I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
Effective ‘dark web monitoring’ is essential for modern businesses. This intelligence practice goes beyond traditional dark web forums, actively scanning the deep web, open web, and social media platforms. It uncovers threats and risks wherever cyber criminals operate – from hidden marketplaces to public social channels – providing crucial visibility into your external threat landscape.
The scope of modern dark web monitoring goes well beyond merely identifying impersonation attacks or gathering intelligence on specific threat actors. While these are undoubtedly vital, a truly effective solution must also proactively search for and alert you to the presence of:
Speaking of exposed credentials, these frequently serve as the initial access point for significant cyberattacks, such as ransomware and account takeovers. When employee or customer login details surface on dark web marketplaces or hacker forums, it presents an immediate and exploitable vulnerability for your organization.
Proactive detection of these leaks enables businesses to take swift action, resetting compromised passwords and investigating potential breaches before they expand into major security events. To learn more about mitigating this specific threat, you can delve into Cyberint’s insights on Preventing Account Takeover by Detecting Leaked Credentials.
For businesses looking to implement or enhance their dark web monitoring capabilities, partnering with the right vendor is paramount. Here’s a step-by-step guide to successful onboarding:
Before you even start looking, understand your internal capabilities and needs. Do you have a large, experienced security team that can handle a high volume of raw alerts and sort through them? Or do you have a smaller team that requires a vendor who can provide analyst support to augment your capabilities and deliver highly contextualized, actionable intelligence?
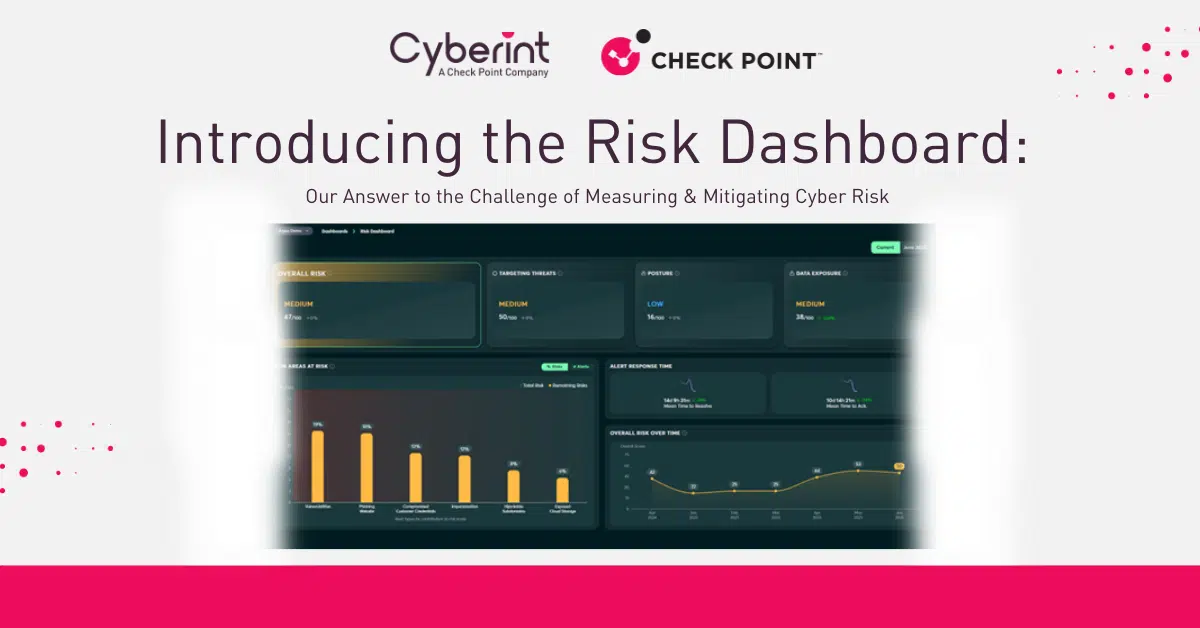
Consider the data processing capabilities of the solution. For instance, Cyberint processes over 60 million new intelligence items every month. While this volume is critical for comprehensive coverage, what you ultimately need is a lower, manageable amount of high-accuracy alerts with rich context. Look for vendors that boast a high true positive rate – Cyberint, for example, prides itself on an unmatched 93% true positive rate, meaning minimal false alarms that can exhaust your team. As one G2 reviewer highlighted, “The Threat Intel platform is excellent and provides a good set of alerts,” underscoring the value of actionable intelligence.
Finally, determine if you need a consolidated solution that covers multiple external risk areas (like brand protection, attack surface management, and dark web monitoring) or a point solution specifically for dark web monitoring.
Here’s a quick checklist of things to look for in your vendor:
Cyberint has deep knowledge on how threat actors operate on the Deep and Dark Web. Take a look at an explanation of how these actors operate.
Once your requirements are clear, research potential vendors and narrow your list to a few strong contenders. Don’t just rely on marketing materials; request a Proof of Concept (PoC). This allows you to test the solution with your specific needs and data, gauging its effectiveness in your environment. During the PoC, evaluate how well the solution aligns with your budget and, most importantly, your defined security goals. Pay close attention to the quality of alerts, the user interface, and the responsiveness of their support.
With your chosen vendor, the onboarding process should be straightforward. Provide them with the essential information required for monitoring, such as your company’s brand names (including variations and common misspellings), key executive names, critical domains, and any other sensitive digital assets you wish to protect. Once this information is fed into the system, the alerts relevant to your organization should begin to flow in.
Your onboarded solution should provide easy to digest training and the UIUX of the solution should be simple to use.
Initial alerts might contain some false positives. This is a normal part of any new intelligence system. It’s crucial to actively report these false positives back to your vendor. This feedback loop is vital for the solution’s algorithm to learn and improve its accuracy over time. Your onboarded solution should use AI/ML for this. The more you engage in this process, the better the system will become at distinguishing genuine threats from irrelevant noise, further boosting its true positive rate and overall performance.
After the initial tuning and optimization phase, you should be well on your way to effectively utilizing your dark web monitoring solution. Aim to dedicate a short amount of time daily – even just 30 minutes – to review the high-accuracy alerts received. These timely, contextualized alerts will provide invaluable insights into potential threats, enabling you to take proactive measures. By identifying and mitigating risks early, you can significantly improve your organization’s cyber posture, reduce the likelihood and impact of successful attacks, and stay ahead of emerging threats.
By following these steps and committing to a proactive approach, businesses can transform a potential blind spot into a powerful source of actionable intelligence. This helps secure their assets and reputation, and allows them to stay ahead.
Cyberint, otherwise known as Check Point Infinity External Risk Management, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact.
The solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start