


Cybercriminals are always on the lookout for vulnerabilities to exploit and steal sensitive information. One such threat is credential stuffing, a type of cyberattack that can cause significant damage to both individuals and businesses.
Credential stuffing is a cyberattack that involves the use of stolen account credentials to gain unauthorized access to user accounts on other systems. In other words, attackers use lists of stolen usernames or email addresses with their corresponding passwords, often obtained through a data breach, to gain access to other systems. They do this by directing large-scale automated login requests against a web application.
Unlike password cracking, which involves guessing passwords or using brute force, credential stuffing attacks rely on the fact that many users reuse the same credentials across multiple accounts. This makes these attacks highly effective, with success rates of up to 2% for one million stolen credentials.
Open Bullet 2 is a web testing tool created for developers, but it has become popular among hackers who use it for credential-stuffing attacks. Attackers can easily automate these attacks and avoid detection by using a combo wordlist, distributed IPs via proxies, and manipulating request headers/cookies. Open Bullet 2 can also solve various CAPTCHA challenges, making login attempts appear much like legitimate customer activity.
The most concerning aspect of Open Bullet 2 is that it allows attackers to appear like real users, making attacks very challenging to detect. Open Bullet 2 is free, available for anyone to download and use, and comes with a user-friendly interface and up-to-date configurations. Attackers can even access a dedicated forum where they can get help and advice from other users.
It’s crucial to keep in mind that even legitimate software like Open Bullet 2 can be misused. It’s essential to have strong, unique passwords for each account and enable two-factor authentication to prevent credential-stuffing attacks. Additionally, using reputable anti-malware software can help detect and prevent attacks.
Bullet 2 is a web automation software that allows developers to distribute or separate different projects using a mechanism that involves creating a .opk file. The .opk file is basically a ZIP archive with a different extension name. Those files usually contain 4 main files.
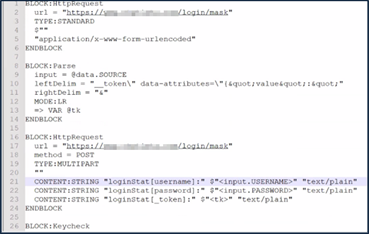
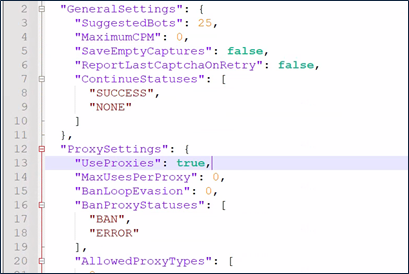
Analyzing these files can provide businesses with crucial insights into the methods that threat actors use to prepare for and carry out credential stuffing attacks. This knowledge is essential for enhancing security measures and protecting sensitive information.
The threat posed by credential stuffing attacks is significant and should not be taken lightly. By taking proactive measures such as using unique passwords, enabling two-factor authentication, and employing tools to detect and stop credential-stuffing attacks, users and companies can protect themselves and their sensitive information from cybercriminals.
Open Bullet 2 is a web testing tool for developers. Hackers and pen-testers alike are using it to automate credential-stuffing attacks, evading bot detection and fraud defenses. Open Bullet 2 makes login attempts appear like legitimate user activity.
Open Bullet 2 can be prevented by:
We learned a few ways to prevent using this tool from the configuration file. First, the actual operation of the Loli script depends on the specific implementation of the website. Small Changes to the website could potentially break the script.
The settings file can reveal some of the configurations the Open Bullet 2 program uses, such as the expected number of spike in login attempts. As this pattern could indicate the usage of the program, it is essential to note that those settings can be changed by other threat actors that bought this configuration file. Due to that, it is imperative to create rules that match more general guidelines than a specific use case.
Cyberint, the Impactful Intelligence company, reduces risk by helping organizations detect and mitigate external cyber threats before they have an adverse impact. The Cyberint Argos platform’s patented technology provides superior visibility through continuous discovery of the evolving attack surface, combined with the automated collection and analysis of vast quantities of intelligence from across the open, deep and dark web. A team of global military-grade cybersecurity experts work alongside customers to rapidly detect, investigate, and disrupt relevant threats – before they have the chance to develop into major incidents.
Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to protect themselves from an array of external risks, including vulnerabilities, misconfigurations, phishing, impersonation attacks, malware infections, exposed credentials, data leaks, fraud, and 3rd party risks.

Fill in your business email to start.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


