

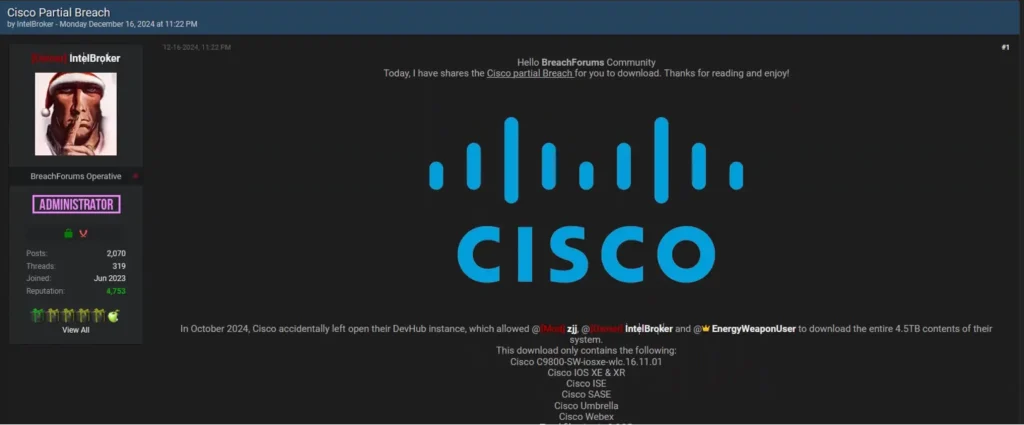
On October 14th, prior to the data leak on December 16th, a threat actor known as IntelBroker announced on BreachForums that he was offering a Cisco breach for sale. As is typical for his operations, he provided samples and credited another well-known collaborator, EnergyWeaponUser. The price for the breach was not specified and was to be negotiated privately, with payments accepted exclusively in XMR cryptocurrency.
Two months later, on December 16th, IntelBroker leaked 2.9 gigabytes of files from Cisco’s DevHub platform on BreachForums. The leaked data reportedly included source code, certificates, and internal documentation related to Cisco products such as Catalyst, IOS, WebEx, and Secure Access Service Edge. According to Cisco, the incident was attributed to a configuration error rather than a compromise of their internal systems.
It is likely that IntelBroker released the data in the BreachForums community because no buyers emerged and as a means of gaining recognition and enhancing his reputation among high-profile organizations worldwide.
IntelBroker, a Serbian hacker and notorious member known for orchestrating high-profile cyber attacks, specializes in initial access brokering—identifying and selling access to compromised systems to facilitate various malicious activities.
Following the FBI’s takedown of breach forums’ administrators, Cyber Niggers emerged as a significant threat group within the revived Breach Forums. While recruitment efforts have slowed, key member IntelBroker has assumed a prominent role in leading the group’s cyber activities. This racist threat group, comprising a small membership all currently active on Breach Forums, has been targeting critical entities, particularly within the US.
The motive behind IntelBroker’s attacks remains unclear. Their range of targets suggests potential motivations: either seeking financial gain by selling stolen data on the dark web or aiming to sow disruption and chaos across various sectors.
As we mentioned, the issue began on Oct. 14, when IntelBroker posted screenshots of files on BreachForums, claiming to have breached Cisco’s systems.

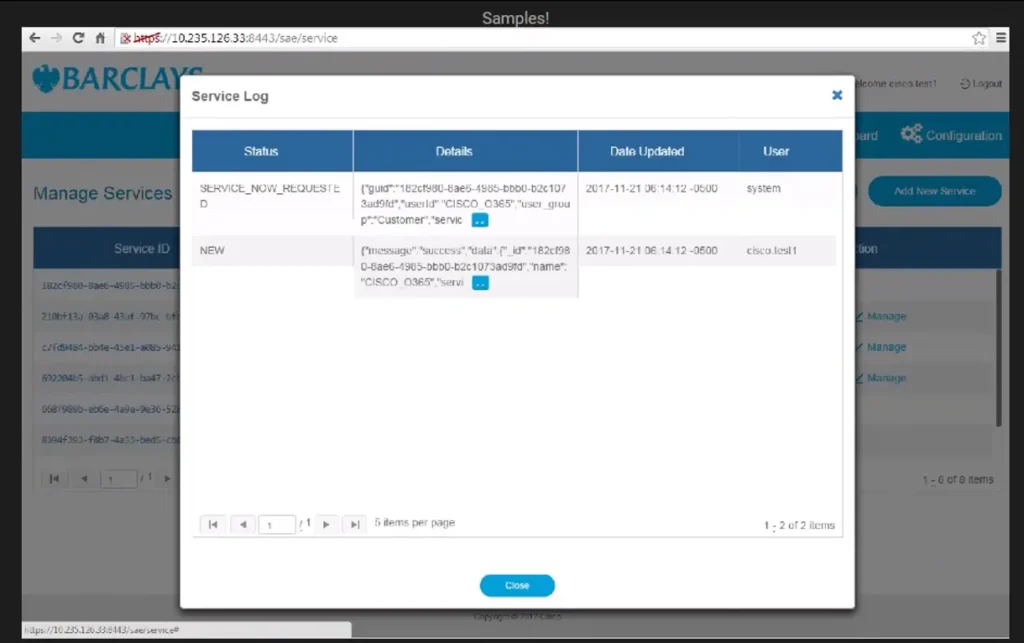
According to Intelbroker, the compromised data contains: Github projects, Gitlab Projects, SonarQube projects, Source code, hard coded credentials, Certificates, Customer SRCs, Cisco Confidential Documents, Jira tickets, API tokens, AWS Private buckets, Cisco Technology SRCs, Docker Builds, Azure Storage buckets, Private & Public keys, SSL Certificates, Cisco Premium Products and more.
Cisco stated that it had involved law enforcement and launched a comprehensive investigation into the incident. The company confirmed that the exposed files did not contain any sensitive information, such as Personally Identifiable Information (PII) or financial data.
It clarified that the leaked data came from DevHub, a public-facing resource center aimed at supporting the community by providing access to software code and scripts. As a precautionary measure, Cisco suspended access to DevHub to address any potential risks.
Cisco confirmed that some of the exposed files were related to a limited number of Cisco CX Professional Services customers. The company reported that it had directly notified the affected customers, provided them with copies of the relevant files, and offered assistance in assessing potential risks.
Cisco detailed the actions it took in response to the incident. Public access to DevHub was temporarily disabled to facilitate a thorough investigation. The company collaborated with law enforcement and enlisted third-party forensic experts to analyze the breach.
Cisco identified a misconfigured data migration script as the root cause of the exposure and promptly corrected the issue. Affected customers were notified and offered support to evaluate any potential risks arising from the exposure.
Additionally, Cisco outlined the enhanced measures it implemented to prevent similar incidents in the future. These measures include stricter controls over automation processes, improved monitoring systems for public-facing platforms, and expanded quality assurance testing to detect vulnerabilities before deployment.
This incident represents another chapter in IntelBroker’s calculated and evolving tactics. The actor’s repeated success in targeting high-profile organizations and maintaining visibility, even on public platforms like Twitter, underscores a strategic combination of technical expertise and psychological manipulation.
IntelBroker’s focus on companies like Cisco suggests a broader agenda that goes beyond data theft, aiming to build a reputation for high-profile breaches that expose corporate security weaknesses and highlight systemic vulnerabilities.
Stay updated with Cyberint. now a Check Point Company’s latest insights on emerging threat actors and similar incidents. Additionally, monitor Cisco’s official website for any announcements or guidance on necessary future actions.
Cyberint, now a Check Point company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Check Point External Risk Management solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.
A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Check Point External Risk Management to protect themselves from an array of external risks, including vulnerabilities,
misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

Fill in your business email to start