an attack in which this protocol is leveraged must include the detection on an internet-connected RDP server. The selection for detection tools is large, ranging from legitimate PT port scanning tools such as Nmap, to shady port scanners shared within the threat actors’ community[3]. These scanners flag IPs that have an open port 3389, the default RDP port. Then, the vulnerable server will face 1 out of 3 main attack vectors, depending on the sophistication and experience level of the attacker:
In the past few years, the cyber-security community discovered several critical exploits (risk rate is 9.8), that render RDP servers vulnerable to remote code execution:
From authentication perspective, obtaining the credentials of an RDP server is a similar effort to other ATO attempts, using brute-force tools and dictionary attacks. Threat actors that choose this methodology rely on the unfortunate habit of using default or weak passwords.
Even with poor technical skills, a beginner could register to one of the many dark web marketplaces, and purchase RDP access. These were likely obtained through one of the methods above, and are sold for a limited timeframe. The listings start from surprisingly low prices, only a few dollars, and get higher according to machine’s geo-location, its content, and what it has access to.
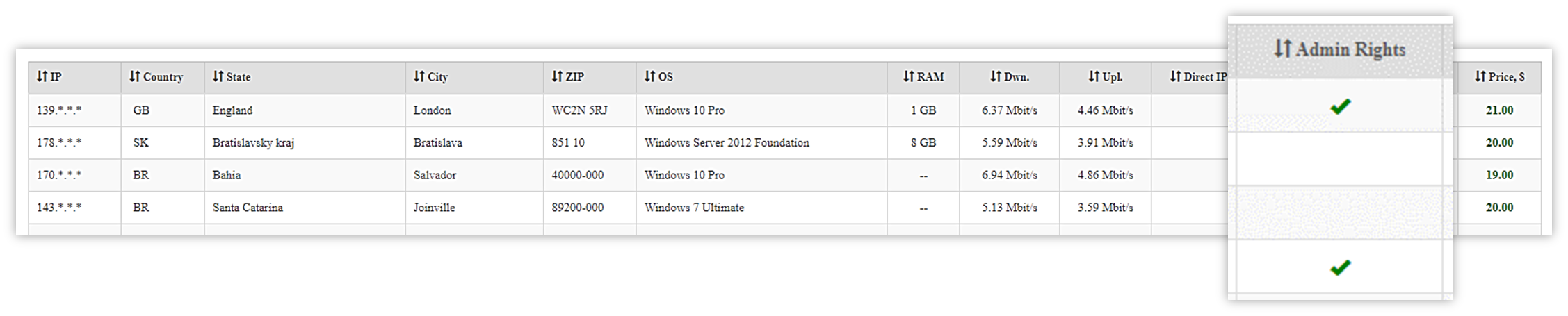 RDP marketplace listings, specify whether the server has Admin privileges
RDP marketplace listings, specify whether the server has Admin privileges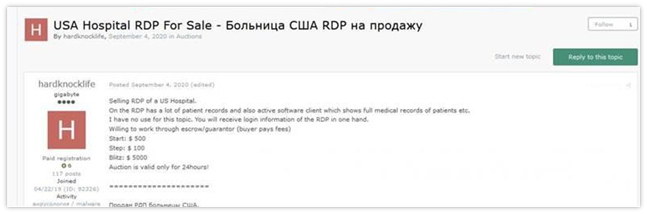
Listing on an RDP designated section on an underground forum
As part of its online monitoring, Cyberint identified an RDP access for a server of a home furniture retailer, which is offered for sale in an online marketplace.
In the listing, the threat actor mentions that the hacked RDP server in question contains a back-up database. Furthermore, the TA provides 3 screenshots allegedly taken from the compromised machine, as an evidence for the compromise; one of them shows the properties window of a 15.3 GB DB.
Once purchased, the information disclosed by the screenshot and the rest of the machine’s content are at risk of theft and/or corruption. It is worth mentioning that besides the business impact, such attack can also harm the customers of the retailer, which may result it customer churn and lawsuits.
Now more than ever, in the times of COVID-19, organizations around the world are relying on the RDP protocol for effective and productive work environment. Nevertheless, the protocol has several security flaws that make it a popular target of malicious actors. In order to avoid the potential risk of using RDP, Cyberint recommends taking the following precautions:
[4] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2019-0708
[6] https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-0610
Fill in your business email to start


