


Five months have passed since Hamas’s brutal attack against Israeli settlements surrounding the Gaza Strip that led Israel to a declaration of war. The ongoing conflict is accompanied by attacks by militant terror organizations such as Hezbollah (Lebanon), the Houthis (Yemen), and Hacktivists groups. They have been launching multiple cyber-attacks in the form of DDoS, Data Breaches, Phishing campaigns, and system compromises against Israeli institutes, infrastructures, and civilian’s personal information.
Evidence shows that OpIsrael has become a year-round campaign that shifts to high gear around substantial events such as religious holidays, military operations, and the geopolitical status in the Middle East.
The fast of Ramadan, one of Islam’s five pillars, which starts on the week of March 10, is one of those gear changers. The fast of Ramadan lasts for a month and, according to Islam belief, leads to spiritual uplifting. Its religious significance, and the Middle East’s political situation may affect cyber-attack levels. If negotiations for a cease-fire succeed, attacks may stabilize, yet a decrease is unlikely.
Additionally, the OpIsrael campaign conventionally begins on April 7, which this year falls at the end of the Ramadan fast and marks six months since the start of the war against Hamas.
Furthermore, during April, the Jewish holidays of Passover will take place, followed by several Jewish memorial days – Holocaust Memorial Day, Israeli Defense Forces Memorial Day, and Israeli Independence Day. This potentially can keep the momentum of cyber-attacks targeting Israel.
This report aims to explain potential cyber-attacks during Ramadan and steps to mitigate them. It outlines attack vectors and remediations for prevention or mitigation. Following the recommendations outlined in this report, can help better protect against cyber threats and minimize the risk of data breaches, financial loss, and reputational damage.
Since the war began Cyberint has observed an Anti-Israeli campaign accompanied by multiple attacks by Threat Actors such as Hacktivists and state-funded groups targeting Israeli-related entities domestically and abroad. We assume that the fast of Ramadan, due to its religious importance to Islam, can further motivate those groups to keep attacking Israel and its supporting allies, and even inspire new groups or individuals to join the campaign.
The following examples demonstrate common attack vectors used by Threat Actors. These include DDoS attacks, website defacement, accessing CCTV camera control panels, malware distribution, and data breaches. These attacks are typically targeted at high-value entities, such as governmental institutes, critical infrastructures like electricity and telecommunication, and transportation services. Based on our experience, we believe that these attack vectors will continue to be the most prevalent ones in the upcoming months.
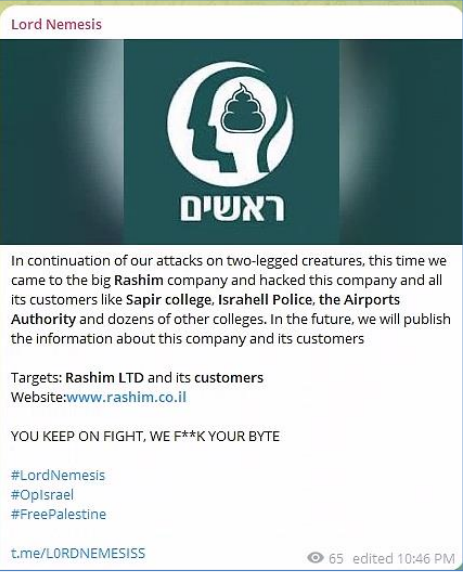
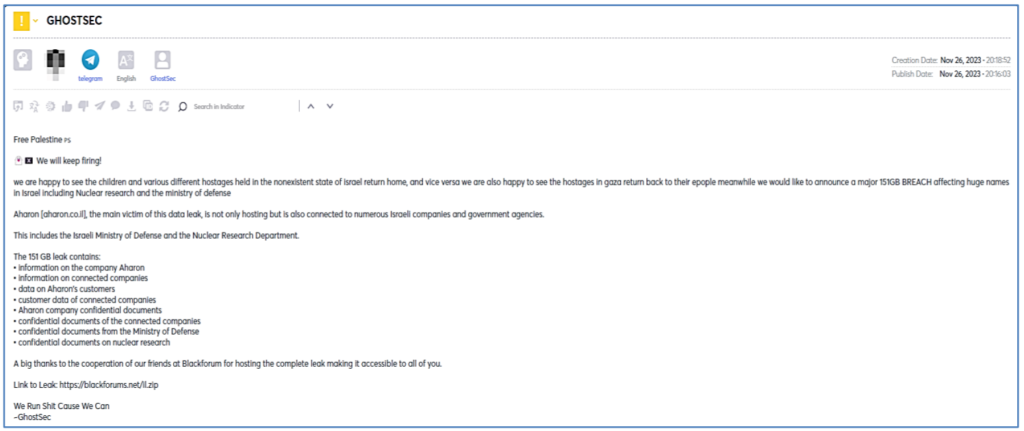
This is the most common attack conducted by hacktivist groups since it can be easily launched, it requires basic online accessible knowledge, and those who lack it can acquire the service or a bot to launch the attack for them for different purposes.
More advanced groups, believed to hold a state backed infrastructure, such as the notorious Anonymous Sudan have launched more distractive DDoS attacks targeting larger targets. For example, on January 12, the group claimed to have successfully launched an “unprecedented & catastrophic cyber-attack” targeting the largest telecommunications company Bezeq, taking responsibility for any damage done to it and related services.
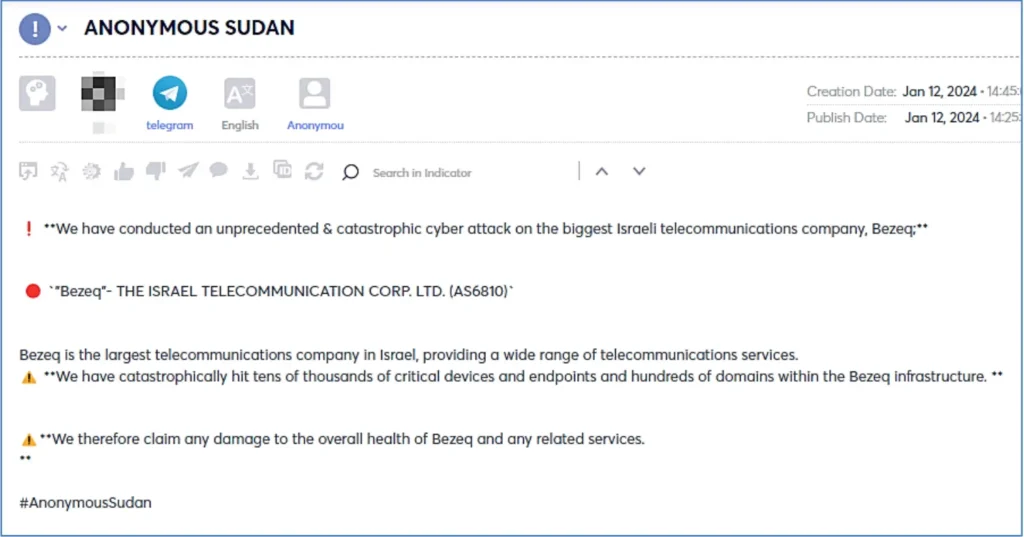
Furthermore, the group offers a tailor-made DDoS service for hire named InfraShutdown leveraging campaigns targeting governments, agencies, and individuals.
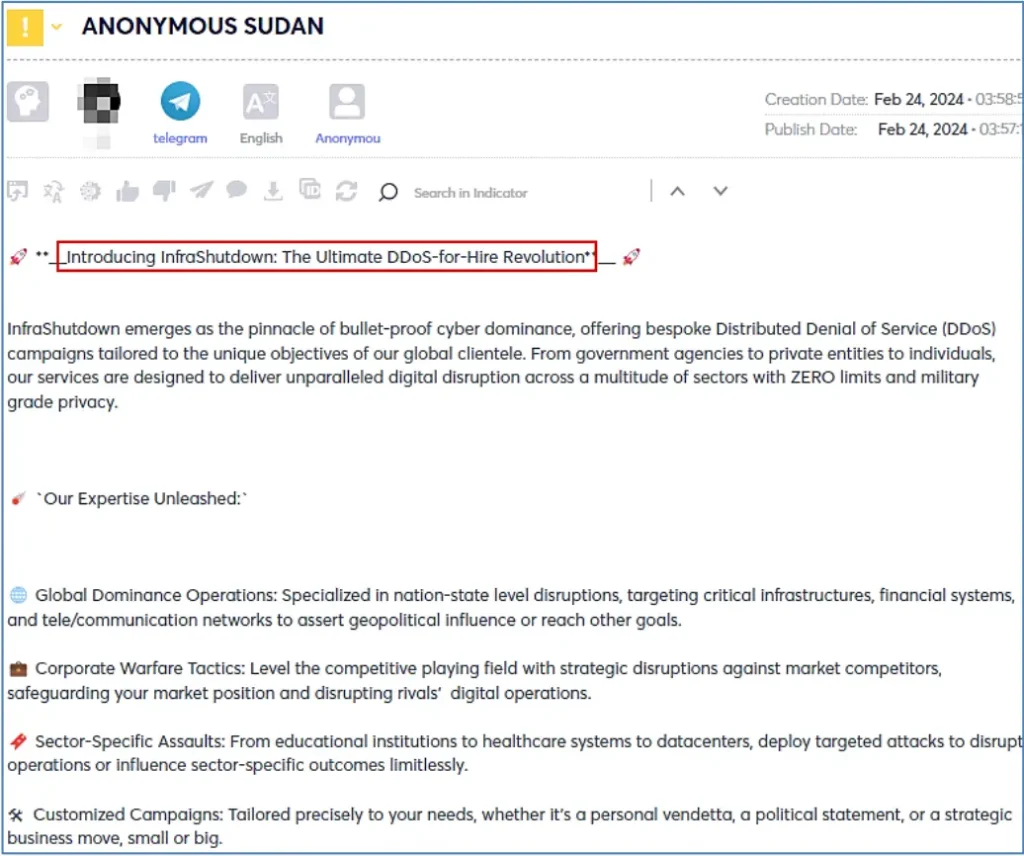
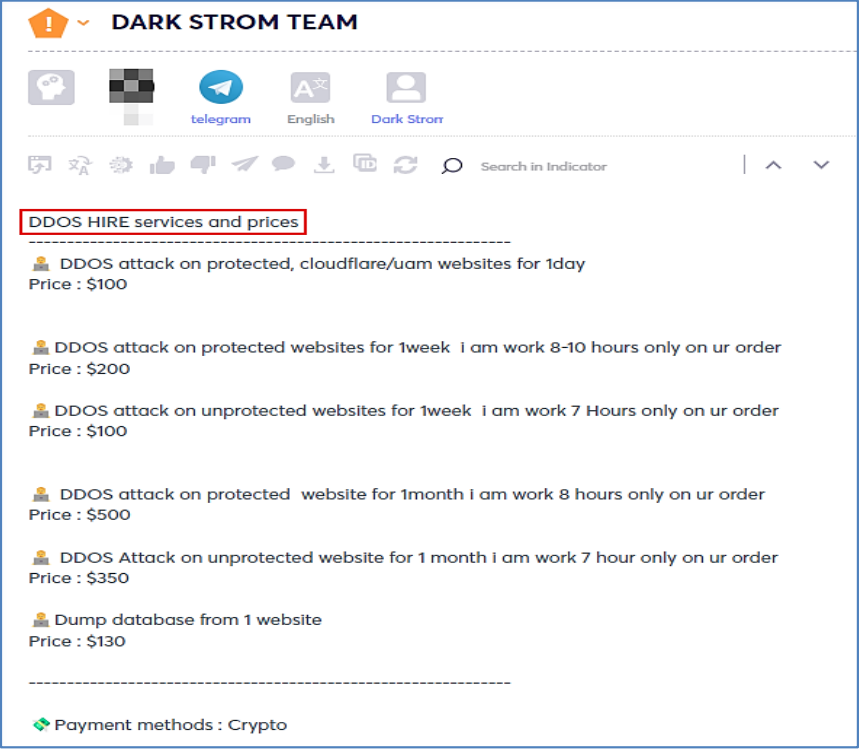
Lately, we have also witnessed an additional hacktivist group, named DarkStormTeam who offers DDoS service for sale.
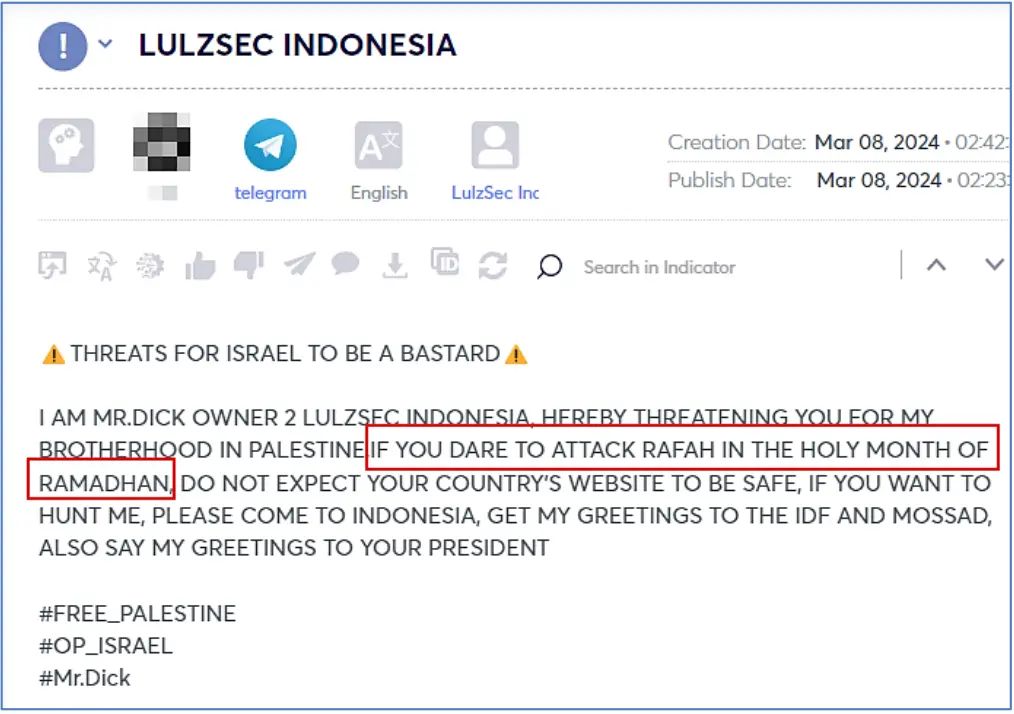
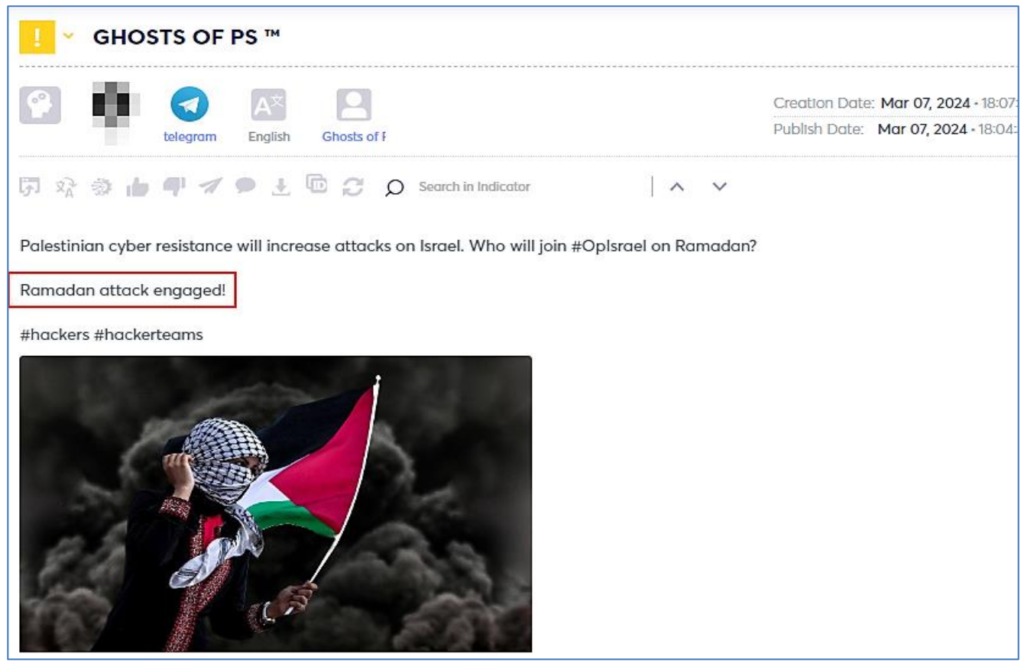
Cyberint conducted further analysis using Argos™ and was able to observe two posts (LulzSec, Ghosts of PS) calling for action during the month of Ramadan, joining the OpIsrael campaign. It most likely that more groups will join and spread the call, even more so if no cease-fire agreement is established and Muslims will be forbidden to enter the Al-Aqsa Mosque for Ramadan prayers on the Temple Mount in Jerusalem.
Notably, the following post was removed from the Ghost of PS Telegram channel, from unclear reasons.
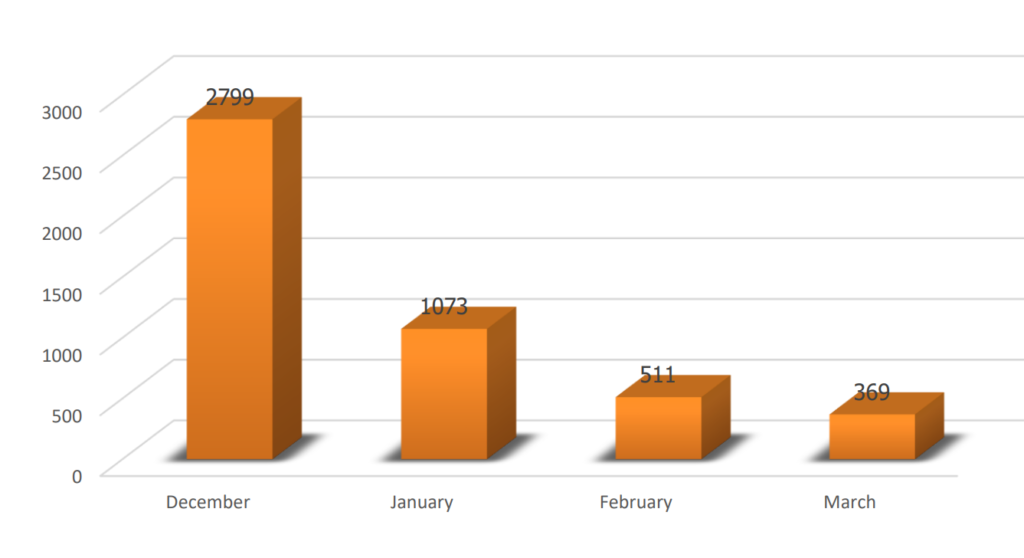
As we are distancing from October 7, we see a decline in the mentions of the Hashtag OpIsrael. However, the Hashtag is not used in every launched attack, and the number of mentions in March is only until the 10th of March so it could change significantly.
Israel has been at war for the last five months, facing multiple fronts at the south border, north border, and in the cyber realm which has no borders. This has enabled multiple Threat Actors to join the fight and launch cyber-attacks in the form of DDoS, Data Breaches, and system compromises against Israeli institutes, infrastructures, and civilian’s personal information.
As mentioned, OpIsrael is an ongoing campaign that rescales according to different, not necessarily cyber-related events. The fast of Ramadan is one of those that starts on the week of March 10, and we are already witnessing a call to action and threats against Israel while keeping the military activity in Gaza relevant. Taking into consideration the religious importance of Ramadan, and the current geopolitical situation in the Middle East, we expect an influx in cyber-attacks in the upcoming month, continuing into April and Israeli holidays and memorial days.
During this period of time, Cyberint will keep monitoring Threat Actors, and hacktivist groups activity for additional IOCs that could indicate potential targets. It is advised to prepare the security network infrastructure for a DDoS type of attack by ensuring the following tools and procedures are set up accurately:
It is advised to prepare the security network infrastructure for Data Breach attempts by ensuring the following tools and procedures are set up accurately:
It is advised to prepare the security network infrastructure for a Malware Distribution type of attack by ensuring the following tools and procedures are set up accurately:
If infected systems are found, isolate them to prevent the malware from spreading.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.
For more information or to get a demo visit this page.

Fill in your business email to start.
Fill in your business email to start


