BlackGuard is a fairly new info stealer from the end of January 2022 with a business model of Malware-as-a-Service (MaaS). The malware is sold in underground forums and a dedicated Telegram channel of the operators’ named blackteam007.
The malware will look to obtain the assets info stealers often look for such as machine’s information, cookies, and browsing sessions, Various email and VPN clients’ credentials along with instant messaging applications’ credentials such as Telegram and Discord. Furthermore, the stealer supports the functionality to obtain browser-based cryptocurrency wallets such as Metamask.
The Cyberint Research Team recently discovered campaigns abusing gaming forums and Discord channels to distribute BlackGuard, along with a new data exfiltration technique using Telegram.
As mentioned, BlackGuard’s team advertises their product in underground forums and Telegram channel (Figures 1,2).
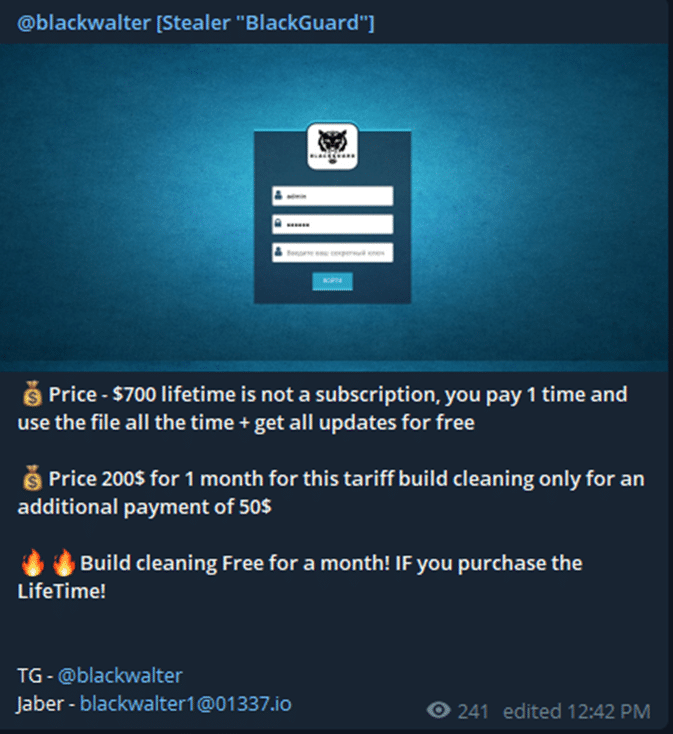
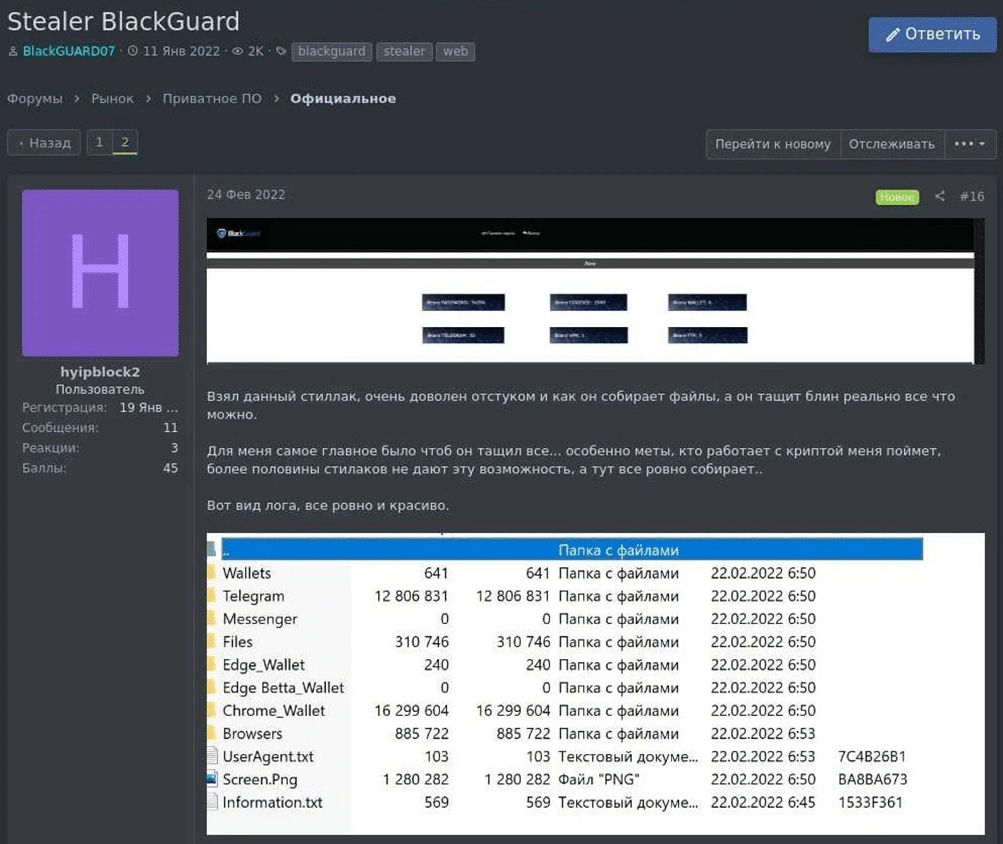
The purchasing is done via the Telegram channel created by the group. The price varies between 200 and 700USD depending on the subscription period, paid with cryptocurrency of course.
BlackGuard’s developers were advertising the malware since January 2021 on underground forums for a very short period of time, although for unknown reason they went silent only to come back on last January.
BlackGuard Team does not provide any delivery methods when purchasing the stealer. Therefore, the threat actor that is looking to purchase the stealer will need to apply its own delivery method.
It is very common within this type of threat to use malspam campaigns containing malicious documents that will download or load the BlackGuard stealer sample.
In this report, we have encountered a social engineering technique when a threat actor published a patch for the popular game CountnerStrike, presumably on gaming community forums or Discord channels.
The initial phase begins with a victim being lured to download and run the “patch”.
As the victim downloads and executes the malicious patch, the executable creates a new directory in the %APPDATA% directory named "NTDYxmw5zzLIBxcMt", a hard-coded name.
Once the directory is created, the loader will create two new executables (Figure 3) within this directory:
AnimeSoftware.exe – a somewhat legitimate file that is the real patch for the CounterStrike game.Natasha.exe – The BlackGuard sample.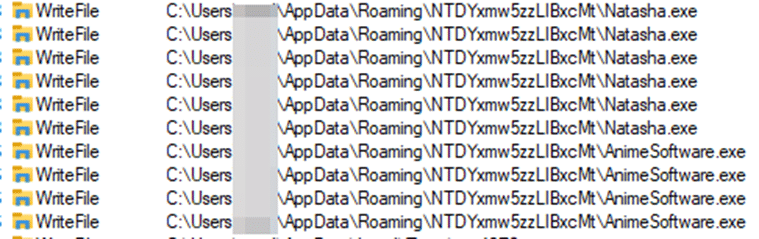
Once both files are created, the loader executes both files (Figure 4). The first one, AnimeSoftware.exe's purpose is to make the process look “as intended” while the second, Natasha.exe, initiates the information-stealing phase.

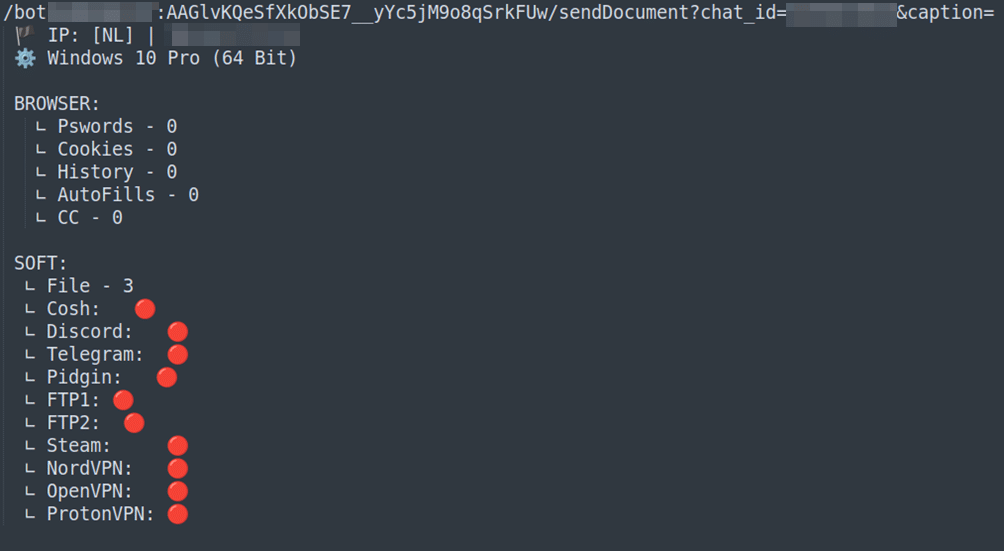
BlackGuard is focusing on valuable information such as cryptocurrency wallets, and browsers information including cookies, sessions, and history. It supports browsers such as Chrome, Edge, Firefox, Opera, Brave and more.
Furthermore, the notorious stealer looks for credentials in applications such as Telegram, Discord, FileZilla, Email and VPN clients. Among the VPN clients, it seems that BlackGuard targets ProtonVPN, OpenVPN and NordVPN.
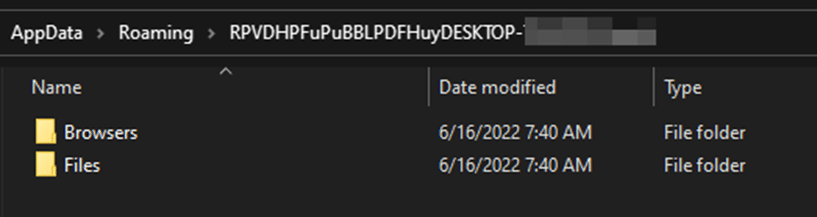
BlackGuard’s working directory is also located within the %APPDATA% directory as it creates and names it with a combination of random 14 characters, the victim’s machine name, and the username of the machine (Figure 5).
The information is zipped into a .rar file that will be sent later to the C2.
Like other malware that looks to use an anonymous and evasive C2 infrastructure, BlackGuard turned to Telegram as the ultimate solution.
Recent campaigns suggest that the info stealer has evolved in the past months and now exports the stolen data to a Telegram channel, presumably given by the operators of the MaaS.
BlackGuard uses the Telegram’s API service to create simple calls for the C2 channel as it sends metadata first using the sendDocument functionality (Figure 6), followed by a compressed file containing the relevant data.
Malicious CounterStrike Patch:
BlackGuard Samples:
Fill in your business email to start