I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
Cyber threats are like microbes: They’re constantly evolving, and the defenses that worked against them yesterday may no longer work today. Just as a vaccine crafted for an earlier iteration of a virus may not be effective anymore, the cybersecurity tools and processes that shut down risks in the past might not be enough to keep your business safe today.
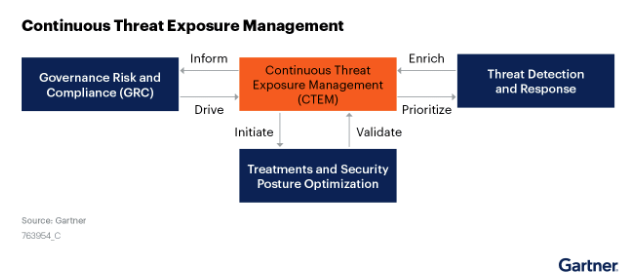
That’s why Continuous Threat Exposure Management, or CTEM, is a critical component of any cybersecurity strategy.
CTEM is the use of real-time data to detect and react to constantly changing threats on a continuous basis. Attack Surface Management (ASM) – meaning the process of identifying which potential attacks your organization faces and which parts of the IT estate they may impact – is just one part of it.
CTEM plays a central role in keeping businesses safe by helping them to adjust to changes in their attack surface. New vulnerabilities or exploit techniques can change an organization’s attack surface at any time, unless you continuously monitor for emerging threats using CTEM, you will struggle to defend against them before threat actors actually carry out attacks.
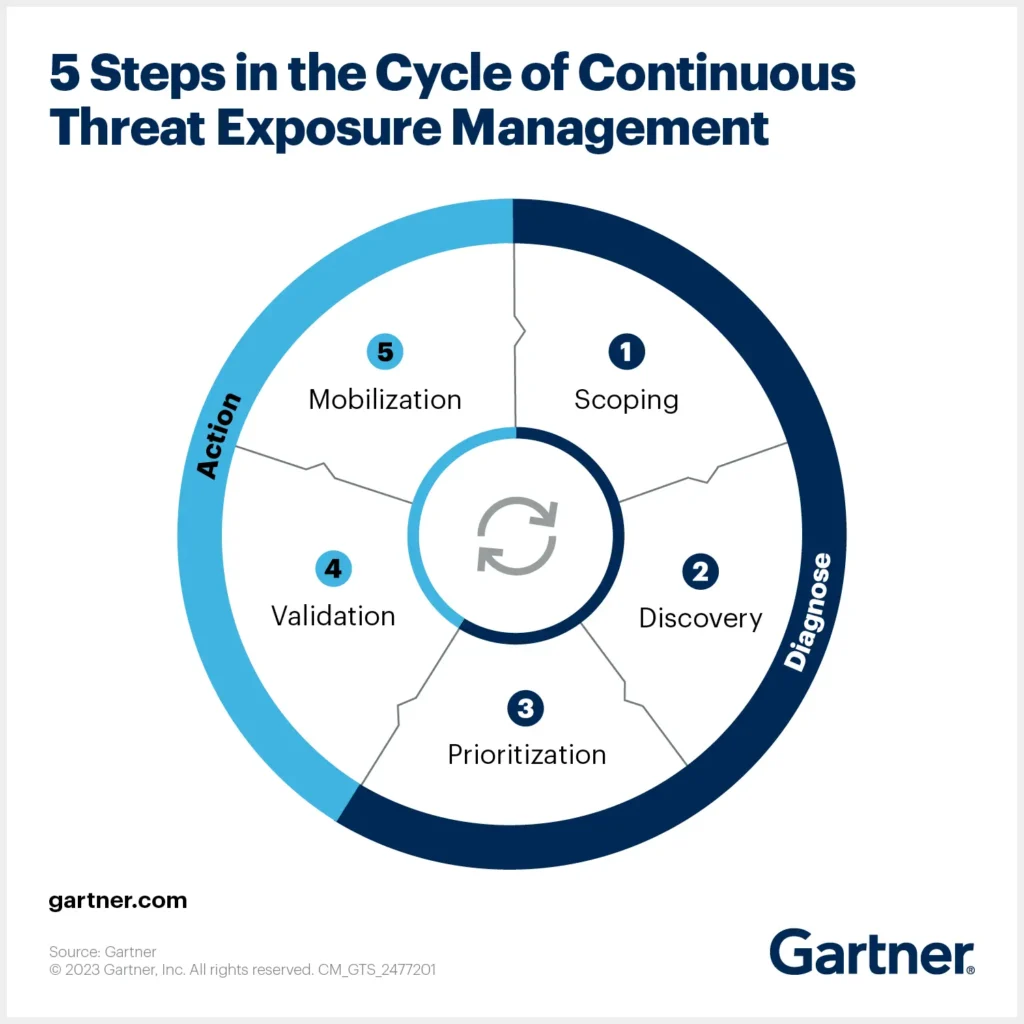
Here’s what it takes to put Continuous Threat Exposure Management into practice.
Scoping means determining the scope of the assets that your company owns, and that may be subject to cyberattacks. For example, scoping allows you to identify which domains, subdomains, IP addresses etc. your organization manages.
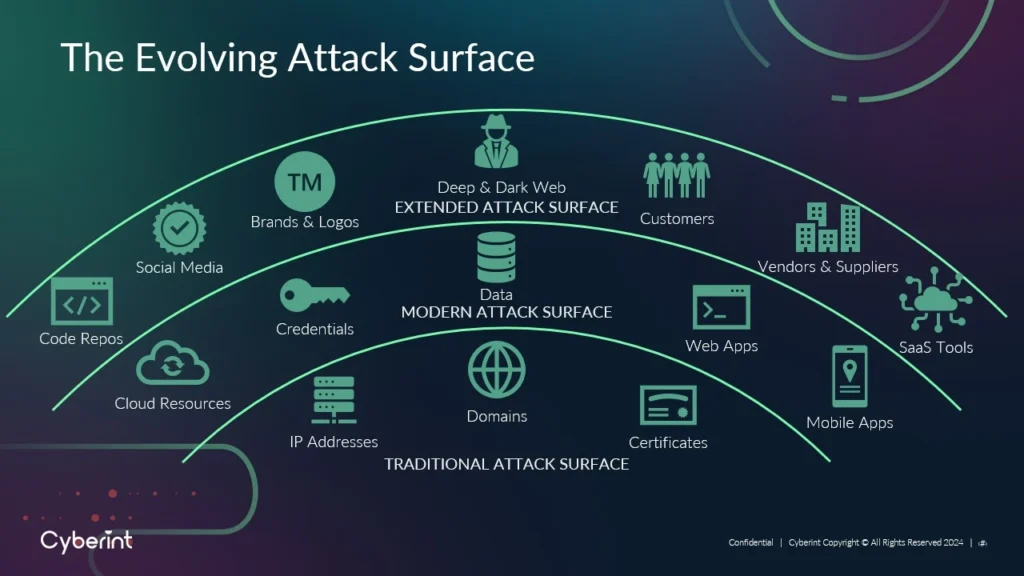
Scoping can also extend to non-standard assets that might expose you to attack, such as social media accounts or third-party technologies you depend on – a critical consideration given that attack surfaces have become much larger and more complex. As Microsoft notes, today’s “broader, more dynamic environment results in an expanded set of attack surfaces.” See the image below for Cyberint’s definition of an organization’s attack surface.
Scoping is essentially a form of ASM; an ASM tool actively mapping and tracking company assets is key to effective scoping. Attempting to track your asset scope manually isn’t realistic in most cases because assets change too quickly. You need software that can continuously map assets as your attack surface evolves.
Once you have a list of your assets, you can move onto discovery, which means identifying threats that may impact them. Typical ASM tools don’t discover threats like lookalike domains, phishing sites, fraudulent social media pages and leaked Dark Web data, but these threats are critical. It’s crucial to test all your assets in relation to Mitre attack scenarios.
“By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.”
Gartner
Not all threats pose the same level of risk, which is why prioritization is an important part of CTEM. Prioritization allows you to determine which threats to address first, based on both how likely they are to trigger an attack and how much damage a potential attack could cause.
Prioritization is important because it helps organizations employ limited cybersecurity resources to maximum effect.

Unfortunately, many ASM tools don’t offer true prioritization. They may help prioritize threats for traditional types of assets, but they are not designed for rapidly growing attack surfaces. To achieve effective threat prioritization for modern IT estates, you need to factor in all threats against all assets then assign risk scores based on factors like the following:
By pairing ASM with threat intelligence and vulnerability intelligence, you can generate effective prioritizations for all threats.
Validation means confirming that security controls you’ve implemented to defend against threats actually work. This is where practices like penetration testing and Red Team exercises come in. They help you validate that the protections you’ve put in place will effectively stop attacks when threat actors attempt to carry them out.
The final step in CTEM is mobilization, which means correcting risks. Given the broad scope of modern attack surfaces and the highly dynamic nature of threats, the ability to optimize risk correction processes is essential. Playbooks can help in this regard by providing clear mitigation flows for your team to follow.
From continuous asset mapping to ongoing mitigation, Cyberint has you covered at all stages of the CTEM process:
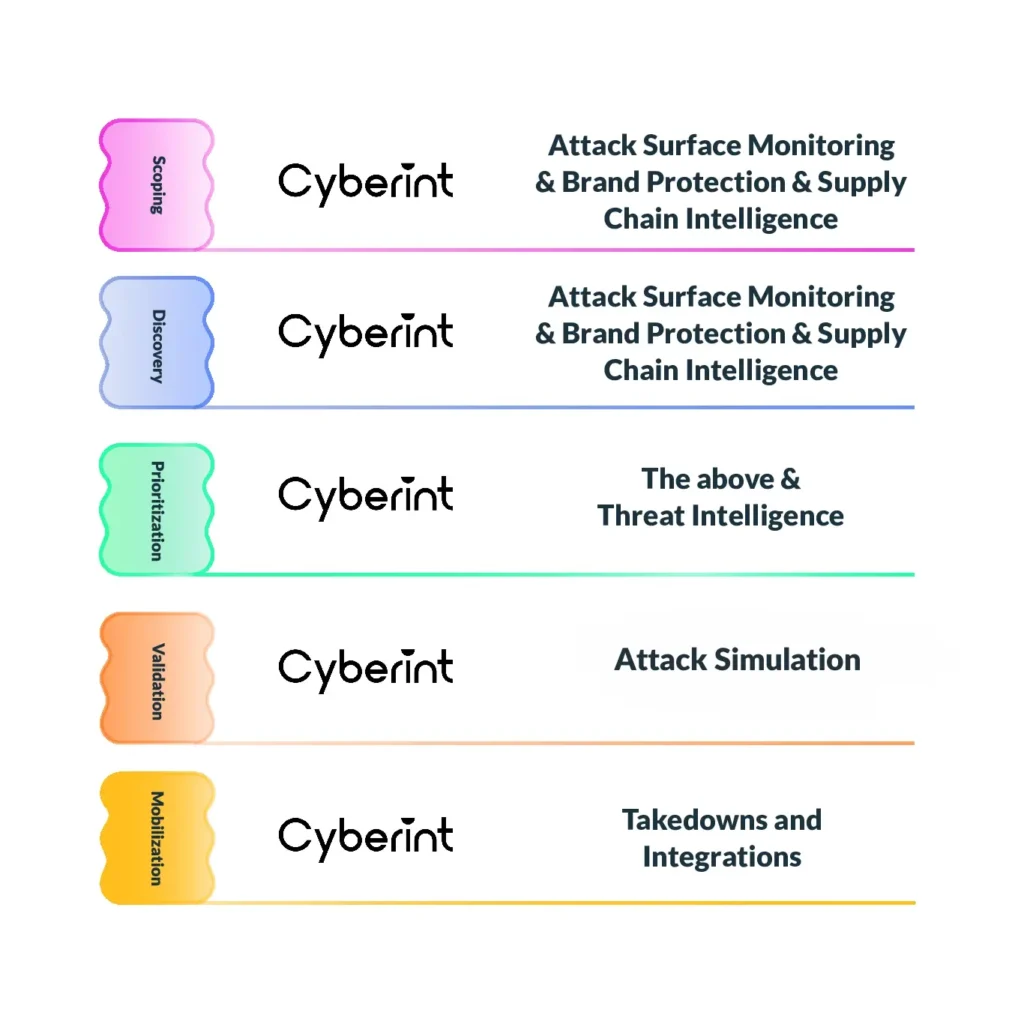
Learn more about how Cyberint helps businesses operationalize CTEM by requesting a demo.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start