


A lot has happened since the emergence of social networking began in the early 2000s. Since then, many people have relied on social media platforms to stay connected with friends, family, community, and more. With this popularity, cyber criminals also took advantage of this trend.
As more features are introduced to well-known social media platforms, mainly Meta (formerly Facebook)—which also includes Instagram, WhatsApp, and Messenger—more tools are also added to the scam operators’ arsenals.
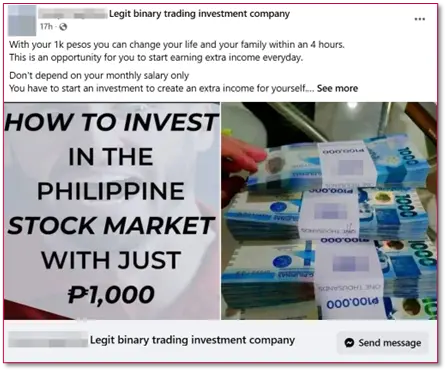
In 2024, several scam operators targeting the Philippines took advantage of Meta’s Ads and some online tools for creating Social Cards—a digital card-like photo with a description and an embedded link that can be shared on social media platforms—to conduct fraudulent activities impersonating local brands.
Over the past months, Cyberint has observed various social media poisoning campaigns, such as the distribution of fake mobile applications related to fake loaning services and fake job opportunities being promoted through different Facebook pages and Ads impersonating local brands.
Scam operators will likely continue to impersonate well-known organizations, mainly in the Financial, Technology, Telecommunications, and Business sectors, through social media platforms targeting Philippine organizations.
Therefore, Cyberint considers this a high risk not only for local entities but also for Filipino citizens in general. With the latest social media technologies, scam operators will continue to conduct nefarious activities, such as Phishing, Love Scam, Job Scam, Fake Loaning Services, and more.
Nowadays, social media platforms are being used by many individuals for digital marketing, such as product advertisements, promotions, and more. On the other hand, some individuals are fond of spreading fake news across social media platforms.
In line with this, the news feeds of social media users will always be flooded with hot and trending topics via the latest data analytics and machine learning technologies incorporated with these platforms.
The method of leveraging the latest technologies and digital marketing for false promotions is dubbed “Social Media Poisoning.”
Over the past few years, many Filipinos have applied digital marketing to their business and services. With this, many products and services are now being promoted through social media advertisements and promotion technologies.
On the other hand, the rise of these digital marketing features also opened a gateway for threat actors and scam operators to promote fake products and services, such as investments, fake mobile applications, and more.
By combining the latest technologies and digital marketing with trending topics, users learned a new way to distribute and promote their products being offered on third-party e-commerce platforms.
In this technique, one will create a Social Card with a customized photo (i.e., trending photo) and embed a redirection link, then post this on their social media feeds. One of the indicators of a social card is the “ⓘ” icon within a post.
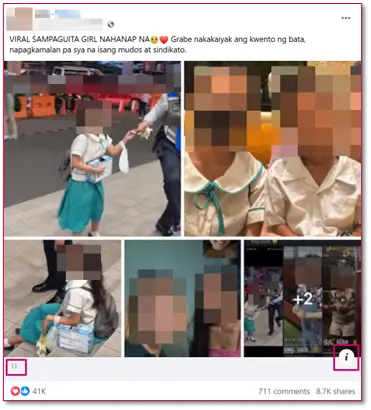
The typical method being used by social media users (see Figure 2 above) is to add trending pictures—make them look like a thumbnail—to lure viewers into clicking it and redirect them to a specific product of an e-commerce website by embedding the product link to the photo.
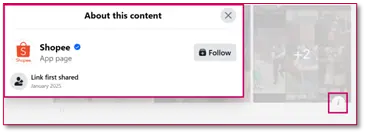
Recently, most of the posts leveraging social cards are redirecting to a legitimate website. However, threat actors might take advantage of this technique to incorporate Phishing URLs within a trending photo.
Over the past years, Meta’s Facebook and Instagram were one of the most used platforms for digital marketing. Thus, making its Ads Manager a powerful tool for disseminating ad campaigns and promotions.
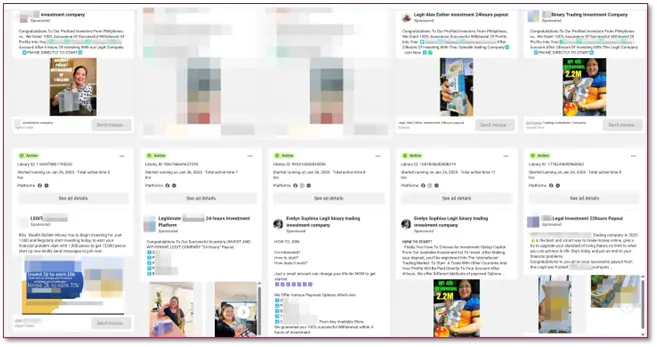
Meanwhile, Cyberint (a Check Point company) has observed a rise in malicious ad campaigns targeting well-known local organizations by impersonating their brands, products, and services over the past few months.
Below is the simple flow for the modus behind these fake advertisements:
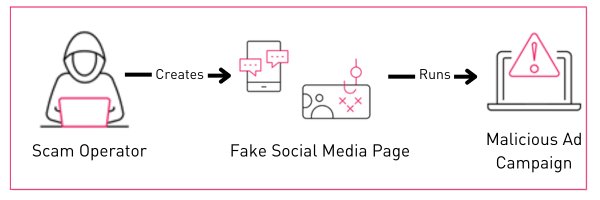
Recently, many social media users gained access to online services offering Social Cards. Users can craft customized social cards, where they can embed a photo, description, and URL. Below is an example of an online tool—ANYIMAGE.io—for social card creation, together with some techniques used by users to hide the card’s title and description or even modify the displayed domain (for premium accounts):
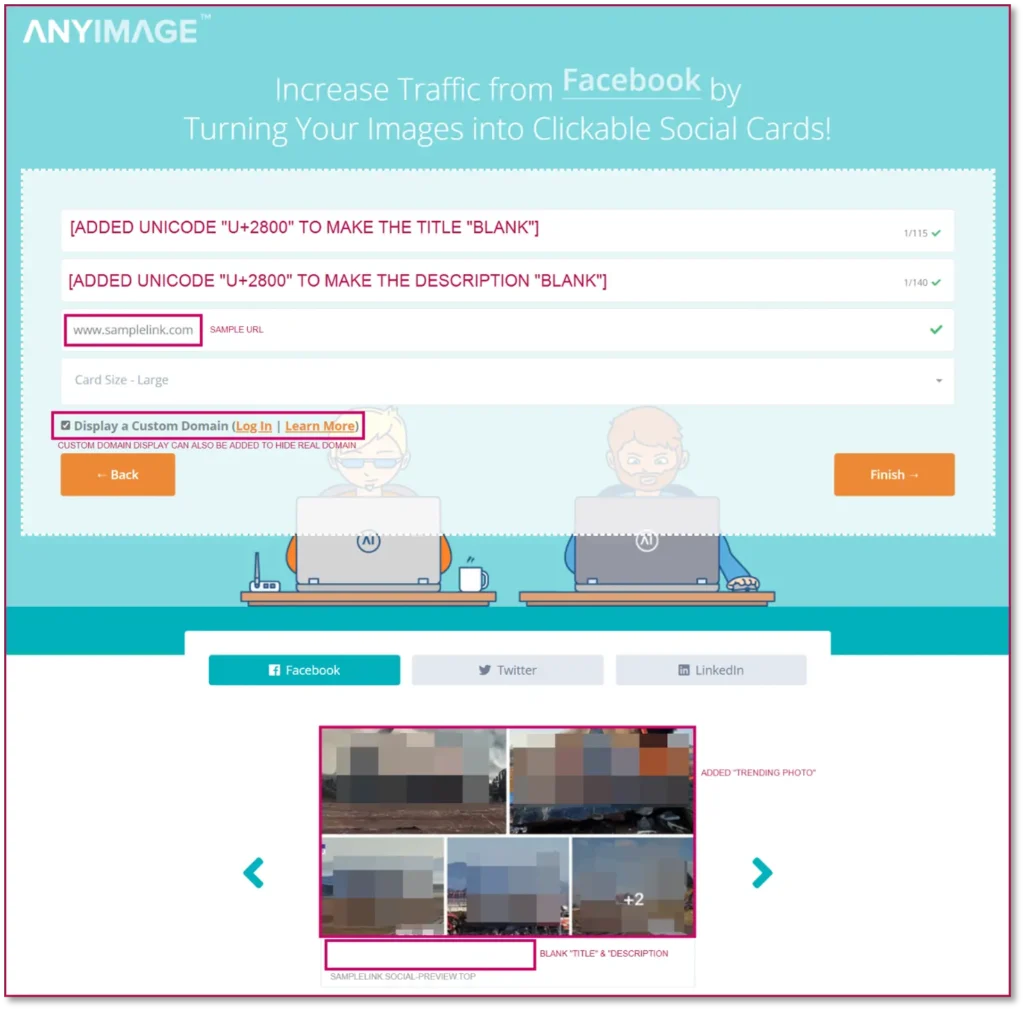
Although most users only use these to promote legitimate products and services by adding a trending photo and embedding a non-related URL in the so-called card, scam operators can leverage this feature to conduct scam operations in the future.
Below is a flow diagram on how scam operators can leverage social cards to conduct malicious ad campaigns:
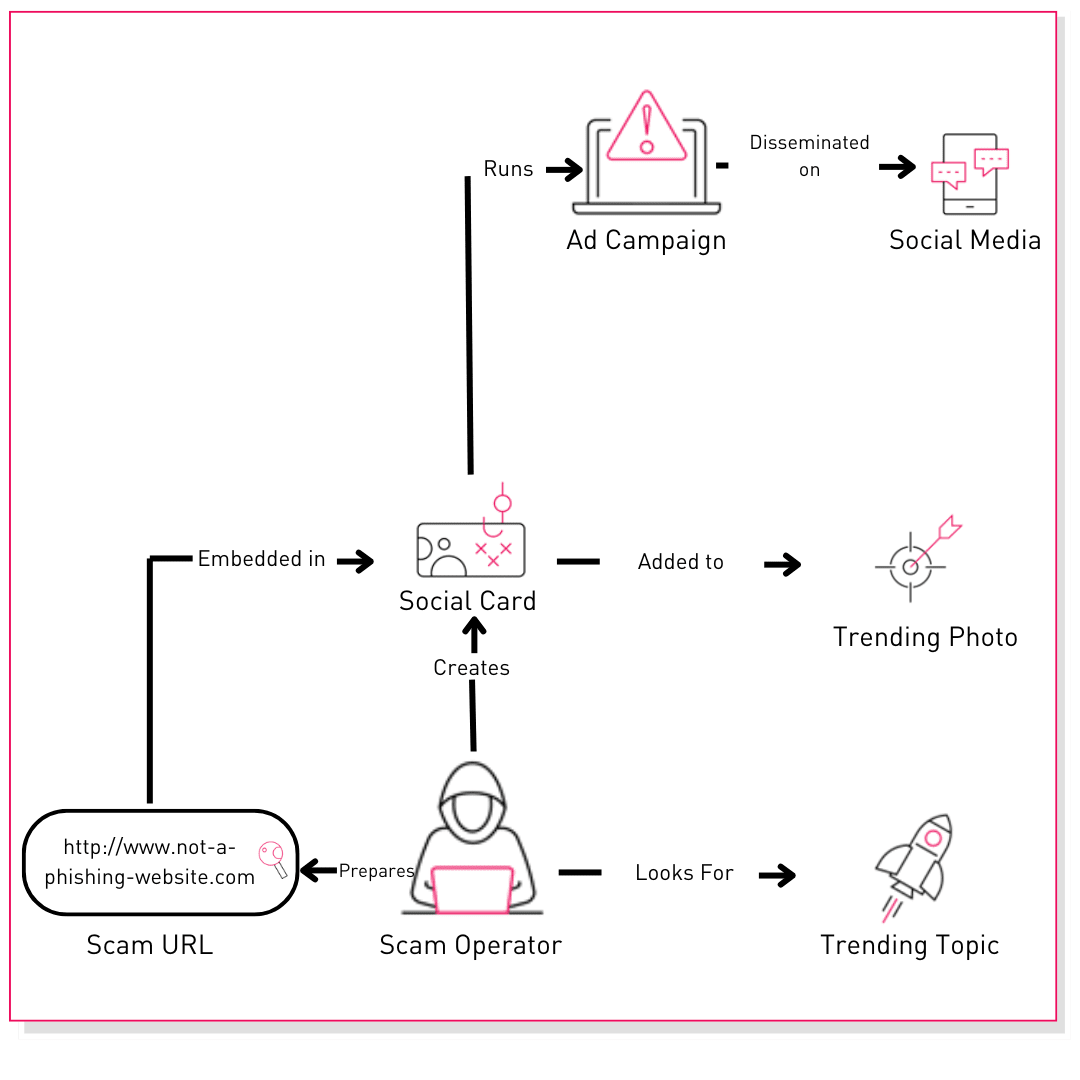
Based on observations from past fraudulent activities, it is common for regular users to click on anything that piques their interest when browsing their social media feeds. Therefore, with social cards, scam operators can easily lure social media users, especially those who are avid followers of trending topics.
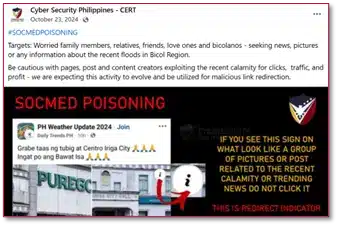
A local non-profit organization—Cyber Security Philippines – CERT—also posted an awareness during the 4th quarter of 2024 regarding Social Media Poisoning.
As part of Cyberint’s (a Check Point company) service to our clients, we ensure that social media impersonation targeting our clients’ brands and employees (VIPs) are monitored regularly.
Nowadays, scam operators are shifting to social media impersonation activities to easily conduct fraudulent activities targeting well-known companies to effectively lure users into trusting their social media postings and ad campaigns.
Recently, we have observed fake mobile applications distributed by random social media pages through ads. One of them—a fake loan application—has been registered on Google Play Store, making it look more reliable for regular users. The link to the said mobile application is also added from the fake ads impersonating well-known local brands.
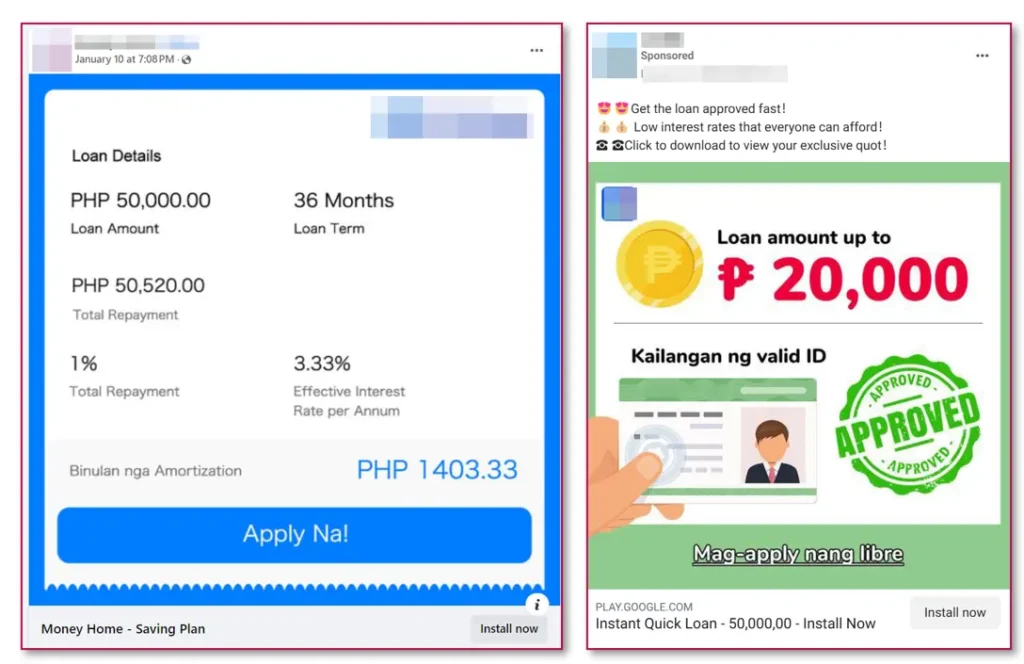
The operators behind these fake mobile applications, mostly related to fake loaning services, are utilizing various social media pages to distribute these ads.
Aside from fake mobile applications, scam operators are now leveraging social media ads for phony job opportunities.
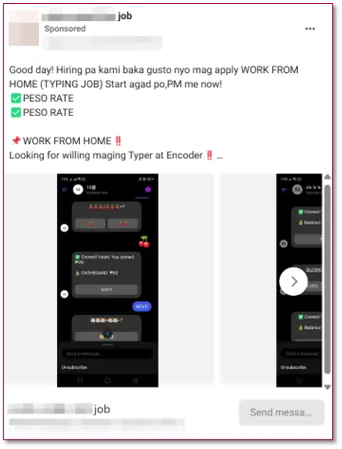
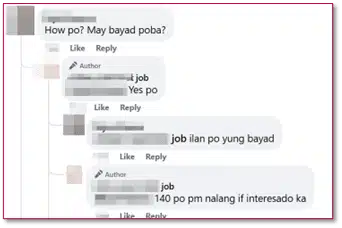
These fake job opportunities usually require a potential applicant to pay a registration fee to start with the so-called job.
With the rise of digital marketing and AIs for social media platforms, Cyberint (a Check Point company) believes, with high confidence, that there will be a constant rise in terms of scam operations in the Philippines leveraging these technologies.
Threat actors and scam operators will continue to impersonate well-known organizations, mainly in the Financial, Technology, Telecommunications, and Business sectors, through social media platforms. With the use of these platforms, they can easily deploy different nefarious campaigns, such as Phishing, Job Scam, Investment Scam, Fake Loaning Services, Love Scam, and more.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

Fill in your business email to start


