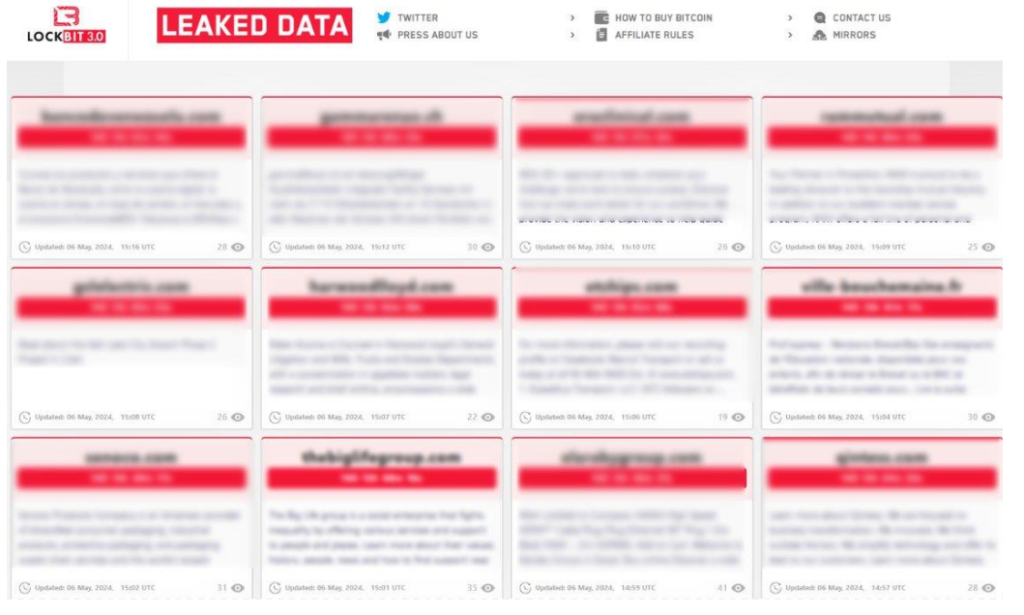
On May 6, 2024, the LockBit ransomware group published a list of over 50 victims on their newly established data leak platform. Among the victims are NASDAQ-listed firms, major corporations, governmental organizations, and technology companies. Interestingly, some of these victims had been targeted previously by other groups or even by LockBit in earlier attacks.
However, a puzzling scenario unfolds: despite the shutdown and subsequent revival of the LockBit site by international law enforcement, LockBit managed to launch a significant attack on 57 different organizations just a day later.
Let’s delve deeper into this situation.
Law enforcement dismantled LockBit’s infrastructure, including 34 servers hosting the data
leak site and its copies, along with stolen victim data, cryptocurrency addresses, 1,000
decryption keys, and the affiliate panel. The operation resulted in the arrests of two people in
Poland and Ukraine and the seizure of 200 cryptocurrency accounts. The takedown, dubbed
“Operation Cronos” was an international coalition of 10 countries.

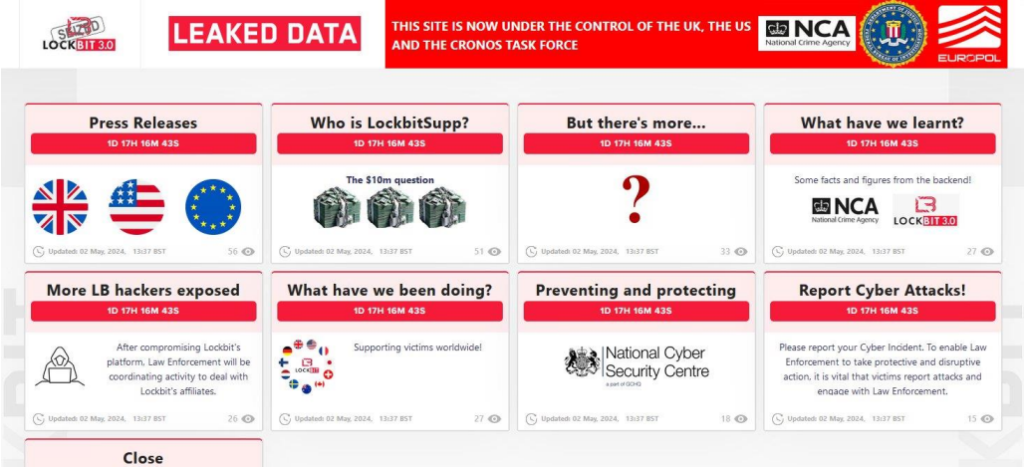
On May 2nd, the NCA, FBI, and Europol reactivated a previously seized LockBit ransomware data leak site to suggest upcoming revelations by law enforcement. This action followed Operation Cronos on February 19.
As part of this disruption, the police repurposed one of the data leak sites into a press release platform. Here, the UK’s National Crime Agency (NCA), the FBI, and Europol disclosed insights from the operation, including a list of affiliates and details on LockBit’s deceptive practices of not always deleting stolen data post-ransom payment.
One post titled “Who is LockBitSupp?” hinted at forthcoming information about the ransomware operation’s orchestrator. However, the eventual blog post simply stated, “We know who he is. We know where he lives. We know how much he is worth. “LockBitSupp” has engaged with Law Enforcement :).” This anticlimactic revelation led to criticism of law enforcement for building anticipation without substantial new details, viewed as a win for “LockBitSupp”, who maintained anonymity.
Those posts on the data leak site were already there on Operation Cronos, but on May 2nd they were updated by Law enforcement. Subsequently, international law enforcement revived LockBit’s data leak and press release site on Sunday, with seven new blog posts scheduled to go live simultaneously on Tuesday at
14:00:00 UTC (10 AM EST).
Is this the End of LockBit?
Tuesday did not bring the anticipated reveal of who is behind the profile “LockBitSupp” or the broader operations of the LockBit group. Instead, the opposite occurred—LockBit swiftly posted details of 57 new victims on their newly established data leak site within just one hour, with an additional two victims added on May 7th. Alarmingly, some of these victims have been attacked again within a short span of 6-8 months since their previous breaches.
These victims hail from various countries, including the United States, Canada, Egypt, Turkey, Belgium, Croatia, Switzerland, Mexico, and more, spanning multiple sectors such as business services, retail, and governmental entities.
Is this resurgence a sign of the group’s revival following recent law enforcement operations against
them? As they say, there is more than meets the eye.
Despite law enforcement’s efforts, which included arresting two affiliates, exposing their infrastructure, and seizing their data leak site, it appears insufficient to deter the LockBit group. They continue to operate and launch global attacks with renewed vigor.
Alternatively, this could signify their final major offensive before an impending shutdown. The response of the FBI and its counterparts will be crucial in determining the trajectory of this unfolding situation.
The Cyberint research team believes that this could be one of the group’s final attempts to garner attention and revenue before law enforcement permanently dismantles their operations, although the group has demonstrated significantly enhanced capabilities with this latest incident.

Fill in your business email to start.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start