Ransomware & Account Takeovers
Prevent account takeovers (ATOs) and Ransomware with real-time leaked data detection
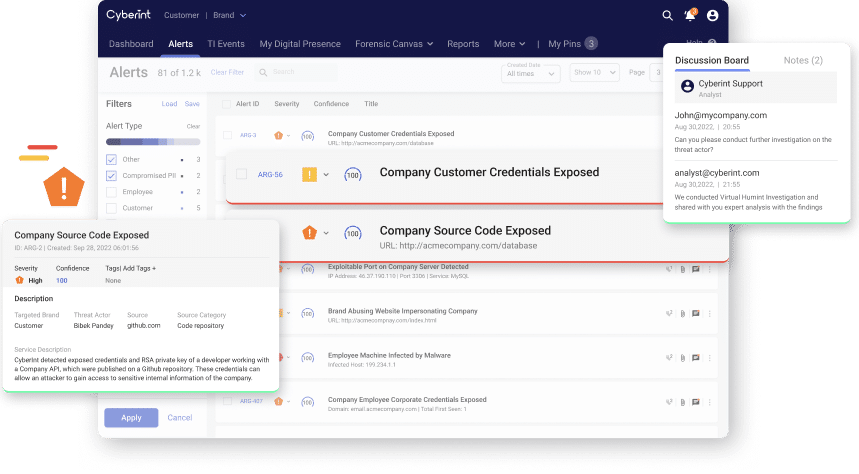
Argos™ detects leaked credentials before they are even being sold on the dark markets so Cybersecurity teams can prevent the next ATO attack, investigate, and further harden security so another leak is less likely to happen.
Leaked credentials in Argos data lake
New databases added annually
Exposed credentials detected/month
New malware logs detected/month
Unparalleled visibility into leaked data
Drill into the details of the leaked credentials the passwords detected for each email, the number of times that each combination of email and password was seen, sources of credentials, the first last time they were published.

Ransomware

Internal Information Disclosure

Compromised Employee Credentials
Compromised PII

Malicious Insider
Compromised Customer Credentials
Compromised Access Tokens

Compromised Payment Cards
Dive into our Resources
See all resources

Videos