Daniel is a seasoned cybersecurity product marketing professional with experience in cryptographic solutions, attack surface management, threat intelligence, and more.
In the world of cybersecurity, it’s widely understood that threat intelligence must be “actionable.” Although this is true, it’s just one characteristic of what makes threat intelligence valuable to a business. There are several other criteria that must be satisfied for intelligence to be impactful.
At Cyberint, we believe that impactful intelligence is the next step in the evolution of cyber threat intelligence. This post will discuss why this shift is needed and outline the requirements for impactful intelligence.
An Increasing Volume Of Cyber Attacks
Every organization with a digital footprint experiences cyber attacks. This is true no matter how small the organization’s digital presence is— even if it only consists of a website and several social media profiles, there are plenty of attack vectors for threat actors to leverage.
Of course, the vast majority of organizations have a much, much larger digital footprint than a single domain and a few social media accounts. Large enterprises often have thousands of IP addresses, domains, and subdomains to manage, typically spread out across different environments, from legacy on-prem data centers and private clouds to public clouds from multiple service providers and infrastructure hosted by third-parties like SaaS providers.
As if all of this complexity wasn’t challenging enough, the volume of cyber attacks is at an all-time high. By one estimate, cybercrime increased by 38% year-on-year from 2020 to 2021. The Anti-Phishing Work Group (APWG) observed over 1.2 Million phishing attacks in Q3 2022 alone, setting a new record for the highest number ever in a single quarter. The 2022 IBM X-Force Threat Intelligence Index reported a 33% increase in security incidents resulting from an exploited vulnerability. You get the picture—and it’s pretty grim.
Although many of these attacks are not sophisticated, the sheer volume of cyber attacks presents serious challenges. Large organizations receive a constant barrage of alerts every day, often with very low fidelity, so it’s not easy to effectively triage alerts and uncover the real threats. If one of the proverbial needles goes undetected in the corporate haystack, it could result in a breach.
This underscores a serious asymmetry in the cyber world: bad actors get unlimited attempts to breach the corporate network, but cyber defenders must have a perfect record to keep the organization secure. After all, it only takes one successful attack to cause serious financial damages to the enterprise.
Time For A Shift In Cyber Strategy
Not so long ago, the goal of the cyber defender was to prevent even a single cyber attack from taking place. Today, this is completely unrealistic. Rather than trying to stop every single attack, the most effective strategy is one of cyber agility.
Cyber agility focuses on identifying the real risks amidst a sea of alerts and responding to them as quickly as possible. The earlier a threat is detected and defeated, the smaller the chances that the attackers will be successful and cause harm to the organization.
So the question becomes: how can organizations accelerate the detection and elimination of a threat? The answer: impactful intelligence that improves visibility on relevant risks and minimizes response and takedown times.
Defining Impactful Intelligence
Intelligence must be actionable—otherwise, it simply wouldn’t be useful. Although it is a necessary condition, actionability alone is not sufficient for threat intelligence to be of value.
Threat intelligence must be impactful and have the following 4 properties:
This new framework views cybersecurity as a business challenge rather than a strictly technical problem. Consequently, this new paradigm requires cyber threats to be addressed in an efficient and cost effective manner.
Threat Intelligence: An Investment, Not An Expenditure
Cybersecurity is currently undergoing a fundamental shift where it is no longer seen as merely an expense. Now, cybersecurity is starting to be viewed as a business enabler. As a result of this change in mindset, security leaders must be able to measure and report the results of investments in cybersecurity tools and technologies.
In other words, threat intelligence can no longer be a line item. It must be an investment that provides measurable outcomes for the customer and helps the business prosper.
At Cyberint, we are committed to providing real value to customers along the following metrics:
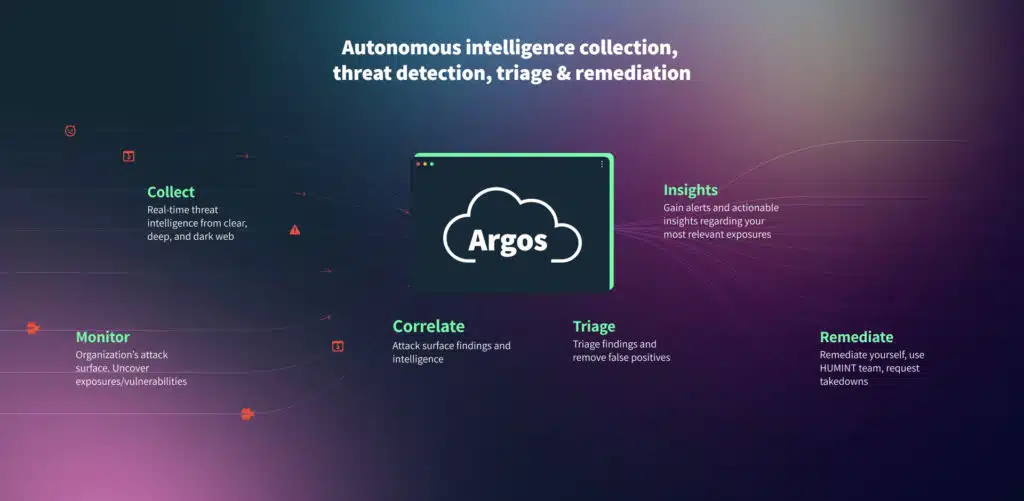
The Cyberint Argos Edge platform delivers these measurable results, helping security leaders to make a business case for deployment.
To schedule a trial of the Argos Edge platform tailored to your organization, submit this digital risk assessment form and Cyberint’s experts will get in touch.
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start