


Originally Published June 26, 2024
Update: In September 2025, the Manhattan District Attorney’s Office seized 12 domain names tied to underground vendors trafficking stolen financial data, including B1ack’s Stash. After an investigation found these sites were selling more than one million stolen credit and debit card records and associated personal information. B1ack’s Stash wasn’t operating in isolation; its infrastructure and the others were sophisticated online marketplaces that let criminals sort stolen cards by bank, geography, and even victim name. All seized domains now display court-ordered notices, and law enforcement continues to investigate the individuals behind and using these platforms
—
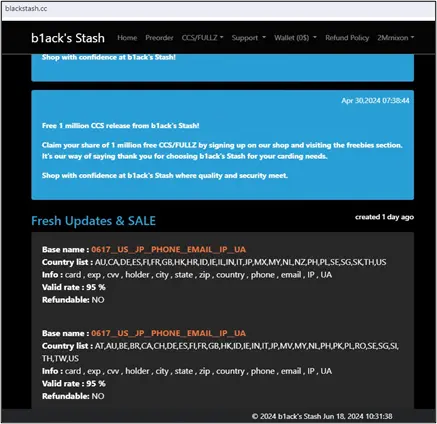
B1ack’s Stash, a new dark web marketplace, recently gained significant attention by releasing 1 million stolen credit card details for free upon their debut on April 30, 2024. The carding shop promoted this giveaway through several known carding forums on the darknet to attract a larger customer base. Typically, carding shops release free data in the thousands, but B1ack’s Stash’s strategy set it ahead of its competition, similar to BidenCash’s tactic last year, where they leaked 2 million stolen cards.
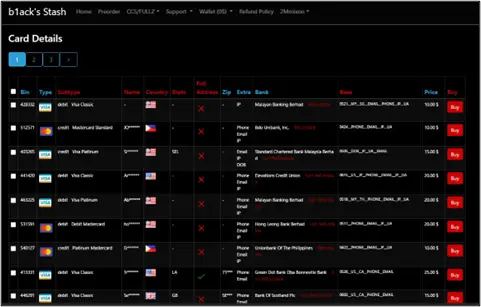
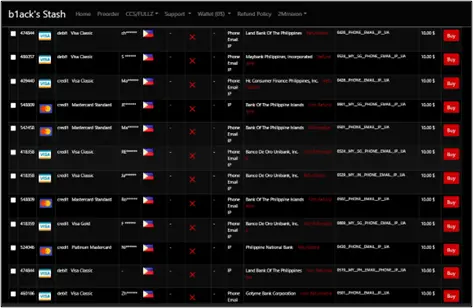
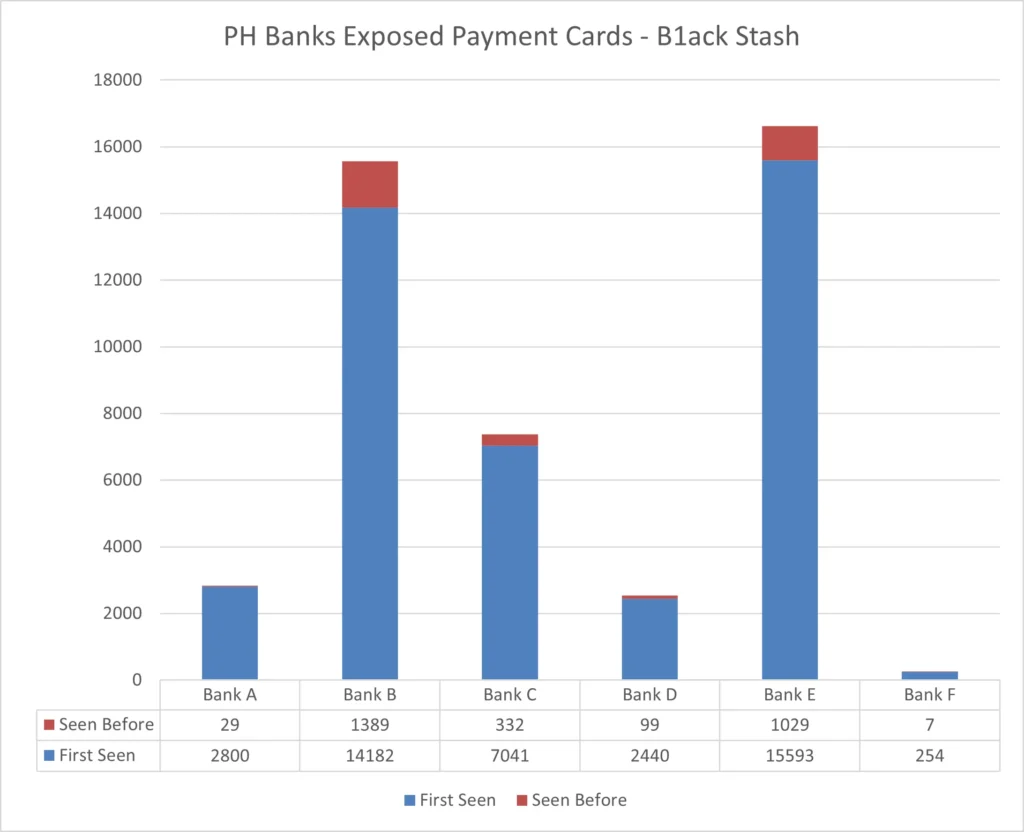
From the data we collected, it was revealed that the leaked information affected cards from various countries, including the Philippines, with a significant number of exposed payment cards. Cyberint’s analysis of the collected data for six major Philippine banks revealed a concerning finding: of the 45,195 local cards, 95% were unique or first seen by Argos, Cyberint’s threat intelligence platform. This implies that the set of stolen data could have originated from a private collection and was not previously released to the public.
The dataset included a mix of debit and credit cards, mainly from MasterCard and Visa, but also included American Express and JCB. This incident highlights the persistent threat of financial fraud on illegal platforms and underscores the urgent need for enhanced cybersecurity measures.
B1ack’s Stash made a significant splash when they officially launched their carding shop by releasing a staggering 1 million stolen payment cards for free last April. Based on the intelligence Cyberint gathered during our investigation, we discovered that the threat actor or group has been active in carding forums as far back as last year under the profile “B1ack,” formerly known as “blackclub,” and often referred to by users as “king.”
B1ack is notorious in these forums for distributing CCS/FULLZ—credit and debit cards along with full personal information, known as “FULLZ,” which contains enough data to commit identity theft or fraud—as freebies. Further investigation indicated that B1ack started this marketing campaign in January this year by posting hundreds of free stolen payment cards to build credibility and attract more customers.
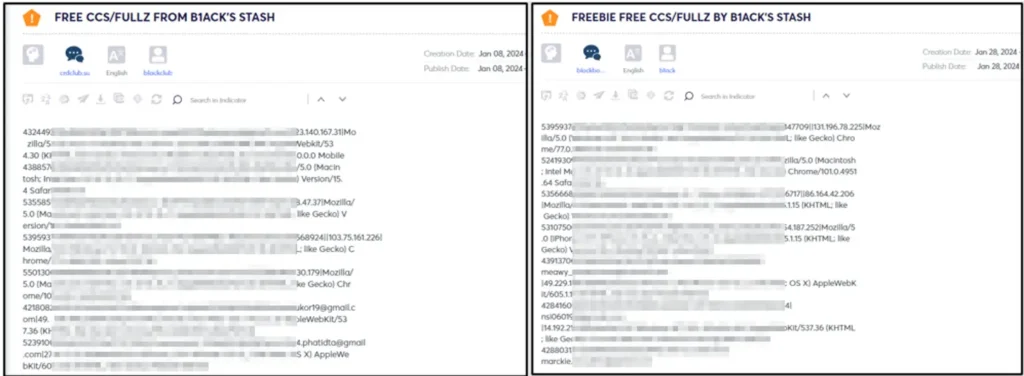
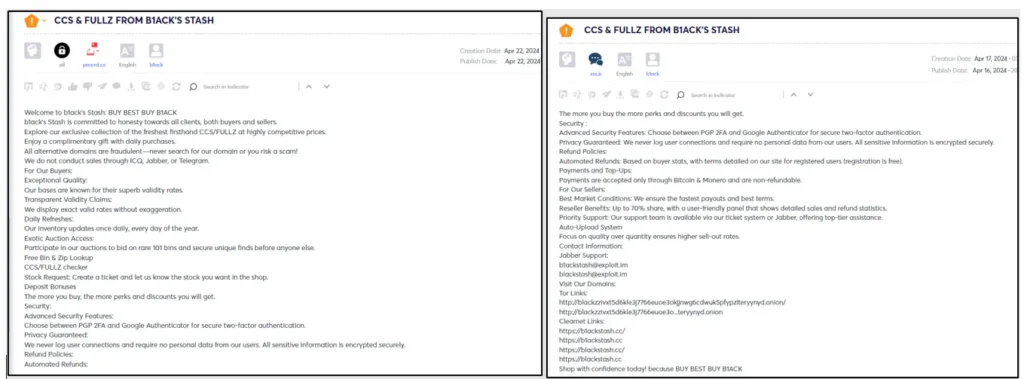

The threat actor initially focused on giving away freebies but eventually began promoting their shop on various dark web forums on April 16, 2024, ahead of their major launch at the end of April.
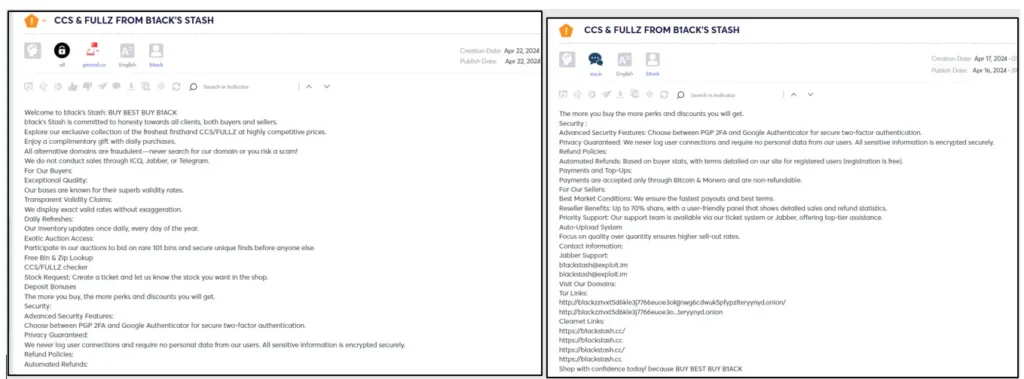
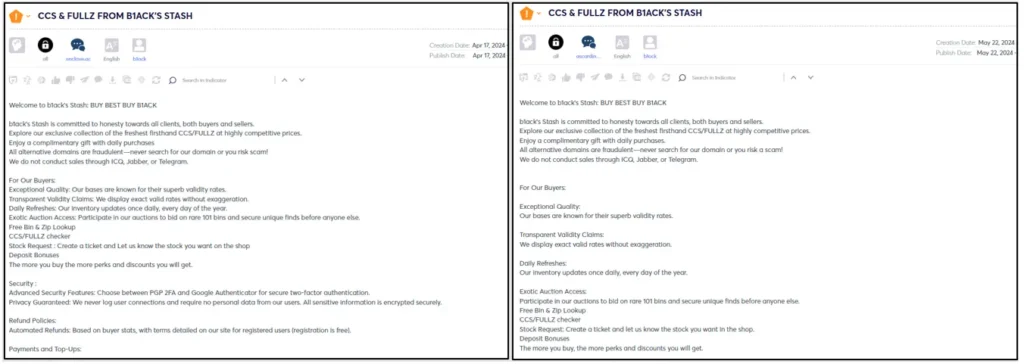
B1ack’s Stash shop is accessible both on the dark web and the open web at the following links:
Over the past few months, as B1ack has been giving away free CCS/FULLZ, the card seller has received positive feedback from customers, who have attested to the high validity rate of the cards. We also observed this customer satisfaction among those who became B1ack’s buyers and visitors to their shop.
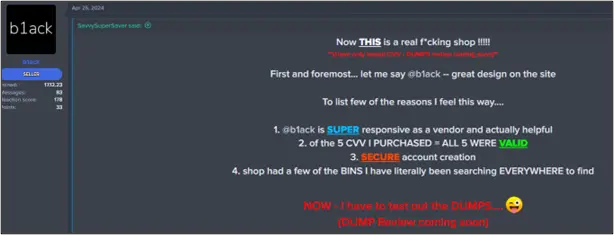
B1ack Stash’s primary motive from the outset has clearly been financial gain, which they have pursued by building a strong reputation as a card seller within the carding community. Our analysis of the payment card details leaked by B1ack over the past six months and the data we’ve collected for the affected local banks indicates that these were largely obtained through phishing campaigns. The data format, which includes user agents and victim IP addresses typically observed in both local and global phishing attacks, allows us to assert with high confidence that it originated from such activities.
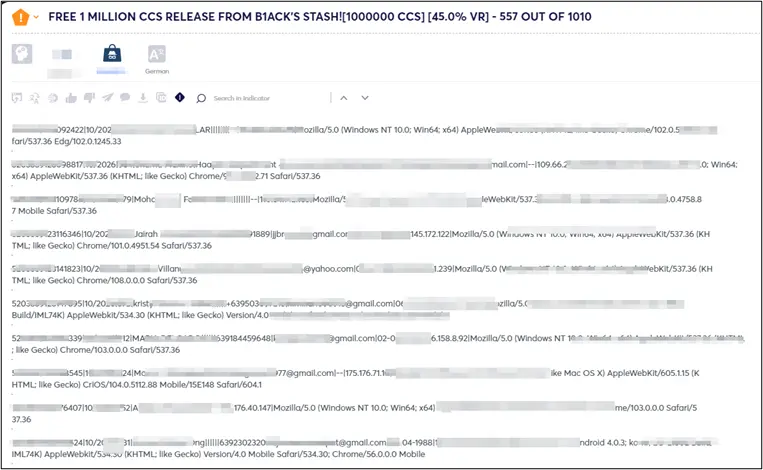
The phishing campaigns may not have specifically targeted the local banks’ customers. Instead, the threat group likely employed various methods to harvest large volumes of credit card details through phishing, including (but not limited to):
These methods are deliberately designed to cast a wide net, targeting users across multiple platforms where significant groups are likely to input their payment card information, thereby maximizing the potential to capture valuable data.
Considering this backdrop, it is evident that b1ack’s primary goal has consistently been to profit from the sale or use of these stolen credit card details. By leveraging dark web markets, underground forums, and direct transactions, they aim to capitalize on the extensive reputation and reach they have established through their effective marketing strategy.
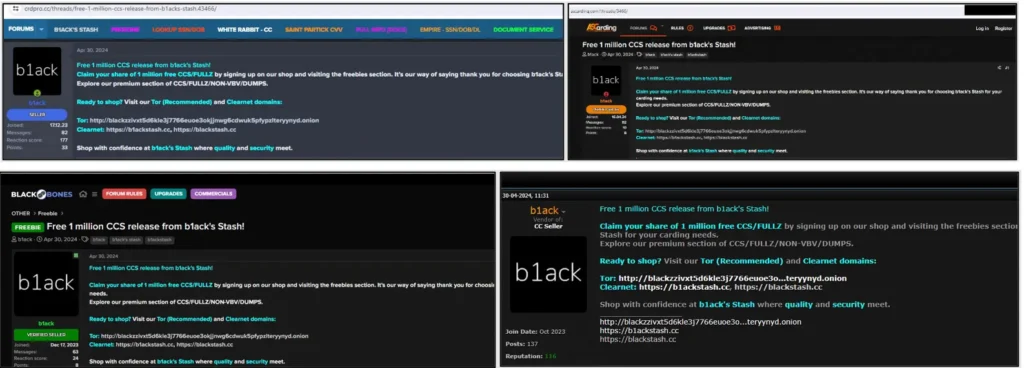
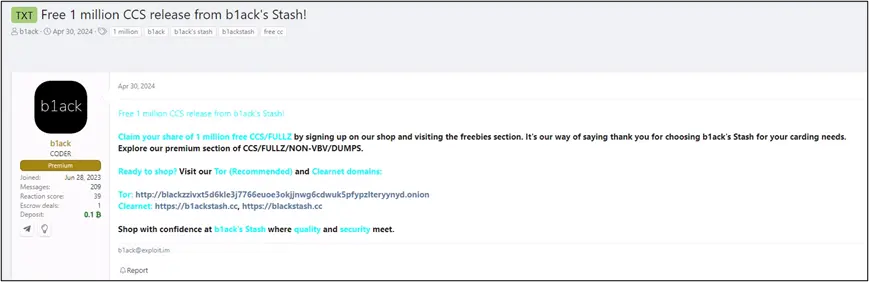
In line with b1ack’s freebie marketing strategy, they announced the release of 1 million stolen payment cards for free on several popular carding forums on the last day of April this year. This massive giveaway served as the grand launch celebration for their “carding shop”. The threat group mentioned that users could claim their share by signing up at their shop and visiting the freebies section. According to them, this gesture was their way of saying thank you for choosing b1ack’s Stash for carding needs. They also highlighted the premium section of their shop, which offers CCS/FULLZ/NON-VBV/DUMPS.
Cyberint conducted an in-depth analysis of a subset of the leaked payment card data involving six major local banks, totaling 45,195 cards. Our analysis showed that 42,310 of these stolen cards were unique or first observed in the Argos intel collection.
Regarding the validity of the stolen payment card dataset, additional details such as user agents, IP addresses, dates of birth, and email addresses suggest with high confidence that the information is authentic and not generated. The validity of cards obtained through phishing can vary; however, they often demonstrate a relatively high validity rate due to several factors. These include direct acquisition from cardholders who input their card details and personal identifiers on phishing websites, targeted attacks that enable the creation of personalized and convincing phishing messages, and the freshness of the data, which depends on how timely it is released. Customer feedback from b1ack’s operations further corroborates this assessment.
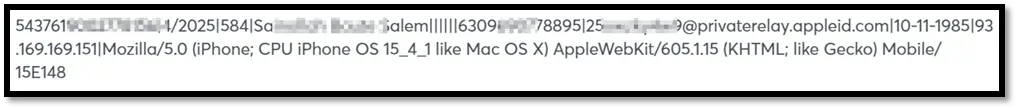
Our investigation into the activities of b1ack’s Stash has unveiled a substantial threat to the security of payment card data across local banks. Analysis of the leaked data, likely sourced from phishing campaigns, suggests a high probability of the validity of these stolen cards based on the available information. A significant portion of this data was uniquely identified in our intel collection.
The marketing strategies of b1ack’s Stash, which range from massive releases to consistent minor free releases, along with the potentially diverse phishing techniques employed by the threat actor or its affiliates, highlight the urgent need for enhanced security measures and vigilant monitoring to protect sensitive financial information and prevent future breaches.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

©1994–2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


