Threat Intelligence
Tired of playing catch-up? Our strategic & tactical threat intelligence turns complex data into sharp, actionable security advisories. Our military-trained analysts, fluent in cyber lingo and geopolitics, arm decision-makers with the wider perspective and meaningful trends.
Experience how our strategic threat intelligence has the edge
inspected daily
items/month
identified each day
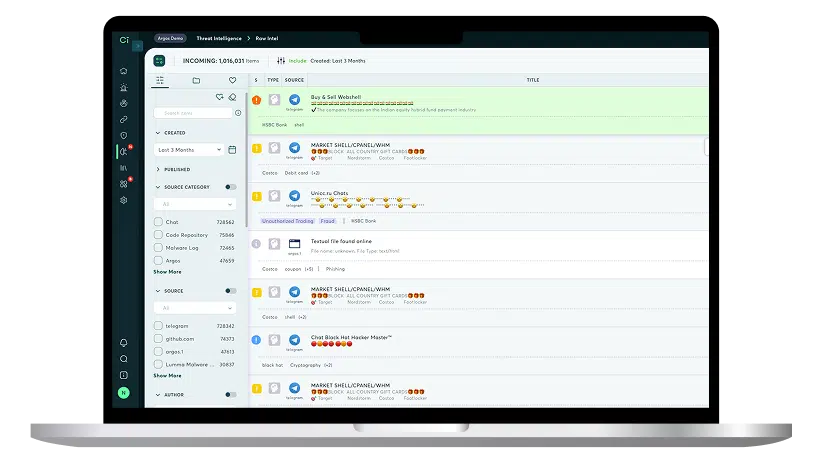
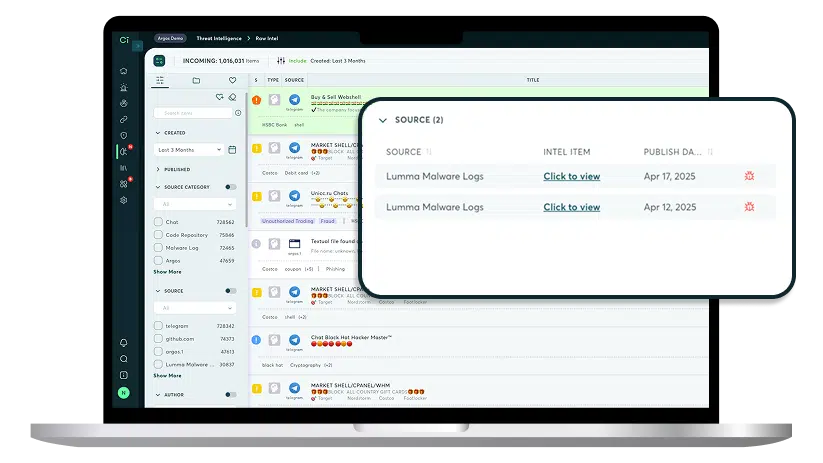
No More Guessing: Threat Intelligence & IOC Feeds
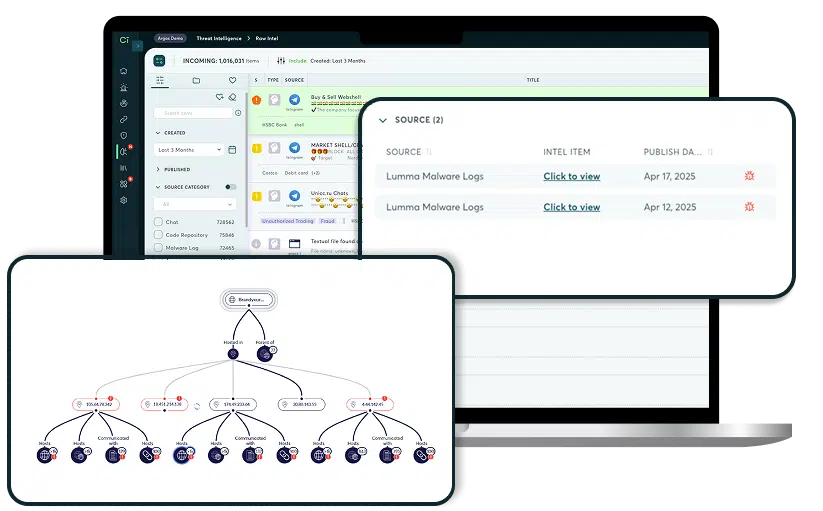
We combine Check Point's global network insights with Cyberint's proprietary threat intelligence feeds and OSINT feeds. Get enriched IP addresses, domains, URLs, and file hashes, choosing consumption via daily IOC feeds or RESTful APIs for custom integrations. Each IOC is enriched with threat type, description, date of observation, confidence level, region, and more.
How it works
Uncover known and unknown assets and access points
Decoded Malware Threat Intelligence
Threat Actor Profiling
Deep Vulnerability Intelligence
New IOC Chrome Extension
Resources
FAQs
What exactly is Cyberint threat intelligence?
It’s actionable information about cyber threats collected from open sources, dark web, and technical indicators, analyzed to help organizations anticipate, prevent, and respond to cyber attacks. It’s not just raw data—it’s context and insights you can use immediately.
Without this, organizations are reacting, not preventing.
How does Cyberint, now a Check Point Company collect threat intelligence?
Cyberint, now a Check Point Company uses a combination of:
-
OSINT (Open Source Intelligence): publicly available information.
-
Dark Web Monitoring: forums, marketplaces, and leaked data sources.
-
Technical feeds: malware signatures, IP/domain reputation, and phishing campaigns.
- Check Point’s Threat Cloud: ThreatCloud AI processes massive telemetry from 150k networks and millions of devices daily. With 50+ AI engines, it detects threats in real time across cloud, network, users, and operations.
and more.
How quickly can I get intelligence on new threats?
Near real-time. Cyberint continuously monitors threat sources, so emerging threats can be flagged within hours, sometimes minute.
Who benefits most from our threat intelligence?
Any organization handling sensitive data or online operations, particularly:
-
Security Operations Centers (SOCs)
-
Incident Response Teams
-
Fraud prevention teams
-
Risk management & executive leadership
How do I know this isn’t just noise?
Most reports produce mountains of raw data. Decision-makers worry if they’ll get signal vs. noise—i.e., actionable insights rather than endless alerts. We address this by contextualizing threats and prioritizing based on risk impact. Not only that but all settings can be manually changed for example confidence score to trigger an alert and password policies.
How do I prove ROI?
Security budgets are scrutinized. Leaders often wonder:
-
“How many attacks did this stop?”
-
“Can we quantify the reduction in risk?”
Our structured reporting and historical threat tracking help make ROI visible. Our Risk Dashboard also helps to clearly demonstrate ROI.
Is this intelligence exclusive?
Check Point provides unique insights from dark web monitoring and specialized feeds, not just open-source news. Feedback from prospects and customers states that we have access to deep & dark web sources our competition lacks.
Our analysts have military grade expertise in interacting anonymously with threat actors and we have access to Check Point’s ThreatCloud AI which is fueled by big data from global endpoints and CP Research. It updates IoCs continuously and uses 50+ AI engines deliver precise threat detection.
How often do we need to act on this intelligence? How much time will it take to manage the tool?
Most analysts report spending 30 minutes a day to achieve value from the tool. As alerts are prioritized and include context such as screenshots, code and more, mitigation is quicker.
How does Cyberint’s vulnerability intelligence platform enhance its threat intelligence?
We integrate vulnerability intelligence directly into its threat intelligence workflow by:
- Prioritizing vulnerabilities based on active exploitation trends observed in the wild.
- Linking vulnerabilities to specific threat actors, campaigns, and attack vectors.
- Enabling security teams to focus remediation where it actually reduces risk, not just where a CVSS score says to patch.
- Eliminates siloed tools and speeds up decision-making.
We don’t just report vulnerabilities; we tell you which ones are actively being targeted and by whom, making your threat intelligence actionable