


Indicators of Compromise, or IOCs, refer to artifacts or clues that may be identified on a network or system indicating a potential security breach. They can be Ips, domain names and more.
IOC feeds, are streams of data that provide cybersecurity teams with information in real-time about potential threats. These feeds include IOCs that have been identified as being associated with harmful activities like malware distribution, command and control servers, phishing websites, and more. If used correctly they allow SOC teams to uncover, classify, understand and mitigate these threats.
Threat intelligence feeds are essentially classified into five primary types:
Open-source feeds: These feeds are available to the public and can include various sources such as forums, blogs, newsletters (such as Alien Vault, C2IntelFeeds, tweetfeed.live and more ), social media platforms, and threat intelligence browser extensions. While they can be a useful source of information, they may necessitate additional manual analysis.
Commercial feeds: These feeds collect anonymized metadata from client networks and analyze it for threat-related data. They typically originate from established cybersecurity vendors and offer extensive insights into cyber threats.
Government and Non-Governmental Organization (NGO) Threat Intelligence Feeds: In some cases these are complementary or offered for a fee. They operate platforms to facilitate the exchange of threat data, such as the Department of Homeland Security’s Automated Indicator Sharing or the FBI’s InfraGard program.
Dark web IOC feeds: The dark web features marketplaces and forums that provide various Tactics, Techniques, and Procedures (TTPs) for cybersecurity. These include listings of domains for sale and websites infected with webshells.
Additionally, security forums often share malware analysis reports containing malware hashes and linked domains, which can help organizations block threats and enhance their defenses.
Community-based feeds: These are shared ventures between individuals and organizations exchanging threat information among themselves, which is particularly useful for specialized or unique security threats. Notable examples include ISACs and CISCP.
Having multiple IOC feeds from various sources is generally considered better than relying on a single feed because it provides a broader range of threat intelligence. Each source may have different areas of focus, methods of data collection, and analysis techniques, which can lead to a more comprehensive set of indicators.
Different feeds may specialize in various types of cyber threats or may have access to unique data sets. This diversity can help in identifying a wider range of potential threats.
If one feed fails to detect a new threat, another might catch it. This layered approach can provide a safety net and ensure that fewer threats slip through the cracks.
Multiple feeds allow for the cross-verification of indicators, which can increase the confidence in the data’s accuracy and relevance.
Combining feeds can offer more comprehensive coverage of the threat landscape, as some feeds might have better visibility into certain regions or specific types of cyber activities.
Organizations can tailor the combination of feeds to their specific needs, focusing on the most relevant threats to their operations.
It’s important to note that while having multiple IOC feeds provides many benefits, it also requires effective management to ensure that the volume of data does not overwhelm the security team. Proper integration, filtering, and prioritization of the feeds are crucial to maximize their effectiveness.
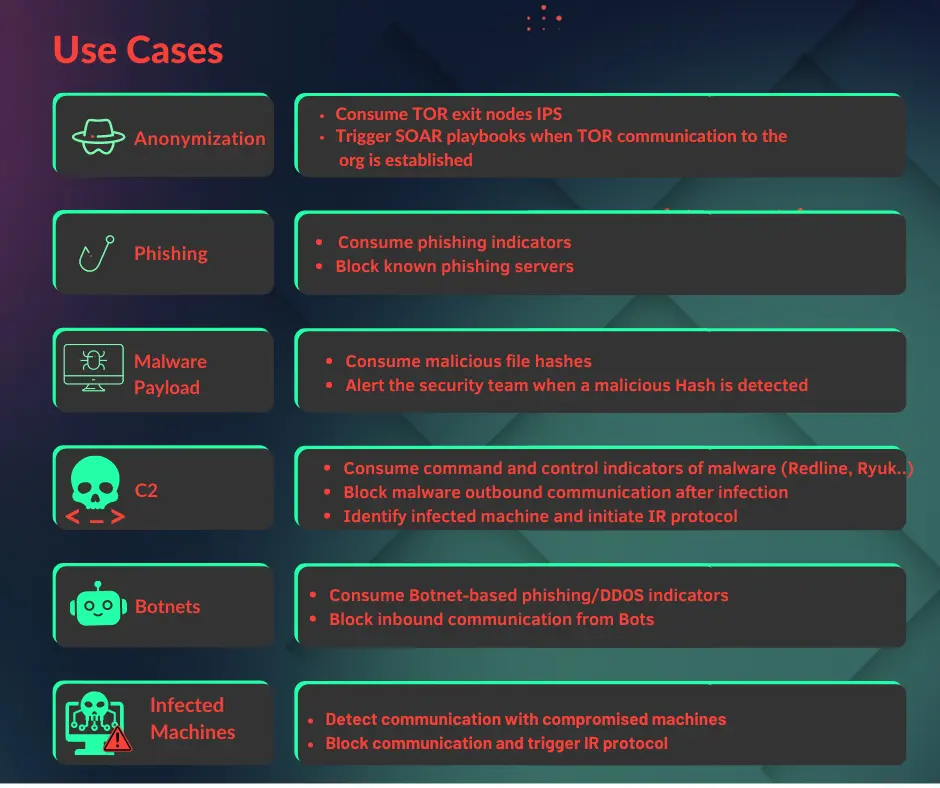
Although extremely useful on their own, when threat intelligence feeds are used in combination with each other cross-correlation can occur and the feed can be enriched. The TIP can then be fed into other SOC tools like a SIEM/SOAR. This enables organizations to prioritize which vulnerabilities to deal with first.
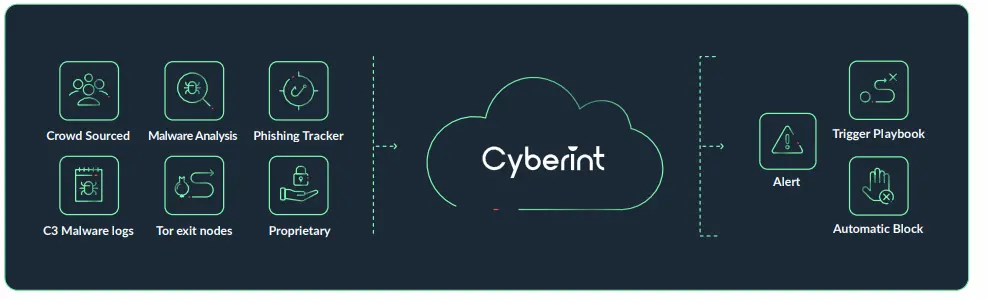
Cyberint’s Risk Intelligence Feed, API, and Google Chrome browser extension integrate IoC (Indicators of Compromise) data from multiple open feeds, as well as Cyberint’s proprietary intelligence, into one comprehensive source. The tool enriches your security stack, blocklists, threat intelligence research, and threat hunting program with IoCs, risk scores and context.
Cyberint collects and analyzes IoCs from best-in-class OSINT sources, as well as Cyberint’s unique array of open, deep and dark web sources.
Cyberint’s Risk Intelligence feed provides cybersecurity teams with structured and automated access to curated, high-fidelity, up-to-date data about emerging cyber threats. These feeds help you proactively detect and defend against evolving threats, in turn saving time and resources while increasing the value you derive from existing security tools and investments.
Each IOC includes several attributes:
The feeds are highly customizable, allowing cybersecurity teams to adjust them to their risk tolerance and other specifications. They can be downloaded manually or pushed into various security technologies like TIP, SIEM, SOAR, EDR, WAF, and Firewalls.

©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


