


I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
Organizations are increasingly recognizing that threats can emerge from various external-facing assets, including web applications, cloud infrastructure, APIs, and even shadow IT. This necessitates a robust Attack Surface Management (ASM) strategy, supported by specialized software solutions.
Organizations need robust attack surface management tools equipped with a comprehensive set of capabilities. Here are critical features to look for in leading attack surface management solutions:
The foundation of effective attack surface management lies in a tool’s ability to automatically discover all internet-facing assets associated with your organization. This goes beyond traditional Attack Surface Management (ASM) by encompassing not just known domains, subdomains, and cloud infrastructure, but also uncovering shadow IT, rogue applications, and even related digital footprints crucial for brand protection, such as social media profiles and mobile applications. Furthermore, it should extend to identifying potential sources of leaked information, like exposed credentials on paste sites or dark web forums.
Real-time or near real-time monitoring is essential to detecting newly exposed assets, configuration changes, and emerging vulnerabilities across your entire digital footprint. However, simply identifying potential issues isn’t enough. Leading attack surface management solutions incorporate the option of automatic threat validation capabilities. This active testing and verification of identified vulnerabilities help security teams differentiate between theoretical risks and genuine, exploitable threats, significantly improving the efficiency of remediation efforts.
3. Context-Rich Alerts and Prioritization Driven by Threat Intelligence
The sheer volume of security alerts can overwhelm security teams. Effective attack surface management tools provide contextualized alerts, enriching findings with information about the asset, the nature of the risk, and potential impact. This can enable quick decision making on whether to escalate the alert or now. Crucially, they integrate with diverse threat intelligence feeds, including information on threat actors actively targeting your specific region (e.g., Israel) and industry. This allows for intelligent prioritization of alerts, ensuring that teams focus on the threats that pose the most immediate and relevant danger to the organization.
A comprehensive attack surface management strategy extends beyond technical vulnerabilities. Tools should actively monitor for leaked credentials associated with your organization’s domains and employees, providing early warnings of potential account takeovers. Furthermore, robust brand protection features are vital, including the detection of domain squatting, social media impersonations, and unauthorized use of your brand assets in potential phishing campaigns.
Identifying risks is only half the battle. Effective attack surface management tools provide clear, prioritized remediation insights and actionable guidance to help security teams address vulnerabilities efficiently. Recognizing that complex threats may require expert intervention, the availability of support from experienced security analysts is a significant advantage. These analysts can provide deeper investigation, validate findings, and offer tailored remediation strategies when needed.
While robust capabilities are paramount, price is always a crucial factor. Organizations should evaluate the pricing models of different attack surface management solutions, considering factors such as the number of assets monitored, the frequency of scans, the level of threat intelligence integration, and the availability of analyst support. The overall value proposition – the balance between cost and the comprehensiveness and effectiveness of the solution – should be carefully assessed to ensure it aligns with the organization’s security budget and risk management objectives.
By prioritizing these key features, organizations can select attack surface management tools that provide a holistic and proactive approach to managing their external risks, ultimately strengthening their overall security posture.
A recent Gigaom report highlighted several key players in the ASM space, offering valuable insights into the leading solutions available. Drawing inspiration from their findings, we’ve compiled a list of the top ASM software solutions to watch in 2025.
Cyberint, now part of Check Point Software Technologies, stands out as a powerful and comprehensive solution in the attack surface management (ASM) landscape. Recognized as an “Outperformer” and a “Leader”, Cyberint offers a unified platform that goes beyond traditional Attack Surface Management (ASM) to provide a wider view of an organization’s external risk exposure.
Their strength lies in their ability to combine extensive threat intelligence with in-depth ASM capabilities, including the crucial aspect of active exposure validation.
Cyberint’s solution is designed to provide organizations with a proactive and comprehensive understanding of their external risk posture. Key features and differentiators include:
Comprehensive External Risk Management (ERM): Unlike purely ASM-focused solutions, Cyberint addresses a wider spectrum of external threats. This includes not only identifying and managing internet-facing assets but also providing robust capabilities in areas like:
Built natively, Cyberint offers a sophisticated attack surface management module that automatically discovers and continuously monitors an organization’s external-facing assets. This includes:
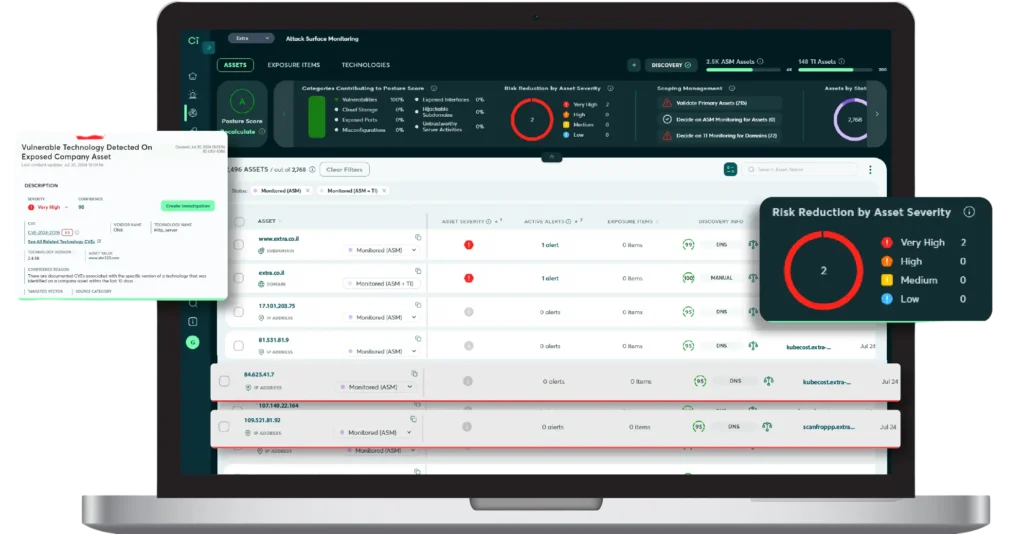
This is a significant differentiator for Cyberint. Beyond passively identifying potential vulnerabilities, the solution actively attempts to validate these exposures to confirm their exploitability. This provides a much higher level of confidence in the identified risks and allows security teams to prioritize remediation efforts on genuine threats.
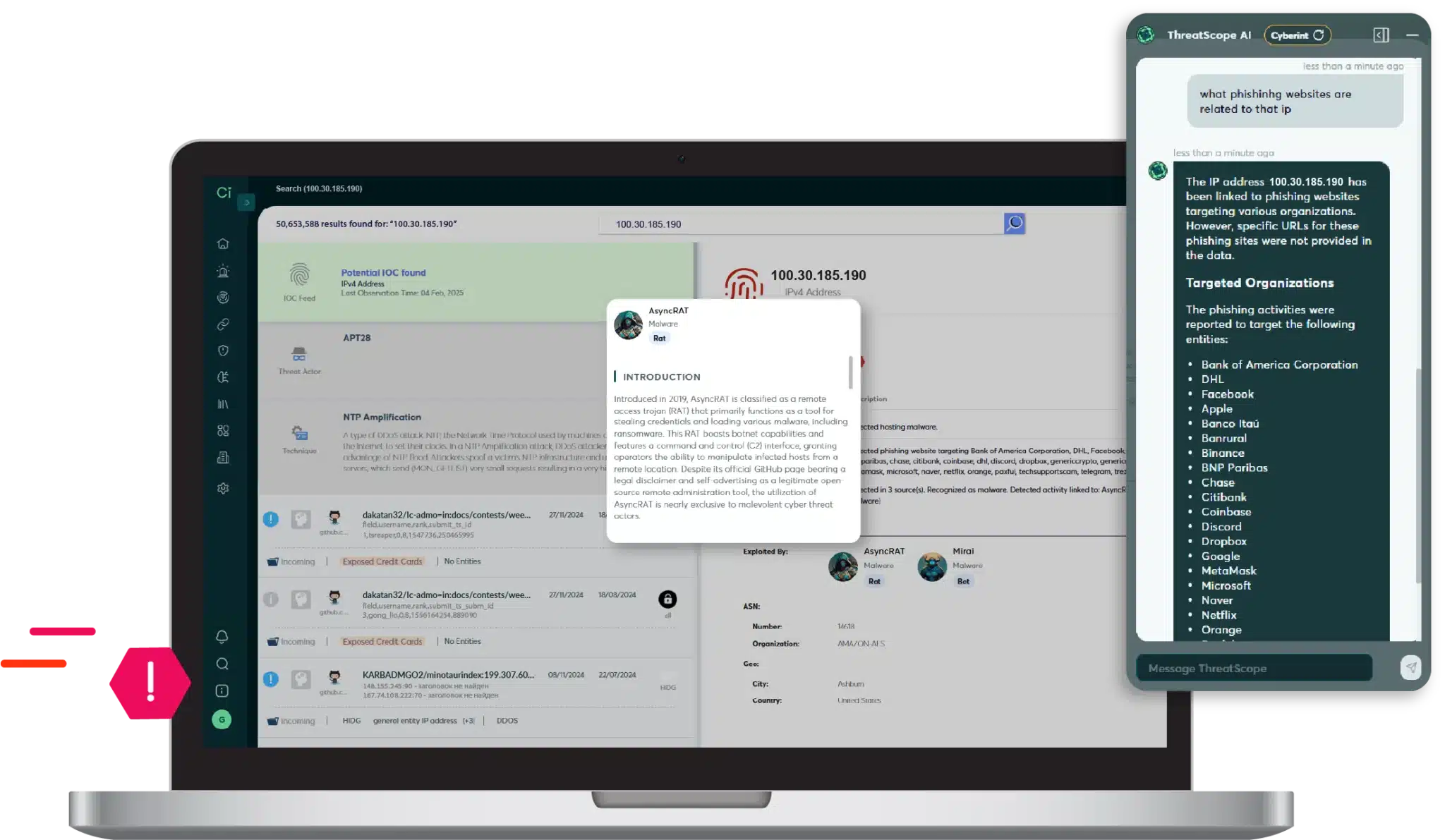
Cyberint, now a Check Point Company’s solution enriches security alerts with extensive context derived from its threat intelligence and active validation processes. This context, combined with an understanding of the threat landscape and potential impact, enables intelligent prioritization of remediation efforts, ensuring that security teams focus on the most critical risks first.
Cyberint, now a Check Point Company seamlessly integrates its ASM findings with its comprehensive threat intelligence. This provides context, such as whether identified vulnerabilities are being actively exploited by threat actors, if there are campaigns targeting similar organizations in the same region (Israel) or industry, and the potential severity of the threat.
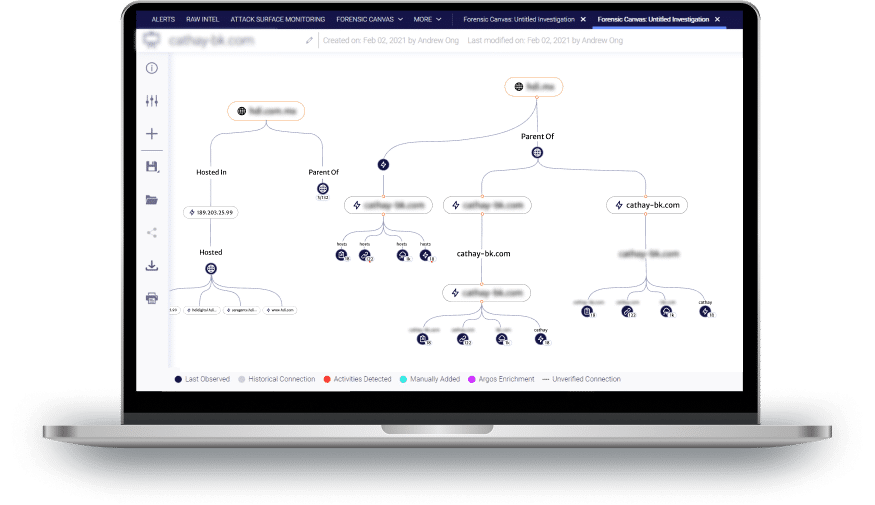
Cyberint, now a Check Point Company provides access to security experts who can help investigate complex threats, filter through alerts, validate findings, and provide tailored remediation guidance. Analysts are military trained and speak over 20 languages combined.
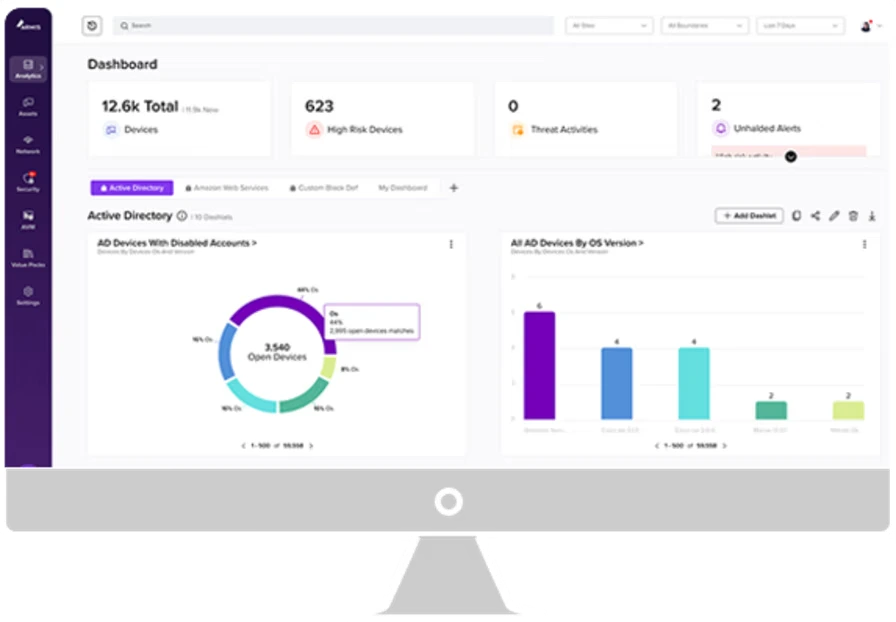
While often recognized for its agentless IoT and OT security platform, Armis also provides significant capabilities in discovering and managing connected assets that contribute to the attack surface. Their comprehensive asset inventory can be important for attack surface management covering the entire organization.
Their platform can identify device types, manufacturers, firmware versions, and communication patterns, providing security teams with a high level of visibility into their extended digital footprint and potential blind spots that attackers could exploit. This deep asset intelligence allows organizations to understand the inherent risks associated with each connected device and incorporate them into their overall attack surface management strategy.
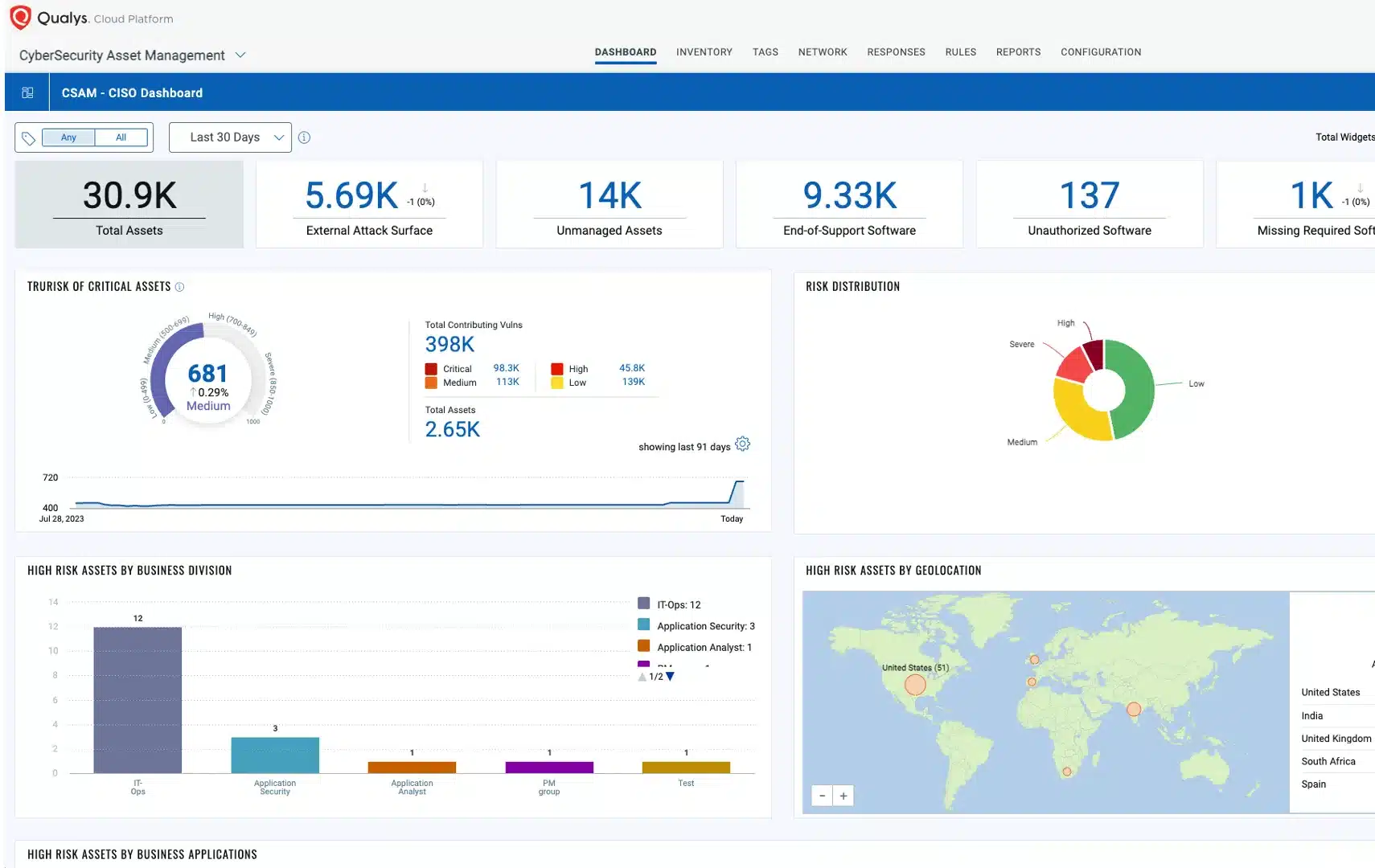
A well-established player in vulnerability management, Qualys offers robust ASM features integrated with its broader security platform. Their ability to continuously discover and assess external assets for vulnerabilities makes them a strong contender in this space.
Qualys’s ASM capabilities extend to identifying and managing the risks associated with “unknown” assets, such as those from subsidiaries or shadow IT, which often represent significant blind spots for attackers.
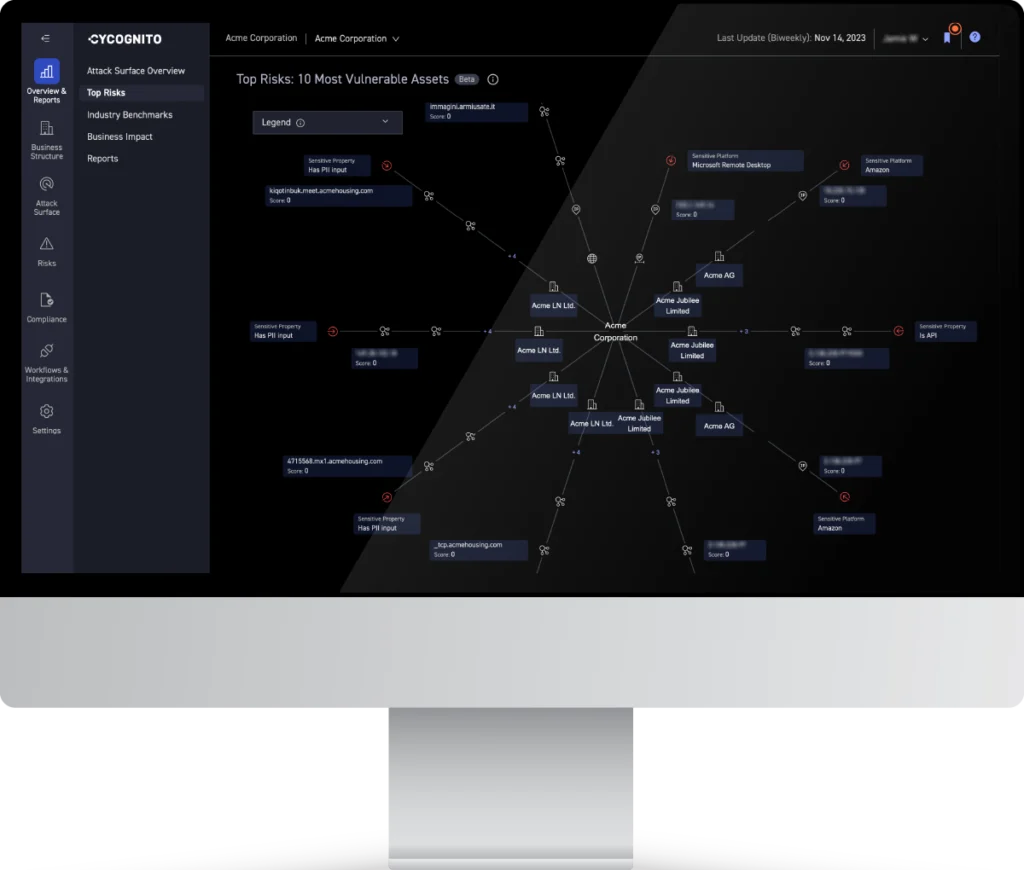
Cygognito stands out for its focus on attack surface discovery and risk prioritization. Their platform leverages AI and graph-based analysis to provide a deep understanding of an organization’s external exposure and potential attack paths.
Their platform emphasizes the importance of understanding how an attacker perceives potential entry points and leverages this perspective to prioritize risks effectively.
Beyond discovery, CyCognito focuses heavily on contextualization. The platform automatically classifies discovered assets based on their business function and relationships within the organization, providing crucial context for understanding the criticality of each asset and prioritizing remediation efforts.
Recognized as an outperformer in the broader ERM landscape (including ASM), NetSPI distinguishes itself through its combination of technology and expert services. Their offensive security heritage provides a unique perspective on identifying and validating real-world attack vectors on the external surface.
Their approach leverages a combination of automated scanning technologies with manual penetration testing expertise.
NetSPI’s services often include ongoing support from their team of security experts, who can provide deeper analysis, assist with prioritization, and offer guidance on remediation strategies tailored to the organization’s specific environment and risk appetite.
Another outperformer in attack surface management and a significant player in ASM, Rapid7, through its acquisition of Intsights, offers a powerful combination of proactive threat intelligence and attack surface monitoring. Their focus on understanding attacker perspectives enhances their ASM capabilities.
Surface Command aims to eliminate blind spots by continuously discovering and monitoring an organization’s digital footprint.
FireCompass takes a unique approach by simulating attacker reconnaissance to map out the external attack surface. Their continuous discovery and risk assessment capabilities provide valuable insights into potential vulnerabilities. This “Continuous Automated Red Teaming (CART)” methodology allows FireCompass to identify not only known assets but also uncover shadow IT, exposed databases, cloud buckets, and other often-overlooked elements that can be exploited.
A key differentiator for FireCompass is its ability to simulate multi-stage attacks safely against an organization’s critical applications and assets. By proactively identifying potential breach paths, FireCompass helps security teams understand how attackers could chain together seemingly minor vulnerabilities to gain access.
Known for its Breach and Attack Simulation (BAS) platform, Cymulate also offers ASM functionalities. Their ability to simulate attacks against the external surface helps organizations validate the effectiveness of their security controls.
A key aspect of Cymulate’s ASM offering is its ability to map potential attack paths that an attacker could take to compromise critical assets, often visualizing how seemingly minor external exposures could be chained together to gain access. This attack path mapping provides crucial context for understanding the true risk posed by identified vulnerabilities.
A broad cyber security vendor, Palo Alto Networks integrates ASM capabilities within its Cortex platform. Their comprehensive security ecosystem offers a unified approach to managing external risks alongside other security domains.
A key capability of Cortex Xpanse is its active discovery. The platform continuously scans the entire internet to identify and map all internet-connected assets associated with an organization, including those that might be unknown, unmanaged, or forgotten. This extensive discovery helps eliminate blind spots and provides a complete inventory of potential entry points for attackers.
Palo Alto Networks positions Cortex Xpanse as a critical component of a broader security strategy, integrating with their other offerings to provide a holistic approach to risk management.
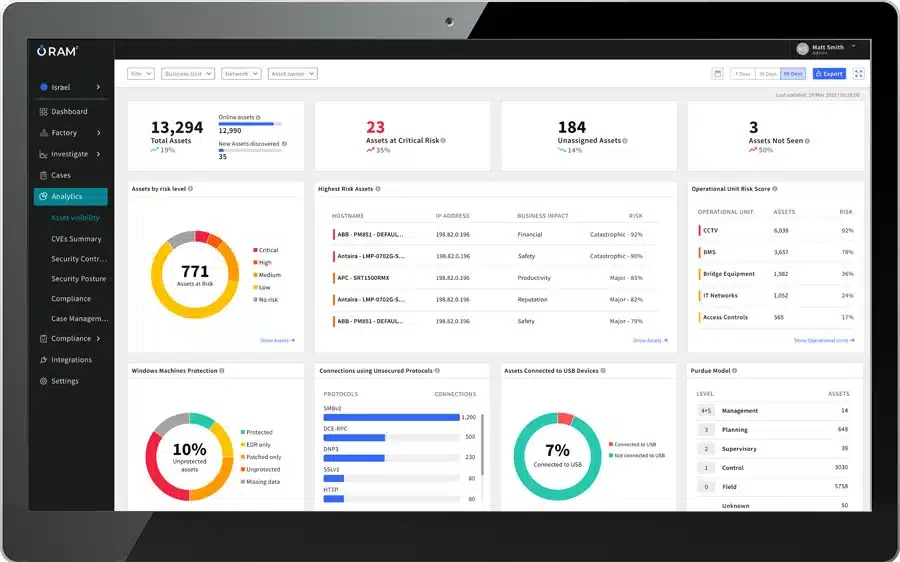
Otorio specializes in providing Attack Surface Management (ASM) and cybersecurity solutions tailored specifically for Operational Technology (OT) and Industrial Control Systems (ICS) environments. Recognizing the unique challenges and critical nature of these systems, Otorio’s platform focuses on delivering visibility, risk assessment, and threat mitigation capabilities designed to ensure the safety, reliability, and resilience of industrial operations.
A key aspect of Otorio’s approach is its deep understanding of the differences between IT and OT environments. Their ASM solution is built to address the specific protocols, devices, and constraints prevalent in industrial settings, where uptime and safety are paramount.
Otorio’s focus on the OT domain differentiates it from many traditional ASM vendors that primarily cater to IT environments.
Selecting the appropriate Attack Surface Management tools is a critical decision, and it’s not just about picking the most feature-rich platform. A successful ASM strategy requires a strategic look at your organization’s specific needs, budget, risk appetite, and industry landscape. Here are some key considerations when evaluating ASM tools and building your strategy:
By carefully considering these factors and evaluating the strengths of various ASM tools.
Cyberint, otherwise known as Check Point Infinity External Risk Management, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact.
The solution provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web.

Fill in your business email to start