



I love to get stuck in and let the creative juices flow. My strengths lie in idea generation, development and execution. Over 5 years experience in B2B cybersecurity. I reign supreme when my imagination and creativity can run wild.
Your organization’s attack surface extends far beyond your direct control. Exposed cloud assets, vulnerable APIs, and the security posture of your third-party vendors all introduce significant risks. Understanding and managing this external exposure is paramount.
Effective External Risk Management (ERM) provides the critical visibility and intelligence needed to proactively address these threats. This post highlights essential ERM tools for 2025 that enable you to secure your organization from the outside in.
To effectively manage external risks, the right tools should offer a robust set of capabilities. Here are some key features to look for in leading ERM solutions:
The External Risk Management Market is a rapidly evolving area. According to the latest Frost & Sullivan ERMM report, several key players are leading the charge in providing innovative solutions. This section highlights ten noteworthy ERM tools in 2025, viewed through the lens of the comprehensive analysis provided by Frost & Sullivan, with a particular focus on how these solutions address critical aspects of external risk.
Cyberint’s solution offers a uniquely powerful and comprehensive approach to external risk management, now amplified by its acquisition by Check Point Technologies. This strategic alignment has created a synergy where Cyberint’s natively built external risk management capabilities seamlessly integrate with Check Point’s extensive security ecosystem, providing unparalleled visibility and protection from external threats.
Comprehensive External Asset Discovery – Cyberint, now a Check Point Company excels at identifying the full spectrum of an organization’s external-facing assets, extending beyond known domains to uncover shadow IT, cloud infrastructure, and interconnected resources.
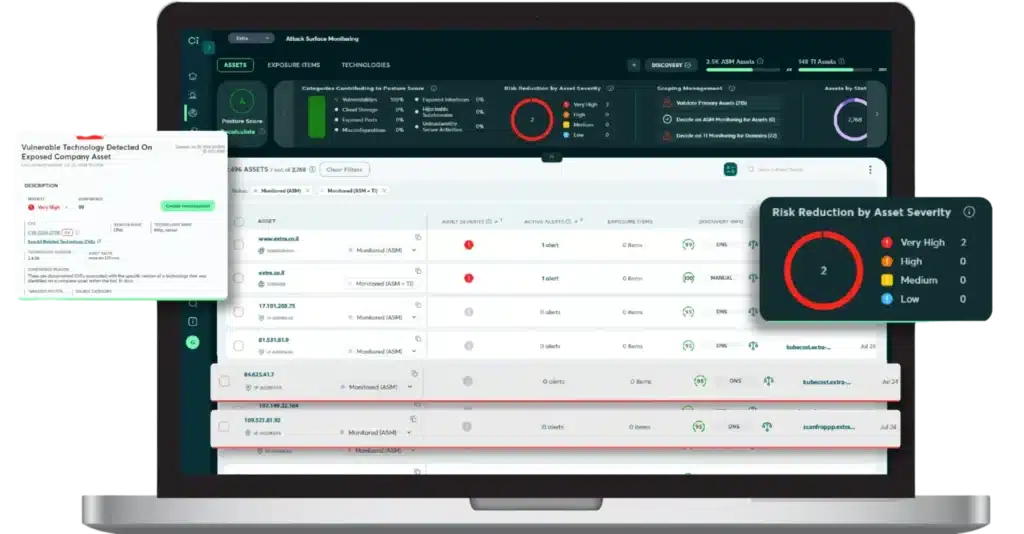
Continuous Attack Surface Monitoring with Active Exposure Validation (AEV) – Cyberint, now a Check Point Company provides continuous, real-time monitoring of the external attack surface. Critically, it incorporates Active Exposure Validation (AEV). Unlike passive scanning, AEV actively tests identified vulnerabilities to confirm exploitability, enabling security teams to prioritize and address genuine threats with greater accuracy and efficiency. This and other features led to GigaOm recently naming Cyberint as a Leader and an Outperformer in Attack Surface Management.

Native Integration and Unified Solution: Built from the ground up with a unified architecture, Cyberint, now a Check Point Company seamlessly integrates all its modules – from attack surface management to brand protection and third-party risk. This native integration ensures smooth data flow, correlated insights, and streamlined workflows.
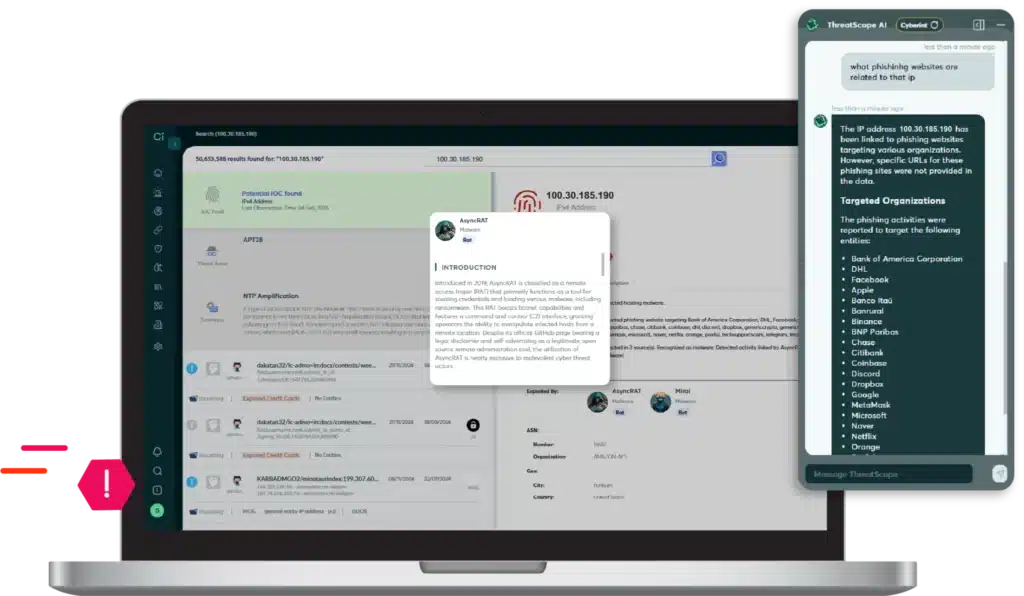
Actionable Threat Intelligence, Including Check Point’s IOC Feed – Cyberint, now a Check Point Company offers a wealth of threat intelligence, including Check Point’s industry-leading IOC (Indicators of Compromise) feed. This provides deep contextual awareness of emerging threats, threat actor tactics, and potential targets, enabling proactive defense and informed decision-making.
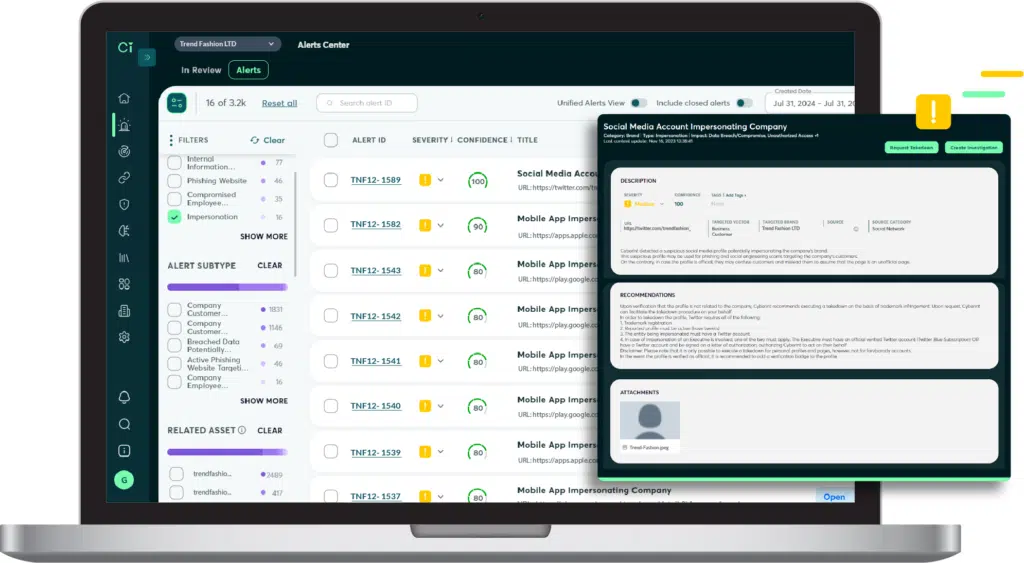
Robust Brand Protection and Digital Risk Monitoring – Protecting your brand is paramount. Cyberint, now a Check Point Company, offers advanced monitoring for social media impersonation, swiftly detects lookalike domains used for malicious activities, and identifies potential phishing campaigns targeting your customers and employees. Its rapid takedown speed and high success rate in neutralizing these threats minimize potential damage.
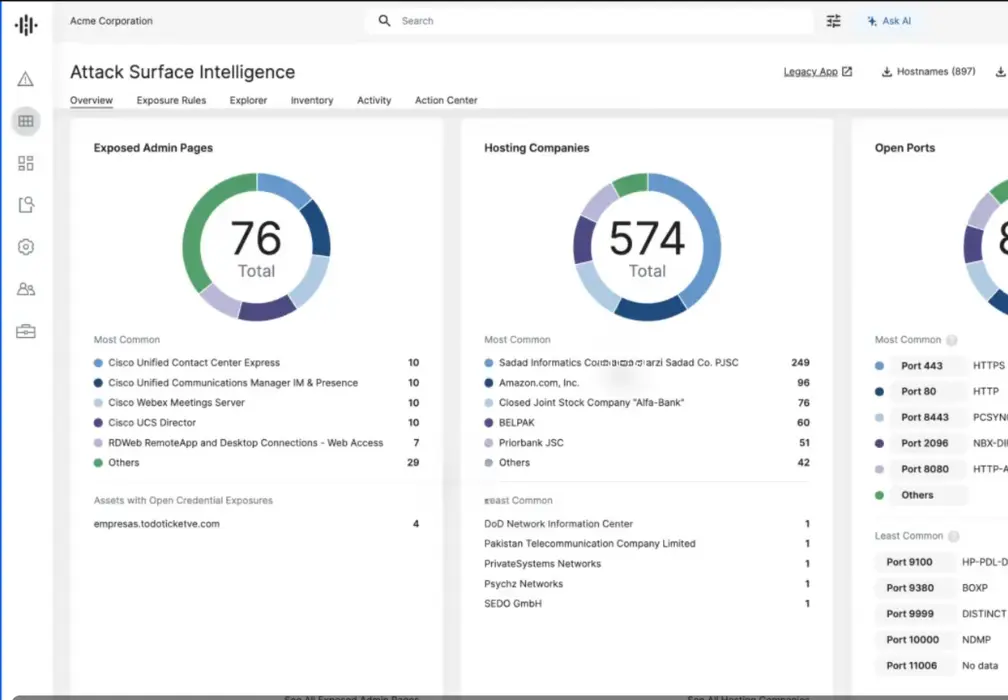
Proactive Third-Party Risk Management – Cyberint, now a Check Point Company, provides comprehensive capabilities to assess and continuously monitor the security posture of your third-party vendors, including tracking dark web activity regarding them, identifying potential risks that could impact your organization’s security.
Exceptional Customer Service and Support – Cyberint, now a Check Point Company, is committed to providing exceptional customer service, ensuring organizations receive the support and expertise needed to effectively manage their external risks. Cyberint’s dedication to innovation and customer success is reflected in its 51 Spring G2 awards, a testament to the value and effectiveness of the Cyberint solution as recognized by its users.

Prioritized Remediation Insights – Cyberint delivers clear, prioritized remediation guidance based on the severity and exploitability of identified risks, empowering security teams to focus on what matters most.
Scalability and Adaptability – The Cyberint solution is designed to scale with your organization’s evolving digital footprint and adapt to new and emerging threats. It offers multi tenancy and various pricing programs to allow for scale
2. Recorded Future – Frost & Sullivan’s ERMM report underscores the significance of robust threat intelligence for understanding the external threat landscape. Recorded Future, a prominent player in this domain is known for its powerful threat intelligence platform.
In the context of ERM, their capabilities can provide crucial context and understanding of external threats. By analyzing a wide range of open-source, dark web, and technical sources, Recorded Future helps organizations understand threat actor motivations, tactics, and targets, enabling them to better anticipate and mitigate external risks to their digital footprint and brand.
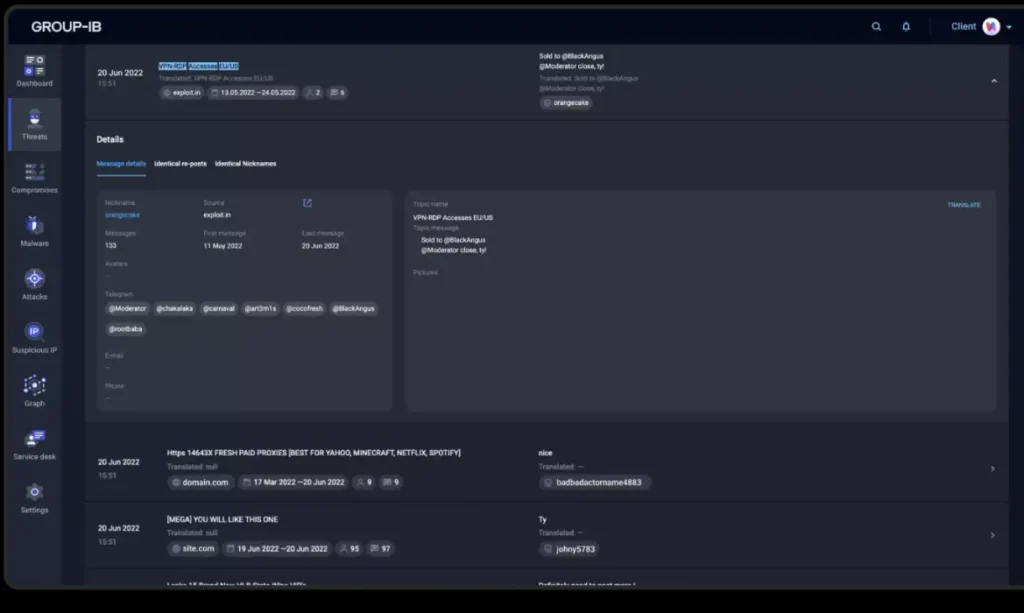
3. Group-IB is recognized for its expertise in threat intelligence, digital forensics, and incident response. In the context of ERM, their threat intelligence capabilities, particularly those related to underground cybercriminal activity and dark web analysis, can provide valuable insights into emerging external threats and potential attacks targeting an organization’s external infrastructure and brand. Their focus on high-fidelity threat intelligence can enhance an organization’s understanding of its external risk exposure
4. BlueVoyant offers a range of cyber security services and solutions, including external risk management. Their approach often involves a combination of technology and expert analysis to provide organizations with a comprehensive view of their external attack surface and potential threats. They focus on identifying vulnerabilities and risks across digital assets and third-party ecosystems.
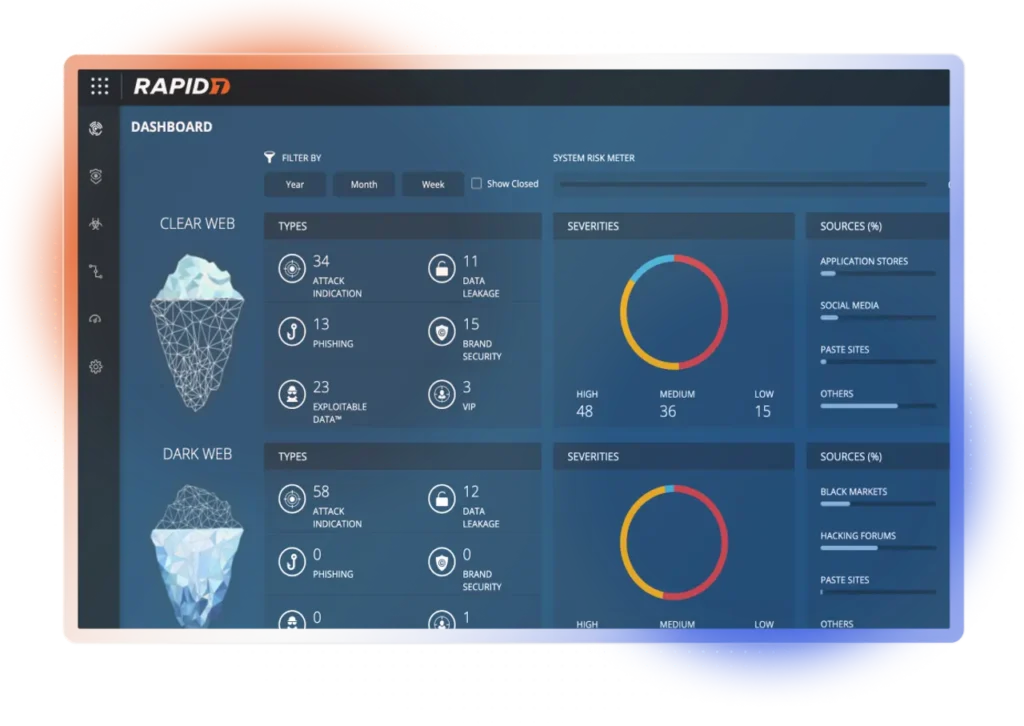
5. Intsights was recently acquired by Rapid7. While traditionally known for its vulnerability management and incident response capabilities, Rapid7 also offers solutions that contribute to external risk management. Their InsightVM platform can help identify externally facing vulnerabilities, and their threat intelligence feeds can provide context for external threats. Rapid7’s broader security analytics capabilities can also be leveraged for monitoring and responding to external risks.
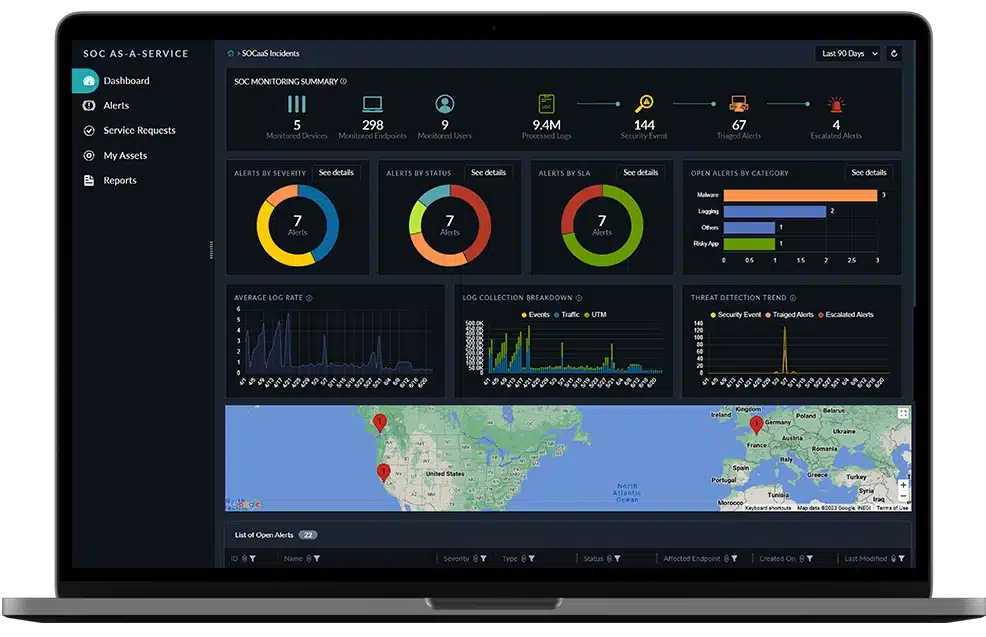
6. Fortinet, while primarily known for its network security solutions, including firewalls, they also offer capabilities that extend into the realm of External Risk Management. Their threat intelligence services, often integrated with their FortiGuard Labs, provide valuable insights into emerging external threats, indicators of compromise, and potential attack vectors. Furthermore, their security fabric approach can offer visibility into an organization’s external-facing assets and help manage the security posture of interconnected environments, contributing to a broader ERM strategy.
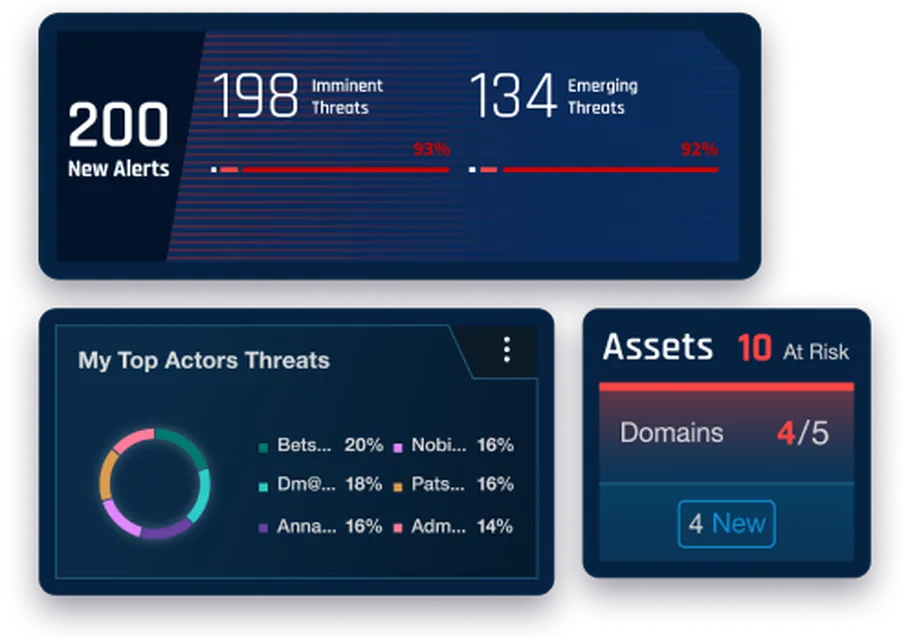
7. Cybersixgill, now BitSight specializes in providing cyber threat intelligence derived from the deep and dark web. Their platform offers insights into threat actor discussions, emerging attack trends, and leaked credentials that could be exploited to target an organization’s external-facing assets. By providing this unique visibility into the underground cyber landscape, Cybersixgill contributes to a more comprehensive understanding of external risks.
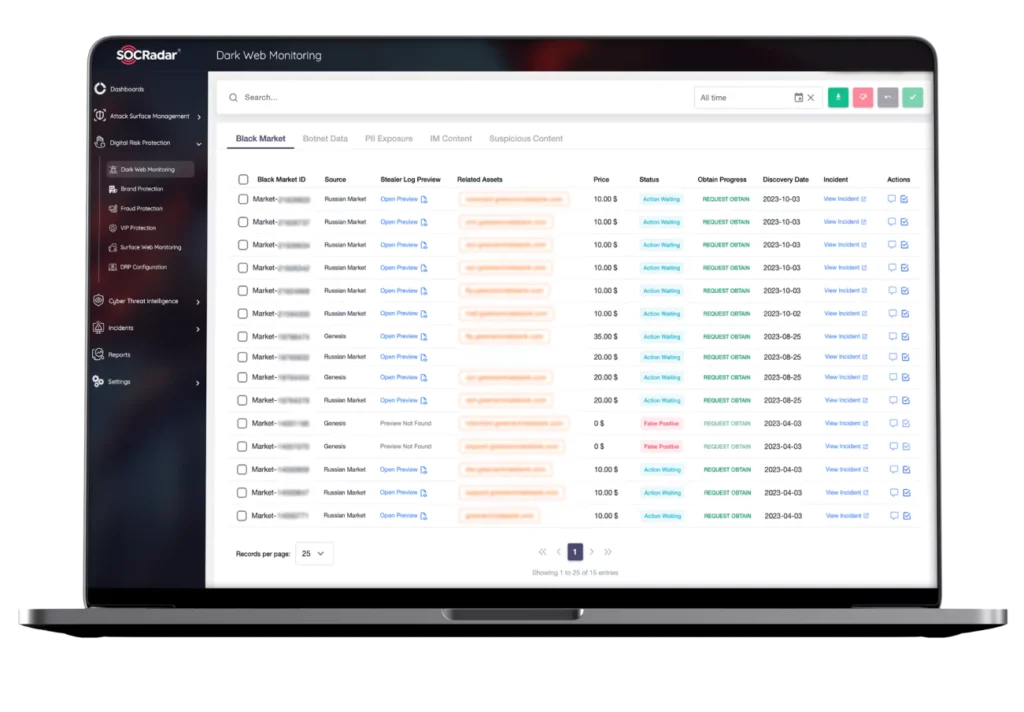
8. SOCRadar offers a comprehensive external threat intelligence and digital risk protection platform. Their capabilities include attack surface management, threat intelligence monitoring, and brand protection. SocRadar helps organizations discover their external assets, monitor them for vulnerabilities, and identify potential threats like domain squatting, phishing, and data leaks across the open and dark web.
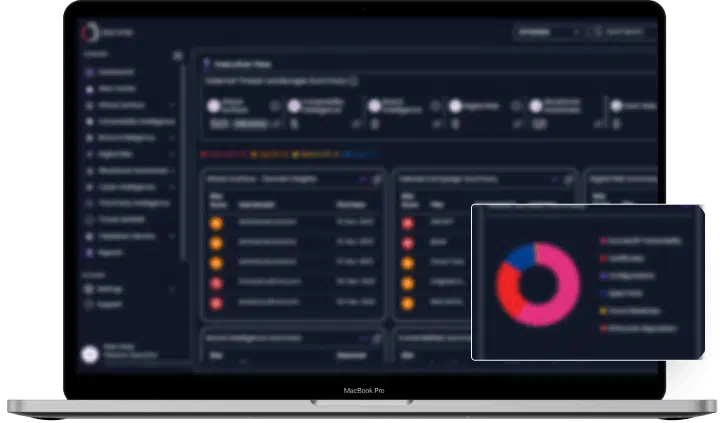
9. Cyfirma focuses on external cyber threat visibility and intelligence, taking a proactive approach to identifying potential risks. Their platform often incorporates threat landscape monitoring, digital risk protection, and early warning systems to detect emerging threats targeting an organization’s external assets, brand, and supply chain. Cyfirma’s emphasis on understanding attacker motivations and methodologies aligns with the proactive nature of effective ERM.
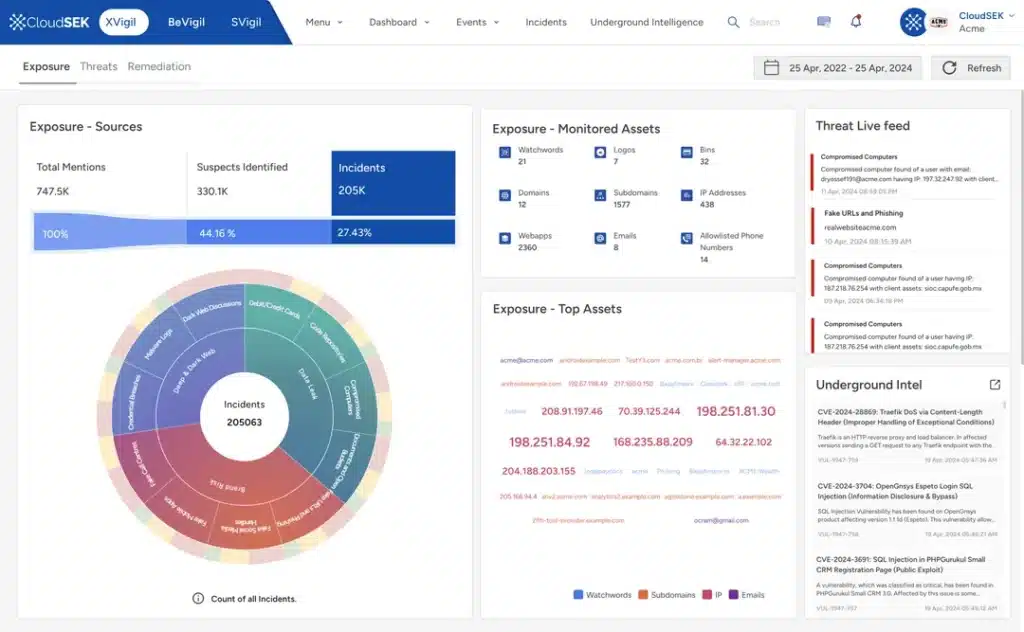
10. CloudSEK takes a unique approach to external risk management by focusing on attack surface monitoring and digital risk discovery using AI-powered analysis. Their platform aims to proactively identify potential security blind spots and external threats across web applications, cloud assets, and the open and dark web. CloudSEK’s emphasis on early detection and risk assessment aligns with the core principles of ERM.
Selecting the appropriate External Risk Management tools is a critical decision, and it’s not just about picking the most feature-rich platform. A successful ERM strategy requires a strategic look at your organization’s specific needs, budget, risk appetite, and industry landscape. Here are some key considerations when evaluating ERM tools and building your strategy:
By carefully considering these factors, organizations can select the ERM tool or tools that best align with your needs.
Get a Demo of Cyberint, now a Check Point Company’s solution.
©1994–2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright | Privacy Policy | Cookie Settings | Get the Latest News
Fill in your business email to start


