Originally published: April 2023
Updated: September 2025
Supply chain attacks are a growing and increasingly sophisticated form of cyber threat. They target the complex network of relationships between organizations and their suppliers, vendors, and third-party service providers. These attacks exploit vulnerabilities that emerge due to the interconnected nature of digital supply chains, which often span multiple organizations, systems, and geographies.
By compromising a trusted component or software within the supply chain, malicious actors can infiltrate the target organization, circumventing traditional security defenses and catching victims off guard. As the world becomes more reliant on global, interconnected digital supply chains, understanding the risks and implications of a supply chain attack is crucial for maintaining security and resilience.
Supply chains are often associated with nation-state sponsored groups aiming to conduct cyber espionage or disrupt critical infrastructure, but it is essential to recognize that recent supply chain attacks are not solely the domain of such groups. Financially motivated cybercriminals and hacktivist groups have also adopted this attack vector to achieve their objectives. These malicious actors exploit vulnerabilities in supply chain vendors to infiltrate targeted organizations, propagate malware, and gain unauthorized access to sensitive information.
In this blog we will focus on third-party cyber attacks and the recent spike in “third-party breached and update tampering attacks”. These attacks are a type of supply chain attack that involves targeting a supplier or vendor providing products or services to an organization. These suppliers or vendors may have access to the organization’s network or systems as part of their service delivery, and attackers can exploit this access to gain unauthorized access to sensitive information or compromise critical systems.
Third-party supplier attacks can take several forms, including:
1. Credential theft: Attackers may steal login credentials of the supplier or vendor to gain access to the organization’s systems. This can be done through phishing attacks, social engineering, or by exploiting vulnerabilities in the supplier’s systems.
2. Software or firmware tampering: Attackers may inject malicious code into the software or firmware used by the supplier, which can then be used to compromise the organization’s systems. This can be done during the development process, or by compromising the supplier’s software distribution channels.
3. Data theft: Attackers may steal sensitive data from the supplier’s systems, which can include data related to the organization’s operations or its customers.
4. Denial of service: Attackers may launch a distributed denial-of-service (DDoS) attack against the supplier’s systems, which can disrupt the supplier’s operations and affect the organization’s ability to access critical services.
During the last six months, we’ve witnessed a spike in supply chain cyber attacks affecting an enormous number of vendors. Here are the major incidents that took place recently:
In early September 2025, attackers executed what is now considered the largest supply chain compromise in npm’s history. They phished the credentials of a trusted open-source maintainer by sending a seemingly legitimate email from a freshly registered “npmjs.help” domain, which coerced them to enter two‑factor authentication details. Once access was gained, the attackers injected cryptocurrency‑stealing malware into more than 18 widely used npm packages, collectively downloaded by billions of applications each week.
The malicious code behaved in subtle yet dangerous ways. In browsers, it intercepted wallet transactions or replaced legitimate cryptocurrency addresses with attacker-controlled ones—even doing so in a way designed to evade human detection by using address strings visually similar to originals. Some functionality also targeted active transaction APIs, making real‑time modifications while maintaining user trust. The infrastructure supporting these operations included attacker‑hosted CDN buckets and a command server that collected credentials and wallet data.
From a defensive perspective, this breach underscores the high risk of trusted dependencies and the cascading impact of supply chain attacks. It demonstrates why continuous monitoring of open source ecosystems, active validation of dependent packages, and threat intelligence into attacker infrastructure are essential. Mitigation steps, such as locking down maintainer accounts with hardware 2FA, auditing dependency changes, pinning versions, and scanning upstream updates are crucial.
In August 2025, the integration between Salesloft and Drift was compromised. Attackers gained access to OAuth refresh tokens issued by organizations to allow Drift integrations. With those tokens, the threat actors accessed data from over 700 organizations, including CRM, cloud, collaboration, and email systems. This is despite the fact that no direct credentials or malware were required.
This case illustrates a shift in supply chain risk: compromise doesn’t always come through software or infrastructure. Risk can be zoomed in on trusted application integrations. The breach underscores the need for governance over delegated access, lifecycle management of app permissions, and continuous monitoring even for “trusted” vendor connections.
In early 2025, it was revealed that a supply chain attack had targeted GitHub Actions, specifically via compromised action workflows that exposed secrets and configurations. The Hacker News stated that the vulnerability allowed attackers to access tokens and credentials tied to CI/CD setups, exploiting trust in automation pipelines rather than traditional code dependencies.
This attack highlights a shift in supply chain risk: it’s not only library dependencies or vendor software being abused, but also the automation and orchestration layers (build, deployment, actions) that organizations trust implicitly.
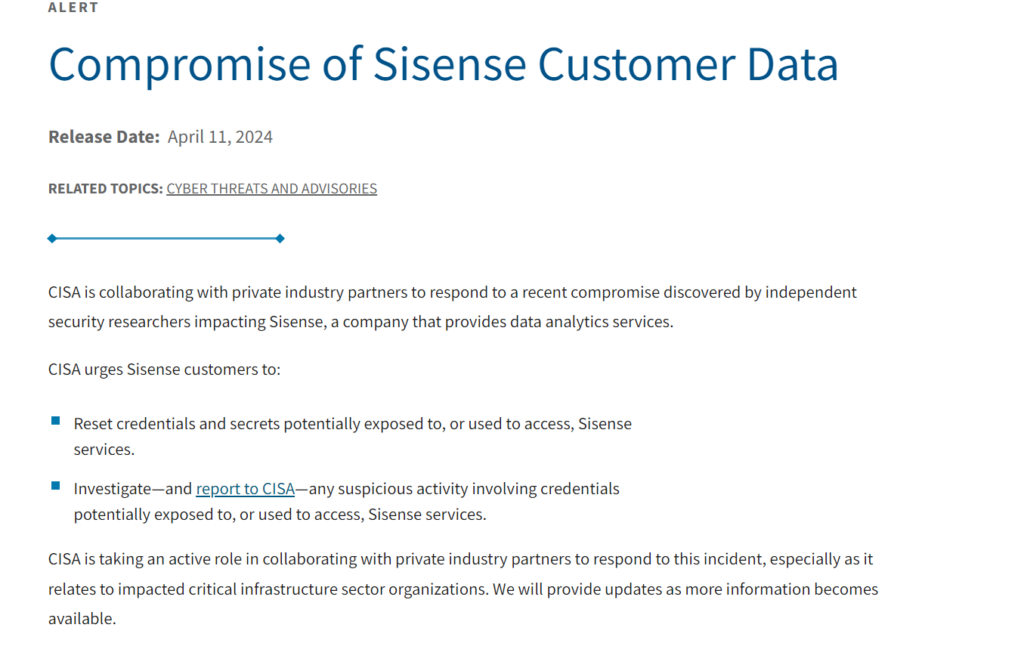
In April 2024, CISA announced that it was probing a breach at Sisense, a business intelligence firm facilitating monitoring of third-party online services. Customers were advised by both CISA and Sisense to reset any shared credentials and secrets promptly. CISA announced that it was taking “an active role in collaborating with private industry partners” to respond to the breach, with a focus on critical infrastructure organizations.
Sisense contacted customers following the breach to announce that had recruited “industry-leading experts” to aid the investigation and that business operations were not interrupted.
KrebsonSecurity cited multiple sources claiming threat actors accessed Sisense’s GitLab code repository that contained credentials for Sisense’s Amazon S3 account.
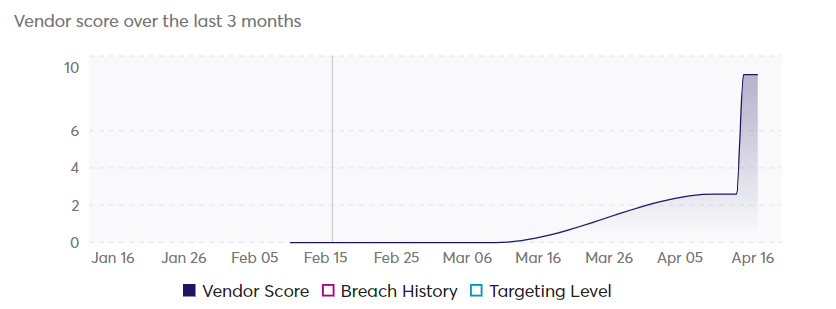
Okta, a provider of identity and authentication management services, reported in October that threat actors were able to access private customer data by obtaining credentials to its customer support management system. The threat actor had the capability to view files uploaded by specific Okta customers in recent support cases.
The cybersecurity company BeyondTrust wass among the recipients of Okta’s security alert. However, according to Marc Maiffret, Chief Technology Officer of BeyondTrust, this alert was delivered over two weeks after BeyondTrust had initially notified Okta about a possible issue.
The consistent data breaches experienced by widely-used companies like Okta, known for their sensitive capabilities, have elevated their attractiveness as prime targets for threat actors. Consequently, Okta’s customers also become targets, as they are susceptible through this third-party supply chain.
In December Government officials warned that the SolarWinds hackers were exploiting a critical vulnerability in JetBrains TeamCity servers. This critical authentication bypass vulnerability raised the attention due to its high severity and potential impact. Unauthenticated attackers with HTTP(S) access can exploit this flaw to execute remote code and gain administrative control of affected servers, presenting a potential vector for supply chain attacks.
It’s been reported by CISA and the FBI among others, that a Russian Threat Actor named Cozy Bear has been exploiting CVE 2023-42793. This group is believed to be linked to the Russian Foreign Intelligence Service (SVR). A patch was made available in September. In the attack, threat actors gain admin access to the server and employ remote code execution. No user interaction is needed. Many large software companies use TeamCity servers for their CI/CD, with over 3,000 directly exposed.
In June, the MOVEit supply chain attack (CVE-2023-34362) targeted users of the MOVEit Transfer tool , which is owned by US company Progress Software. MOVEit is designed to transfer sensitive files securely and is particularly popular in the US.
The attackers have so far managed to compromise more than 620 organizations, including the BBC, Zellis, British Airways, Boots, and Aer Lingus. Personal identifiable information (PII) data that was leaked includes staff addresses, IDs, dates of birth, and national insurance numbers. A patch has since been released, and the US Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning, urgently recommending that users download the patch to prevent further breaches.
Ransomware group Cl0p has been linked to the attack. The attackers used exposed web interfaces (EWIs) to cause significant damage. The web-facing MOVEit application was infected with a web shell called LEMURLOOT. This was then used to steal data from MOVEit Transfer databases.
EWIs can pose a significant security threat. They serve as gateways to internal or confidential services, and if left openly accessible, these interfaces may be manipulated by potential attackers to extract sensitive data or infiltrate integral systems. To mitigate this risk, EWIs need to be detected and timely alerts need to be issued.
Ernst & Young also fell victim to the attack. On August 9th Ernst & Young sent out a letter to impacted Victims. In the letter they stated that they learned about the incident on May 31st and immediantly commenced an investigation into the issue’s scope. According to EY’s letter to the Maine Attorney General, 30,210 individuals were exposed in the attack, including credit card numbers, government ID numbers and more.
This attack shows how quickly a supply chain attack can escalate and how smaller vendors can have a massive impact on organizational giants such as the BBC and British Airways.
In March, the 3CX supply chain attack targeted Windows and macOS desktop apps, raising concerns about the integrity and security of the software’s supply chain. The attackers managed to compromise the apps by bundling an infected library file, which subsequently downloaded an encrypted file containing Command & Control information. This enabled the attackers to perform malicious activities within the victim’s environment.
The fact that the malicious versions of the apps were signed with valid 3CX certificates suggests that the company’s build environment may have been compromised. This resulted in the distribution of tampered apps directly from 3CX’s download servers. This highlights the vulnerability of software supply chains, as even a seemingly minor breach can have far-reaching consequences for customers who trust and rely on the software.
With links to the North Korean state-sponsored APT Lazarus Group, the attack demonstrates the increasing sophistication and persistence of threat actors targeting supply chains to infiltrate organizations and gain access to sensitive information.
In February, a recent supply chain cyber attack targeted a business partner of semiconductor company Applied Materials disrupted shipments and was expected to cost $250 million in Q1 2023 . The company has not identified the affected partner, but it is speculated that industrial equipment supplier MKS Instruments may have been the breach point, as they announced a ransomware attack on February 3 and had to reschedule their fourth-quarter earnings call.
Applied Materials referred to the targeted company as a “major” supplier. MKS Instruments was still recovering from the attack at that time, which impacted its Vacuum Solutions and Photonics Solutions divisions. This reportedly caused delays in processing and shipping orders.
On December 2022, the open-source machine learning framework PyTorch experienced a supply chain attack in which nightly builds were injected with malware. The attack was made possible by compromising the Python Package Index (PyPI) code repository of Torchtriton, a dependency of PyTorch. The malicious binary was designed to execute when the Triton package was imported, uploading sensitive information from the victim’s machine. The issue only affected the nightly builds of PyTorch on Linux, and stable package users were not impacted.
The PyTorch maintainers have removed Torchtriton as a dependency, replaced it with Pytorch-Triton, and created a dummy Pytorch-Triton package on PyPI to prevent similar attacks. They have also removed all nightly packages dependent on Torchtriton from their package indices and informed the PyPI security team of the incident.
An Iran-linked Advanced Persistent Threat (APT) actor, Agrius, deployed a new wiper called Fantasy in attacks against entities in South Africa, Israel, and Hong Kong. Active since at least 2020, Agrius primarily targets victims in Israel and the UAE. The group was previously known for using the Apostle wiper disguised as ransomware.
The supply chain attack involved an Israeli software developer that provides a software suite to organizations in the diamond industry. Agrius, the threat actor, targeted the software developer and managed to infect the developer’s customers with the new Fantasy wiper malware. This type of attack is considered a supply chain attack because the threat actor compromised the software developer’s product, using it as a conduit to infect the end-users, who were customers of the software developer.
The attack was relatively short, lasting less than three hours, but it affected five organizations, including a diamond wholesaler, an HR consulting firm, an IT support services provider in Israel, a South African organization from the diamond industry, and a jeweler in Hong Kong. The Fantasy wiper was named similarly to the legitimate software and was executed on all victim systems from the Temp directory within a 2.5-hour timeframe.
In the realm of software development and maintenance, dependencies, CI/CD pipelines, and software updates are essential components that streamline the development process and facilitate the rapid delivery of updates and new features. However, these components also present opportunities for attackers to exploit the complex web of dependencies, infiltrate CI/CD systems, and compromise update mechanisms. By targeting these critical aspects, malicious actors can potentially gain access to multiple projects, applications, and sensitive systems, effectively bypassing traditional security measures and delivering malicious payloads under the guise of legitimate updates.
The SolarWinds attack, also known as the SolarWinds supply chain attack, was attributed to a Russian state-sponsored hacking group known as APT29 or Cozy Bear. This group is believed to be linked to the Russian Foreign Intelligence Service (SVR). The attack, discovered in December 2020, involved the compromise of SolarWinds’ Orion software, which was subsequently used to distribute a malicious backdoor called SUNBURST to numerous organizations, including U.S. government agencies and private companies. The attackers leveraged this backdoor to gain access to sensitive data, conduct cyber espionage, and maintain a persistent presence within the targeted networks.
The perpetrator of the Codecov attack has not been definitively identified or attributed to a specific group or nation-state. However, given the nature of the attack, which involved compromising the Bash Uploader script used by Codecov and gaining unauthorized access to sensitive information in customer environments, it is likely that an advanced threat actor was responsible. The attack was discovered in April 2021, and the investigations that followed revealed that the breach had gone undetected for several months. As of now, there isn’t enough publicly available information to attribute the attack to a specific group or nation-state with certainty.
The Kaseya supply chain attack, which occurred in July 2021, was attributed to a Russia-based cybercriminal group known as REvil or Sodinokibi. REvil is a notorious ransomware-as-a-service (RaaS) group that has been responsible for multiple high-profile ransomware attacks against various organizations worldwide. In the Kaseya incident, the group exploited a vulnerability in the company’s VSA software to distribute ransomware to numerous managed service providers and their clients, resulting in significant disruptions and financial losses for the affected organizations.
Supply chain cyber attacks pose a significant risk to organizations of all sizes and industries. By understanding the nature of these threats and implementing appropriate security measures, organizations can better protect themselves against the devastating consequences of a successful supply chain attack. As cyber threats continue to evolve and become more sophisticated, a proactive and comprehensive approach to supply chain security is crucial for maintaining the integrity and resilience of our interconnected digital ecosystem.
To effectively mitigate these risks, organizations must adopt a proactive and comprehensive approach to supply chain security. This includes continuously monitoring and assessing the security posture of suppliers, vendors, and third-party service providers, as well as implementing robust security controls and incident response plans. Threat intelligence plays a crucial role in this process, enabling organizations to stay informed of emerging threats, vulnerabilities, and attack techniques, and to adapt their security strategies accordingly. By leveraging threat intelligence and fostering a culture of security awareness, organizations can better protect their supply chains and reduce the potential impact of future attacks.
Learn about Cyberint’s latest Supply Chain Intelligence module here.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start